S sdlc datasheet q1-2015 v fnl
•
0 likes•160 views
Developing applications securely is important to avoid delays, vulnerabilities, and loss of revenue. Traditional development approaches often fail to consider security risks adequately, resulting in insecure applications that are costly to fix. To address this, companies must implement security practices across the entire software development lifecycle (SDLC) through frameworks like the Microsoft SDL. This proactive approach allows development, security, and risk teams to work together throughout the application development process to deliver secure products on time.
Report
Share
Report
Share
Download to read offline
Recommended
Effective Security Metrics

This document discusses how to effectively communicate about security issues with business stakeholders. It recommends framing security risks and opportunities in terms that business stakeholders understand and care about, such as revenue, profit, customers, reputation, and costs. When discussing security, reference documents the business already uses like annual reports, business plans, and internal documents. Choose words carefully and discuss impacts on the business. Up-level security conversations to focus on business objectives and outcomes.
Security Metrics Program

This document provides an overview of security metrics and how to develop an effective security metrics program. It discusses that metrics should be based on security goals and objectives, quantifiable, and useful for improving performance. The document outlines key steps for developing a metrics program including determining goals and baselines, selecting relevant metrics, gathering and analyzing metrics data, and using metrics for decision making and resource allocation. Examples of common security metrics and guidelines for effective metrics are also provided.
Strengthening Security with Continuous Monitoring

This paper examines the increased complexity of the healthcare industry, fueled by increasing reliance on automation, information technology, and the changing regulatory and reform environment. Healthcare organizations face an environment characterized by rapid changes in mandates, technology, and stakeholder expectations, all of which combine to increase the consequences of historical risks and generate new risks. Existing informal, siloed, and reactive risk management processes cannot effectively identify and manage the greatest, strategic-level risks facing the industry. Through years of working with commercial and government clients, Booz Allen Hamilton, a leading strategy and technology consulting firm, has developed a proven strategic risk management methodology to ensure the effective management of these strategic risks.
overview 2015

Developed numerous risk management and security programs for financial institutions and large companies, including operational risk programs, IT security programs, information security frameworks, disaster recovery policies, and intrusion detection systems policies. Provided consulting services related to risk assessment, security controls, and regulatory compliance. Established new business lines and sales channels in cybersecurity insurance and developed assessment tools to rate insurability. Delivered over 500 audit training classes to over 4,500 professionals on topics like integrated auditing, client/server systems, and distance learning. Conducted numerous security, audit, and risk-related presentations to executives, regulators, and professional organizations.
Using Security Metrics to Drive Action

The document discusses strategies and security metrics that can be used to effectively communicate a company's security posture to business executives and boards. It contains perspectives from 33 security experts on selecting metrics that tell a compelling story, are specific and measurable, demonstrate adherence to security plans and risk management, and link to business objectives. The experts emphasize choosing contextual metrics that assess critical risks and can be used to prioritize and drive security actions.
Meaningfull security metrics

This document discusses meaningful security metrics for various stakeholders. It recommends metrics that measure policy compliance, control maturity, and value at risk for CIOs. For operations managers, it suggests metrics that track systems outside of SLAs and security incidents breaching SLAs. For CISOs, suggested metrics include value at risk, compliance, and annual risk reduction compared to spending. For CEOs and boards, total exposure and unmanaged risk are recommended metrics. It also provides characteristics for effective security metrics and metrics for evaluating the metrics themselves.
MCGlobalTech Cyber Capability Statement_Final

MCGlobalTech is an information security and IT consulting firm that provides a full range of cybersecurity services including assessments, authorization, risk management, engineering, and network security. They have experience serving both government agencies and commercial clients. The document provides an overview of MCGlobalTech's capabilities and experience in order to establish them as a qualified cybersecurity partner.
Legal Compliance Software | Compliance Management 

Legal compliance management software, including governance, risk & compliance (GRC) systems and industry-specific solutions. https://www.chetu.com/legal/compliance.php
Recommended
Effective Security Metrics

This document discusses how to effectively communicate about security issues with business stakeholders. It recommends framing security risks and opportunities in terms that business stakeholders understand and care about, such as revenue, profit, customers, reputation, and costs. When discussing security, reference documents the business already uses like annual reports, business plans, and internal documents. Choose words carefully and discuss impacts on the business. Up-level security conversations to focus on business objectives and outcomes.
Security Metrics Program

This document provides an overview of security metrics and how to develop an effective security metrics program. It discusses that metrics should be based on security goals and objectives, quantifiable, and useful for improving performance. The document outlines key steps for developing a metrics program including determining goals and baselines, selecting relevant metrics, gathering and analyzing metrics data, and using metrics for decision making and resource allocation. Examples of common security metrics and guidelines for effective metrics are also provided.
Strengthening Security with Continuous Monitoring

This paper examines the increased complexity of the healthcare industry, fueled by increasing reliance on automation, information technology, and the changing regulatory and reform environment. Healthcare organizations face an environment characterized by rapid changes in mandates, technology, and stakeholder expectations, all of which combine to increase the consequences of historical risks and generate new risks. Existing informal, siloed, and reactive risk management processes cannot effectively identify and manage the greatest, strategic-level risks facing the industry. Through years of working with commercial and government clients, Booz Allen Hamilton, a leading strategy and technology consulting firm, has developed a proven strategic risk management methodology to ensure the effective management of these strategic risks.
overview 2015

Developed numerous risk management and security programs for financial institutions and large companies, including operational risk programs, IT security programs, information security frameworks, disaster recovery policies, and intrusion detection systems policies. Provided consulting services related to risk assessment, security controls, and regulatory compliance. Established new business lines and sales channels in cybersecurity insurance and developed assessment tools to rate insurability. Delivered over 500 audit training classes to over 4,500 professionals on topics like integrated auditing, client/server systems, and distance learning. Conducted numerous security, audit, and risk-related presentations to executives, regulators, and professional organizations.
Using Security Metrics to Drive Action

The document discusses strategies and security metrics that can be used to effectively communicate a company's security posture to business executives and boards. It contains perspectives from 33 security experts on selecting metrics that tell a compelling story, are specific and measurable, demonstrate adherence to security plans and risk management, and link to business objectives. The experts emphasize choosing contextual metrics that assess critical risks and can be used to prioritize and drive security actions.
Meaningfull security metrics

This document discusses meaningful security metrics for various stakeholders. It recommends metrics that measure policy compliance, control maturity, and value at risk for CIOs. For operations managers, it suggests metrics that track systems outside of SLAs and security incidents breaching SLAs. For CISOs, suggested metrics include value at risk, compliance, and annual risk reduction compared to spending. For CEOs and boards, total exposure and unmanaged risk are recommended metrics. It also provides characteristics for effective security metrics and metrics for evaluating the metrics themselves.
MCGlobalTech Cyber Capability Statement_Final

MCGlobalTech is an information security and IT consulting firm that provides a full range of cybersecurity services including assessments, authorization, risk management, engineering, and network security. They have experience serving both government agencies and commercial clients. The document provides an overview of MCGlobalTech's capabilities and experience in order to establish them as a qualified cybersecurity partner.
Legal Compliance Software | Compliance Management 

Legal compliance management software, including governance, risk & compliance (GRC) systems and industry-specific solutions. https://www.chetu.com/legal/compliance.php
MCGlobalTech Commercial Cybersecurity Capability Statement

Mission Critical Global Technology Group (MCGlobalTech) is an information security and IT consulting firm that provides enterprise information security management services for commercial businesses. The document discusses why businesses need a formal security program to take an organized, enterprise-wide approach to managing security risks in a proactive manner. It outlines the key components of a security program and how MCGlobalTech can help clients develop a tailored program to protect their data, systems and meet their unique security needs.
'Re-writing' Infrastructure management

An efficient, ITIL compliant, round-the-clock service desk and infrastructure management for a global insurance firm.
When a global insurance and reinsurance provider needed an experienced IT infrastructure management partner, it turned to CSS Corp. Our experience in simplifying IT Operations for complex IT environments with a wide range of technologies made CSS Corp the ideal choice for this engagement.
The prominence of it lifecycle assurance

Maveric Systems is a leading provider of assurance services across the technology lifecycle. They offer requirements assurance, application assurance, and program assurance services to help clients in banking, insurance, and telecom deliver successful digital transformation programs. Maveric's assurance-only business model brings together diverse competencies to deliver high-quality assurance solutions tailored to each client's domain.
Jeff kushner trends in grc management

Modulo is a global leader in automated GRC management solutions with over 400 employees worldwide. It has developed its product for nine years and the product provides a mature, automated platform to help organizations manage increasing complexity and risk from constant changes in regulations, policies, people, processes, and technology. Previously, most organizations took a fragmented approach to GRC management using multiple disconnected systems and mostly manual processes, which introduced greater exposure, inefficiency, and higher costs. Modulo's solution provides a common GRC metaframework architecture across applications to help organizations gain enterprise-wide visibility, consistency, and automation while relieving the burden on their business through improved compliance and lower risk.
Accenture Banking Security Index

The Accenture Security Index, based on Accenture's High Performance Security research, assesses performance across 33 cybersecurity capabilities within the Banking industry. It is intended to help banking leaders understand the effectiveness of their security measures. To learn more about Banking results, read our blog series: https://accntu.re/2vj59KC
The Future of Your Security Operations - Part 2: Tech Integration

Integrating your security operations is no longer a nice to have, it’s a must. In this presentation you’ll learn the benefits of integrating your access control, video and other alerting systems for optimal security.
Presentation by: Dan Ireland, Director – Strategic Alliances, Resolver Inc.
Rethinking compliance

This document discusses rethinking approaches to compliance to focus on business continuity beyond just security. It notes that data breaches are inevitable so compliance activities need to ensure systems can continue running when failures occur. It advocates taking a proactive approach through standards like ISO and continual disaster recovery testing to prove systems can be recovered. It also stresses designating a compliance team and accountability for continually reviewing practices.
Security metrics 

This document discusses the importance of cyber security metrics for communicating with stakeholders and seeing overall security performance. It defines key performance indicators and key risk indicators for tracking security trends. The document outlines several types of metrics for controlling cyber security risk, including metrics to measure threat level, risk level, compliance level, and number of cyber incidents. Finally, it lists some specific cyber security KPIs that are important to track, such as patching times, number of intrusion attempts, and speed of detecting and resolving security threats.
An Intro to Resolver's Incident Management Application

Interested in seeing how Resolver is tackling the future of Incident Management? What about implementing something today? Get a first look at the relaunch of Incident Management on Core. Learn how we have taken the best of Perspective to a whole new (and often simpler) level. And we’re not stopping there — learn about the incident/investigation functionality and see how it all ties together with risks that impact the security of your organization.
BizCarta-2

BizCarta provides cyber security consulting services to help companies establish comprehensive cyber security strategies and integrated cyber defense platforms. They leverage their proprietary Adept 6 consulting methodology to assess clients' security gaps and develop customized solutions. BizCarta's services include cyber security consulting, technology integration, and managed security services to monitor systems and respond to threats.
Moving Forward: Setting The Direction - A Findings Review of CTEK’s 2020 Annu...

Dave Bailey presented key findings from CTEK's 2020 annual report on cybersecurity assessments. The summary is:
1) Overall, organizations showed no improvement in cybersecurity process maturity over the past 3 years, indicating a need to focus on continuous improvement rather than just achieving good assessment grades.
2) Smaller organizations and those with less than $50M in revenue tended to have lower process maturity scores across the NIST Cybersecurity Framework functions of Identify, Protect, Detect, Respond, and Recover.
3) The presentation highlighted that organizations should continue focusing on active risk management, growing their security programs, and most importantly mitigating risks, in order to improve cybersecurity maturity over time.
Why Corporate Security Professionals Should Care About Information Security 

This document discusses why corporate security professionals should care about information security. It begins by explaining how physical and logical security systems are now interconnected, meaning threats can affect physical security without a physical presence. It then gives an example of the 2016 Mirai botnet attack, which took down major websites by overloading them with traffic from compromised IoT devices. The document recommends that organizations use a risk management framework to inventory and classify assets, scan for vulnerabilities, remediate issues, and create an incident response plan. Coordination is needed between IT, security, and other teams to effectively manage cybersecurity risks.
SOC 2 Type 1 Vs. Type 2: Do You Really Need It? This Will Help You Decide! 

The prevalence of cyber security attacks and data breach in the recent years have brought to light how vulnerable organizations are to a cyber-attack. The financial losses and the tarnish of reputation caused by such attacks cannot be underestimated by any organization handling confidential data. Data breach still continues to be a pressing concern for companies across the globe. Indeed, information security has now become a major concern for organizations handling sensitive data and including those who outsource their business requirements to third-party organizations such as SaaS providers, data analytic companies and Cloud computing providers.
Needless to say, all IT managers and security stakeholders have been scrambling to find ways to tackle the situation and gain control over their network and data security. One way to ensure the security and privacy of data is by obtaining a SOC 2 Type1 & Type 2 report from a CPA. So, let us today understand in detail about the SOC 2 audit and its application to your organization.
Software Security Metrics

More often than not, company executives ask the wrong questions about software security. This session will discuss techniques for changing the conversation about software security in order to encourage executives to ask the right questions – and provide answers that show progress towards meaningful objectives. Caroline will discuss a progression of software security capabilities and the metrics that correspond to different levels of maturity. She’ll discuss an approach for developing key metrics for your unique software security program and walk through a detailed example.
Cybersecurity: Intelligence, innovation, and information warfare

This presentation discusses cybersecurity, intelligence, innovation, and information warfare. It contains forward-looking statements about future offerings and performance that are subject to risks and uncertainties. The presentation provides 10 observations about the current state of security and how to succeed in this environment. It describes how security has become a data problem and how the Elastic stack uses data analytics, visualization, and operations across Elasticsearch, Logstash, and Kibana to power security solutions. Examples are given of how Elastic solutions are used for security orchestration, automation, response, and incident response.
Applicaiton Security - Building The Audit Program

Why and How to build an Application Security Audit Program from the ISACA Chicago 2012 Boat Cruise Event
7 Lessons Learned From BSIMM

The BSIMM is a study of existing software security initiatives. By quantifying the practices of many different organizations, we can describe the common ground shared by many as well as the variation that makes each unique.
BSIMM is not a “how to” guide, nor is it a one-size-fits-all prescription. Instead, BSIMM is a reflection of software security. Here are some things we've learned and observed over the years that may help you.
ISO 27004- Information Security Metrics Implementation

ISO 27004 provides guidance and describes a set of best practices for measuring the result of ISMS in an organization. The standard specifies how to set up a measurement program, what parameters to measure, when to measure, how to measure and helps organizations to decide on how to set performance targets and success criteria.
How to measure your cybersecurity performance

This document discusses the challenges of cybersecurity benchmarking for CIOs and introduces Security Ratings as a solution. Some of the key challenges of benchmarking include: the difficulty gathering accurate metrics over time to compare performance to peers; clearly communicating benchmarking results to boards; and identifying security issues affecting competitors. Security Ratings provide an objective, quantitative method to continuously monitor an organization's cybersecurity performance and compare to others in the same industry through daily analysis of external network data, helping CIOs address these challenges.
Insight into Security Leader Success Part 2

This document provides recommendations for security leaders to create a business-focused security department that provides value to the enterprise. It discusses communicating security issues using common business terms, measuring the value of security programs through meaningful metrics, analyzing the total costs of security, developing a shared security strategy with business units, and selecting next generation security leaders with skills in business alignment, risk management, compliance, and performance measurement. The intended audience is security leaders seeking to ensure their department is valued by the business.
M4 ui a1_proyectofinal iava_pac

Este documento presenta un proyecto de capacitación para docentes sobre el uso de las TIC en la enseñanza. Actualmente, la mayoría de los docentes de la Escuela Secundaria Técnica No.91 tienen limitado conocimiento sobre TIC. El proyecto tiene el objetivo de capacitar a los docentes en el uso y aplicación de las TIC, como la webquest, para mejorar la enseñanza. El proyecto incluye talleres mensuales sobre diferentes programas y herramientas TIC a lo largo de un año escolar, con evaluaciones periódic
More Related Content
What's hot
MCGlobalTech Commercial Cybersecurity Capability Statement

Mission Critical Global Technology Group (MCGlobalTech) is an information security and IT consulting firm that provides enterprise information security management services for commercial businesses. The document discusses why businesses need a formal security program to take an organized, enterprise-wide approach to managing security risks in a proactive manner. It outlines the key components of a security program and how MCGlobalTech can help clients develop a tailored program to protect their data, systems and meet their unique security needs.
'Re-writing' Infrastructure management

An efficient, ITIL compliant, round-the-clock service desk and infrastructure management for a global insurance firm.
When a global insurance and reinsurance provider needed an experienced IT infrastructure management partner, it turned to CSS Corp. Our experience in simplifying IT Operations for complex IT environments with a wide range of technologies made CSS Corp the ideal choice for this engagement.
The prominence of it lifecycle assurance

Maveric Systems is a leading provider of assurance services across the technology lifecycle. They offer requirements assurance, application assurance, and program assurance services to help clients in banking, insurance, and telecom deliver successful digital transformation programs. Maveric's assurance-only business model brings together diverse competencies to deliver high-quality assurance solutions tailored to each client's domain.
Jeff kushner trends in grc management

Modulo is a global leader in automated GRC management solutions with over 400 employees worldwide. It has developed its product for nine years and the product provides a mature, automated platform to help organizations manage increasing complexity and risk from constant changes in regulations, policies, people, processes, and technology. Previously, most organizations took a fragmented approach to GRC management using multiple disconnected systems and mostly manual processes, which introduced greater exposure, inefficiency, and higher costs. Modulo's solution provides a common GRC metaframework architecture across applications to help organizations gain enterprise-wide visibility, consistency, and automation while relieving the burden on their business through improved compliance and lower risk.
Accenture Banking Security Index

The Accenture Security Index, based on Accenture's High Performance Security research, assesses performance across 33 cybersecurity capabilities within the Banking industry. It is intended to help banking leaders understand the effectiveness of their security measures. To learn more about Banking results, read our blog series: https://accntu.re/2vj59KC
The Future of Your Security Operations - Part 2: Tech Integration

Integrating your security operations is no longer a nice to have, it’s a must. In this presentation you’ll learn the benefits of integrating your access control, video and other alerting systems for optimal security.
Presentation by: Dan Ireland, Director – Strategic Alliances, Resolver Inc.
Rethinking compliance

This document discusses rethinking approaches to compliance to focus on business continuity beyond just security. It notes that data breaches are inevitable so compliance activities need to ensure systems can continue running when failures occur. It advocates taking a proactive approach through standards like ISO and continual disaster recovery testing to prove systems can be recovered. It also stresses designating a compliance team and accountability for continually reviewing practices.
Security metrics 

This document discusses the importance of cyber security metrics for communicating with stakeholders and seeing overall security performance. It defines key performance indicators and key risk indicators for tracking security trends. The document outlines several types of metrics for controlling cyber security risk, including metrics to measure threat level, risk level, compliance level, and number of cyber incidents. Finally, it lists some specific cyber security KPIs that are important to track, such as patching times, number of intrusion attempts, and speed of detecting and resolving security threats.
An Intro to Resolver's Incident Management Application

Interested in seeing how Resolver is tackling the future of Incident Management? What about implementing something today? Get a first look at the relaunch of Incident Management on Core. Learn how we have taken the best of Perspective to a whole new (and often simpler) level. And we’re not stopping there — learn about the incident/investigation functionality and see how it all ties together with risks that impact the security of your organization.
BizCarta-2

BizCarta provides cyber security consulting services to help companies establish comprehensive cyber security strategies and integrated cyber defense platforms. They leverage their proprietary Adept 6 consulting methodology to assess clients' security gaps and develop customized solutions. BizCarta's services include cyber security consulting, technology integration, and managed security services to monitor systems and respond to threats.
Moving Forward: Setting The Direction - A Findings Review of CTEK’s 2020 Annu...

Dave Bailey presented key findings from CTEK's 2020 annual report on cybersecurity assessments. The summary is:
1) Overall, organizations showed no improvement in cybersecurity process maturity over the past 3 years, indicating a need to focus on continuous improvement rather than just achieving good assessment grades.
2) Smaller organizations and those with less than $50M in revenue tended to have lower process maturity scores across the NIST Cybersecurity Framework functions of Identify, Protect, Detect, Respond, and Recover.
3) The presentation highlighted that organizations should continue focusing on active risk management, growing their security programs, and most importantly mitigating risks, in order to improve cybersecurity maturity over time.
Why Corporate Security Professionals Should Care About Information Security 

This document discusses why corporate security professionals should care about information security. It begins by explaining how physical and logical security systems are now interconnected, meaning threats can affect physical security without a physical presence. It then gives an example of the 2016 Mirai botnet attack, which took down major websites by overloading them with traffic from compromised IoT devices. The document recommends that organizations use a risk management framework to inventory and classify assets, scan for vulnerabilities, remediate issues, and create an incident response plan. Coordination is needed between IT, security, and other teams to effectively manage cybersecurity risks.
SOC 2 Type 1 Vs. Type 2: Do You Really Need It? This Will Help You Decide! 

The prevalence of cyber security attacks and data breach in the recent years have brought to light how vulnerable organizations are to a cyber-attack. The financial losses and the tarnish of reputation caused by such attacks cannot be underestimated by any organization handling confidential data. Data breach still continues to be a pressing concern for companies across the globe. Indeed, information security has now become a major concern for organizations handling sensitive data and including those who outsource their business requirements to third-party organizations such as SaaS providers, data analytic companies and Cloud computing providers.
Needless to say, all IT managers and security stakeholders have been scrambling to find ways to tackle the situation and gain control over their network and data security. One way to ensure the security and privacy of data is by obtaining a SOC 2 Type1 & Type 2 report from a CPA. So, let us today understand in detail about the SOC 2 audit and its application to your organization.
Software Security Metrics

More often than not, company executives ask the wrong questions about software security. This session will discuss techniques for changing the conversation about software security in order to encourage executives to ask the right questions – and provide answers that show progress towards meaningful objectives. Caroline will discuss a progression of software security capabilities and the metrics that correspond to different levels of maturity. She’ll discuss an approach for developing key metrics for your unique software security program and walk through a detailed example.
Cybersecurity: Intelligence, innovation, and information warfare

This presentation discusses cybersecurity, intelligence, innovation, and information warfare. It contains forward-looking statements about future offerings and performance that are subject to risks and uncertainties. The presentation provides 10 observations about the current state of security and how to succeed in this environment. It describes how security has become a data problem and how the Elastic stack uses data analytics, visualization, and operations across Elasticsearch, Logstash, and Kibana to power security solutions. Examples are given of how Elastic solutions are used for security orchestration, automation, response, and incident response.
Applicaiton Security - Building The Audit Program

Why and How to build an Application Security Audit Program from the ISACA Chicago 2012 Boat Cruise Event
7 Lessons Learned From BSIMM

The BSIMM is a study of existing software security initiatives. By quantifying the practices of many different organizations, we can describe the common ground shared by many as well as the variation that makes each unique.
BSIMM is not a “how to” guide, nor is it a one-size-fits-all prescription. Instead, BSIMM is a reflection of software security. Here are some things we've learned and observed over the years that may help you.
ISO 27004- Information Security Metrics Implementation

ISO 27004 provides guidance and describes a set of best practices for measuring the result of ISMS in an organization. The standard specifies how to set up a measurement program, what parameters to measure, when to measure, how to measure and helps organizations to decide on how to set performance targets and success criteria.
How to measure your cybersecurity performance

This document discusses the challenges of cybersecurity benchmarking for CIOs and introduces Security Ratings as a solution. Some of the key challenges of benchmarking include: the difficulty gathering accurate metrics over time to compare performance to peers; clearly communicating benchmarking results to boards; and identifying security issues affecting competitors. Security Ratings provide an objective, quantitative method to continuously monitor an organization's cybersecurity performance and compare to others in the same industry through daily analysis of external network data, helping CIOs address these challenges.
Insight into Security Leader Success Part 2

This document provides recommendations for security leaders to create a business-focused security department that provides value to the enterprise. It discusses communicating security issues using common business terms, measuring the value of security programs through meaningful metrics, analyzing the total costs of security, developing a shared security strategy with business units, and selecting next generation security leaders with skills in business alignment, risk management, compliance, and performance measurement. The intended audience is security leaders seeking to ensure their department is valued by the business.
What's hot (20)
MCGlobalTech Commercial Cybersecurity Capability Statement

MCGlobalTech Commercial Cybersecurity Capability Statement
The Future of Your Security Operations - Part 2: Tech Integration

The Future of Your Security Operations - Part 2: Tech Integration
An Intro to Resolver's Incident Management Application

An Intro to Resolver's Incident Management Application
Moving Forward: Setting The Direction - A Findings Review of CTEK’s 2020 Annu...

Moving Forward: Setting The Direction - A Findings Review of CTEK’s 2020 Annu...
Why Corporate Security Professionals Should Care About Information Security 

Why Corporate Security Professionals Should Care About Information Security
SOC 2 Type 1 Vs. Type 2: Do You Really Need It? This Will Help You Decide! 

SOC 2 Type 1 Vs. Type 2: Do You Really Need It? This Will Help You Decide!
Cybersecurity: Intelligence, innovation, and information warfare

Cybersecurity: Intelligence, innovation, and information warfare
ISO 27004- Information Security Metrics Implementation

ISO 27004- Information Security Metrics Implementation
Viewers also liked
M4 ui a1_proyectofinal iava_pac

Este documento presenta un proyecto de capacitación para docentes sobre el uso de las TIC en la enseñanza. Actualmente, la mayoría de los docentes de la Escuela Secundaria Técnica No.91 tienen limitado conocimiento sobre TIC. El proyecto tiene el objetivo de capacitar a los docentes en el uso y aplicación de las TIC, como la webquest, para mejorar la enseñanza. El proyecto incluye talleres mensuales sobre diferentes programas y herramientas TIC a lo largo de un año escolar, con evaluaciones periódic
03 DSD-NL 2016 - Simona Gebruikersmiddag - Floating point onnauwkeurigheid en...

03 DSD-NL 2016 - Simona Gebruikersmiddag - Floating point onnauwkeurigheid en gevoeligheid van rekenmodellen - Edwin Spee, Deltares
04 DSD-NL 2016 - Simona Gebruikersmiddag - Detailmodellen, modellering tot aa...

04 DSD-NL 2016 - Simona Gebruikersmiddag - Detailmodellen, modellering tot aan de grens (of erover) - Ron Agtersloot, Agtersloot Hydraulisch Advies
Programacion power C++

Este documento proporciona una introducción a los conceptos básicos de programación, incluyendo los tipos de datos primitivos como enteros, flotantes y caracteres, operadores aritméticos y lógicos, estructuras de control como if/else y while, y arrays. Explica los tipos de datos, operaciones, variables, estructuras de control y arrays para introducir los conceptos fundamentales de programación.
Ahmad_CV

The document summarizes the educational and professional experience of Ahmed Samir El-Sayed. He holds a B.Sc. in English-Commerce/Accounting from Mansoura University in Egypt. He has over 10 years of experience in accounting and auditing roles, including as Chief Internal Auditor, Accounting Manager, and Internal Auditor for various companies. He also has several accounting and business-related certifications. El-Sayed is seeking new opportunities that utilize his education and qualifications in accounting.
17 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Hoe goed is mijn kansverwachting ...

17 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Hoe goed is mijn kansverwachting - Jan Verkade, Deltares
BeeCon 2016 Alfresco Engineering lightning talk

A quick review of how Alfresco Engineering (the RM development team specifically) work (current as of April 2016).
2 identificação e interpretação dos riscos ocupacionais 2

Apresentação 2 - Curso de Medicina do Trabalho - Identificação e Interpretação dos Riscos Ocupacionais - Parte II
16 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Jeroen Ligtenberg, RWS-WVL & Edwi...

16 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Jeroen Ligtenberg, RWS-WVL & Edwin Snippen, Deltares
02 - DSD-NL 2016 - Geo Klantendag - Workshop funderingen voor on- en offshore...

02 - DSD-NL 2016 - Geo Klantendag - Workshop funderingen voor on- en offshore windmolens I - Lars Beuth, Deltares
Ecommerce Solution BuildaBazaar Infibeam

This document discusses e-commerce solutions from Infibeam, an India-based digital commerce company. It provides an overview of Infibeam's business platforms and services, including its B2C e-commerce marketplace Buildabazaar, loyalty and rewards program, and bring-your-own-device solutions. It also outlines key features of Buildabazaar like catalog management, promotions, payments integration, logistics, and business analytics tools. Infibeam aims to provide a full-stack digital commerce ecosystem for online retailers and merchants.
DESARROLLO SOCIAL EN LA PRIMERA INFANCIA

La familia es la institución más importante en el desarrollo de una persona. Factores como la educación, las relaciones sociales y el contexto histórico también influyen. Según Erickson, la principal crisis en la primera infancia es lograr un equilibrio entre iniciativa y culpa. Los niños resuelven el complejo de Edipo e identificándose con el padre del mismo sexo. Los procesos de socialización incluyen la adquisición de conocimientos, el desarrollo de empatía y amistades, y el control de la conducta.
Primera infancia desarrollo social

El documento describe las etapas clave del desarrollo social en los primeros 3 años de vida. En los primeros meses, los bebés comienzan a comunicarse a través de sonrisas, vocalizaciones y reconocimiento de emociones. Entre los 7-12 meses, prefieren a personas conocidas y comienzan a imitar gestos. De 1-2 años, aprenden su nombre e identidad y expresan emociones como celos. De 2-3 años, insisten en independizarse aunque aún muestran egocentrismo y se unen brevemente a otros niños para j
Kirtika_Resume

This document contains the resume of Kirtika Kavya. It includes her contact information, career objective of seeking a challenging professional career, and lists her core skills including technologies like SQL Server, ASP.Net, C#, HTML, and JavaScript. It also provides details of her over 3 years of experience in development and implementation using ASP.Net and C#. Her areas of expertise are listed as planning, development, and implementation along with experience handling a team of 7 members. Her education includes an MCA degree from IGNOU in 2011 and a BCA degree from IGNOU in 2008.
Acidente hospitalar - Enfermagem

O ambiente hospitalar apresenta diversos riscos à saúde dos profissionais, como riscos biológicos, químicos, físicos e ergonômicos. Acidentes são comuns, especialmente cortes de agulhas. Equipamentos de proteção individual e treinamento contínuo são essenciais para prevenir acidentes e doenças ocupacionais.
Plan de protección las seis jugadas maestras 

Ante la amenaza de un terremoto, las instituciones educativas y la comunidad en general, deben tener siempre presente la estrategia de las seis jugadas maestras que nos permiten prepararnos para responder a este posible evento
Viewers also liked (18)
03 DSD-NL 2016 - Simona Gebruikersmiddag - Floating point onnauwkeurigheid en...

03 DSD-NL 2016 - Simona Gebruikersmiddag - Floating point onnauwkeurigheid en...
04 DSD-NL 2016 - Simona Gebruikersmiddag - Detailmodellen, modellering tot aa...

04 DSD-NL 2016 - Simona Gebruikersmiddag - Detailmodellen, modellering tot aa...
17 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Hoe goed is mijn kansverwachting ...

17 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Hoe goed is mijn kansverwachting ...
2 identificação e interpretação dos riscos ocupacionais 2

2 identificação e interpretação dos riscos ocupacionais 2
16 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Jeroen Ligtenberg, RWS-WVL & Edwi...

16 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Jeroen Ligtenberg, RWS-WVL & Edwi...
02 - DSD-NL 2016 - Geo Klantendag - Workshop funderingen voor on- en offshore...

02 - DSD-NL 2016 - Geo Klantendag - Workshop funderingen voor on- en offshore...
Similar to S sdlc datasheet q1-2015 v fnl
Cyber risk management-white-paper-v8 (2) 2015

This document discusses a holistic approach to cyber risk management. It recommends conducting regular vulnerability assessments to understand risks and identify security gaps. Once vulnerabilities are found, assets should be protected according to the organization's risk tolerance by implementing security measures like access control and user training. Continuous monitoring is also important since threats change over time. The holistic approach involves people, processes, and technology, not just technology alone.
Small Business Playbook for Security and Compliance Success.pdf

Small Business Playbook for Security and Compliance Success.pdf
Small Business Playbook for Security and Compliance Success.pptx

Small Business Playbook for Security and Compliance Success.pptx
Meraj Ahmad - Information security in a borderless world

The document discusses information security challenges in today's borderless world of increased mobile and cloud computing use. It notes that while organizations recognize new risks from these technologies, many are not adjusting policies or security awareness accordingly. The presentation recommends that organizations establish comprehensive risk management programs, conduct risk assessments, take an information-centric view of security, and increase security controls, awareness and outsourcing to address risks from mobile, cloud and social media use. It also provides a framework to transform security programs to better protect important data and enable business needs.
MCGlobalTech Service Presentation

Mission Critical Global Technology Group (MCGlobalTech) provides information security and IT infrastructure management consulting services. They help organizations comply with industry standards and federal regulations to strengthen their security posture. MCGlobalTech assesses clients' security gaps and develops customized solutions involving governance, processes, and technology controls. Their full lifecycle of services includes assessment, planning, implementation, and continuous monitoring.
Lead Through Disruption Guide PDF

The document discusses strategies for organizations to lead through disruption by managing cyber and business risk with confidence. It outlines 12 key objectives including protecting devices and operations through security, building trust with customers and data use, managing multifaceted risk through dynamic programs, and providing vision for growth. Each objective is described in more detail with considerations around stakes, needs, and potential outcomes.
Security of the future - Adapting Approaches to What We Need

The document discusses how security approaches need to adapt to new digital disruptors. It argues that traditional security governance is not adequate for fast-paced business models and can inhibit innovation. A new security mindset is needed that focuses on breach acceptance, resiliency, and securing data rather than trust. It also recommends decentralizing security ownership across teams, incorporating security earlier in the software development lifecycle through DevSecOps strategies, and instilling a security culture to drive key business objectives.
Power your businesswith risk informed decisions

Enterprises face increasing risks
Every day, modern enterprises face significant risk concerns. Consider the potential
impact of business disruption, technology breaches, and workforce safety issues, as
well as disconnected tools/systems/processes, productivity issues, and brand and
reputation damage. Other risks are ones that can’t be controlled as easily, including
extreme weather, the ever-growing cost associated with the number of global
compliance regulations, supply chain disruption—and global pandemics. This last one
previously didn’t seem that likely, but we’ve all experienced how that can change.
These concerns are present for every department across the enterprise. They impact
how people work and the business’s bottom line.
Governance, Risk, and Compliance (GRC) programs help ensure that enterprises
address risks and meet compliance mandates. Today, these programs are even
more critical as enterprises around the world embrace digital transformation and
cloud-based platforms. Such innovations enable workforces and customers to easily
access digital services and processes, but these seamless experiences also bring
increased risks.
Outdated GRC practices and solutions
Many existing GRC solutions were developed and implemented before the largescale adoption of digital technology. These outdated solutions were not designed for
front-line employees, and they place a heavy burden on risk and compliance teams.
Neither the tools nor the teams can keep up. Right now, typically every department
in an enterprise has silos of data that these solutions must attempt to work with or
around. Compliance teams are forced to use manual, outdated, and inconsistent risk
management and compliance practices that don’t provide a real-time, overall view of
risk across the business
IT Guide for Mobility: Making the case for Security leaders

Learn how to make the case to Security Leaders around mobility. Get Started: www.cisco.com/go/mobility
Software Development

Do you want to learn how to make a strong presentation? You must enrol in a Micro Wave Computer Institute's Best MS PowerPoint Course in Khanna. With the Best MS PowerPoint Course in Khanna, we offer high-quality instruction while showing students how to create presentations for both personal and professional usage by including animations, graphics, videos, sound effects, etc.
Strategic Insights on IT & Cyber Risk Assessments.pdf

In today’s organizations, IT risk assessments are crucial for effective cybersecurity and information security risk management.
Solution Spotlight IT Consulting Services

IT Services through a Managed Service Provider provides the opportunity to develop your business strategy through technology. There are so many different solutions to chose from that can help take your business to the next level.
DEPL Consulting Brochure

DEPL Consulting is an IT audit and advisory firm based in Lagos Nigeria. We provide a high-quality information technology consulting services that cut across governance and risk management, cybersecurity, compliance program, audit and assurance services.
Building a business case for expanding your AppSec Program

This guide will help you develop a strong business case that can drive real-world results.
We’ll explain how to frame budget issues, identify key metrics, and use customer sentiment to
your advantage, all so you can get the funding you need to create a more mature AppSec program.
Cyber Defence - Service portfolio

An effective cybersecurity program starts with a risk-based strategy and framework focused on protecting client and organizational information. Risk frameworks can help businesses design, measure, and monitor goals to improve cybersecurity. While employees remain a top source of attacks, incidents from business partners are also increasing. Outsourcing cybersecurity professional services can help reduce costs, ensure regulatory compliance, and provide expertise that organizations may lack. Services include designing security frameworks, auditing controls, and developing policies to protect assets, detect incidents, and recover operations.
MCGlobalTech Consulting Service Presentation

MCGlobalTech Consulting Service helps government and business leaders effectively and efficiently manage their security and technology.
New technologies - Amer Haza'a

The document discusses strategic approaches for information security in 2018, focusing on continuous adaptive risk and trust assessment (CARTA). It recommends adopting a CARTA strategic approach to securely enable access to digital business initiatives in an increasingly complex threat environment. The document outlines key challenges in adapting existing security approaches to new digital business realities and recommends embracing principles of trust and resilience, developing an adaptive security architecture, and implementing a formal risk and security management program.
Top 6 Web Application Security Best Practices.pdf

Want to know how to secure your web apps from cyber-attacks? Looking to know the Best Web Application Security Best Practices? Check this article, we delve into six essential web application security best practices that are important for safeguarding your web applications and preserving the sanctity of your valuable data.
Building Success from Scratch Custom Web Application Development Strategies.pdf

Successful custom web application development begins with meticulous planning and a comprehensive analysis of requirements. This phase involves close collaboration between developers and stakeholders to outline project objectives, functionality, and user expectations. By identifying potential challenges and opportunities early on, businesses can lay the foundation for a successful development process.
7 Steps To Developing A Cloud Security Plan

The document outlines a 7-step process for developing a cloud security plan. The steps are: 1) Review business goals; 2) Maintain a risk management program; 3) Create a security plan that supports business goals; 4) Establish corporate-wide support; 5) Create security policies, procedures, and standards; 6) Audit and review often; 7) Continuously improve. Following these steps will help organizations develop effective security plans to take advantage of cloud services while meeting security and compliance needs.
Similar to S sdlc datasheet q1-2015 v fnl (20)
Small Business Playbook for Security and Compliance Success.pdf

Small Business Playbook for Security and Compliance Success.pdf
Small Business Playbook for Security and Compliance Success.pptx

Small Business Playbook for Security and Compliance Success.pptx
Meraj Ahmad - Information security in a borderless world

Meraj Ahmad - Information security in a borderless world
Security of the future - Adapting Approaches to What We Need

Security of the future - Adapting Approaches to What We Need
IT Guide for Mobility: Making the case for Security leaders

IT Guide for Mobility: Making the case for Security leaders
Strategic Insights on IT & Cyber Risk Assessments.pdf

Strategic Insights on IT & Cyber Risk Assessments.pdf
Building a business case for expanding your AppSec Program

Building a business case for expanding your AppSec Program
Building Success from Scratch Custom Web Application Development Strategies.pdf

Building Success from Scratch Custom Web Application Development Strategies.pdf
Recently uploaded
Income Tax exemption for Start up : Section 80 IAC

A presentation on the concept of Exemption of Profits of Start ups from Income Tax
Easily Verify Compliance and Security with Binance KYC

Use our simple KYC verification guide to make sure your Binance account is safe and compliant. Discover the fundamentals, appreciate the significance of KYC, and trade on one of the biggest cryptocurrency exchanges with confidence.
Industrial Tech SW: Category Renewal and Creation

Every industrial revolution has created a new set of categories and a new set of players.
Multiple new technologies have emerged, but Samsara and C3.ai are only two companies which have gone public so far.
Manufacturing startups constitute the largest pipeline share of unicorns and IPO candidates in the SF Bay Area, and software startups dominate in Germany.
Zodiac Signs and Food Preferences_ What Your Sign Says About Your Taste

Know what your zodiac sign says about your taste in food! Explore how the 12 zodiac signs influence your culinary preferences with insights from MyPandit. Dive into astrology and flavors!
Unveiling the Dynamic Personalities, Key Dates, and Horoscope Insights: Gemin...

Explore the fascinating world of the Gemini Zodiac Sign. Discover the unique personality traits, key dates, and horoscope insights of Gemini individuals. Learn how their sociable, communicative nature and boundless curiosity make them the dynamic explorers of the zodiac. Dive into the duality of the Gemini sign and understand their intellectual and adventurous spirit.
Creative Web Design Company in Singapore

At Techbox Square, in Singapore, we're not just creative web designers and developers, we're the driving force behind your brand identity. Contact us today.
How MJ Global Leads the Packaging Industry.pdf

MJ Global's success in staying ahead of the curve in the packaging industry is a testament to its dedication to innovation, sustainability, and customer-centricity. By embracing technological advancements, leading in eco-friendly solutions, collaborating with industry leaders, and adapting to evolving consumer preferences, MJ Global continues to set new standards in the packaging sector.
Dpboss Matka Guessing Satta Matta Matka Kalyan Chart Satta Matka

Dpboss Matka Guessing Satta Matta Matka Kalyan Chart Satta Matka➒➌➎➏➑➐➋➑➐➐Dpboss Matka Guessing Satta Matka Kalyan Chart Indian Matka
Dpboss Matka Guessing Satta Matta Matka Kalyan Chart Indian Matka Indian satta Matka Dpboss Matka Kalyan Chart Matka Boss otg matka Guessing Satta -- June 2024 is National Volunteer Month --

Check out our June display of books on voluntary organisations
Event Report - SAP Sapphire 2024 Orlando - lots of innovation and old challenges

Holger Mueller of Constellation Research shares his key takeaways from SAP's Sapphire confernece, held in Orlando, June 3rd till 5th 2024, in the Orange Convention Center.
The 10 Most Influential Leaders Guiding Corporate Evolution, 2024.pdf

In the recent edition, The 10 Most Influential Leaders Guiding Corporate Evolution, 2024, The Silicon Leaders magazine gladly features Dejan Štancer, President of the Global Chamber of Business Leaders (GCBL), along with other leaders.
Company Valuation webinar series - Tuesday, 4 June 2024

This session provided an update as to the latest valuation data in the UK and then delved into a discussion on the upcoming election and the impacts on valuation. We finished, as always with a Q&A
Anny Serafina Love - Letter of Recommendation by Kellen Harkins, MS.

This letter, written by Kellen Harkins, Course Director at Full Sail University, commends Anny Love's exemplary performance in the Video Sharing Platforms class. It highlights her dedication, willingness to challenge herself, and exceptional skills in production, editing, and marketing across various video platforms like YouTube, TikTok, and Instagram.
Best Forex Brokers Comparison in INDIA 2024

Navigating the world of forex trading can be challenging, especially for beginners. To help you make an informed decision, we have comprehensively compared the best forex brokers in India for 2024. This article, reviewed by Top Forex Brokers Review, will cover featured award winners, the best forex brokers, featured offers, the best copy trading platforms, the best forex brokers for beginners, the best MetaTrader brokers, and recently updated reviews. We will focus on FP Markets, Black Bull, EightCap, IC Markets, and Octa.
Organizational Change Leadership Agile Tour Geneve 2024

Organizational Change Leadership at Agile Tour Geneve 2024
How are Lilac French Bulldogs Beauty Charming the World and Capturing Hearts....

“After being the most listed dog breed in the United States for 31
years in a row, the Labrador Retriever has dropped to second place
in the American Kennel Club's annual survey of the country's most
popular canines. The French Bulldog is the new top dog in the
United States as of 2022. The stylish puppy has ascended the
rankings in rapid time despite having health concerns and limited
color choices.”
Business storytelling: key ingredients to a story

Storytelling is an incredibly valuable tool to share data and information. To get the most impact from stories there are a number of key ingredients. These are based on science and human nature. Using these elements in a story you can deliver information impactfully, ensure action and drive change.
Creative Web Design Company in Singapore

At Techbox Square, in Singapore, we're not just creative web designers and developers, we're the driving force behind your brand identity. Contact us today.
2022 Vintage Roman Numerals Men Rings

Discover timeless style with the 2022 Vintage Roman Numerals Men's Ring. Crafted from premium stainless steel, this 6mm wide ring embodies elegance and durability. Perfect as a gift, it seamlessly blends classic Roman numeral detailing with modern sophistication, making it an ideal accessory for any occasion.
https://rb.gy/usj1a2
Recently uploaded (20)
Income Tax exemption for Start up : Section 80 IAC

Income Tax exemption for Start up : Section 80 IAC
Easily Verify Compliance and Security with Binance KYC

Easily Verify Compliance and Security with Binance KYC
Zodiac Signs and Food Preferences_ What Your Sign Says About Your Taste

Zodiac Signs and Food Preferences_ What Your Sign Says About Your Taste
Unveiling the Dynamic Personalities, Key Dates, and Horoscope Insights: Gemin...

Unveiling the Dynamic Personalities, Key Dates, and Horoscope Insights: Gemin...
Dpboss Matka Guessing Satta Matta Matka Kalyan Chart Satta Matka

Dpboss Matka Guessing Satta Matta Matka Kalyan Chart Satta Matka
Event Report - SAP Sapphire 2024 Orlando - lots of innovation and old challenges

Event Report - SAP Sapphire 2024 Orlando - lots of innovation and old challenges
The 10 Most Influential Leaders Guiding Corporate Evolution, 2024.pdf

The 10 Most Influential Leaders Guiding Corporate Evolution, 2024.pdf
Company Valuation webinar series - Tuesday, 4 June 2024

Company Valuation webinar series - Tuesday, 4 June 2024
Anny Serafina Love - Letter of Recommendation by Kellen Harkins, MS.

Anny Serafina Love - Letter of Recommendation by Kellen Harkins, MS.
Organizational Change Leadership Agile Tour Geneve 2024

Organizational Change Leadership Agile Tour Geneve 2024
How are Lilac French Bulldogs Beauty Charming the World and Capturing Hearts....

How are Lilac French Bulldogs Beauty Charming the World and Capturing Hearts....
S sdlc datasheet q1-2015 v fnl
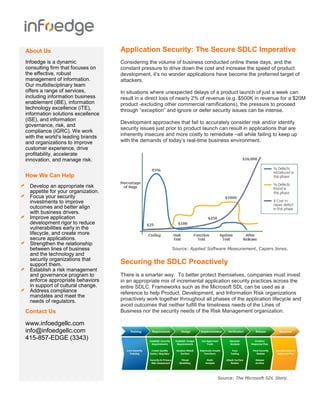
- 1. Application Security: The Secure SDLC Imperative Considering the volume of business conducted online these days, and the constant pressure to drive down the cost and increase the speed of product development, it’s no wonder applications have become the preferred target of attackers. In situations where unexpected delays of a product launch of just a week can result in a direct loss of nearly 2% of revenue (e.g. $500K in revenue for a $20M product -excluding other commercial ramifications), the pressure to proceed through “exception” and ignore or defer security issues can be intense. Development approaches that fail to accurately consider risk and/or identify security issues just prior to product launch can result in applications that are inherently insecure and more costly to remediate –all while failing to keep up with the demands of today’s real-time business environment. Securing the SDLC Proactively There is a smarter way. To better protect themselves, companies must invest in an appropriate mix of incremental application security practices across the entire SDLC. Frameworks such as the Microsoft SDL can be used as a reference to help Product, Development, and Information Risk organizations proactively work together throughout all phases of the application lifecycle and avoid outcomes that neither fulfill the timeliness needs of the Lines of Business nor the security needs of the Risk Management organization. ` About Us Infoedge is a dynamic consulting firm that focuses on the effective, robust management of information. Our multidisciplinary team offers a range of services, including information business enablement (iBE), information technology excellence (iTE), information solutions excellence (iSE), and information governance, risk, and compliance (iGRC). We work with the world’s leading brands and organizations to improve customer experience, drive profitability, accelerate innovation, and manage risk. How We Can Help Develop an appropriate risk appetite for your organization. Focus your security investments to improve outcomes and better align with business drivers. Improve application development rigor to reduce vulnerabilities early in the lifecycle, and create more secure applications. Strengthen the relationship between lines of business and the technology and security organizations that support them. Establish a risk management and governance program to enforce appropriate behaviors in support of cultural change. Address compliance mandates and meet the needs of regulators. Contact Us www.infoedgellc.com info@infoedgellc.com 415-857-EDGE (3343) Source: Applied Software Measurement, Capers Jones. Source: The Microsoft SDL Story.
- 2. Secure Software Development Lifecycle (S-SDLC) Services We understand that different organizations have different requirements and our Secure Software Development Lifecycle approach works for companies at every level of maturity. The S-SDLC service mix delivers a unique set of capabilities to fit each client’s specific security needs and investment appetite. There are four complimentary service offerings that support our approach: Assessment—We work with our clients to thoroughly understand their existing capabilities across the S-SDLC, and then identify opportunities for focused improvement and capability development. Advisory—Using our extensive industry and domain knowledge, we help clients develop practices and apply the most up-to-date S-SDLC thinking across the areas of people, process, and technology. Operationalization—We help our clients implement their S- SDLC strategy using actionable and sustainable program initiatives, coupled with automation activities that ease the developer burden and drive lasting cultural change. Assurance—We help identify impactful business metrics and governance processes that demonstrate the program’s value, and ensure the level of risk management is aligned with the needs of the organization. Examples of Our S-SDLC Services in Action S-SDLC Maturity Assessment S-SDLC Advisory and Operationalization S-SDLC Assessment and Advisory CLIENT CONCERN: Repeated delays in the launch of new products due to late detection of security issues that had to be fixed prior to launch. CLIENT CONCERN: A serious application security bug was released into production without detection, resulting in a potential breach of confidentiality. CLIENT CONCERN: Regulators required additional confidence that the client had taken the right approach to securing applications. OUR SOLUTION: Assessed the service environment and developed new strategies aimed at early notification. Worked with client personnel to implement new services and drive awareness of new touch points and capabilities. OUR SOLUTION: Performed root cause analysis and identified the service gap. Developed capability integration service models and strategy for more effective partnering. Worked with client to implement solution. OUR SOLUTION: Worked with client to develop a multi-year S-SDLC roadmap. Developed and led the implementation of several services across a variety of development approaches (e.g. Agile & Waterfall) and third- party support structures. CLIENT IMPACT: Improved client’s relationship with peers and partners. Reduced the number of last- minute findings and therefore the extent of delays. CLIENT IMPACT: Avoided significant costs and risks by enhancing existing capabilities and integrating new ones. CLIENT IMPACT: Avoided regulatory action, and jump-started an enterprise-wide security transformation across all phases of the application lifecycle.
