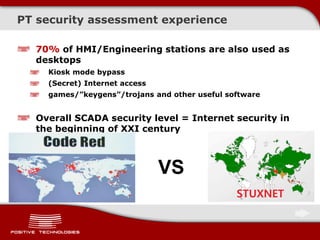
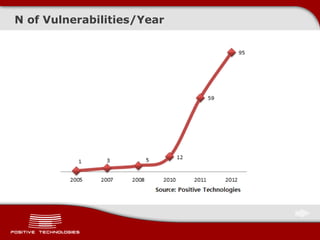
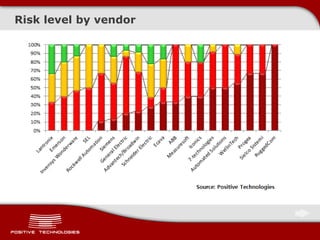
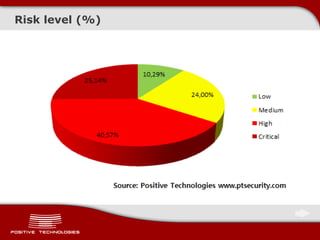
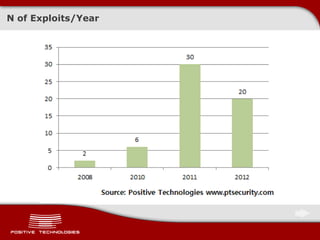
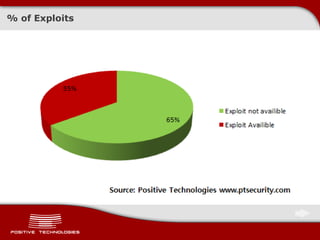
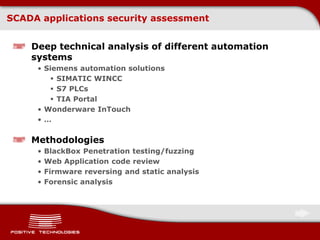
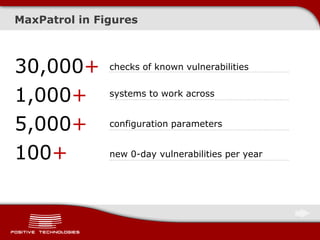
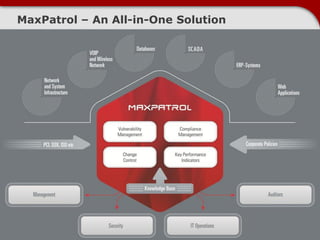
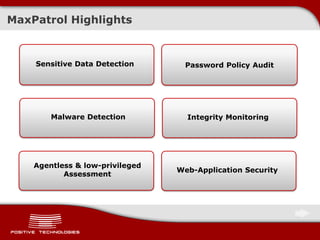
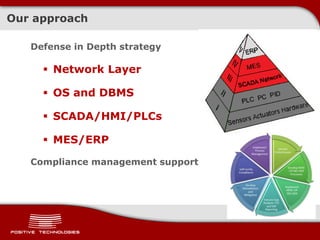
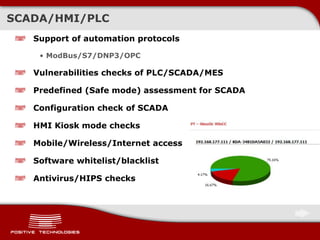
This document discusses securing ICS/SCADA systems. It provides an overview of Positive Technologies, a security company focusing on vulnerability management, penetration testing, and research. The document discusses common myths about SCADA security and research finding vulnerabilities across many systems. Positive Technologies' MaxPatrol product is presented for vulnerability and compliance management. Services include auditing ICS infrastructure and SCADA applications to identify risks.