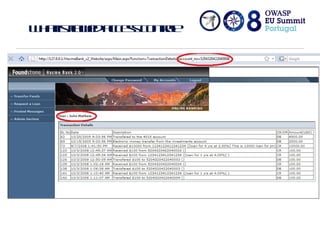
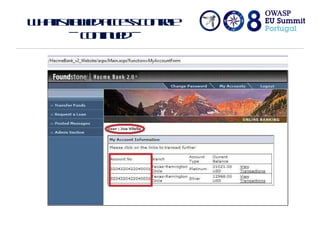
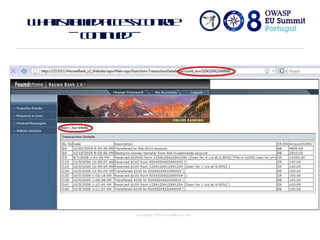
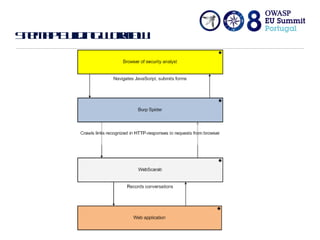
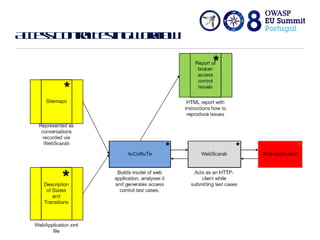
The document discusses flawed access control in web applications and presents the Accorute tool designed to detect inconsistencies in access control rules. It describes the model of web applications as state transition systems and outlines the testing methodology, including a formal model, algorithm, and command line tool for access control assessment. The document also highlights the tools' features, limitations, and future work aimed at enhancing the tool's capabilities.
![Access Control Rules Tester Andrew Petukhov Department of Computer Science Moscow State University [email_address]](https://image.slidesharecdn.com/owaspeusummit2008accorute-110202120025-phpapp01/75/Access-Control-Rules-Tester-1-2048.jpg)