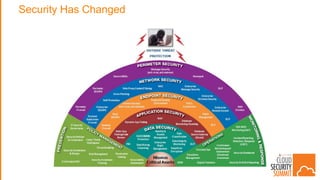
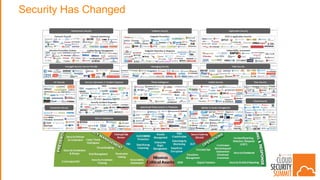
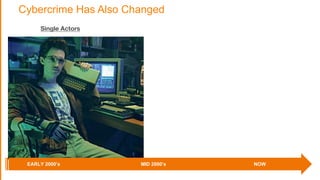
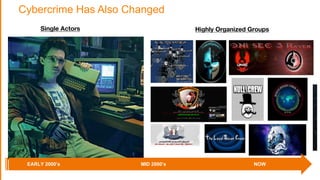
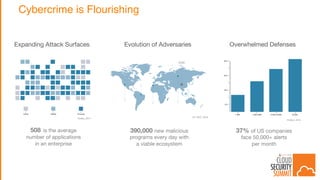
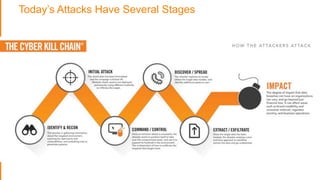
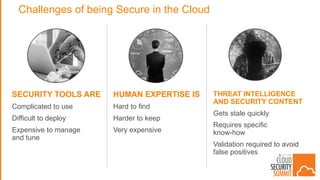
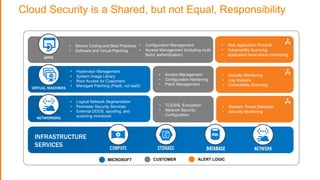
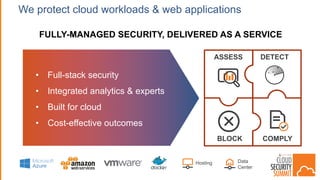
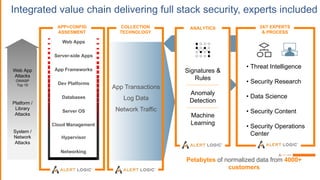
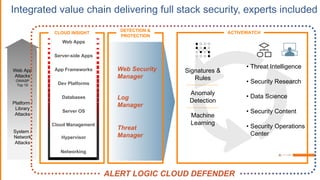
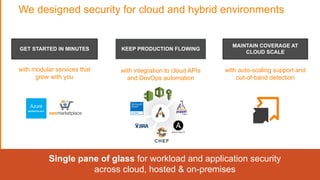
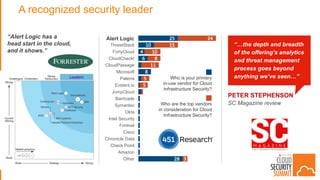
The document discusses the evolving security landscape in cloud environments, emphasizing the increased complexity and risks associated with cybercrime, where attackers have become more organized and attacks more sophisticated. It highlights the need for a shift in security approaches, maintaining traditional security best practices while adapting them for cloud technologies, and stresses the shared responsibility model between service providers and users. Additionally, it presents Alert Logic as a solution for providing integrated security and analytics for cloud workloads and web applications.