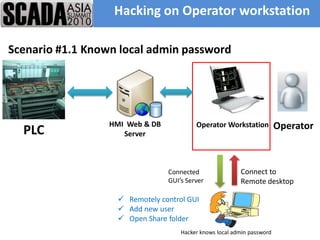
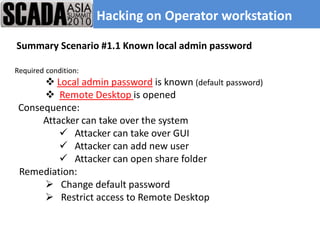
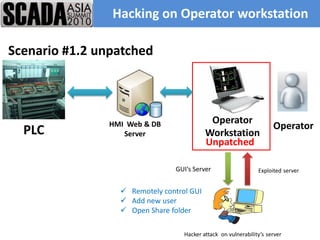
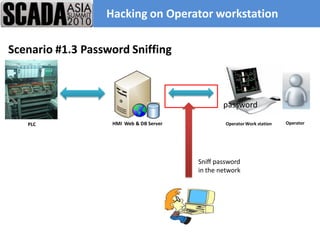
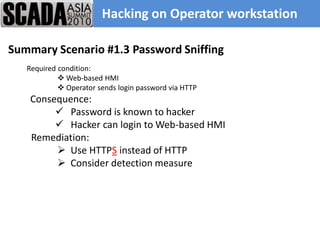
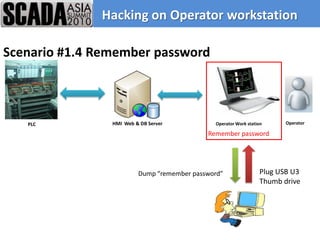
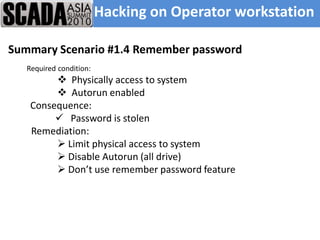
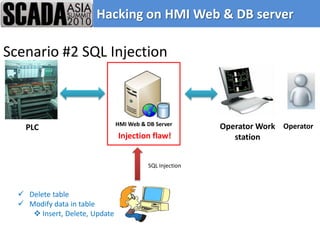
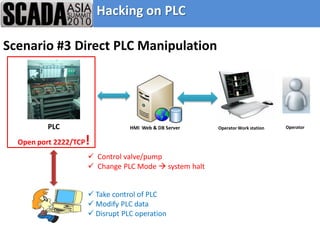
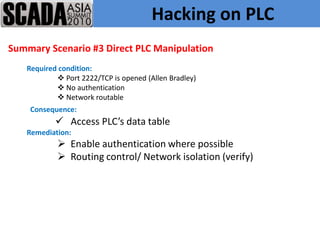
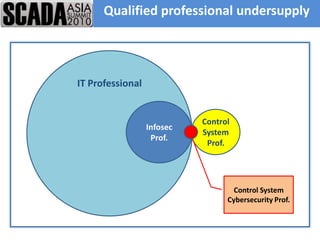
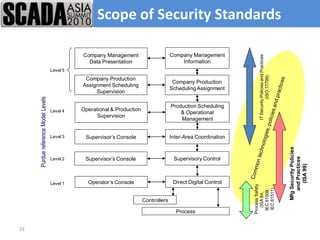
The document discusses improving control system security. It examines current security trends and their impact on SCADA systems. It discusses increasing the security and usability of SCADA systems through understanding tools and techniques to mitigate risks. The document also provides an overview of the speaker and their relevant experience and qualifications.