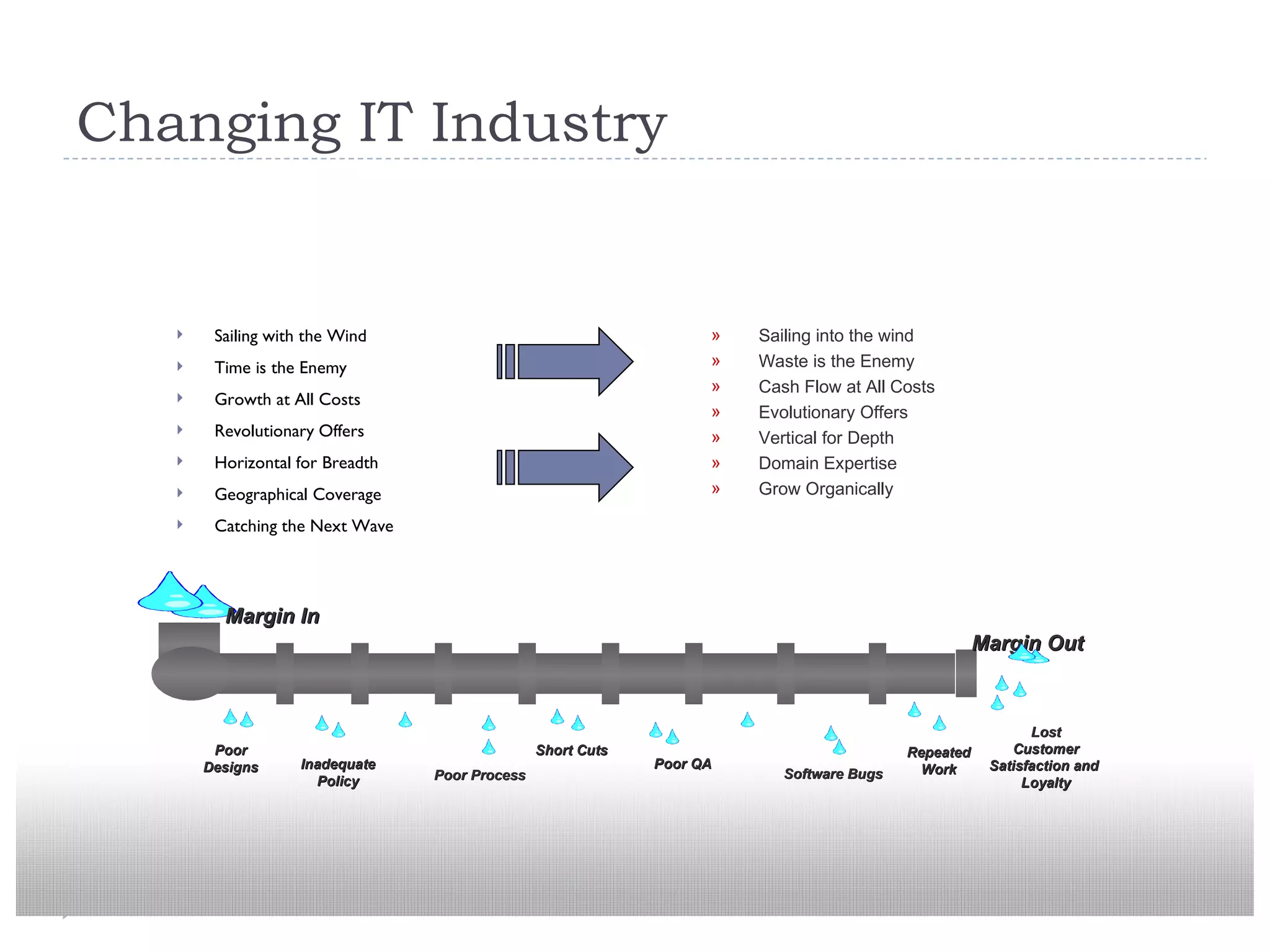
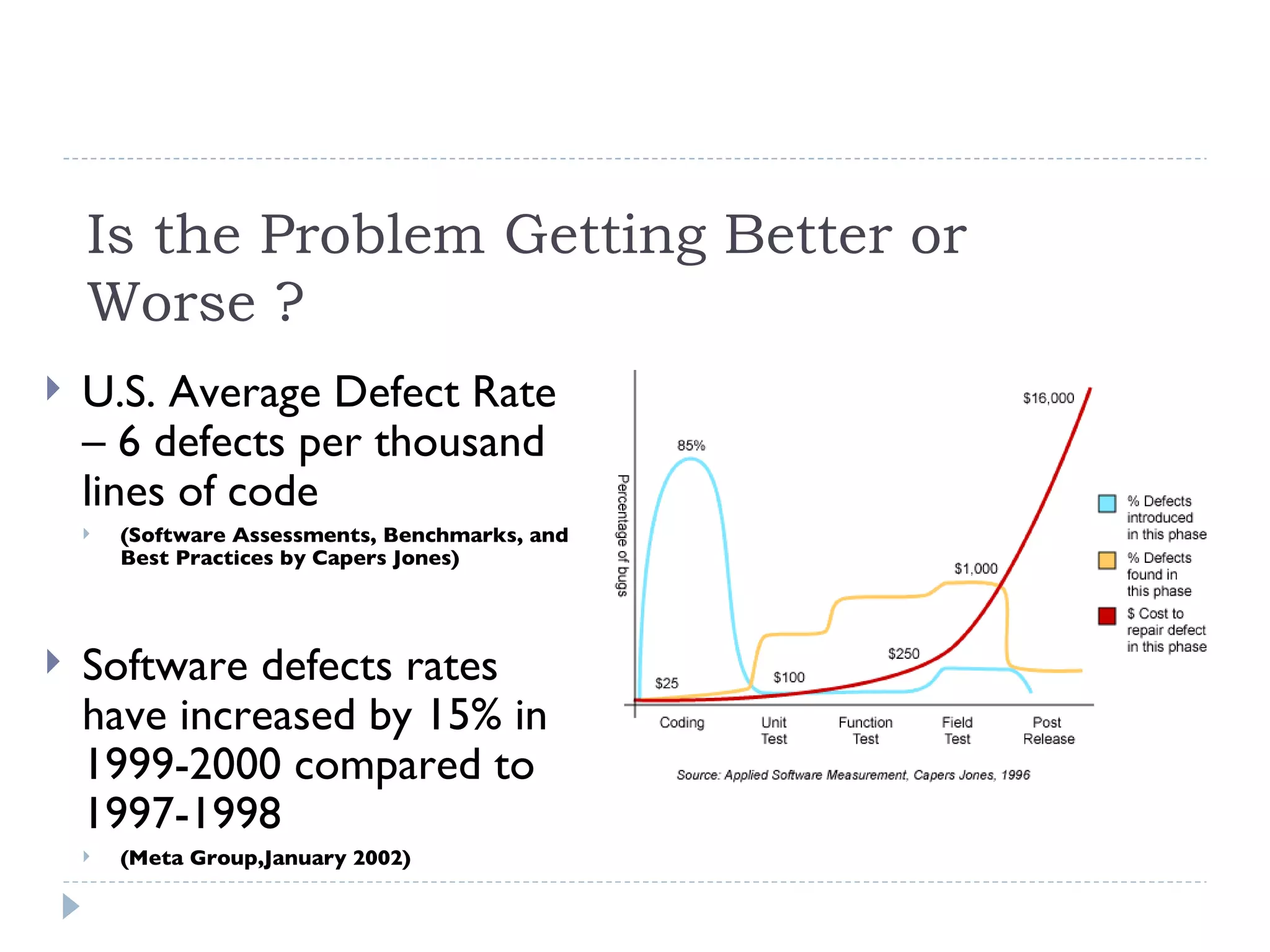
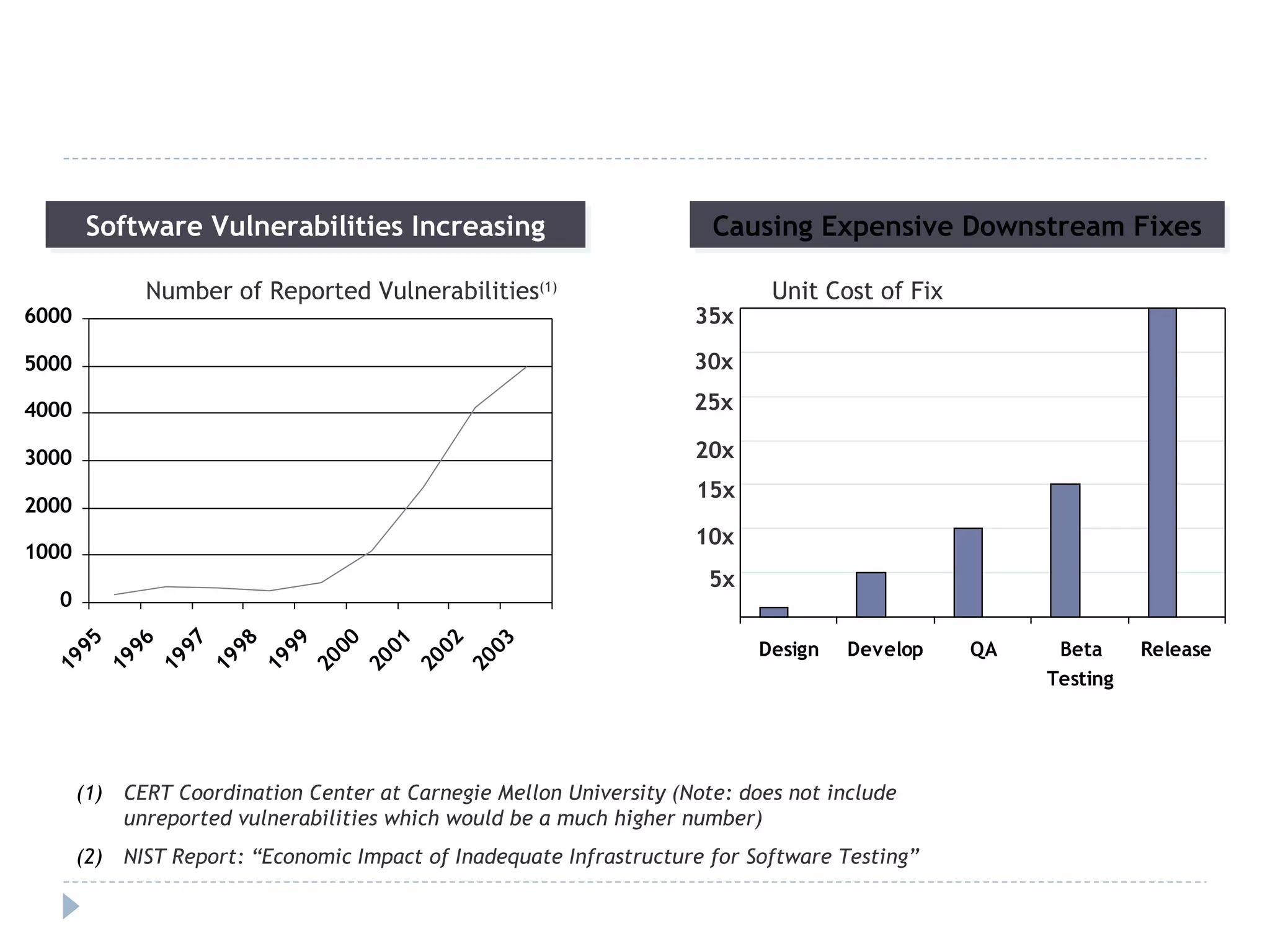
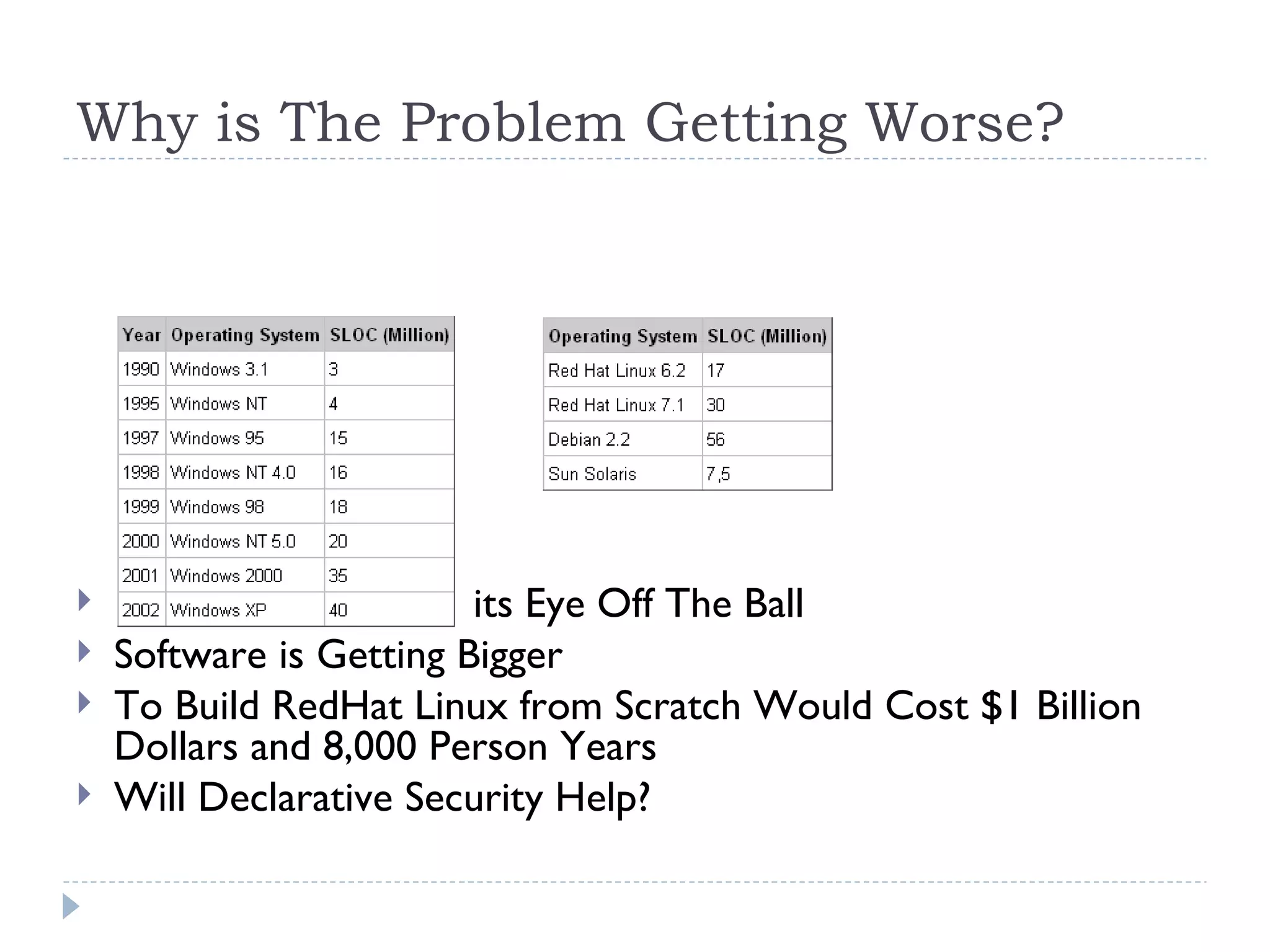
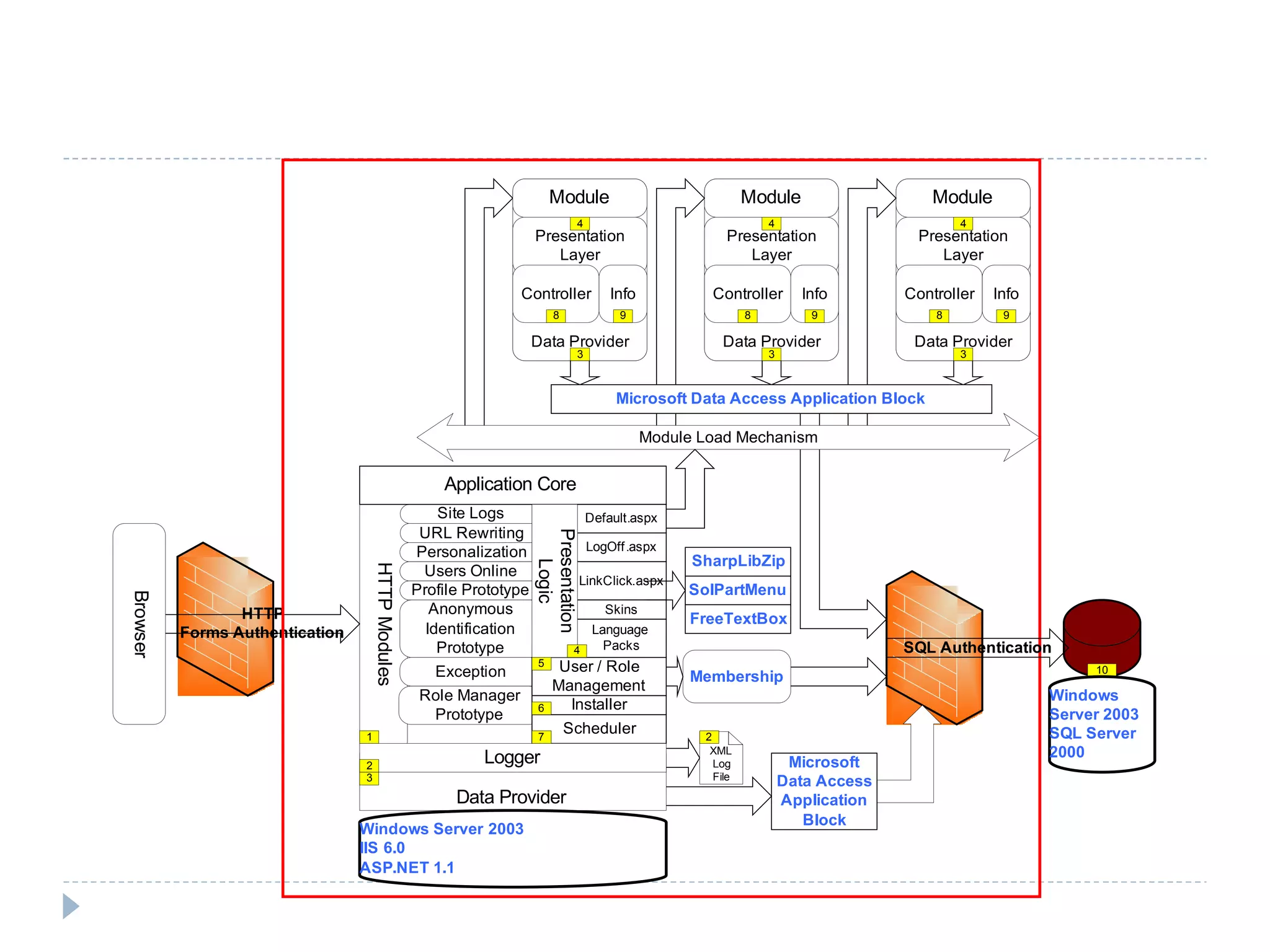
The document discusses security assessments and threat modeling for software applications. It provides an overview of the current state of the software industry and common security issues. It then describes the process for conducting a threat modeling session, including identifying security requirements, understanding the application architecture, identifying potential threats, and determining existing countermeasures and vulnerabilities. Conducting threat modeling helps prioritize testing and inform secure development practices.