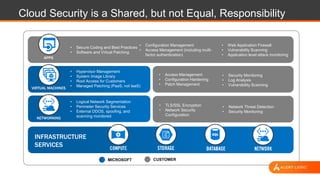
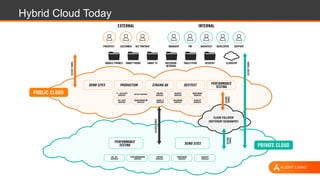
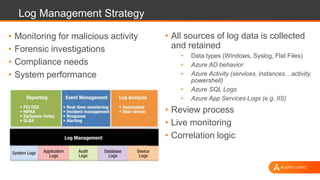
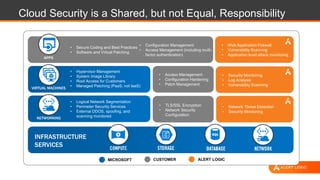
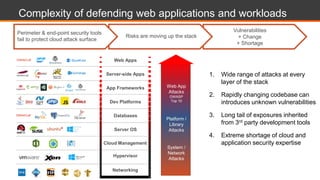
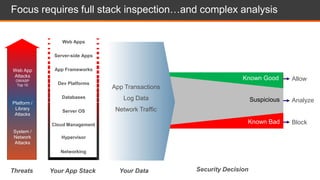
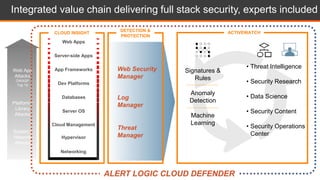
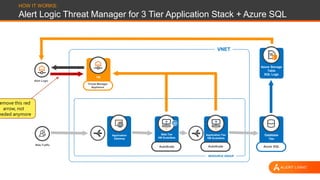
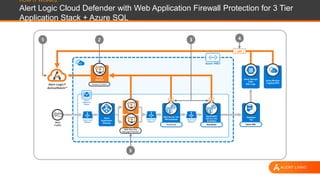
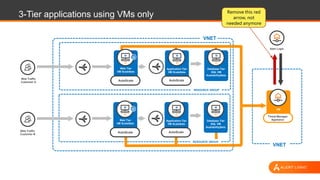
This document discusses shared security responsibility in Azure. It provides an overview of security best practices when using Azure, including understanding the shared responsibility model, implementing network security practices, securing data and access, securely developing code, log management, and vulnerability management. It also describes Alert Logic security solutions that can help monitor Azure environments for threats across the application stack.