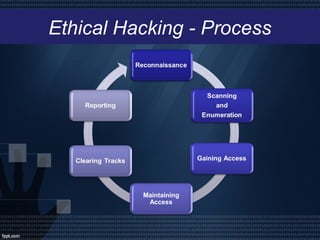
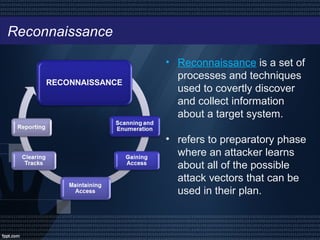
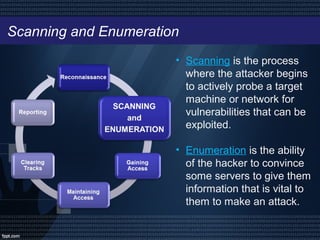
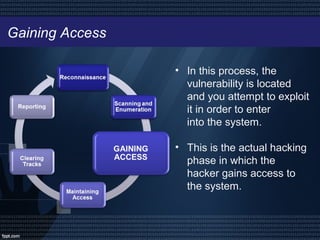
Ethical hacking involves legally probing computer systems or networks to identify vulnerabilities and enhance security, with ethical hackers working to prevent unauthorized access and threats. The process includes steps like reconnaissance, scanning, gaining access, maintaining access, clearing tracks, and reporting findings. While ethical hacking can significantly improve system security, it relies heavily on the hacker's trustworthiness and can be costly to hire professionals.