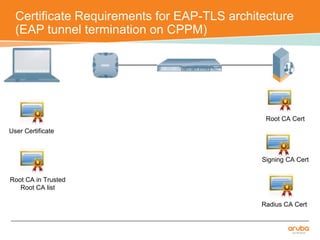
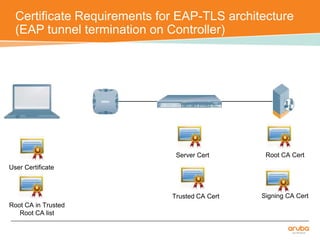
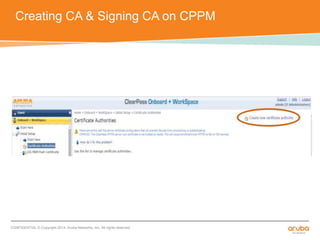
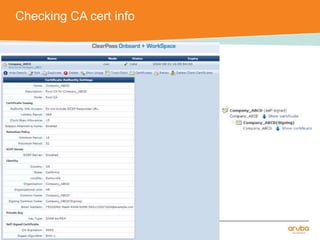
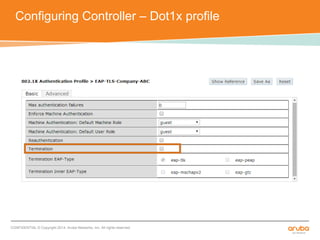
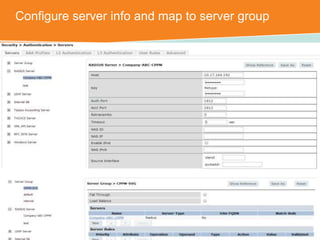
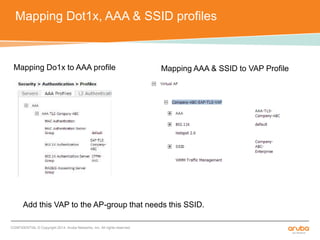
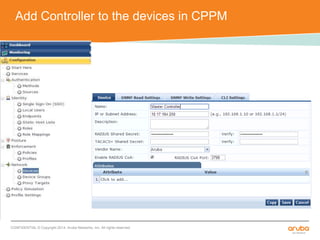
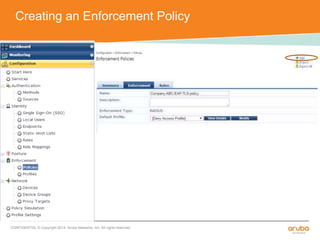
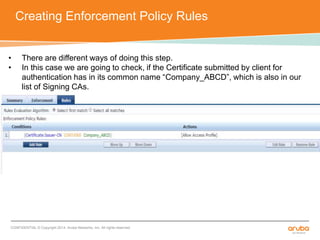
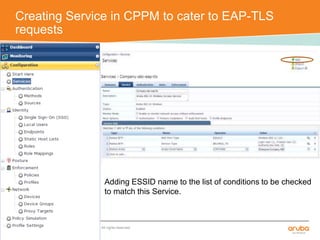
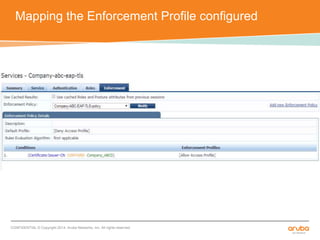
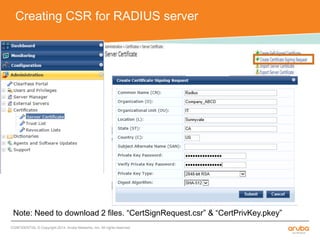
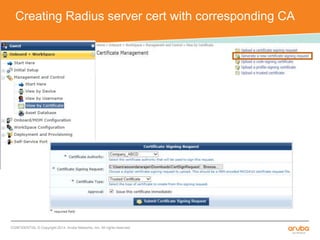
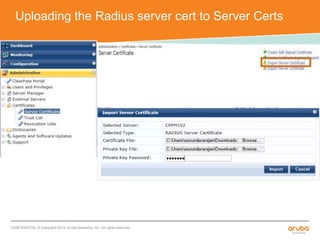
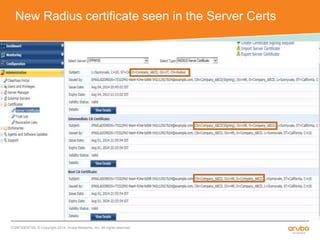
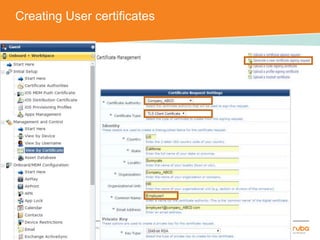
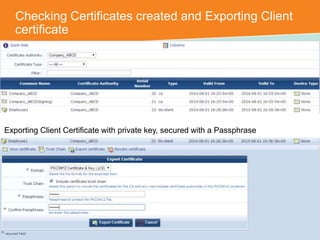
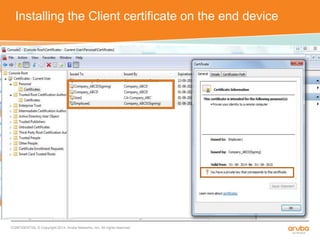
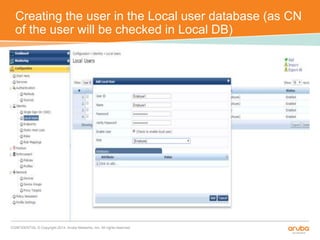
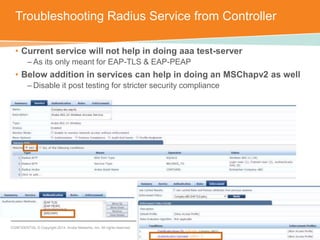
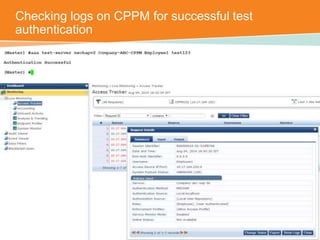
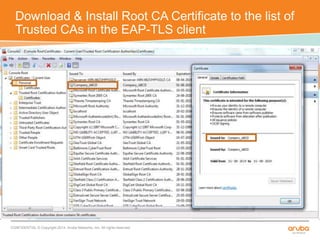
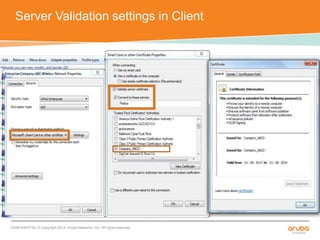
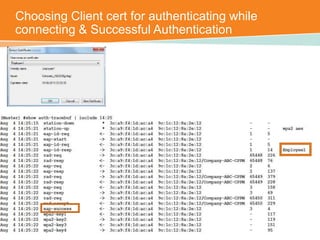
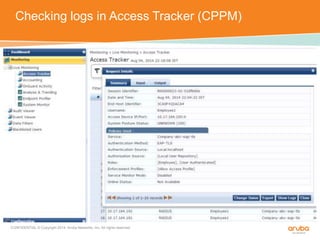
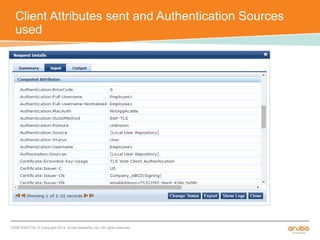
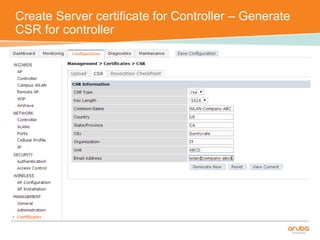
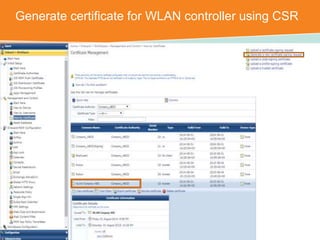
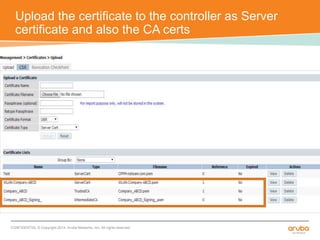
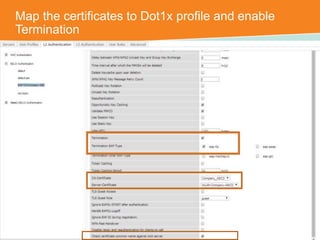
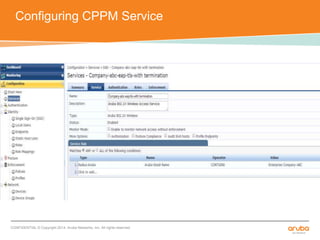
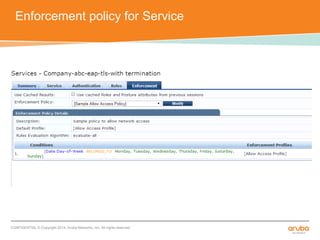
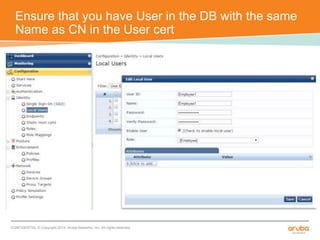
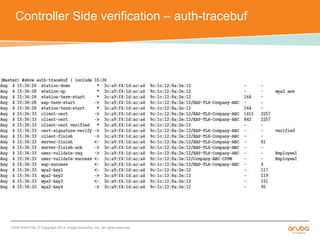
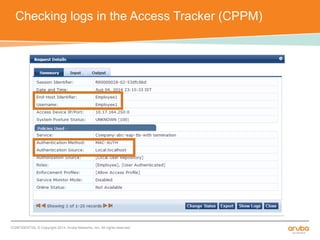
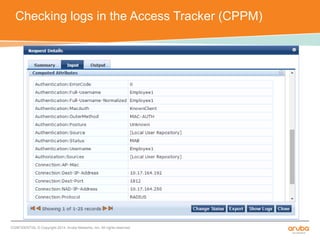
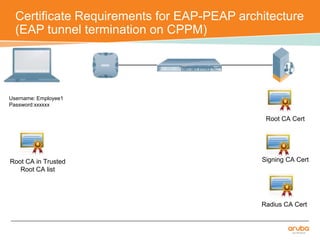
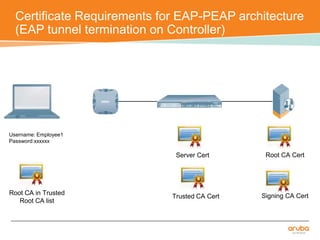
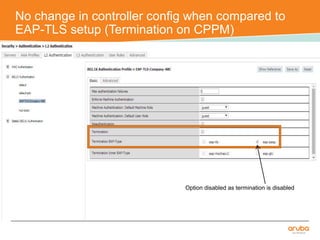
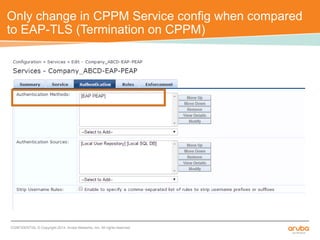
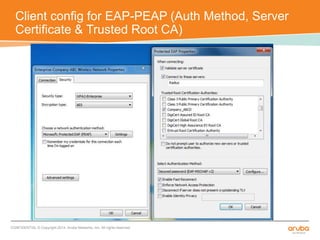
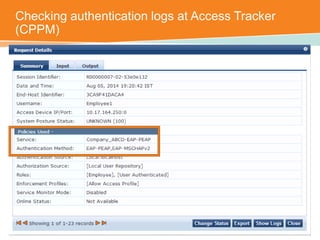
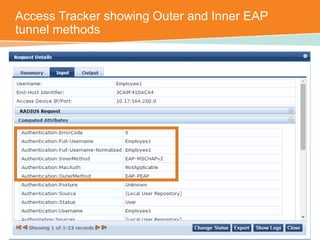
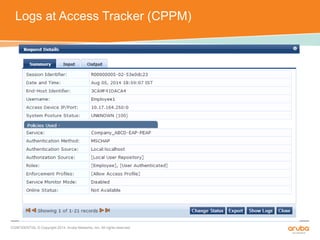
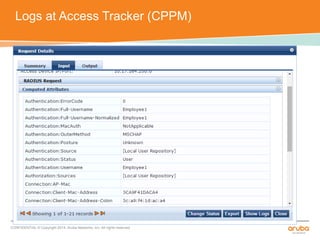
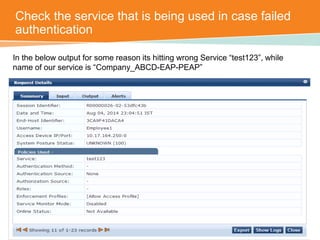
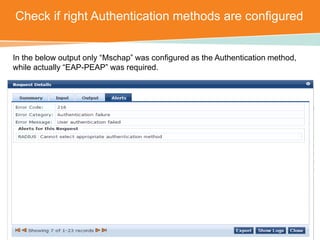
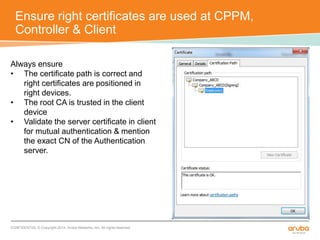
The document discusses the configuration and testing of EAP-TLS and EAP-PEAP authentication between an Aruba controller and CPPM authentication server. It provides step-by-step instructions on setting up EAP-TLS and EAP-PEAP when the EAP tunnel is terminated on the CPPM server or Aruba controller. Troubleshooting tips are also included such as ensuring the correct certificates, authentication methods and services are configured on the controller, CPPM and client devices.