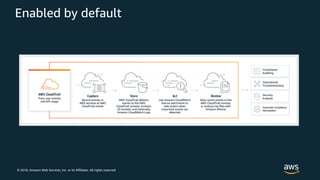
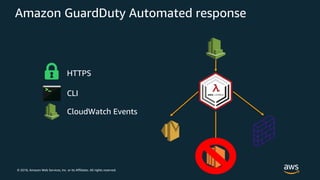
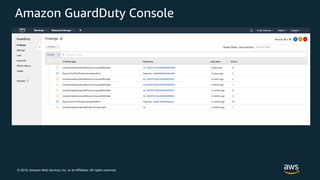
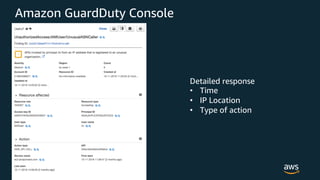
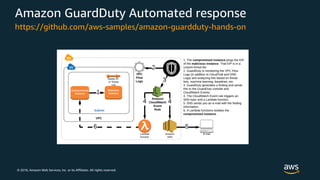
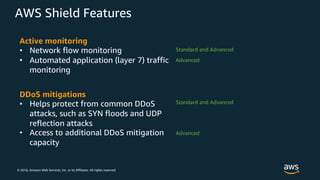
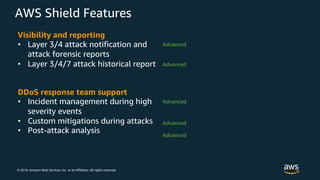
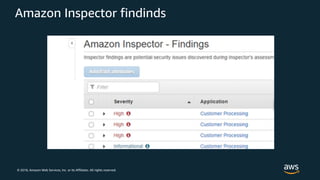
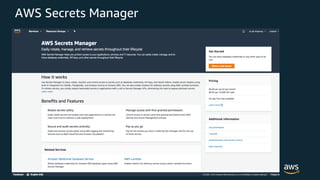
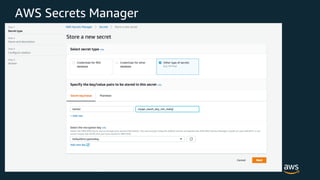
The document discusses various AWS security services including Identity and Access Management (IAM) for authorization, VPCs for network security, CloudTrail for auditing API calls, GuardDuty for threat detection, WAF for web application firewall, Shield for DDoS protection, Inspector for security assessments, and Secrets Manager for secrets management. It provides overviews and examples of how to configure and use these services to help secure workloads running on AWS.