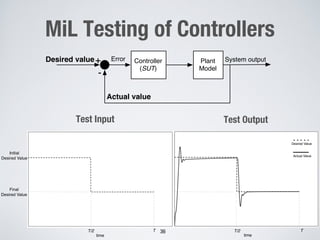
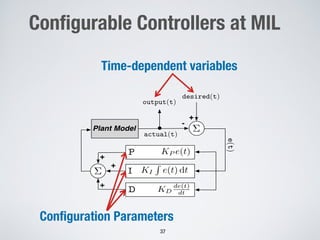
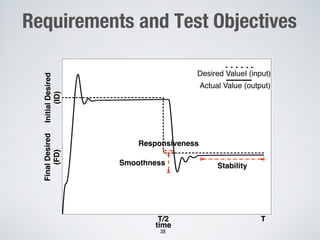
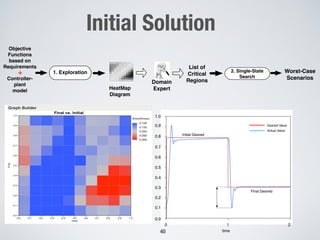
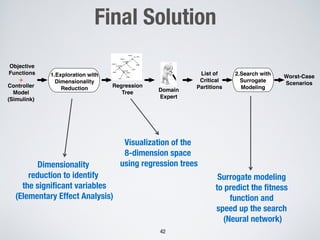
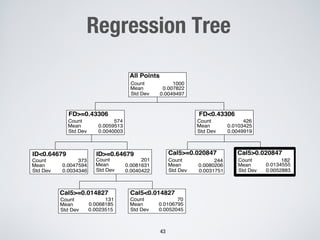
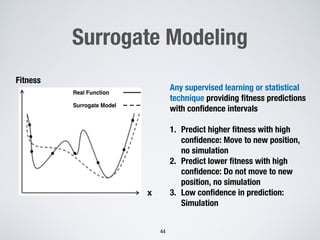
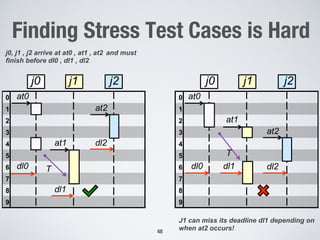
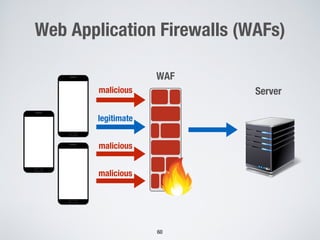
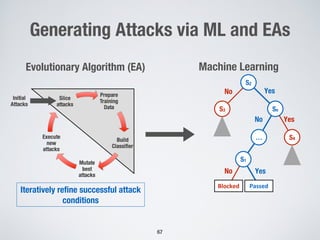
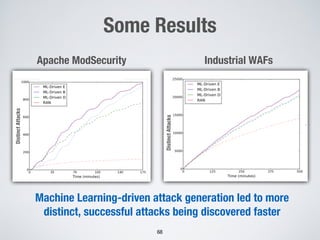
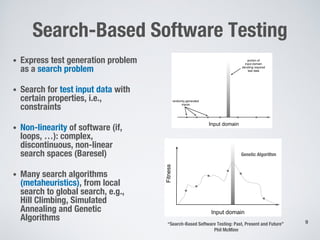
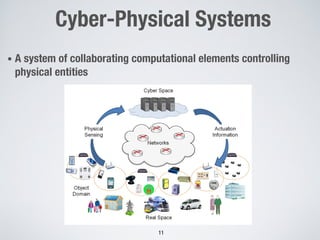
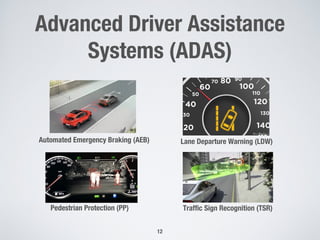
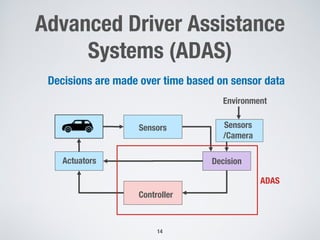
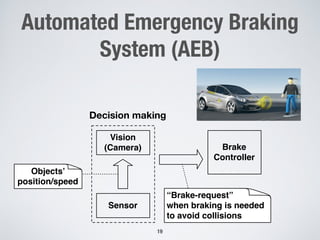
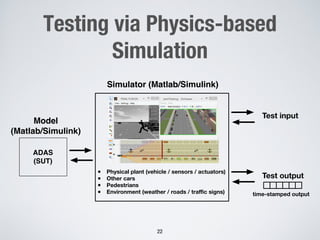
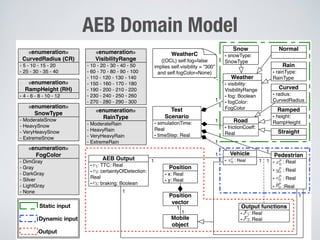
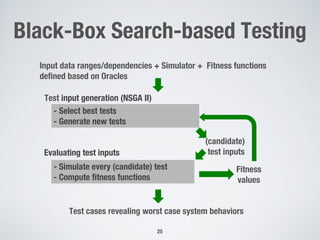
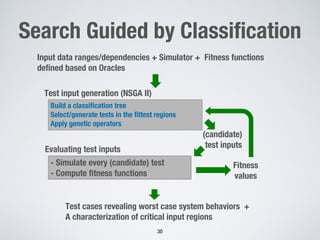
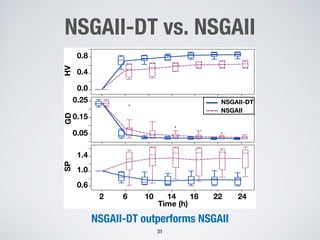
This document discusses challenges in testing advanced driver assistance systems (ADAS) and approaches to address scalability. It describes using physics-based simulation and search-based testing to generate test cases for an automated emergency braking system. The testing faces challenges due to the large, complex input space and computational expense of simulations. Decision trees are proposed to better guide the search by partitioning the input space into homogeneous regions based on criticality.






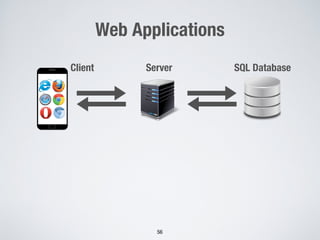
![Software Testing
8
SW Representation
(e.g., specifications)
SW Code
Derive Test cases
Execute Test cases
Compare
Expected
Results or properties
Get Test Results
Test Oracle
[Test Result==Oracle][Test Result!=Oracle]
Automation!](https://image.slidesharecdn.com/raise2018-180609162249/85/Achieving-Scalability-in-Software-Testing-with-Machine-Learning-and-Metaheuristic-Search-8-320.jpg)








)
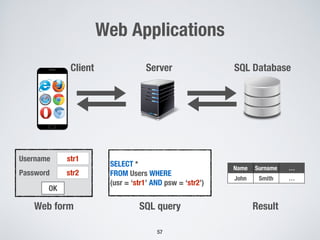
RoadTopology
(CR = [10 40](m))
“non-critical” 31%
“critical” 69%
“non-critical” 72%
“critical” 28%](https://image.slidesharecdn.com/raise2018-180609162249/85/Achieving-Scalability-in-Software-Testing-with-Machine-Learning-and-Metaheuristic-Search-28-320.jpg)


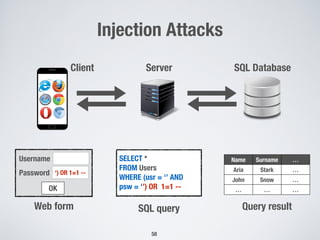
![• Supercharger bypass flap controller
üFlap position is bounded within
[0..1]
üImplemented in MATLAB/Simulink
ü34 (sub-)blocks decomposed into 6
abstraction levels
Supercharger
Bypass Flap
Supercharger
Bypass Flap
Flap position = 0 (open) Flap position = 1 (closed)
Simple Example
35](https://image.slidesharecdn.com/raise2018-180609162249/85/Achieving-Scalability-in-Software-Testing-with-Machine-Learning-and-Metaheuristic-Search-35-320.jpg)