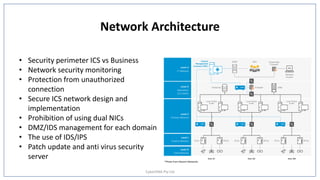
This document discusses an investor opportunity involving auditing industrial control systems (ICS) for security compliance based on the NIST SP 800-82 framework. It highlights the standard's 16 sections for assessing ICS security and provides brief explanations of requirements under sections like planning/policy/procedures, administrative controls, access control, and network architecture. The document promotes CyberDNA as a trusted partner that can help organizations meet the various technical and policy requirements for securely auditing and protecting their ICS environments.