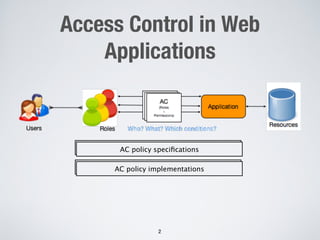
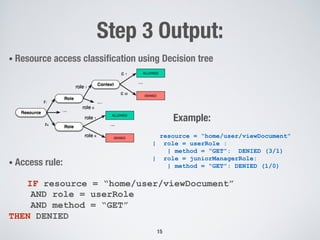
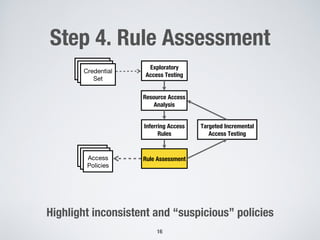
This document proposes an approach to automatically infer access control policies for web applications through dynamic analysis and machine learning. The approach involves exploring the application to discover resources, analyzing resource access data, inferring access rules using decision trees, assessing rule consistency, and targeted testing. An evaluation on two applications found the approach was effective in discovering resources and inferring correct policies for one application. Inconsistencies in the inferred rules also helped detect some access control issues in the applications.