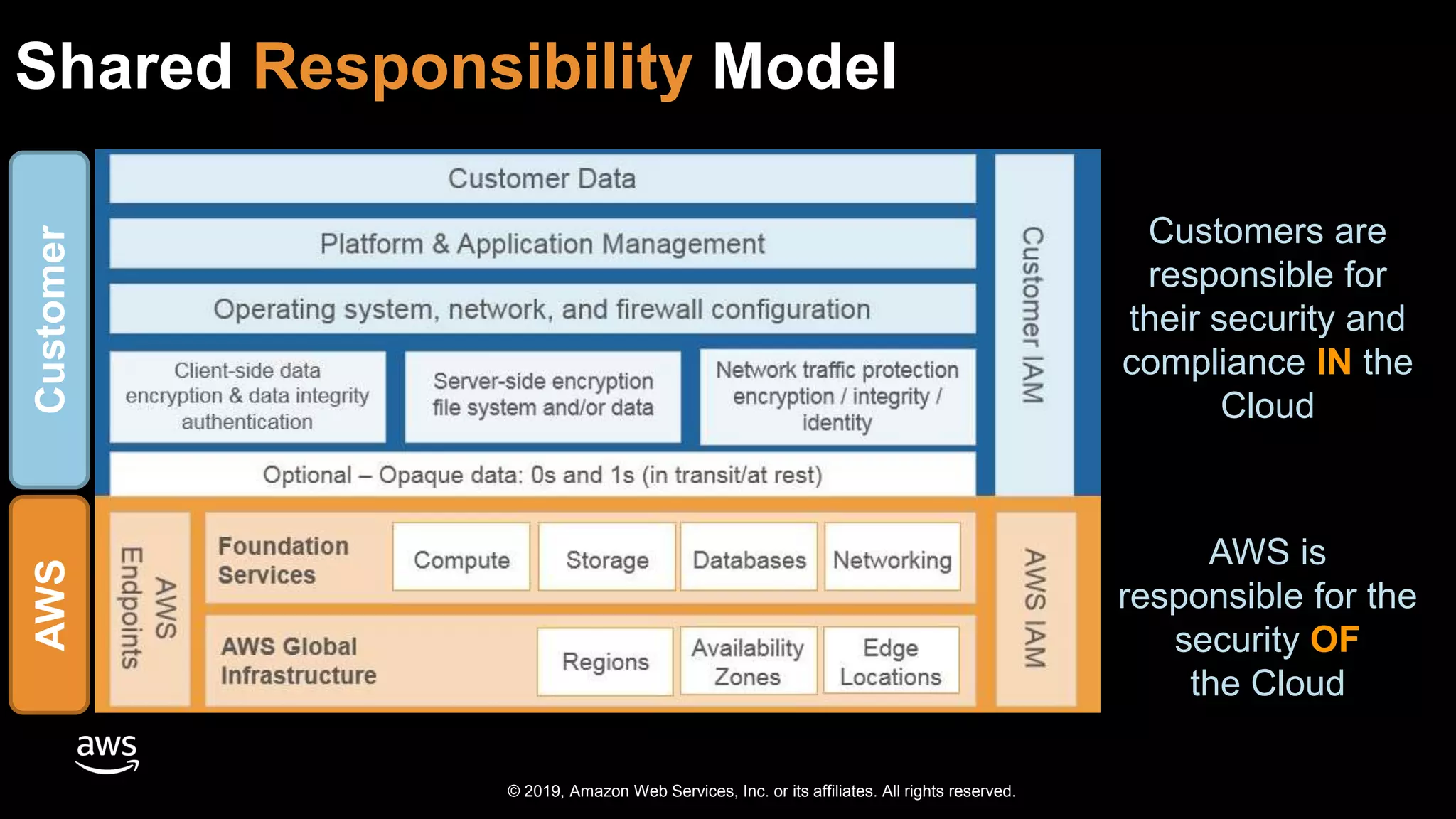
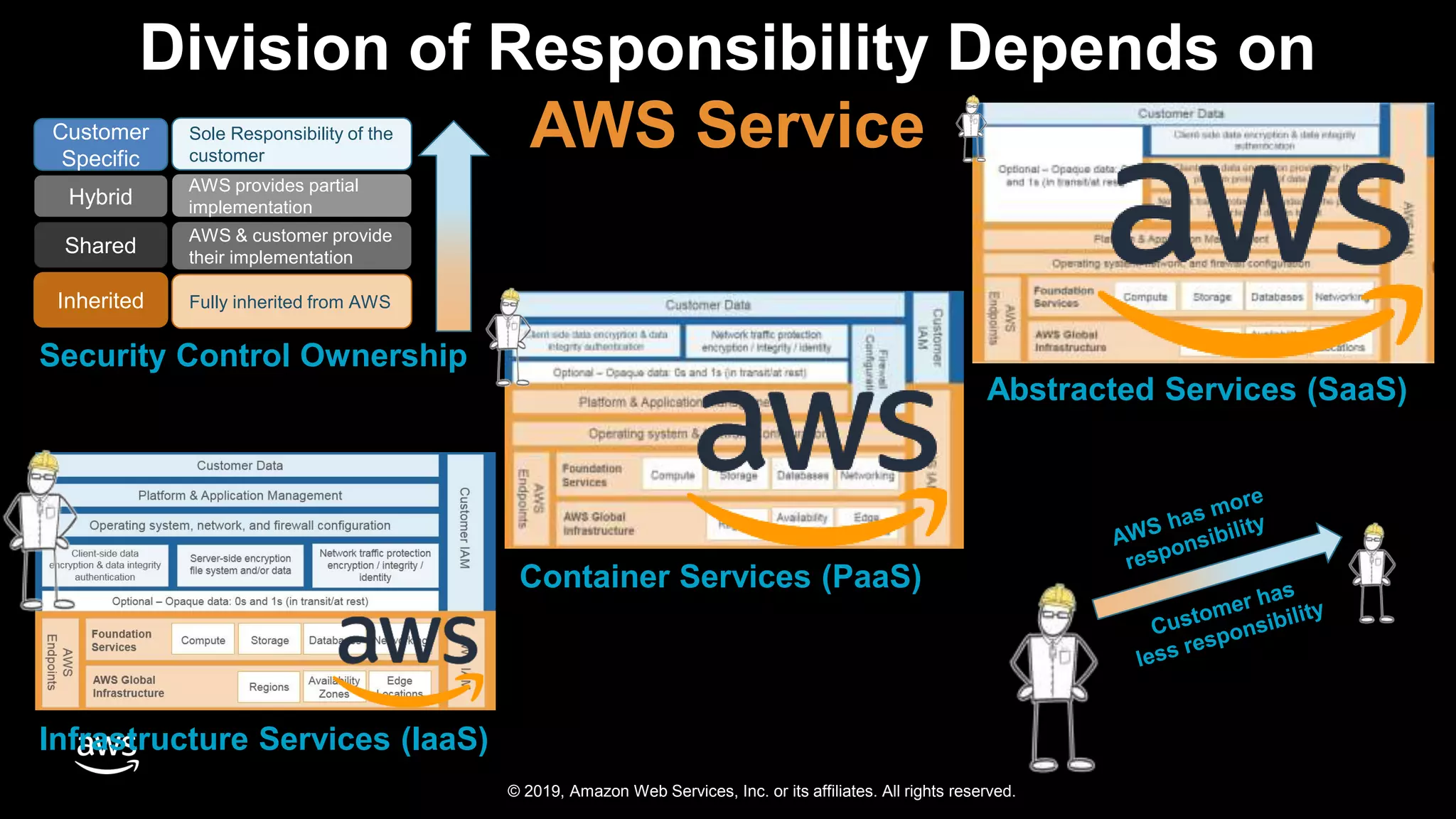
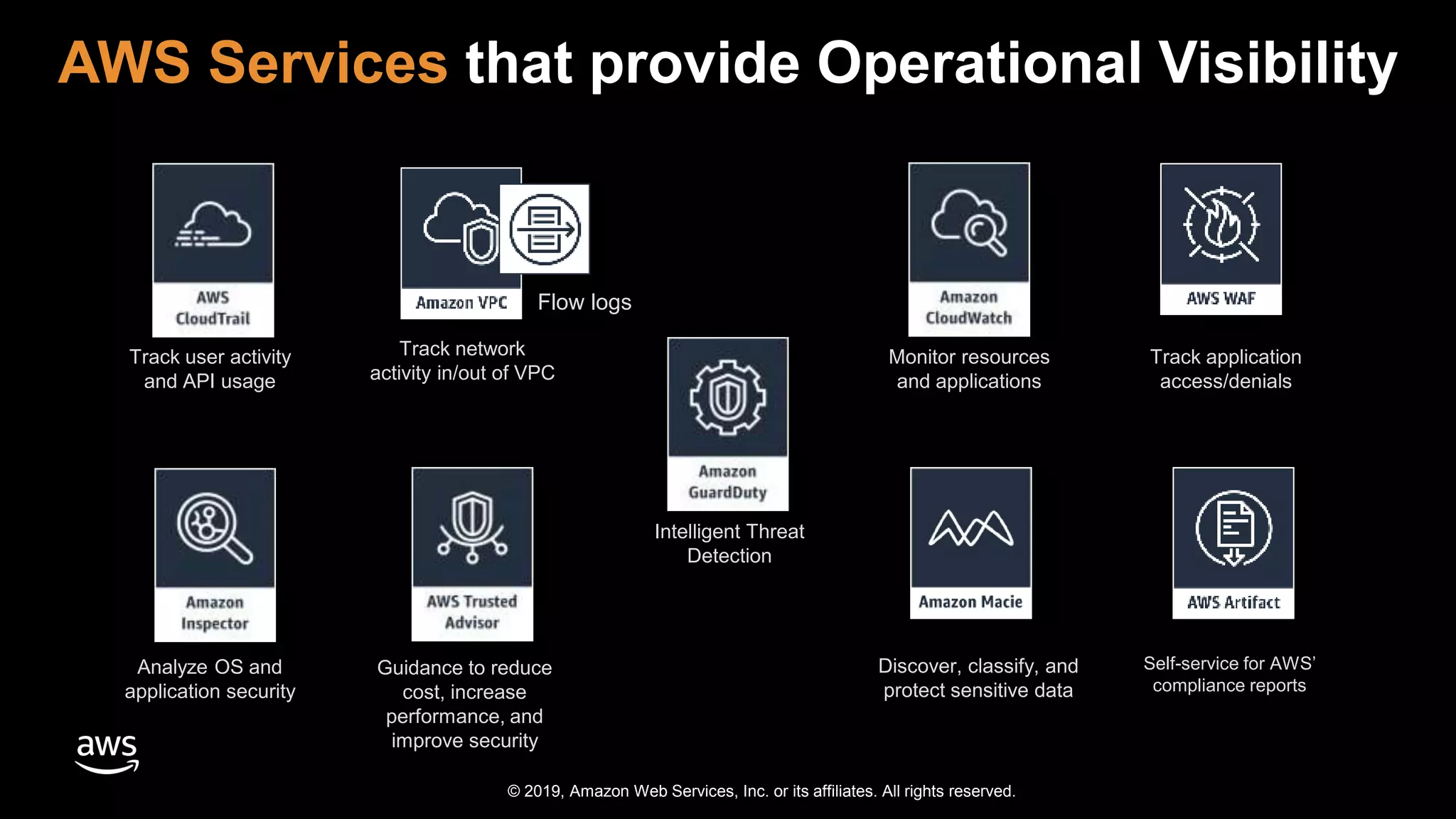
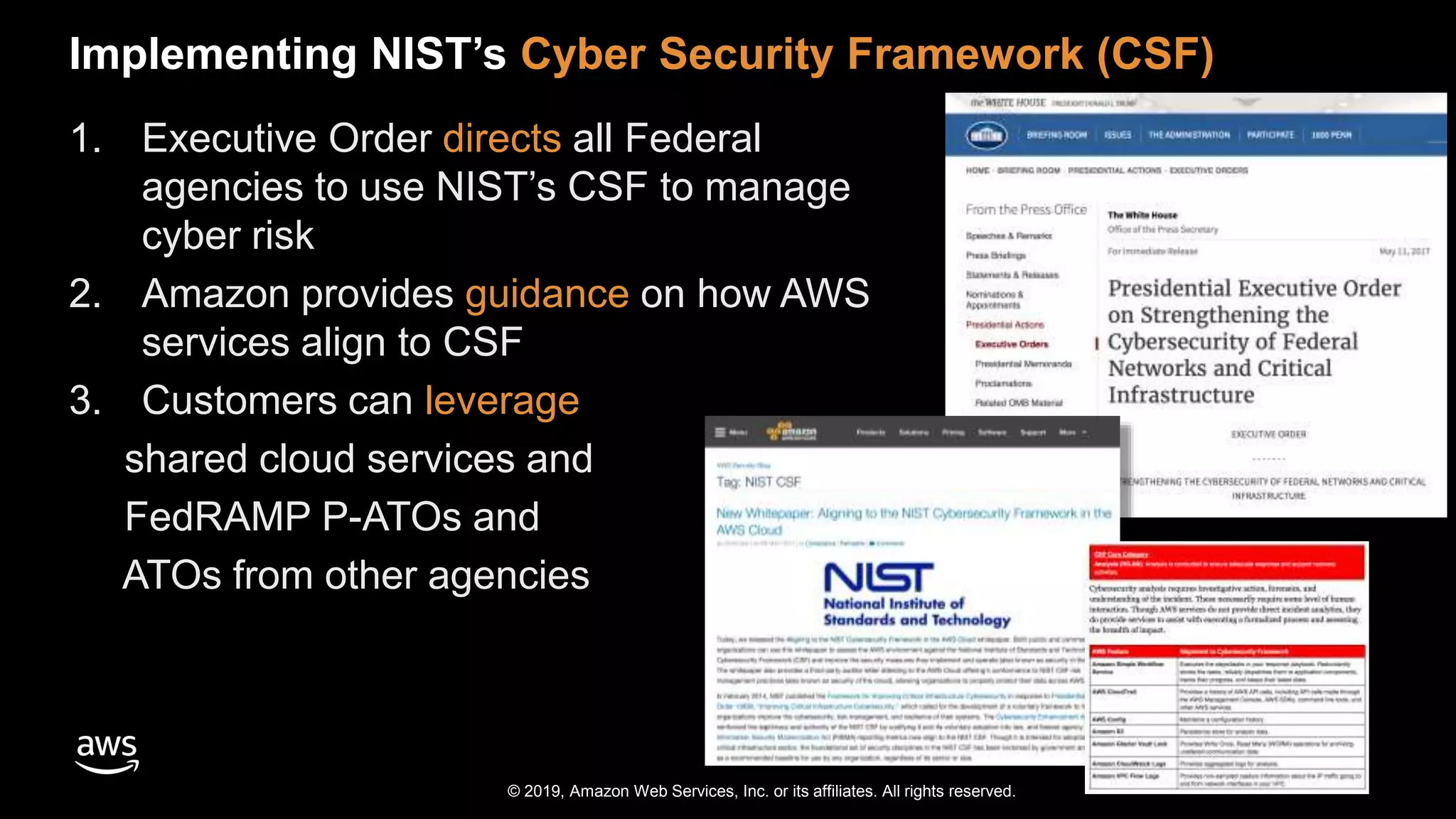
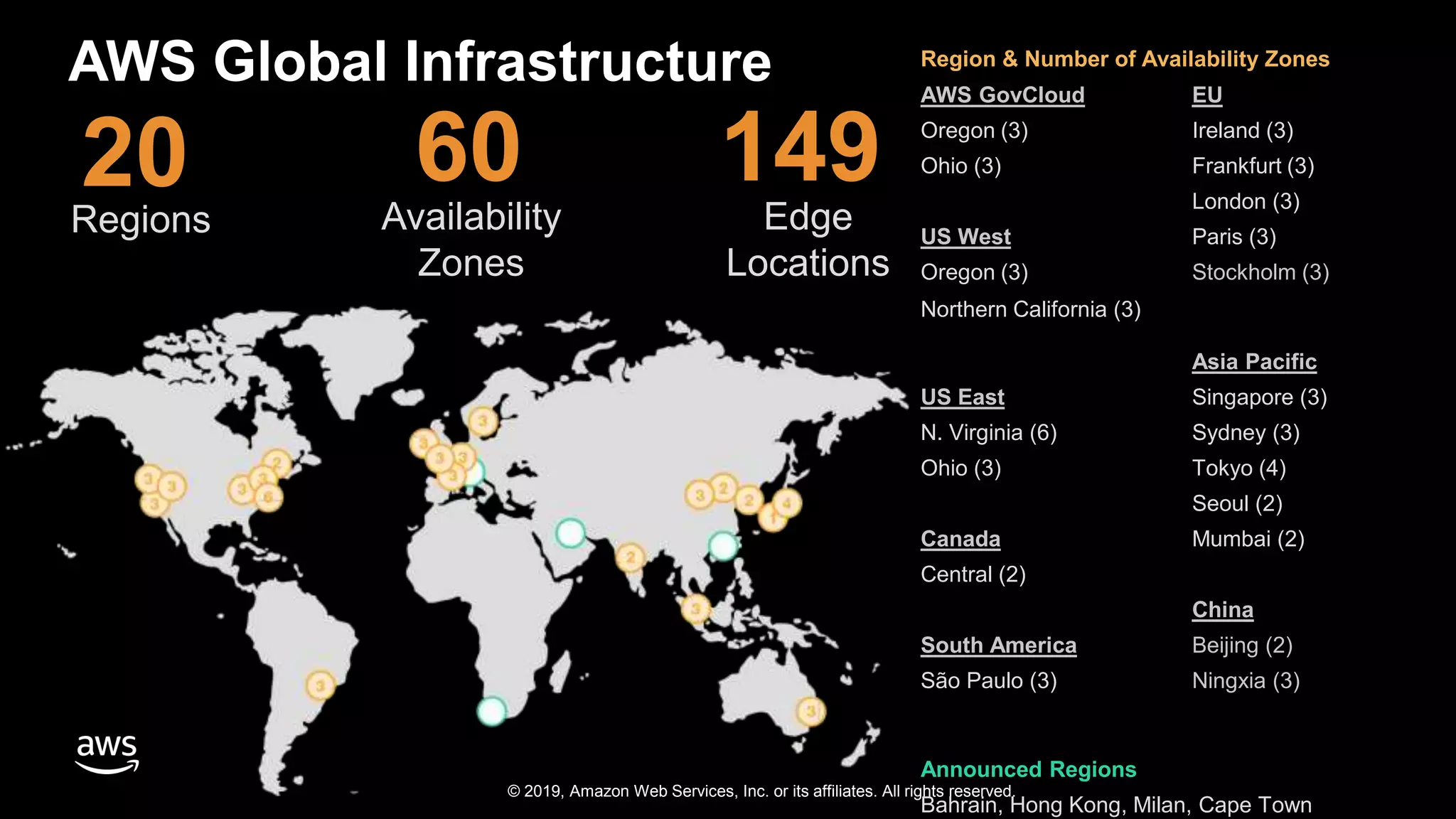
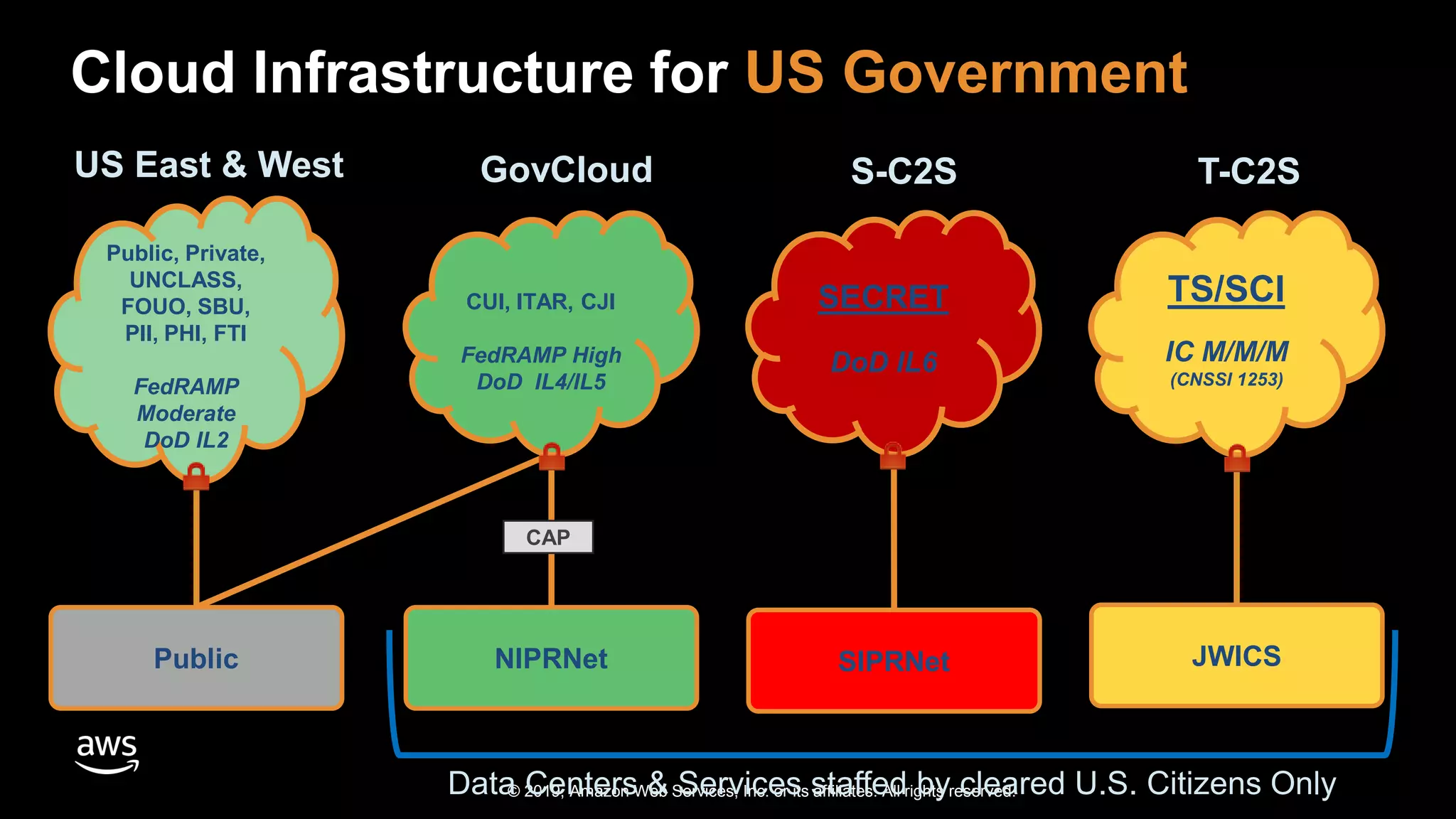
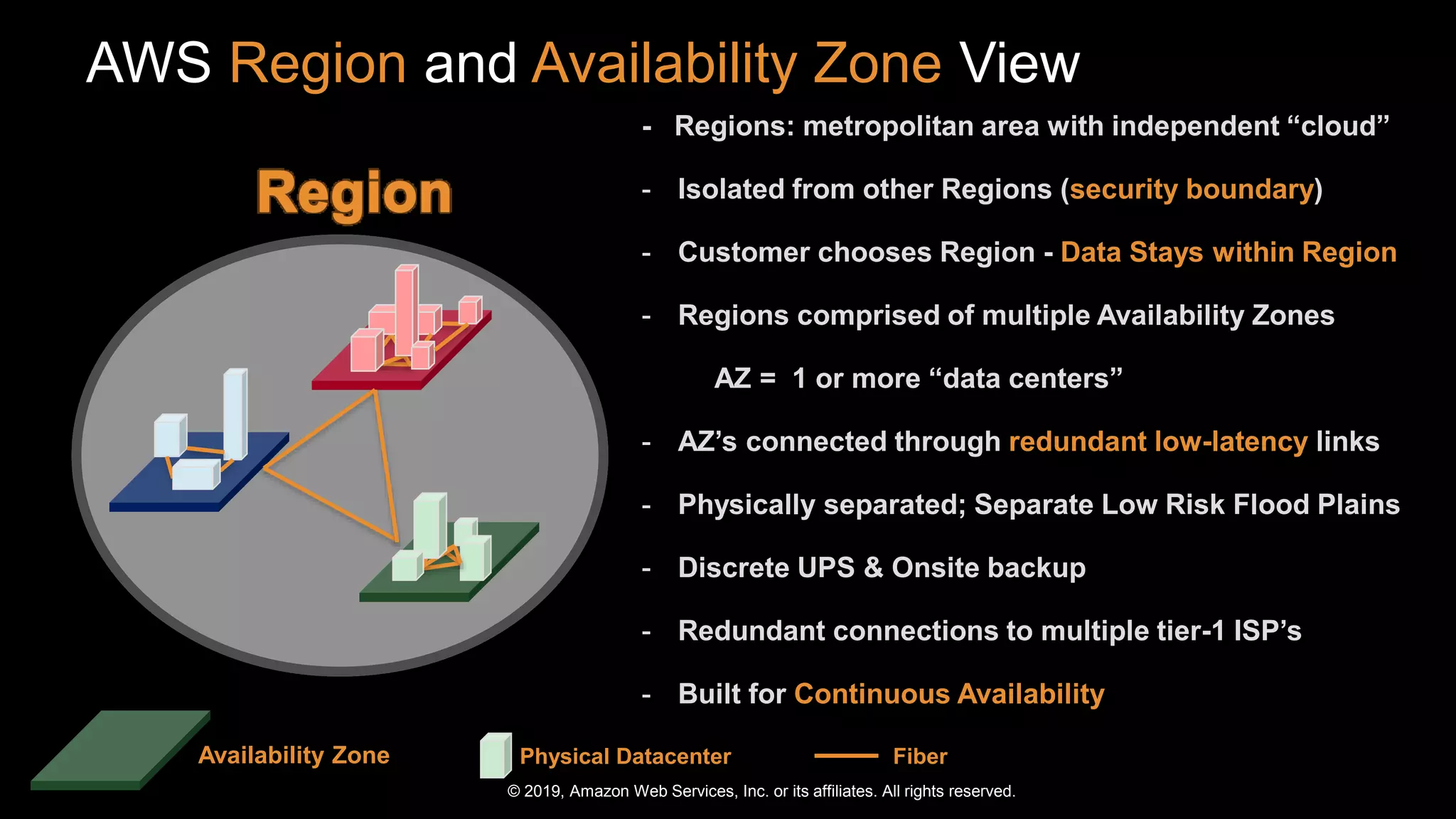
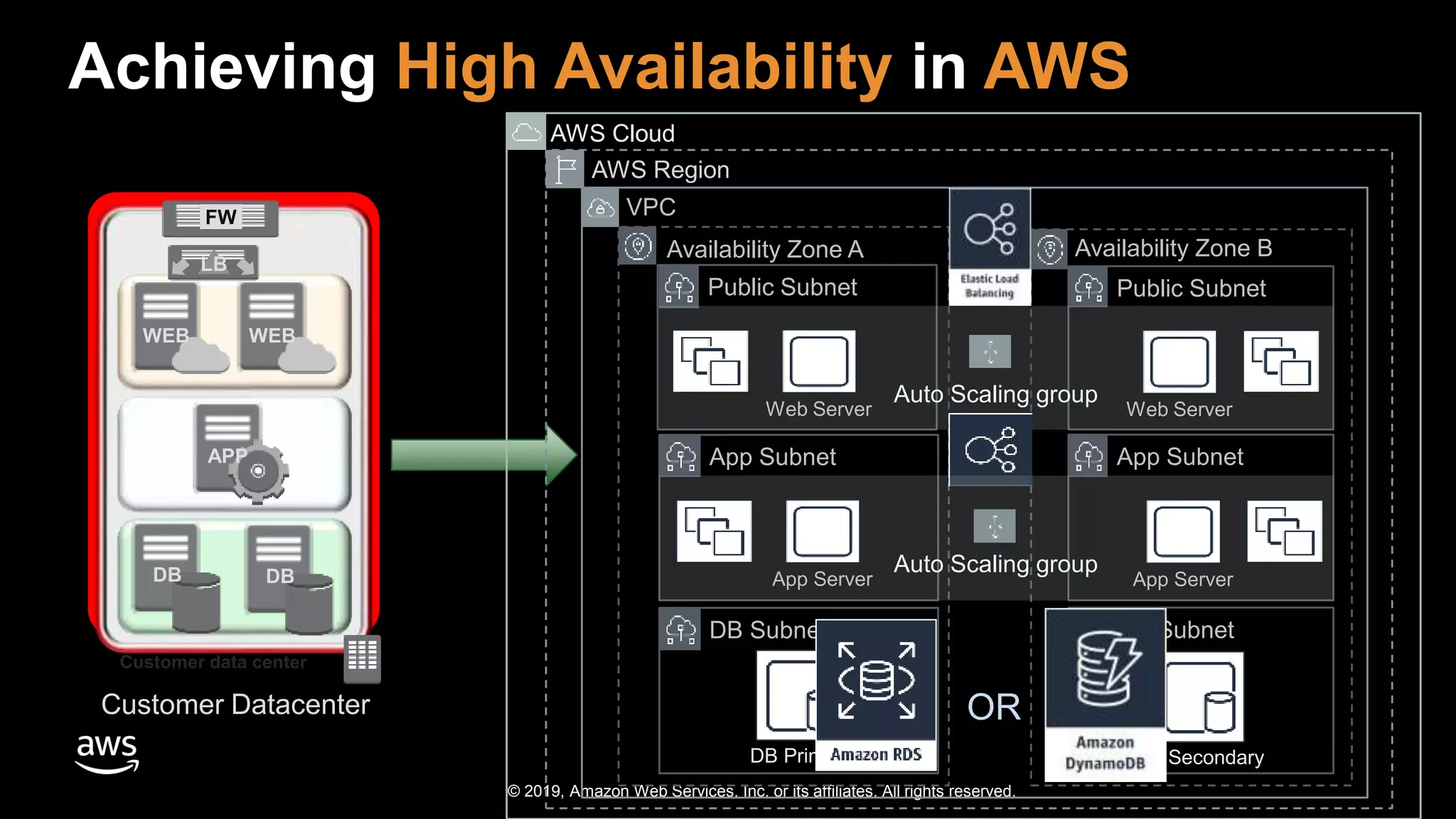
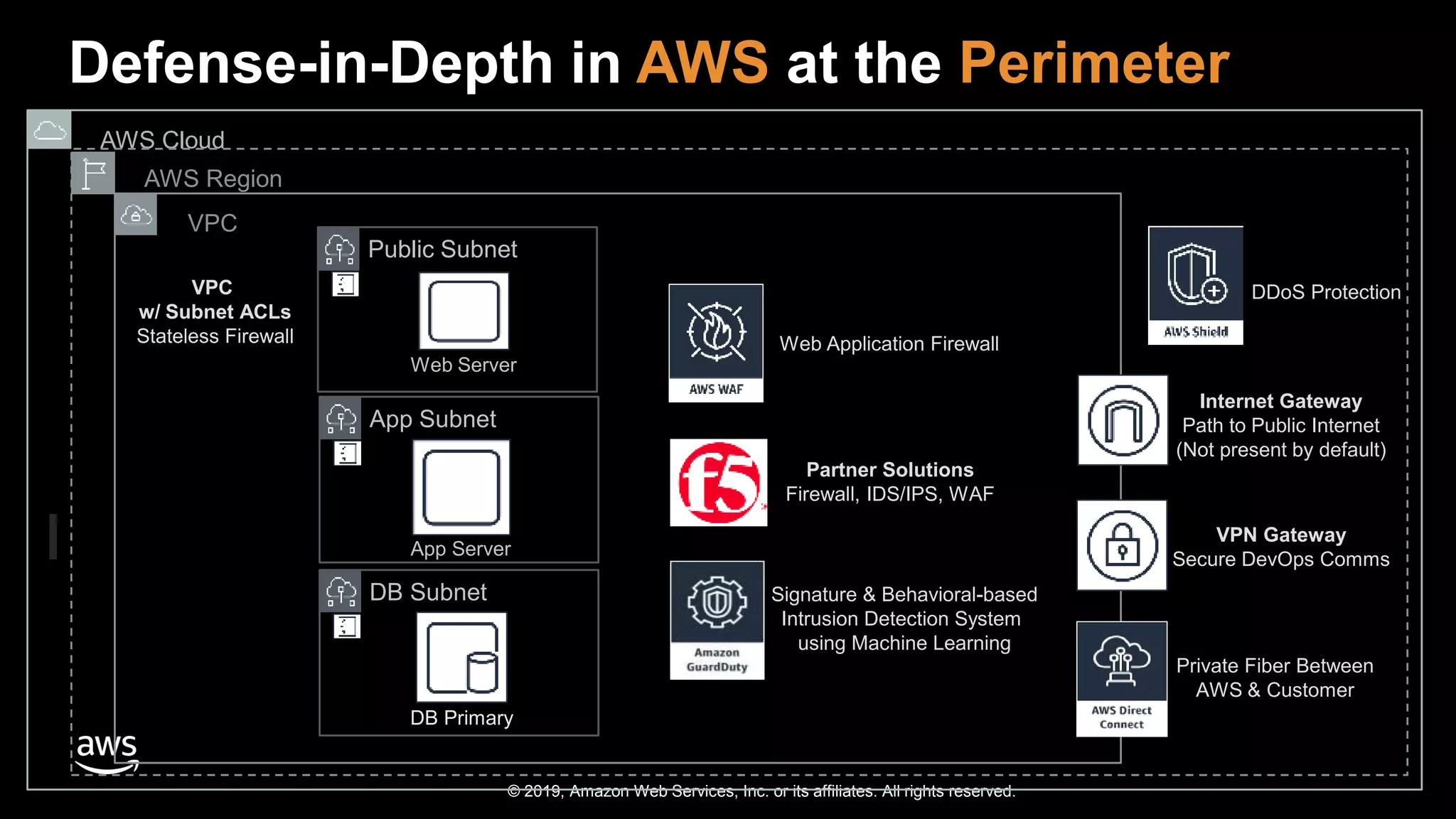
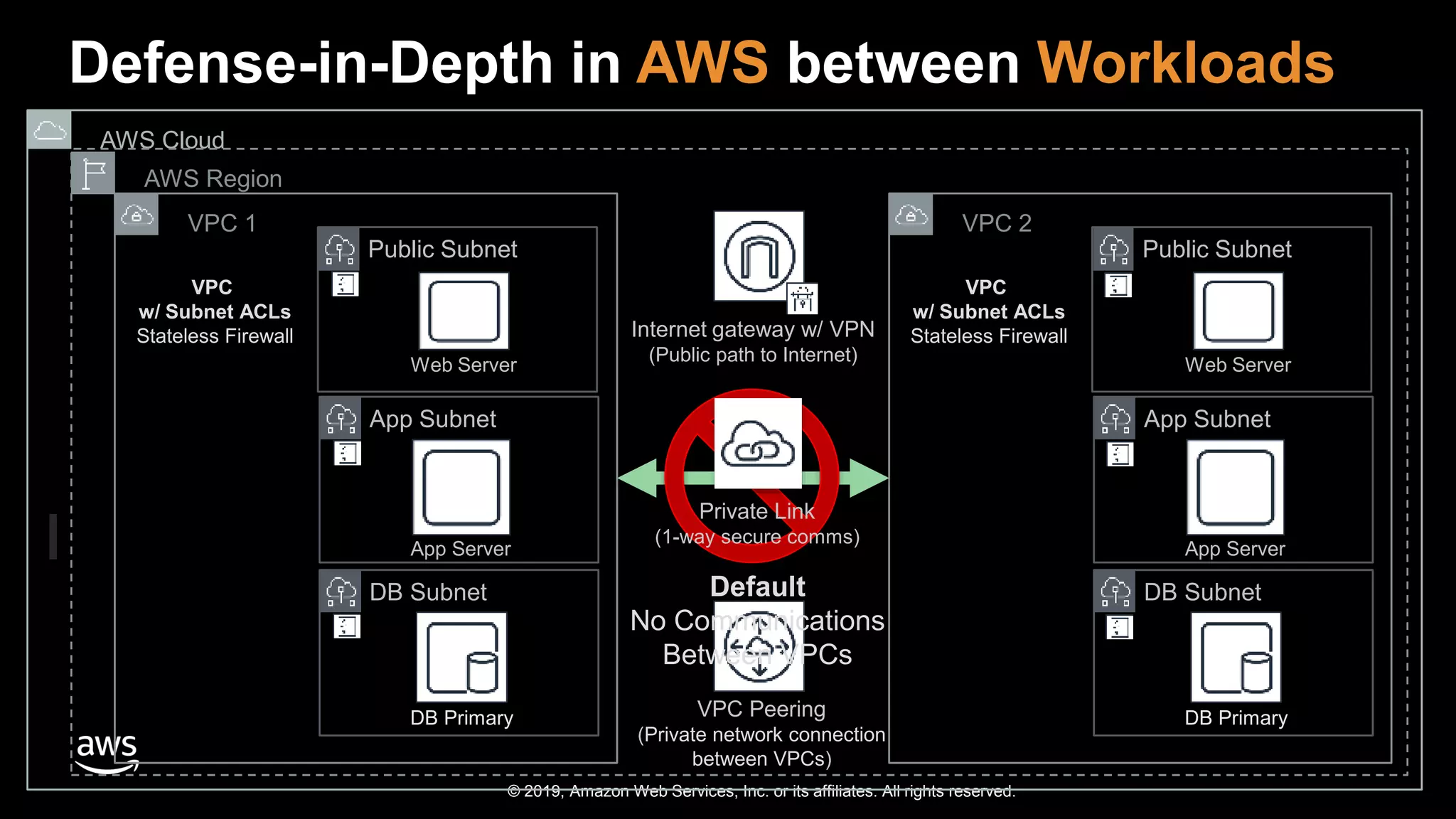
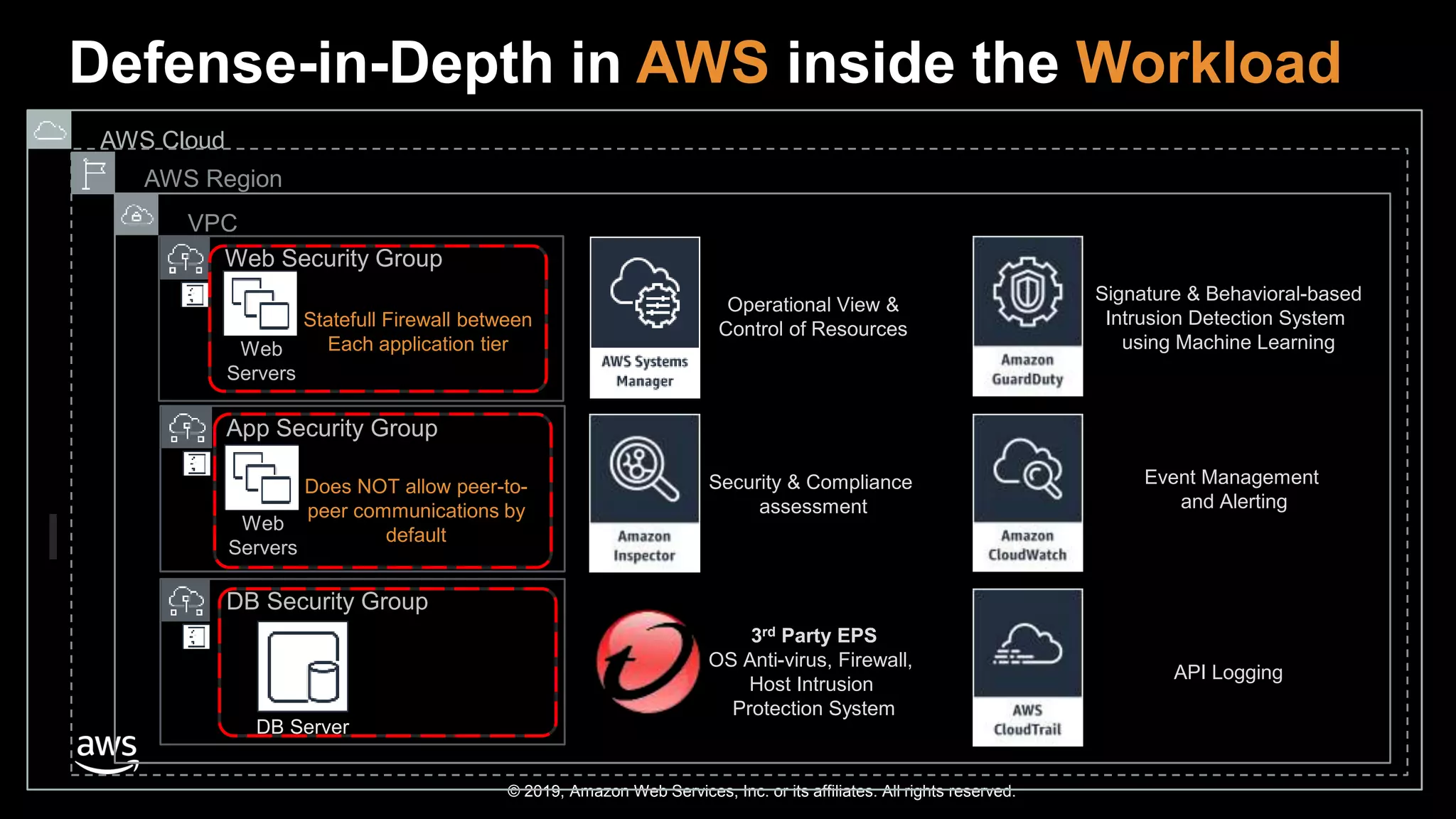
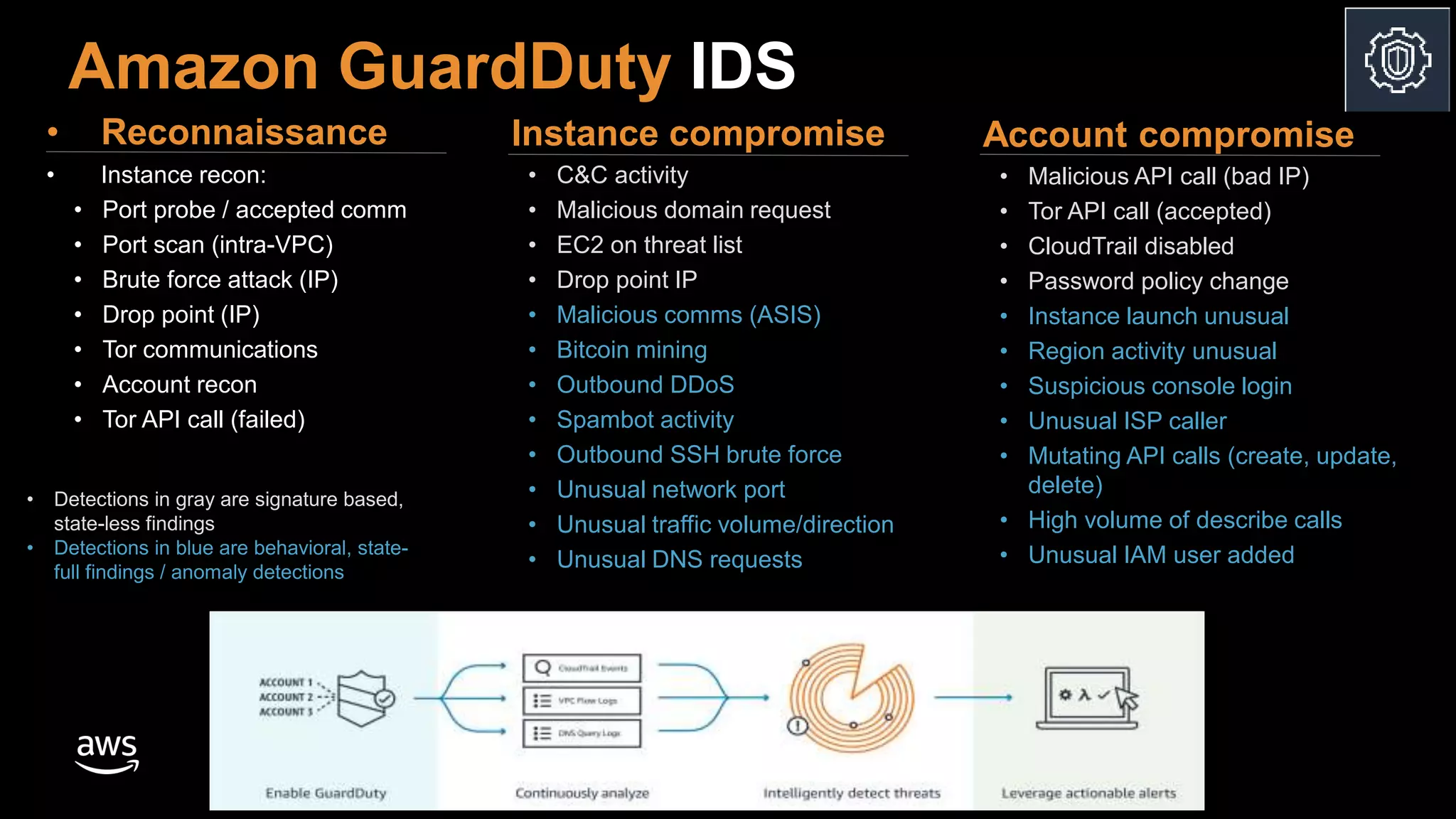
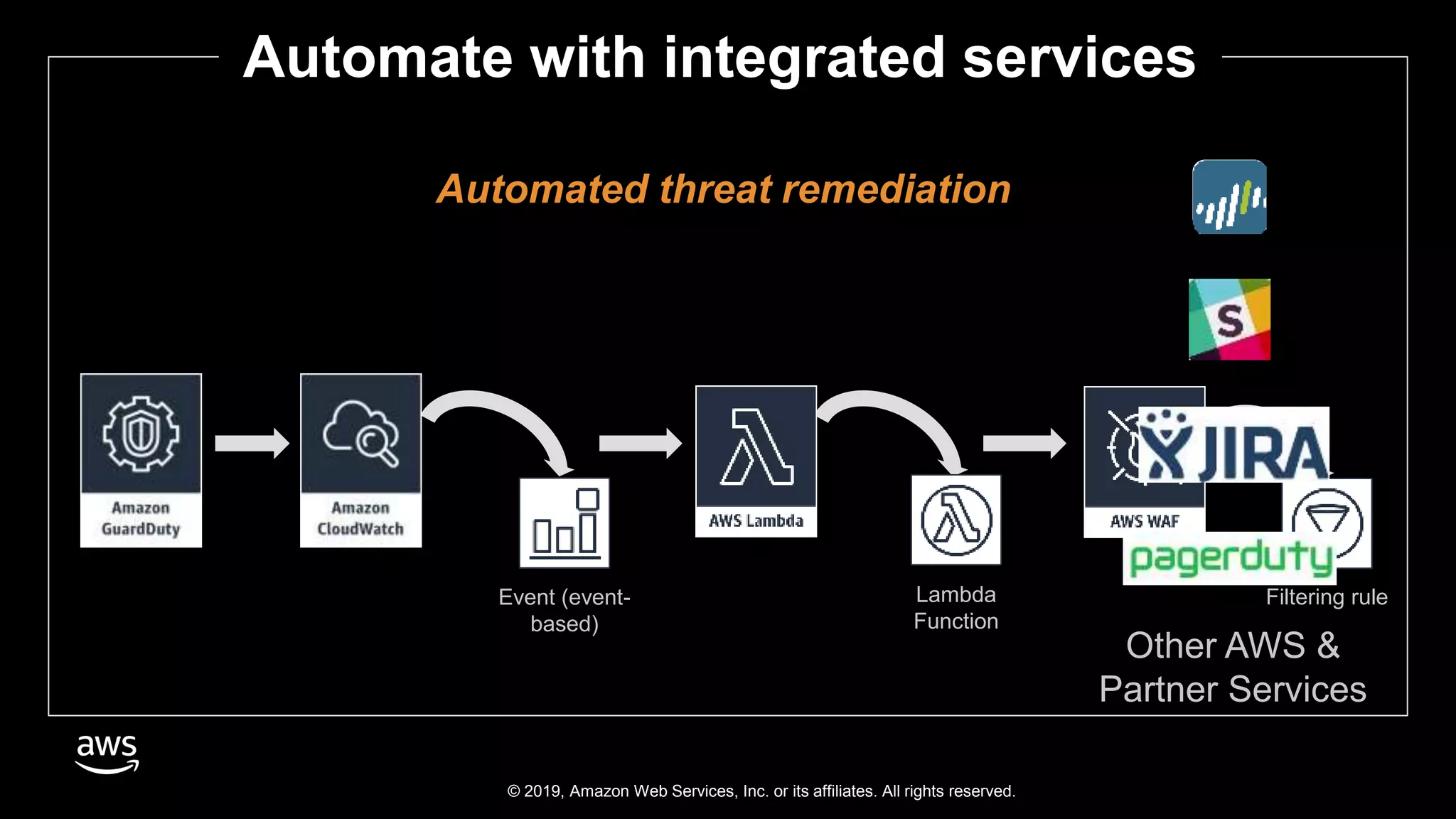
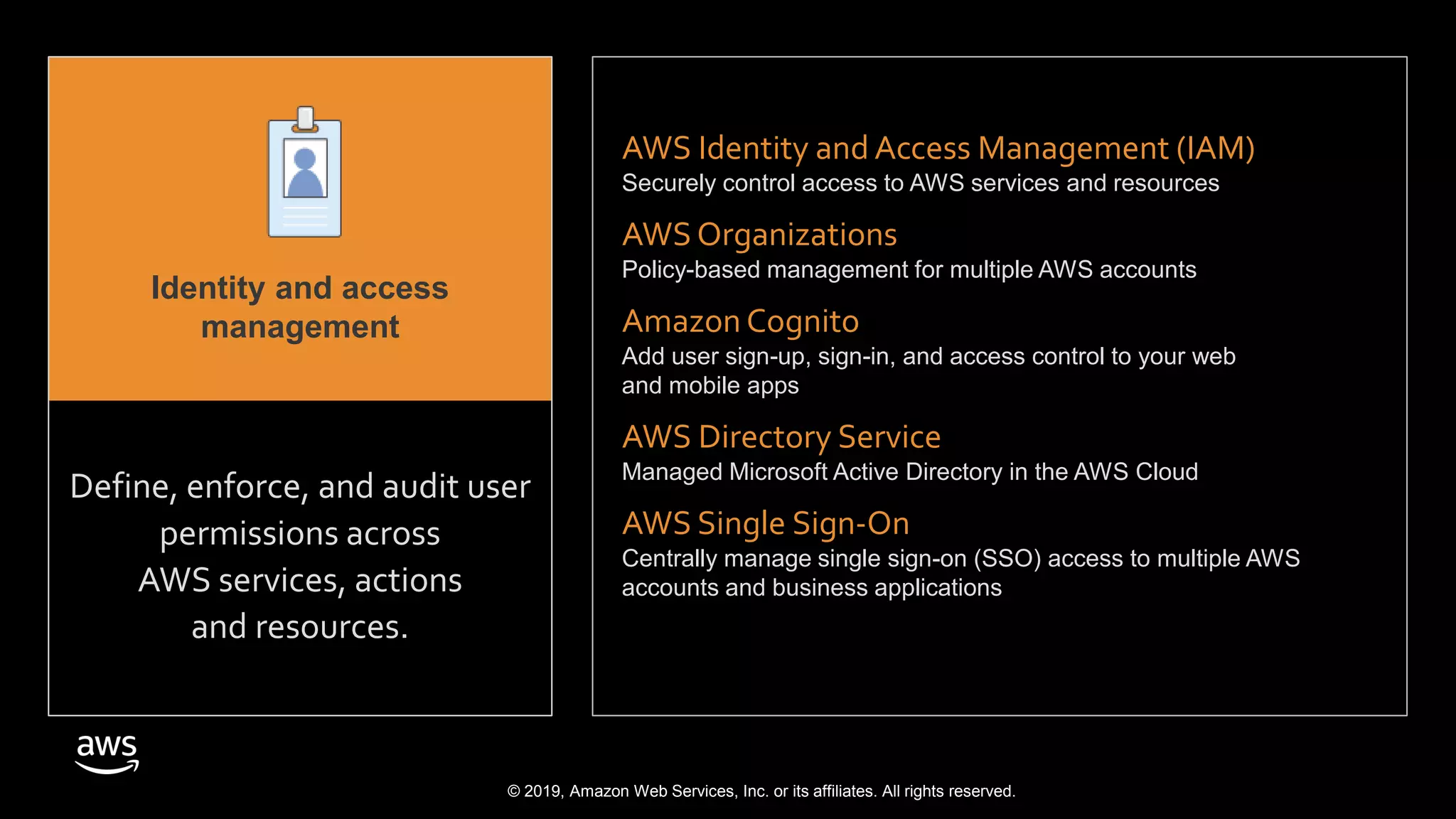
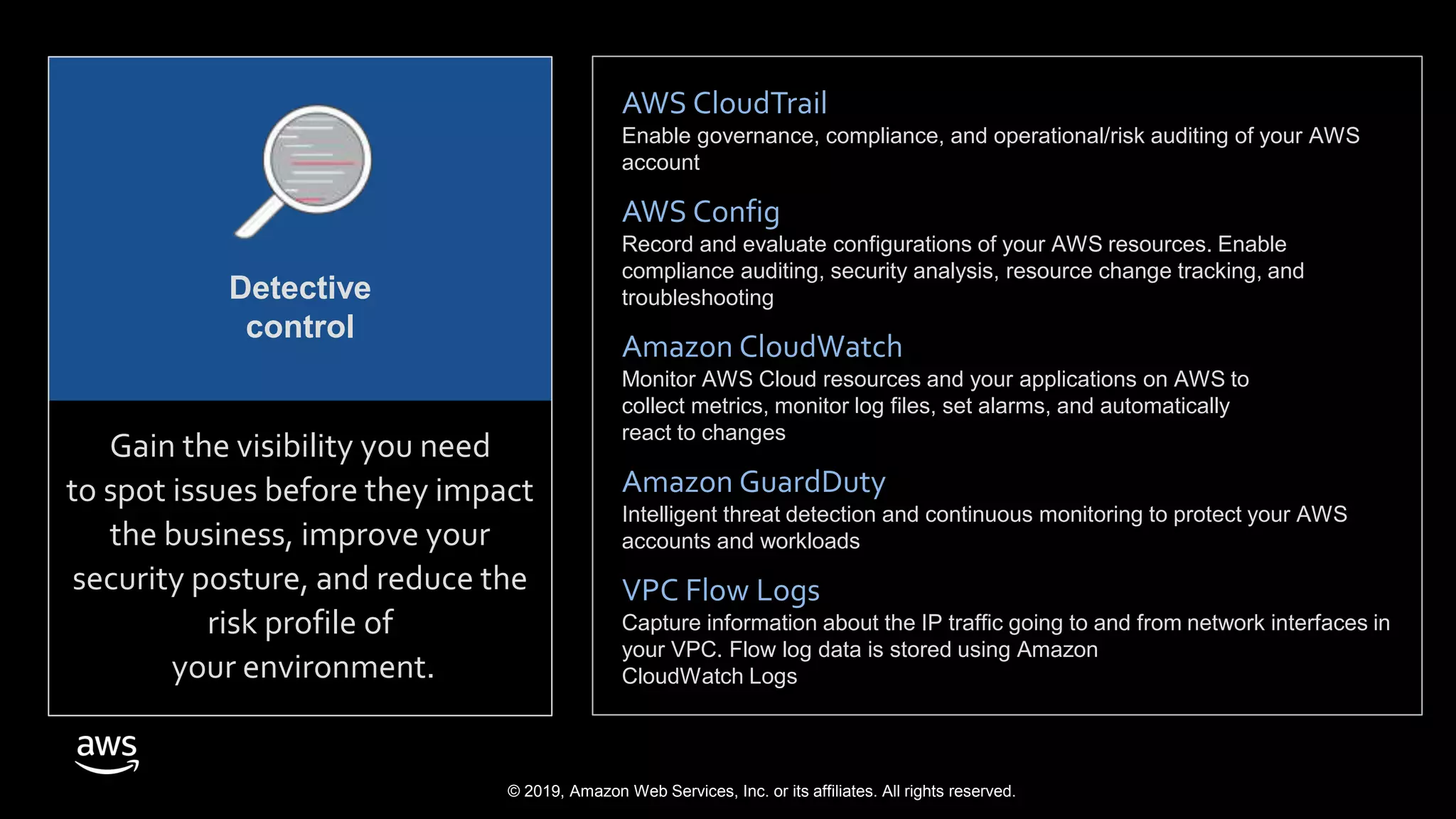
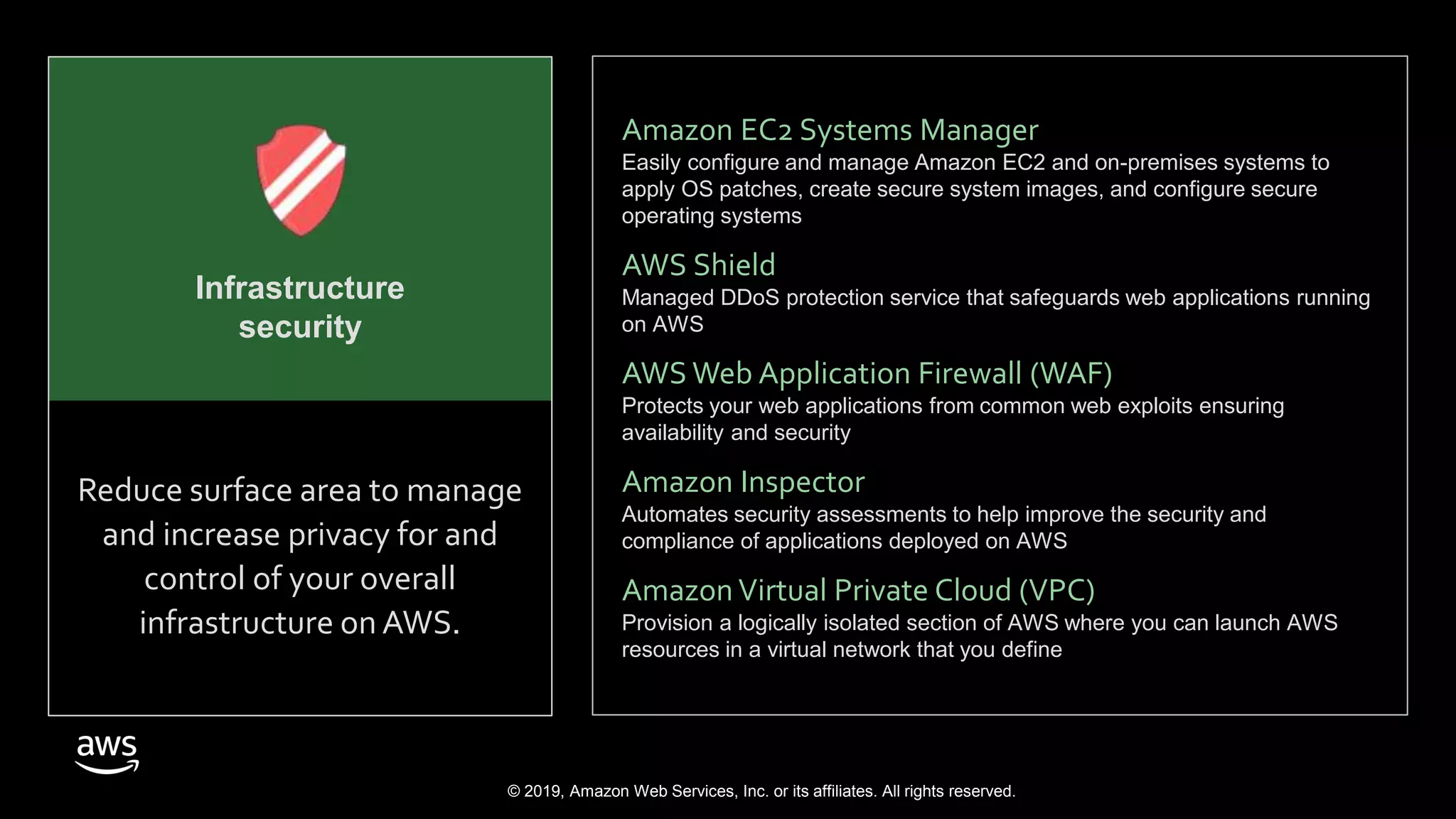
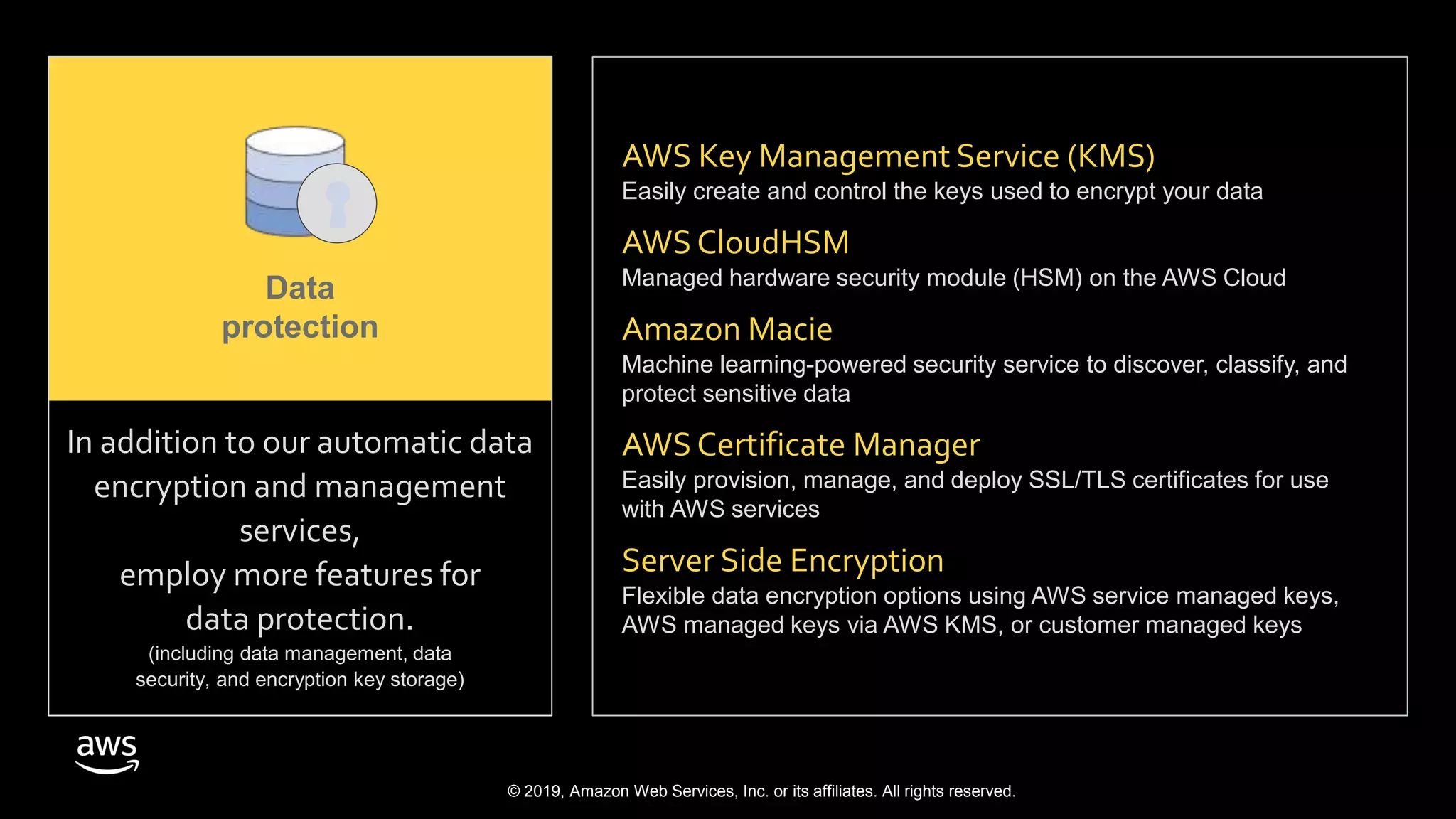
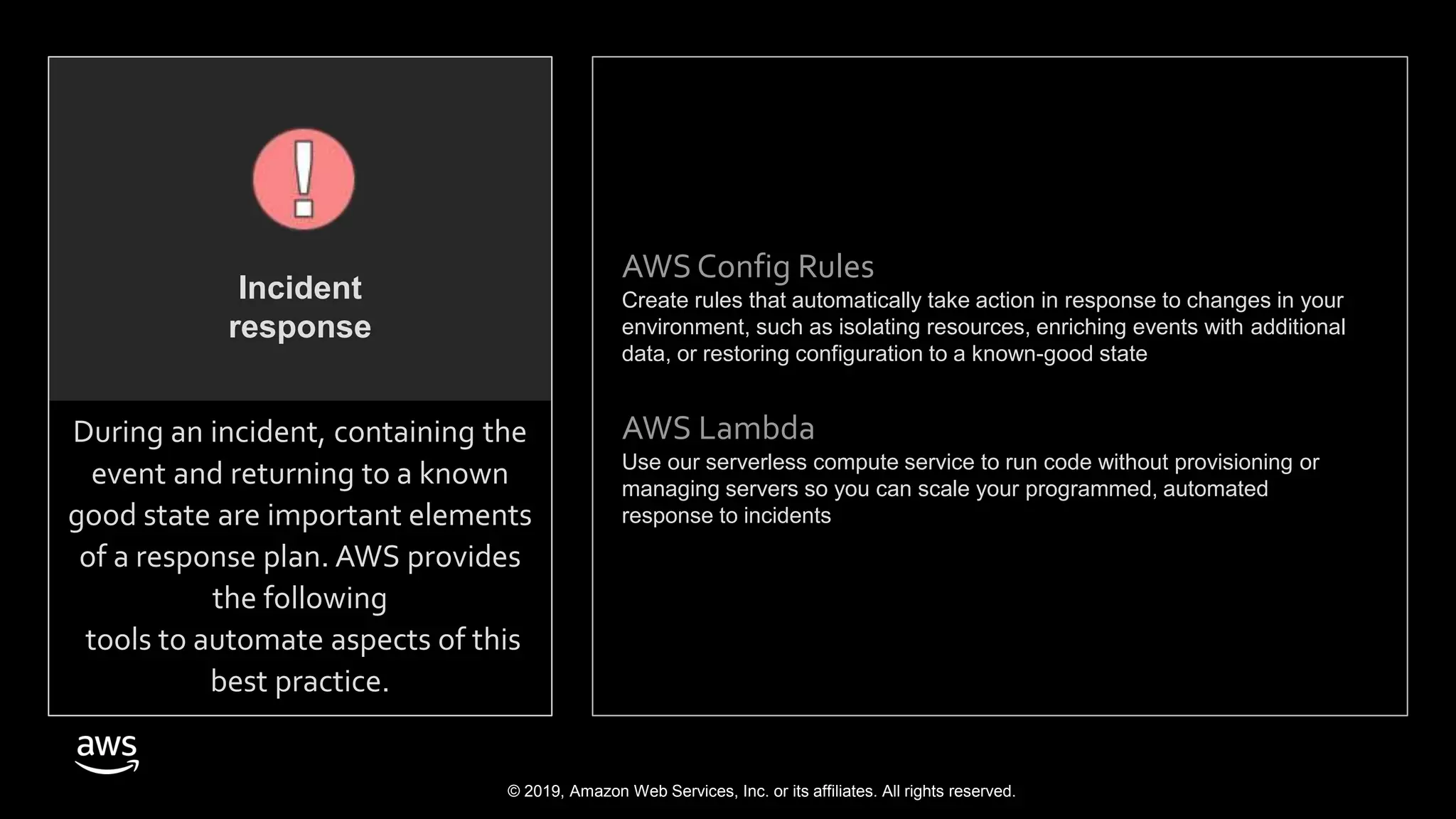
The document discusses the security benefits of transitioning to cloud computing, highlighting the shared responsibility model between AWS and customers. It details various AWS services that enhance operational visibility, resiliency, and data protection, and emphasizes automation in threat detection and incident response. Ultimately, it argues that the cloud can offer enhanced security compared to traditional on-premises data centers.