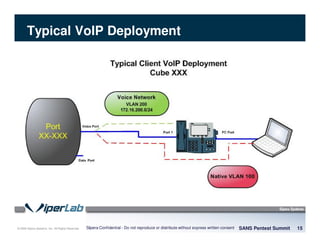
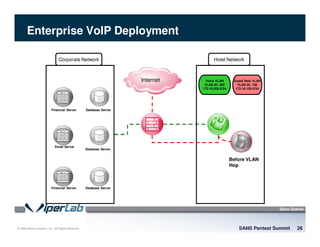
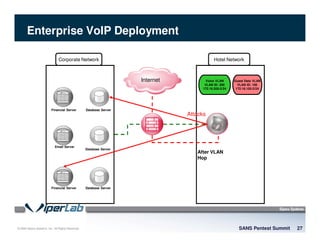
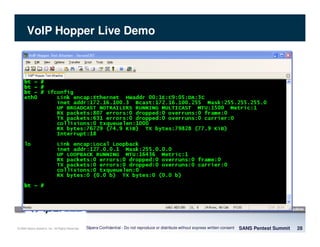
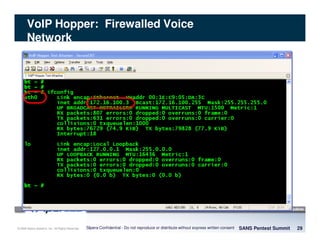
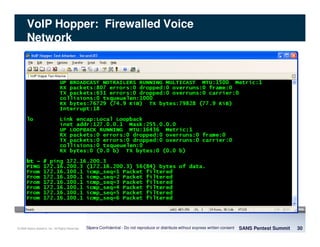
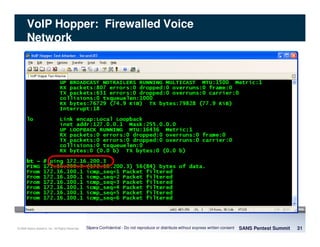
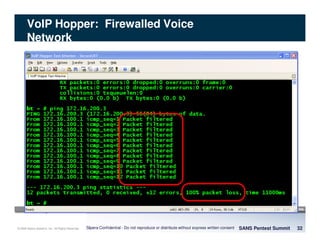
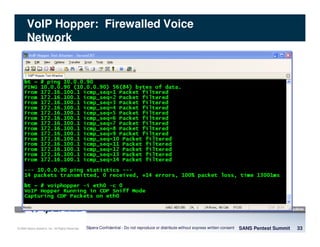
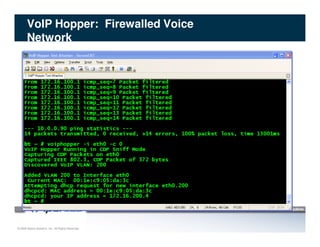
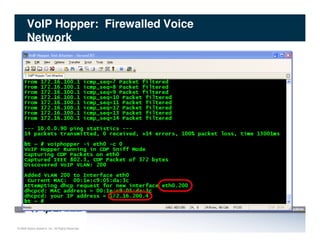
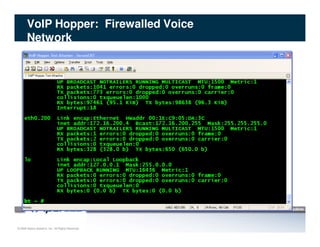
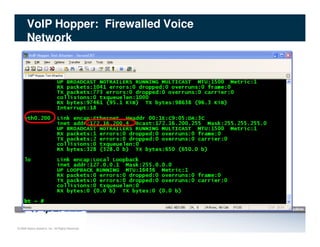
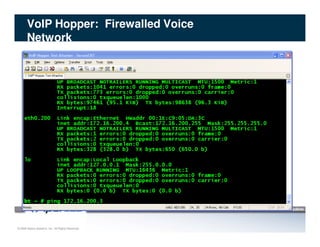
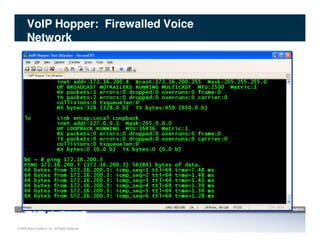
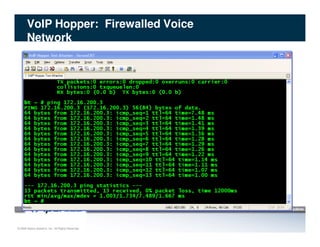
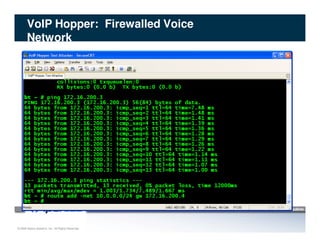
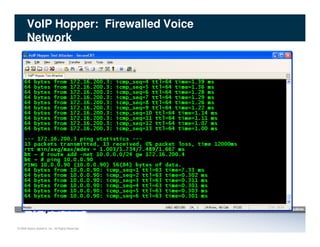
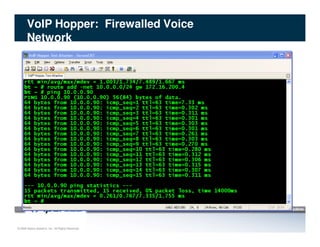
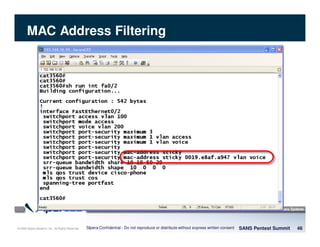
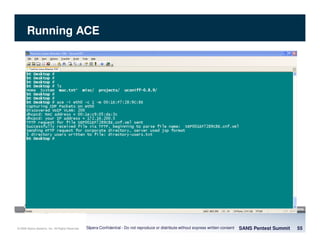
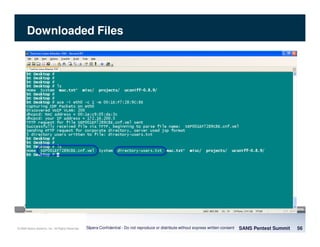
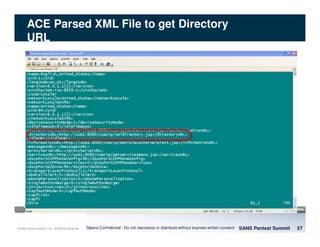
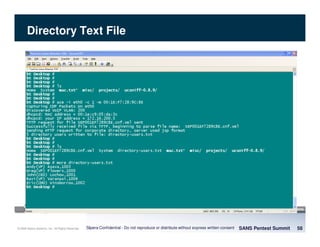
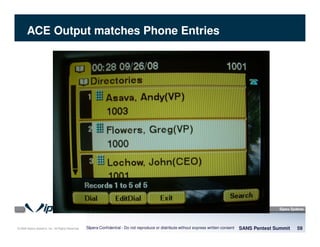
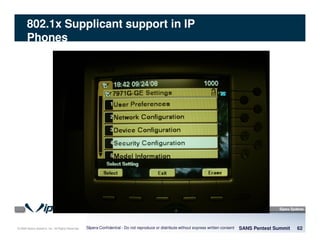
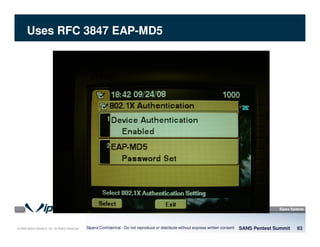
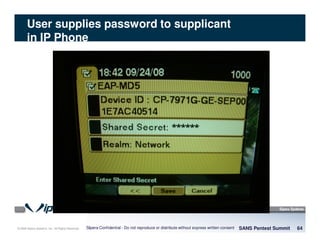
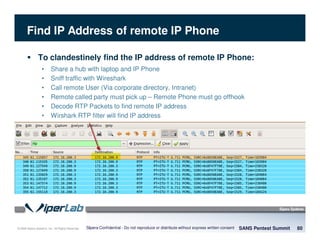
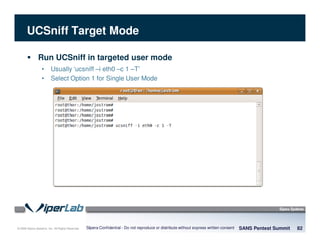
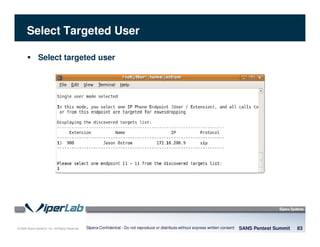
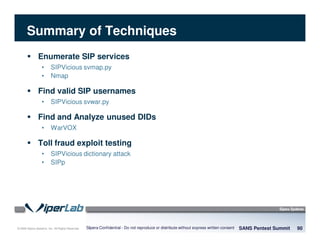
The document discusses penetration testing of VoIP networks. It describes a VoIP security research lab that investigates attack vectors against VoIP systems. When conducting internal VoIP assessments, the objectives are to understand the call requirements, VLAN configuration, and gain access to the voice VLAN to test for vulnerabilities. Sniffing tools can reveal the voice VLAN ID and credentials. VLAN hopping poses a risk if an attacker can access the voice VLAN from their PC. A case study found an attacker was able to hop VLANs in a hotel network and potentially monitor other guests' phone calls due to poor network segmentation. Proper firewalling of voice networks and limiting remote access to voice VLANs are important lessons learned.