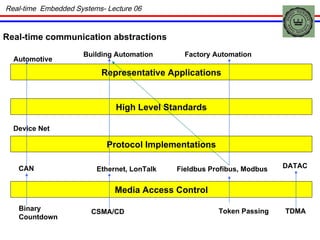
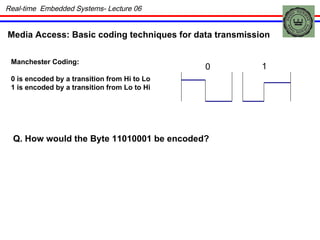
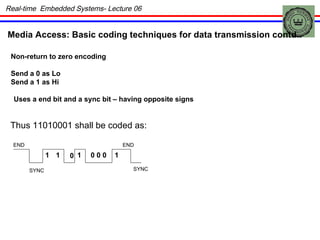
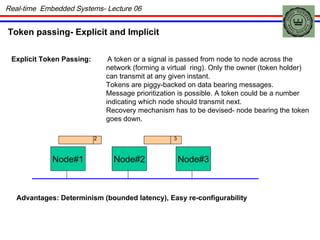
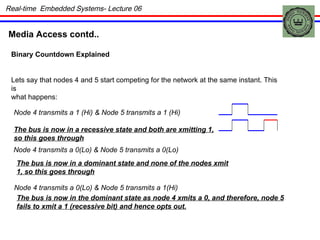
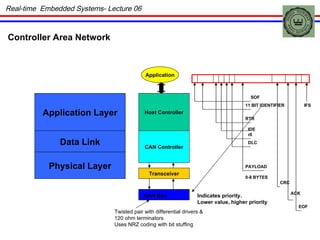
The document discusses real-time embedded communication and networking concepts. It describes explicit and implicit flow control, where explicit uses acknowledgments and implicit relies on redundancy. Media access control methods like TDMA, polling, token passing, and CSMA/CD are explained. Controller Area Network (CAN) is introduced as an example real-time embedded network protocol.