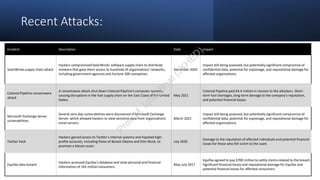
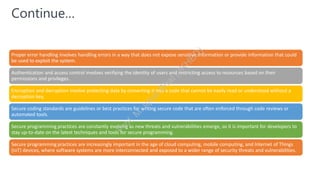
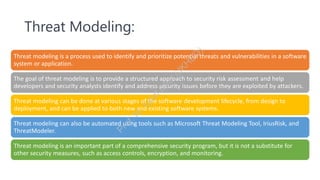
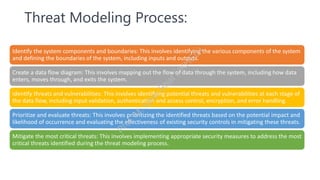
The document discusses program security as a set of practices to protect computer programs from unauthorized access and vulnerabilities, essential due to increasing cyber threats. It highlights recent security breaches and incidents, outlines goals and secure programming practices, and emphasizes the importance of threat modeling and security testing in the software development lifecycle. Additionally, it addresses security standards that organizations must adhere to for effective information security management.