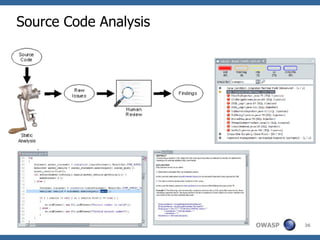
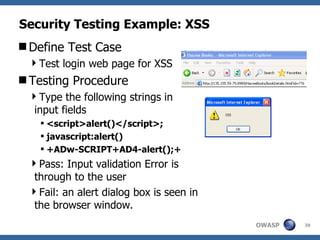
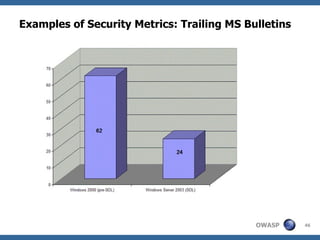
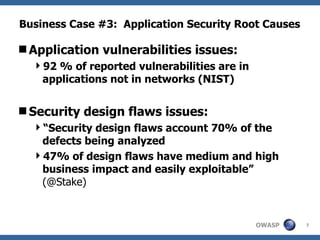
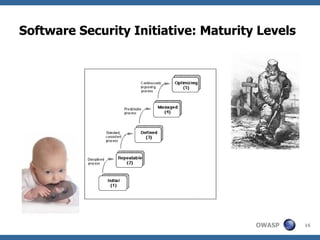
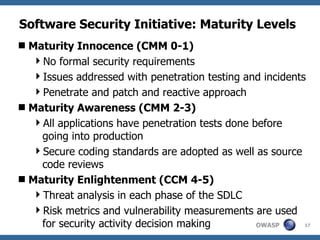
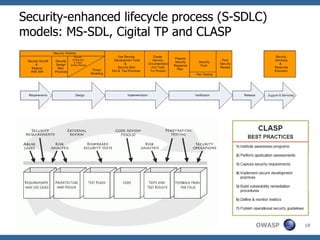
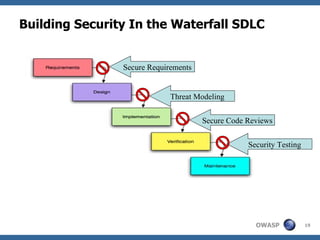
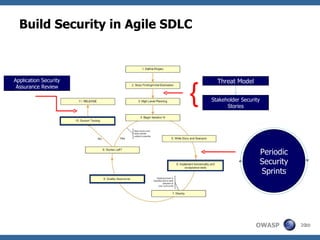
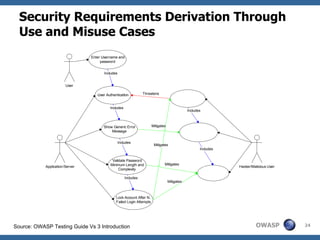
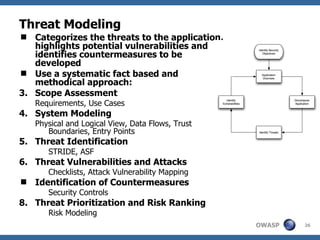
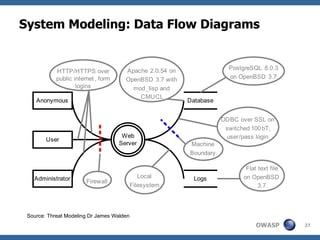
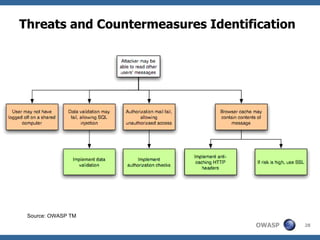
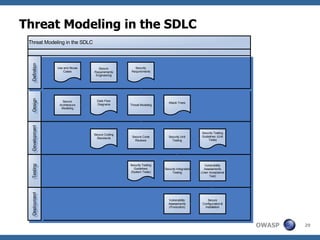
The document discusses approaches to building secure web applications, including establishing software security processes and maturity levels. It covers security activities like threat modeling, defining security requirements, secure coding standards, security testing, and metrics. Business cases for software security focus on reducing costs of vulnerabilities, threats to web apps, and root causes being application vulnerabilities and design flaws.








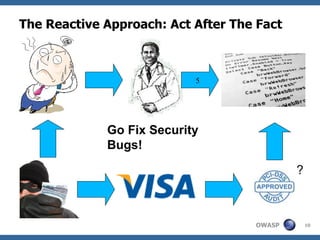
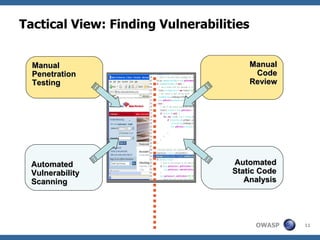
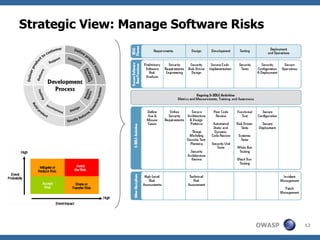
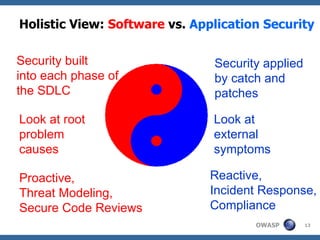










![Example SQL Injection - Secure coding requirements Use SQL parameterized queries, avoid dynamic SQL generation : SELECT * FROM users WHERE username=? JAVA EE use strongly typed “PreparedStatement” in .NET use “SqlCommand” with “SqlParameters” Sanitize input , remove special characters : ' " ` ; * % _ =&\|*?~<>^()[]{}$\n\r Use custom error messages: No SQL exception information in error messages](https://image.slidesharecdn.com/rochestersecuritysummit-1227478857155272-9/85/Software-Security-Engineering-34-320.jpg)