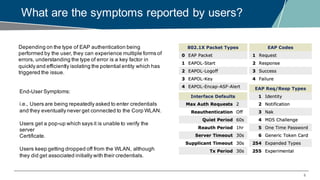
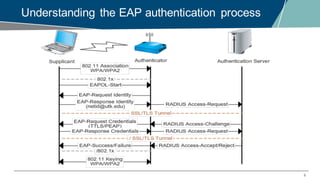
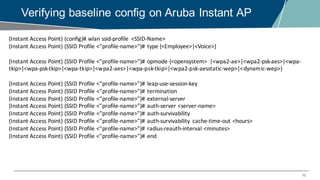
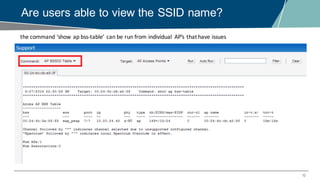
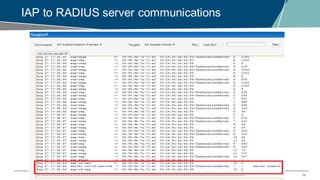
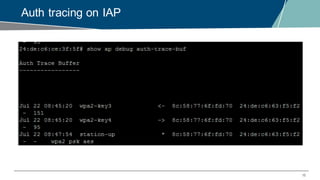
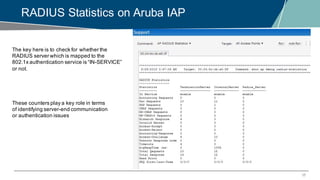
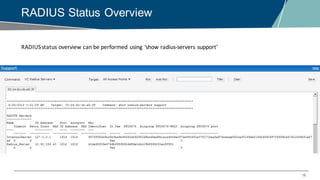
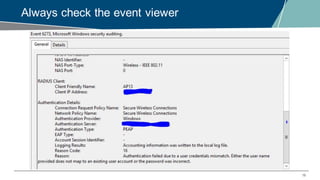
The document details a webinar on troubleshooting 802.1x issues related to Aruba Instant connectivity, focusing on the identification and diagnosis of user authentication problems. It outlines prerequisites for troubleshooting, common user symptoms, and specific configurations for Aruba Instant Access Points. Additionally, it emphasizes the importance of checking radius server status and provides resources for further assistance.