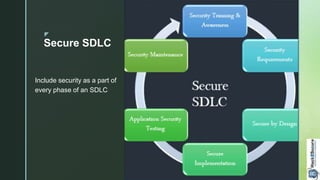
The document discusses the importance of integrating security into the Software Development Life Cycle (SDLC) to mitigate vulnerabilities and reduce risks associated with software applications. It outlines key phases of secure SDLC, including security training, requirement building, secure design and implementation, testing, and maintenance, emphasizing the need for structured processes and skilled personnel. Additionally, it mentions Hack2Secure's certification and training programs that support organizations in developing secure applications.