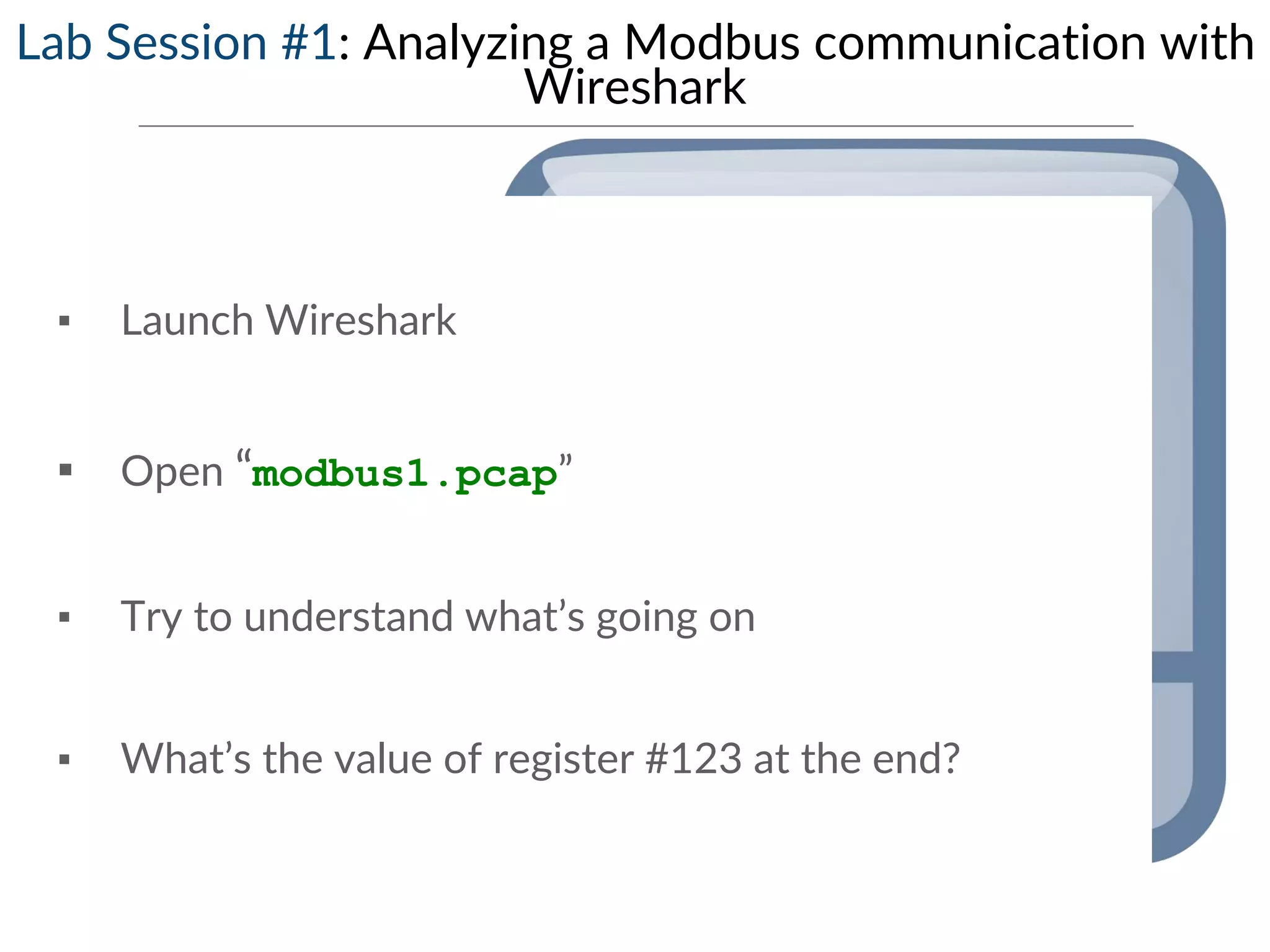
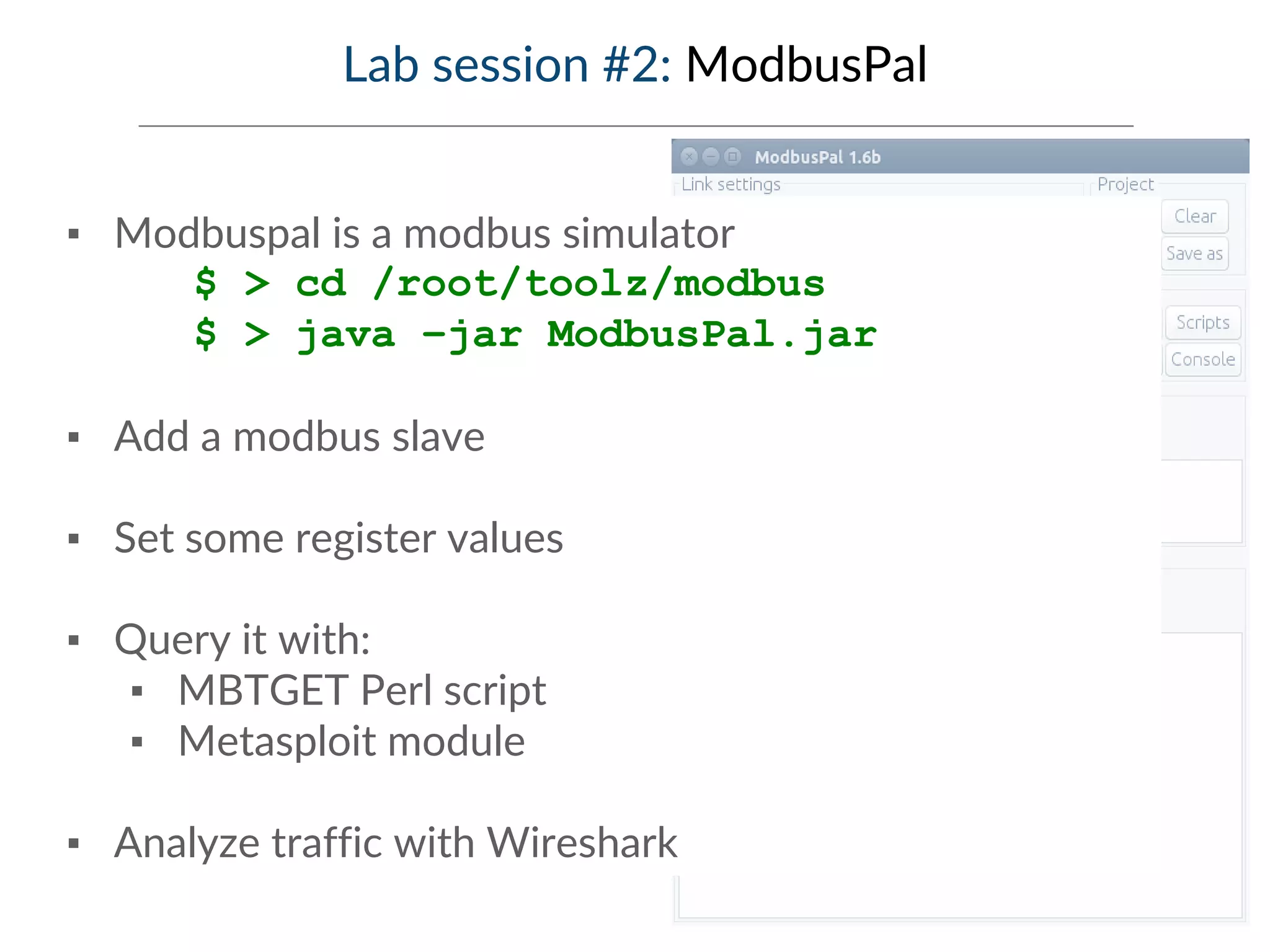
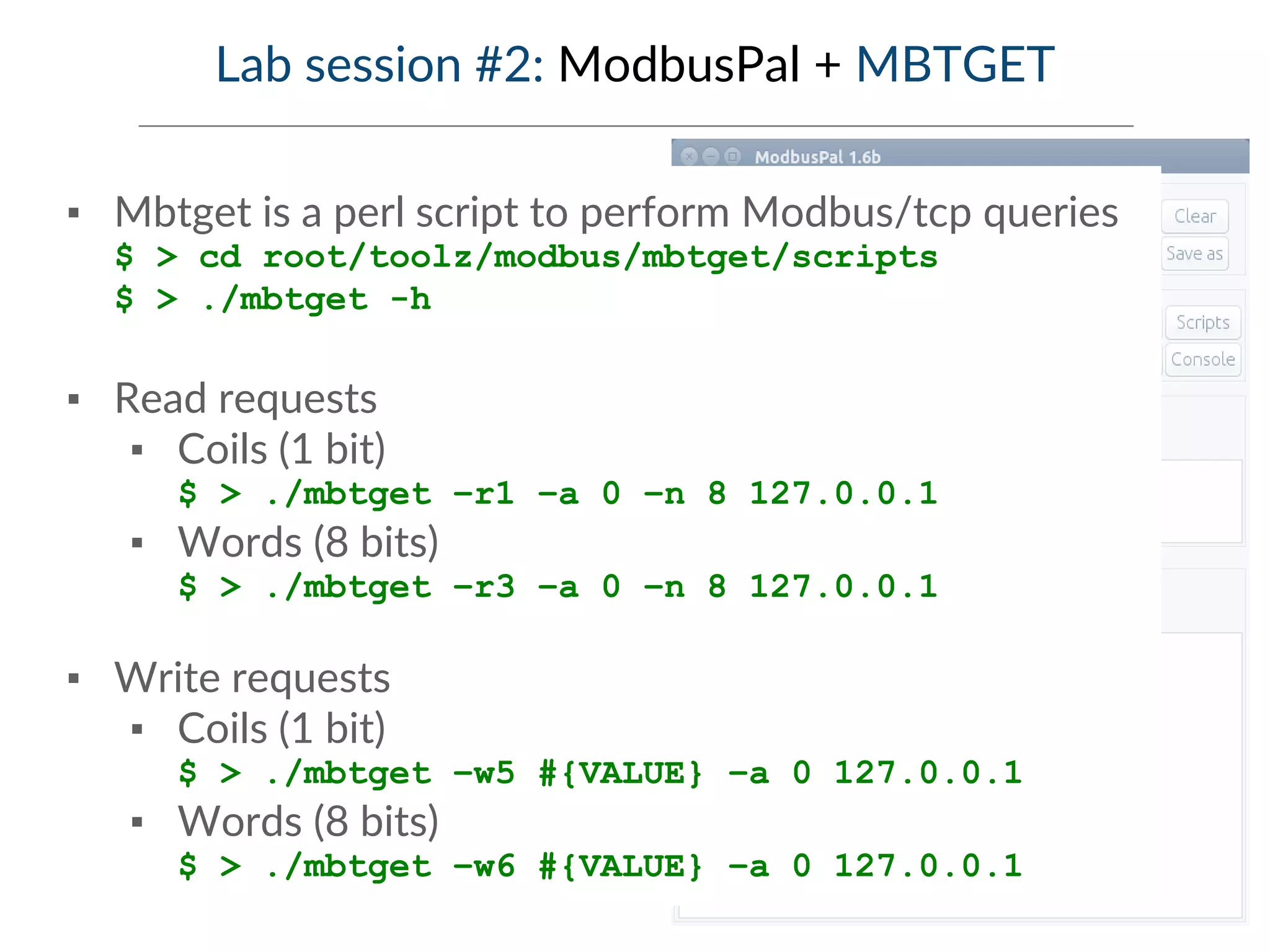
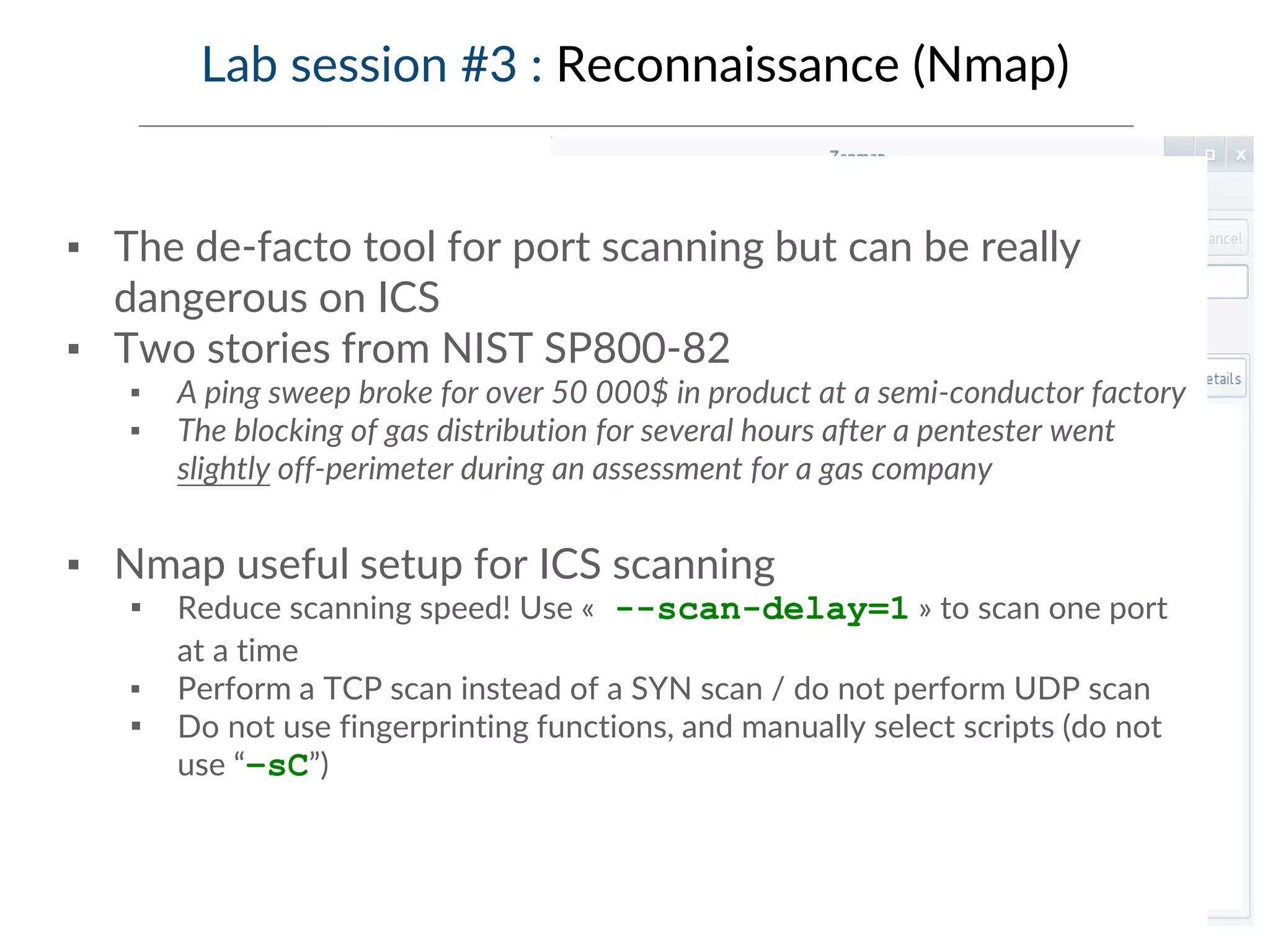
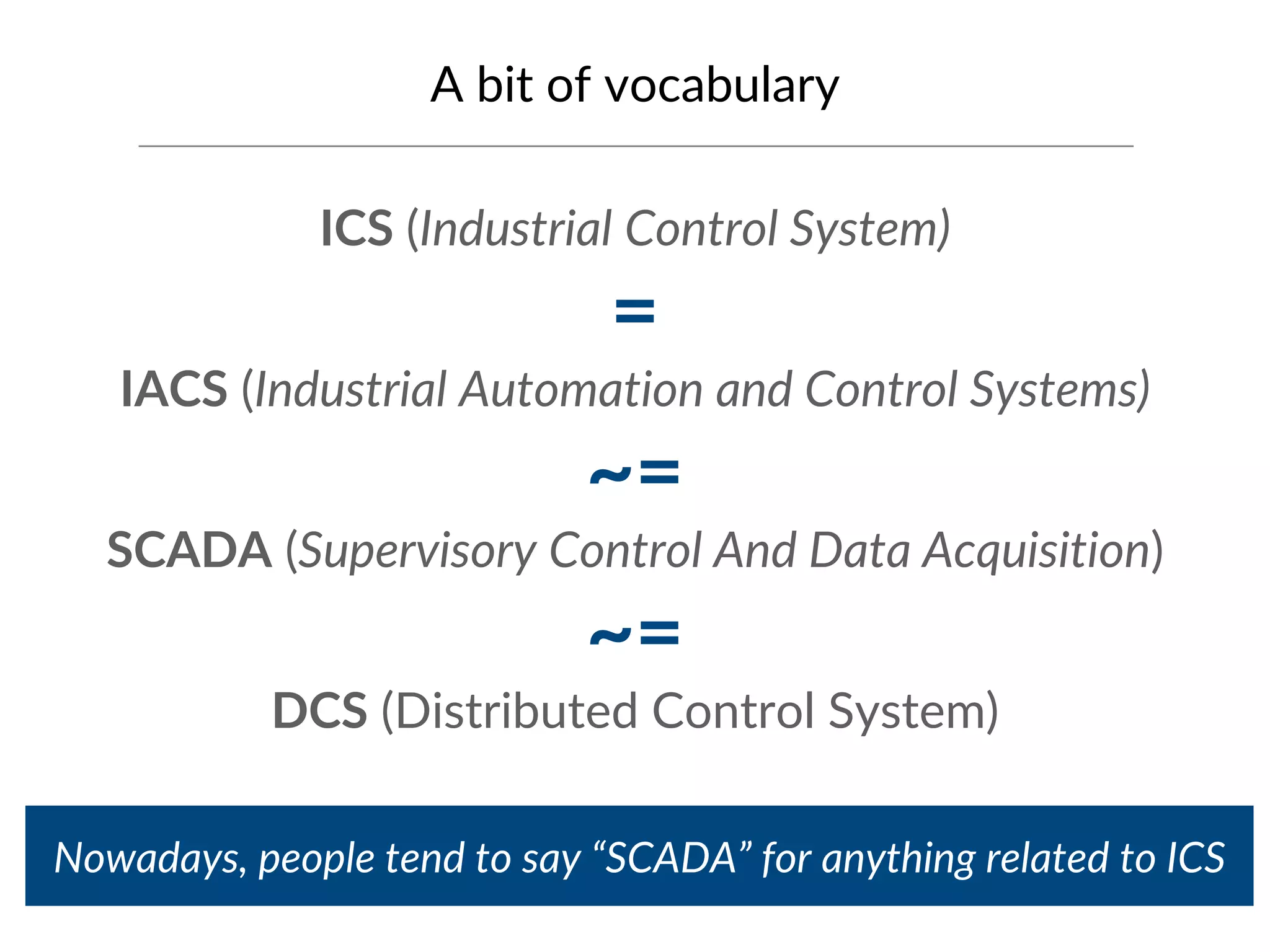
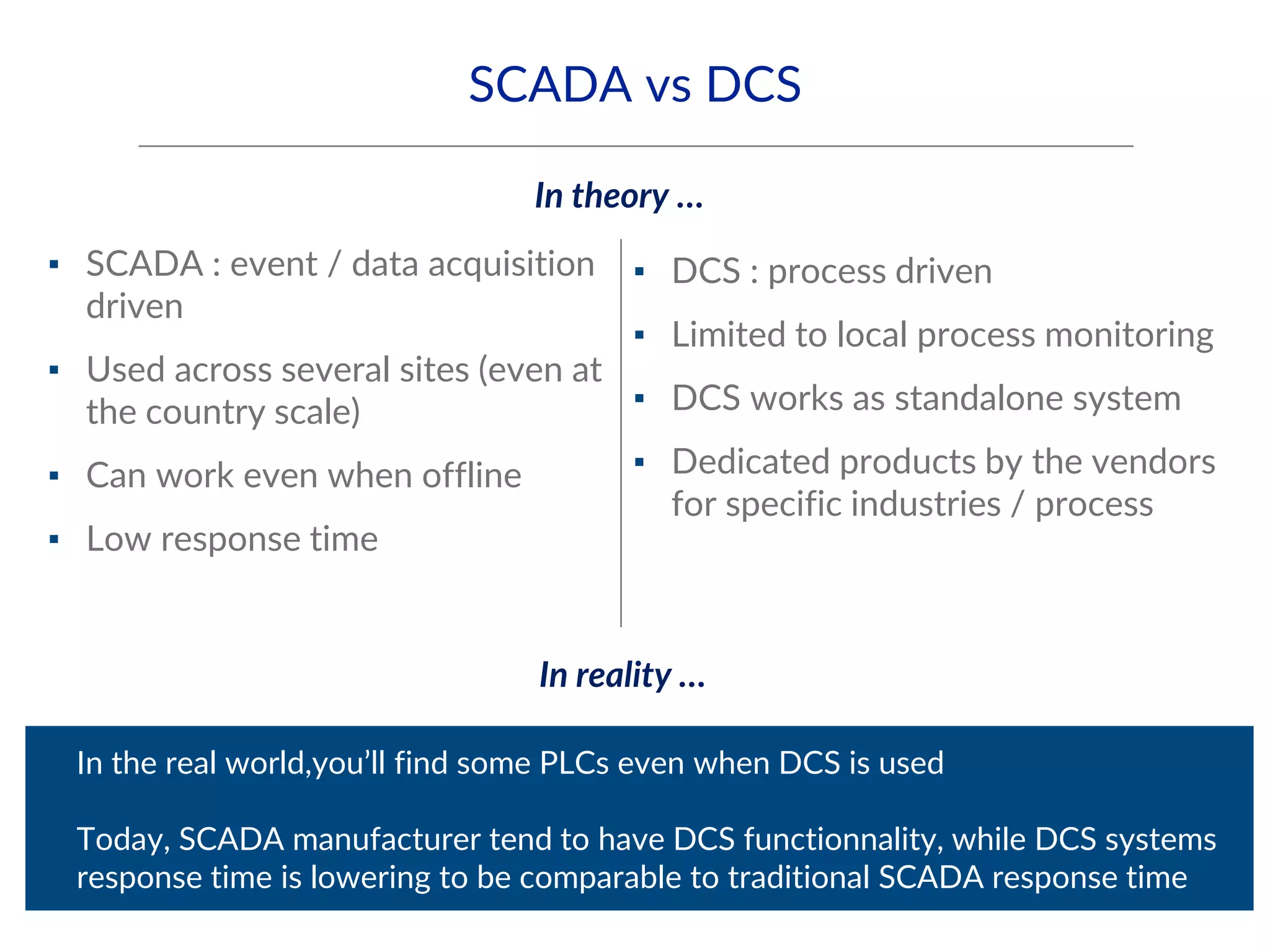
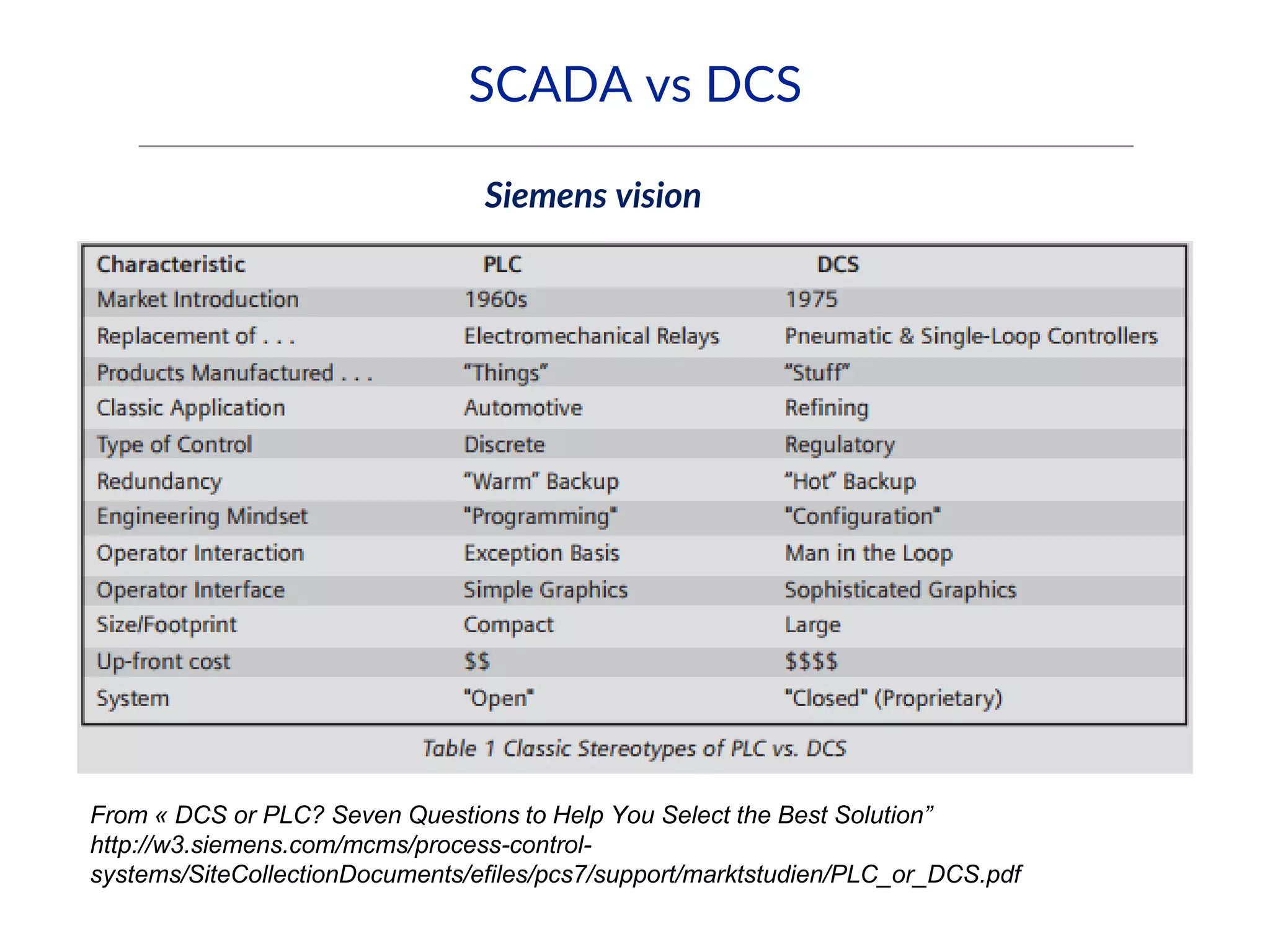
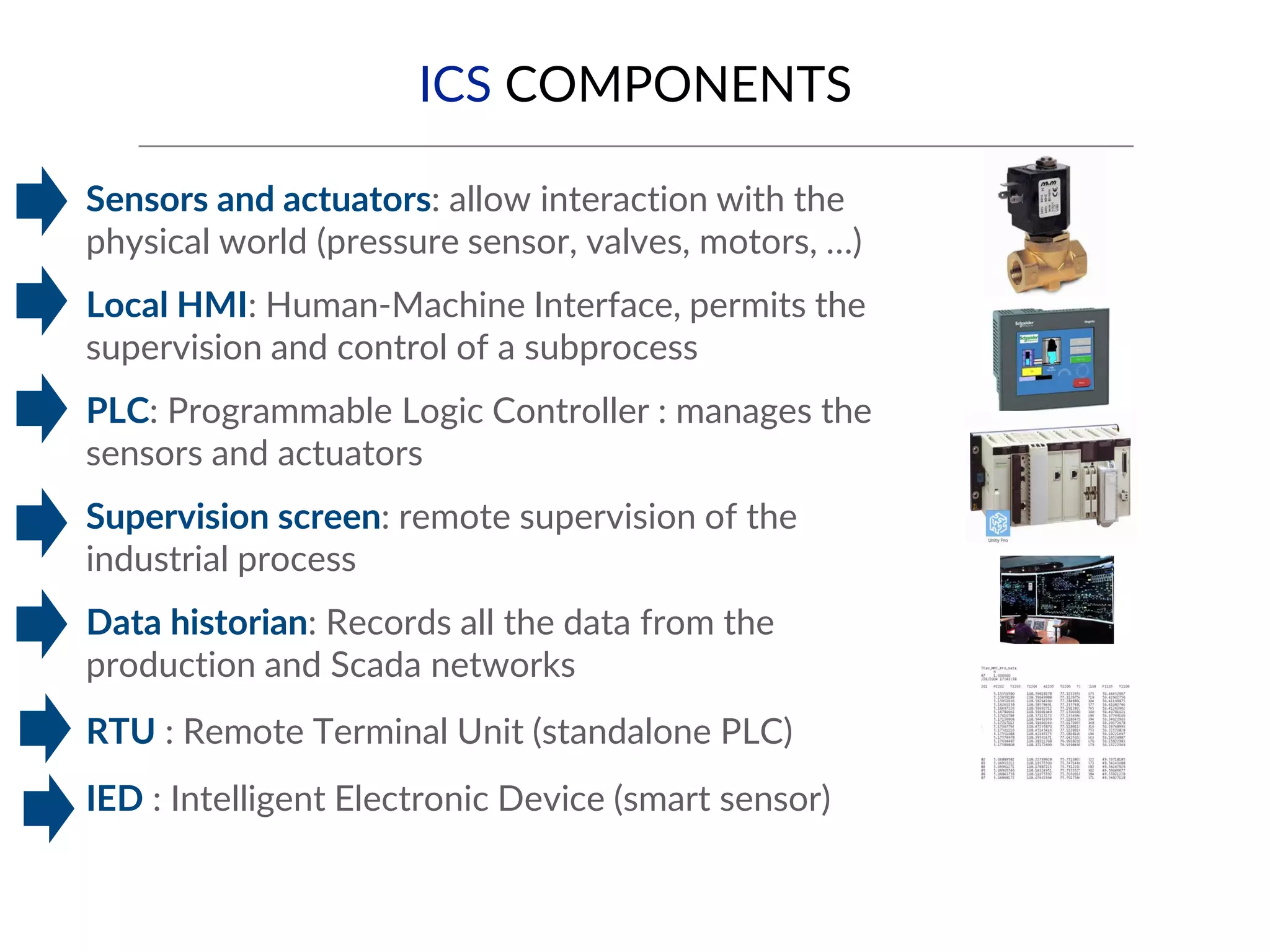
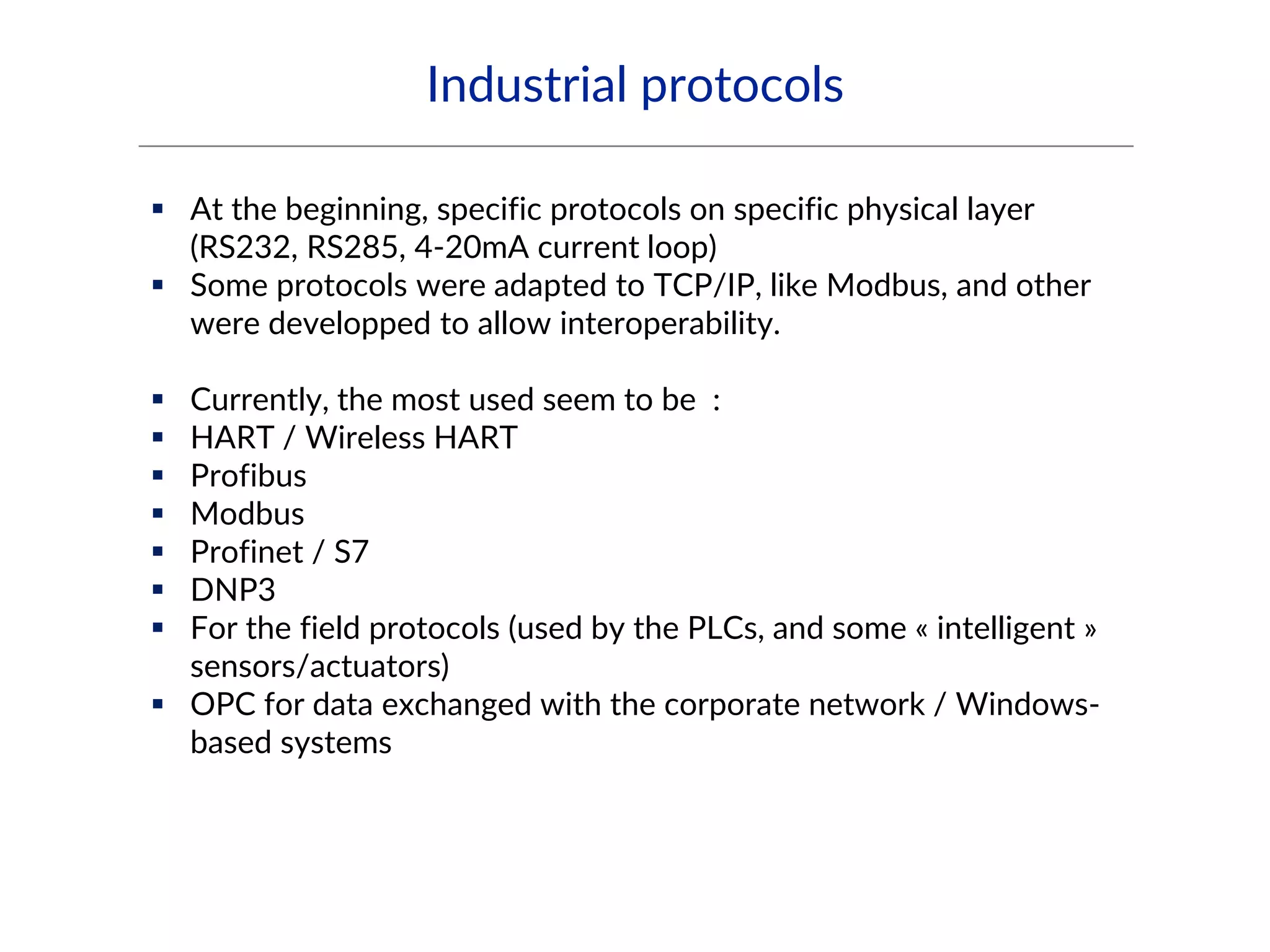
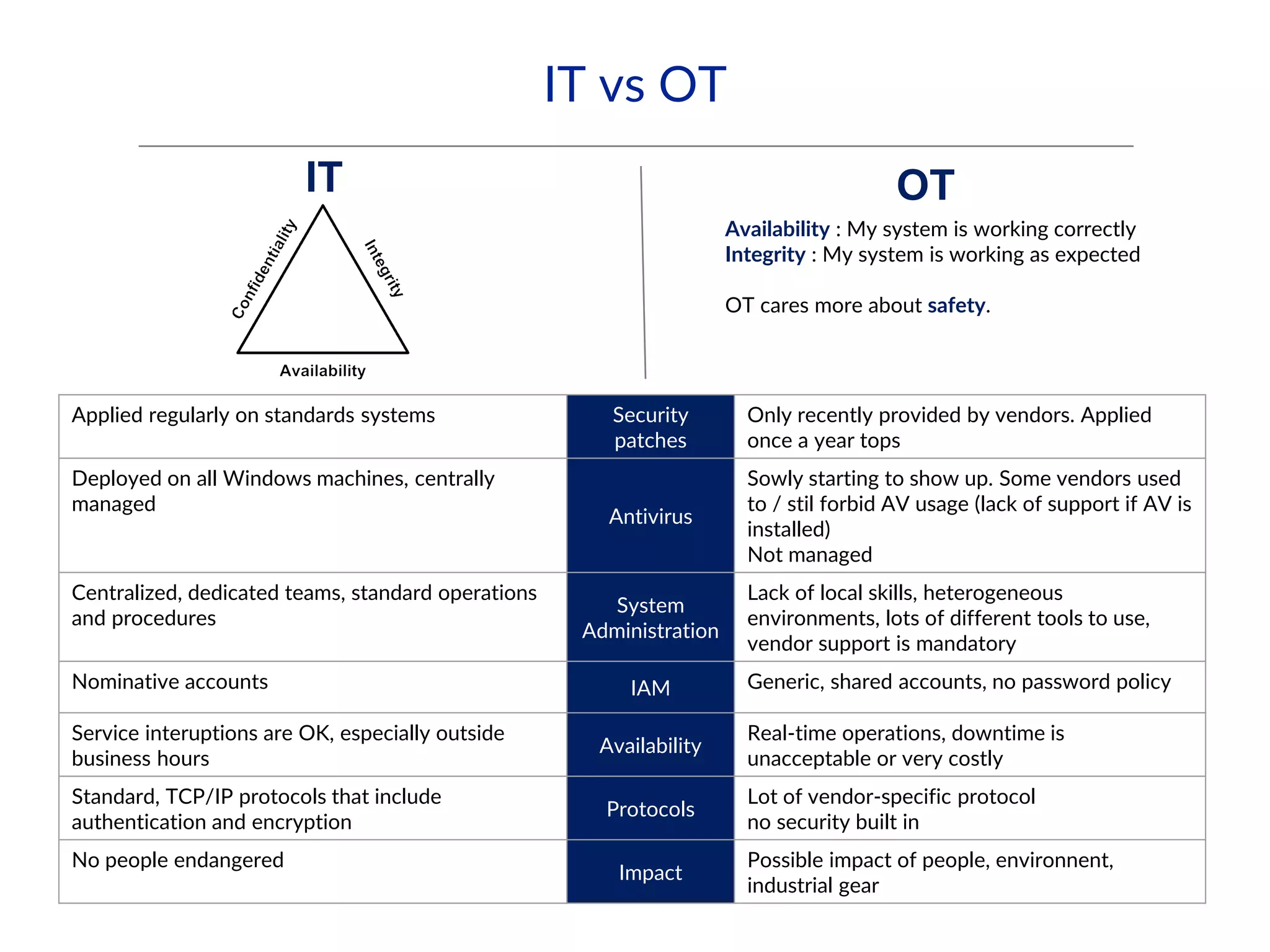
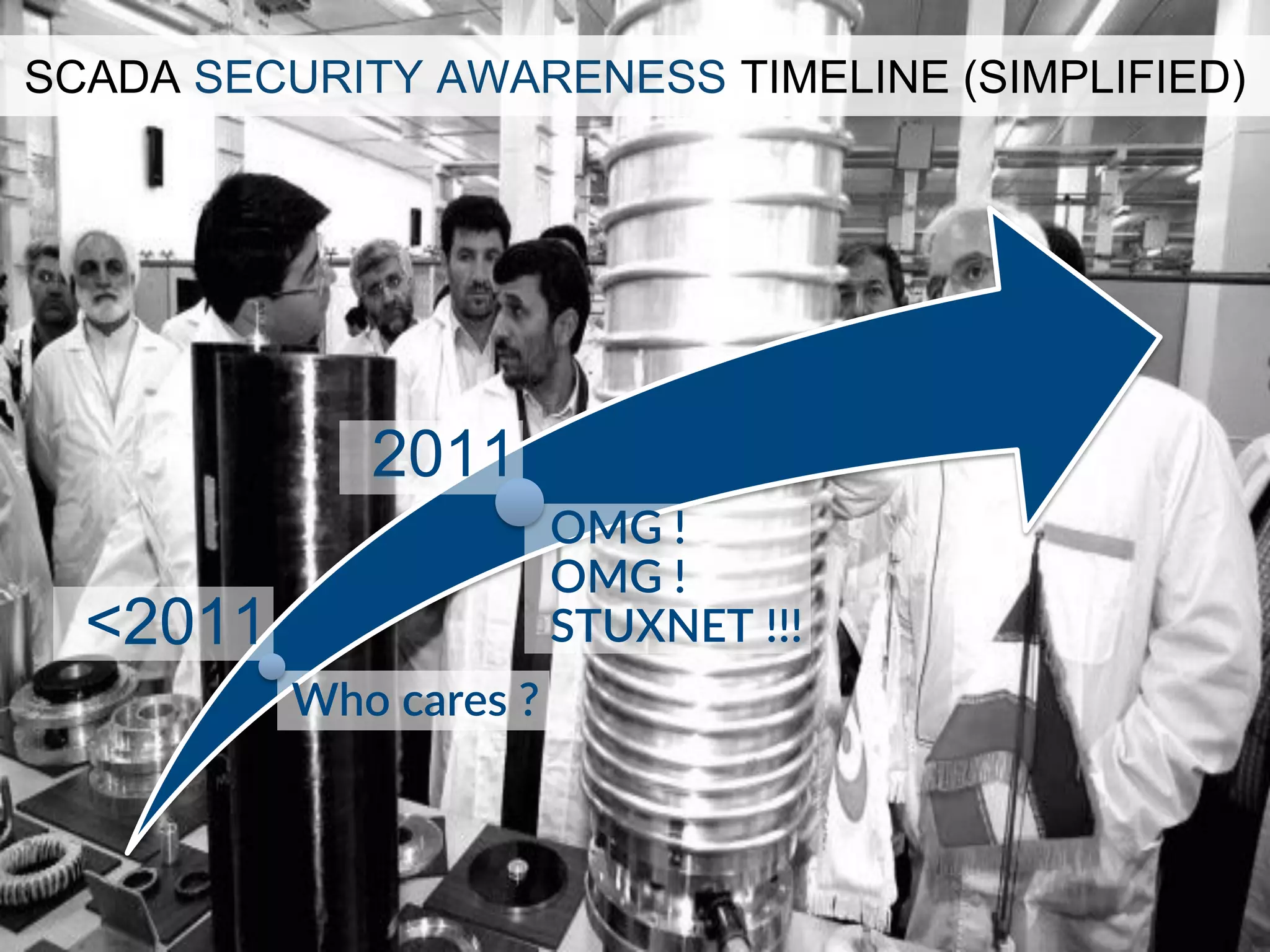
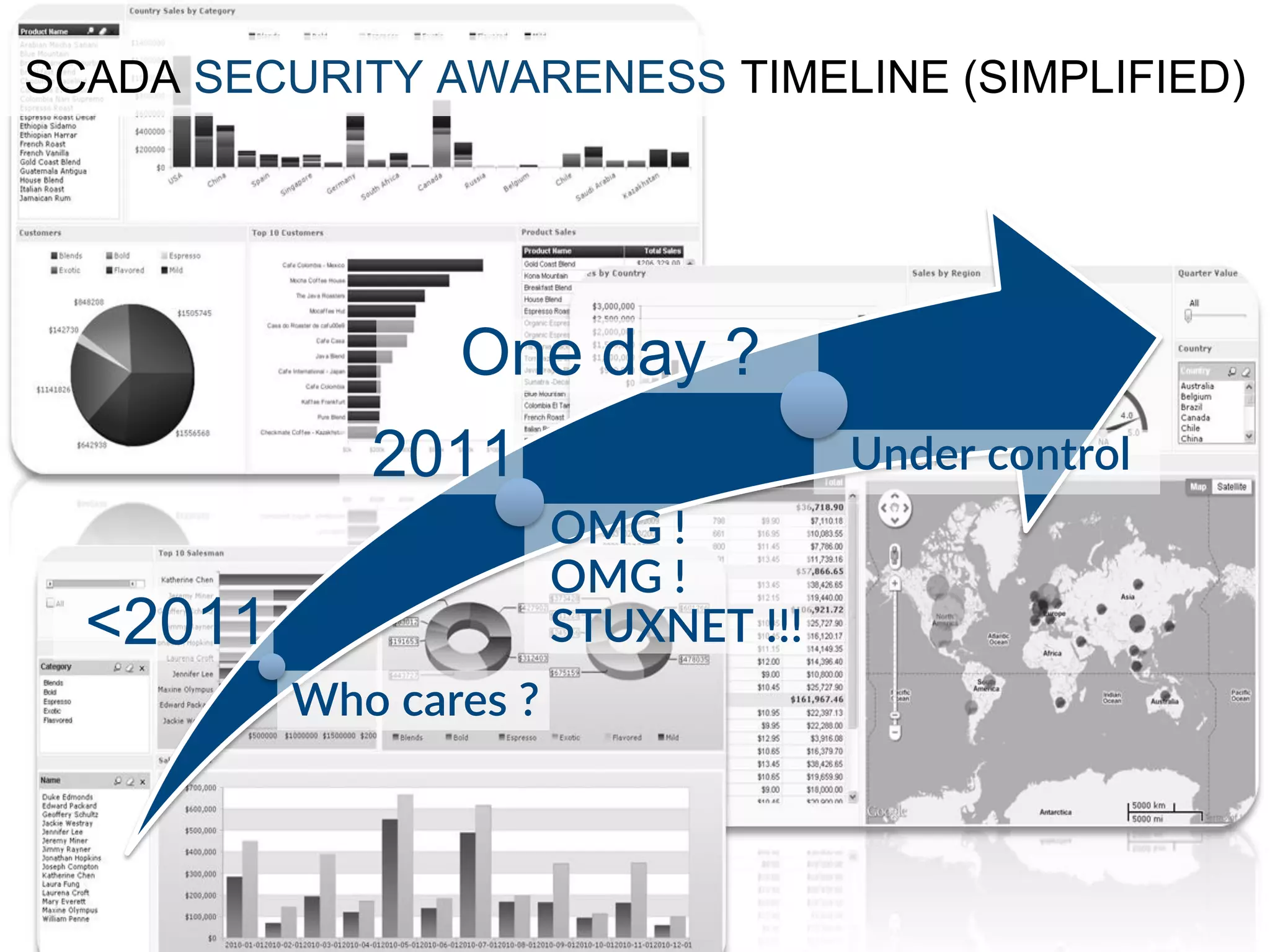
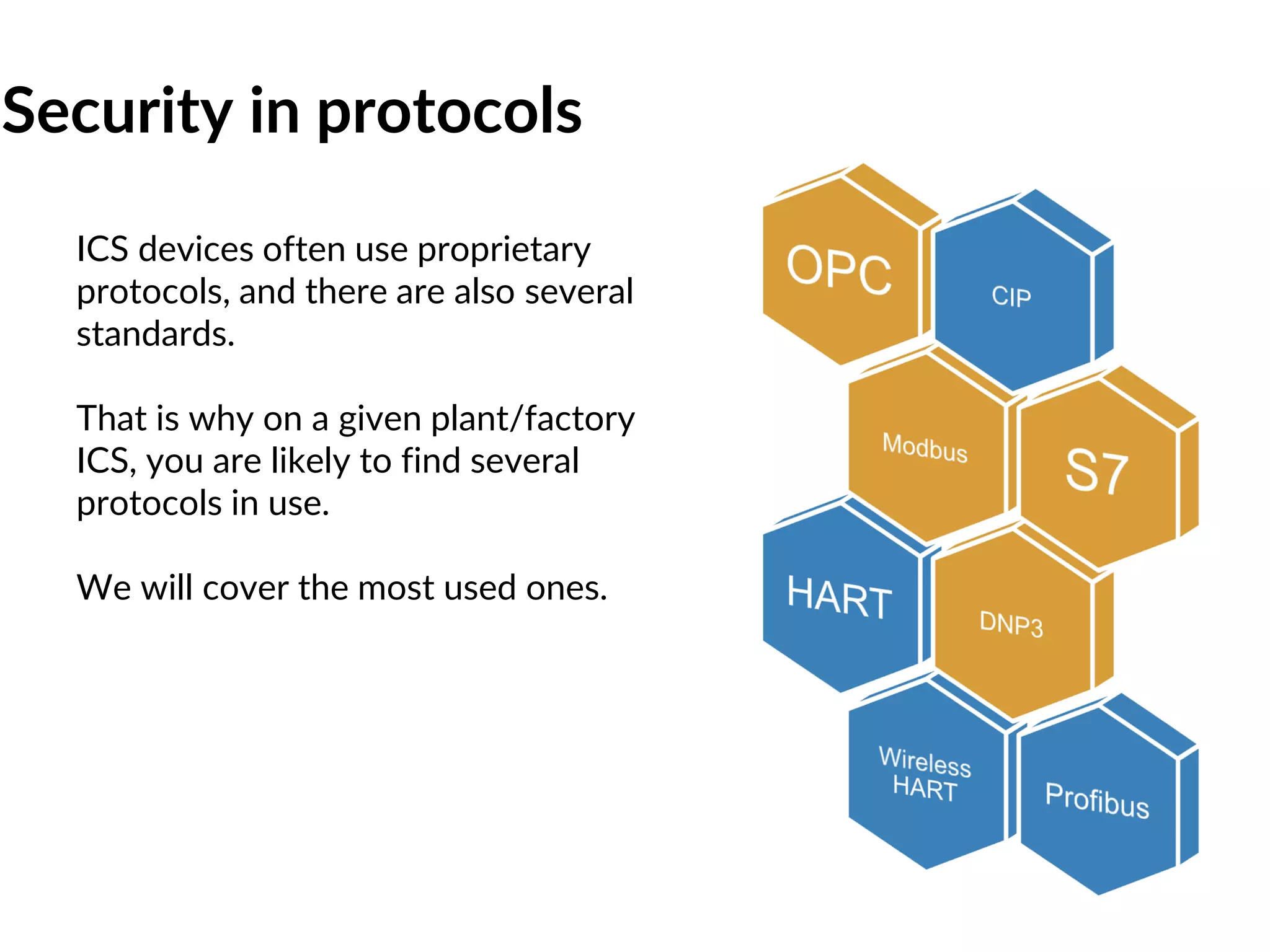
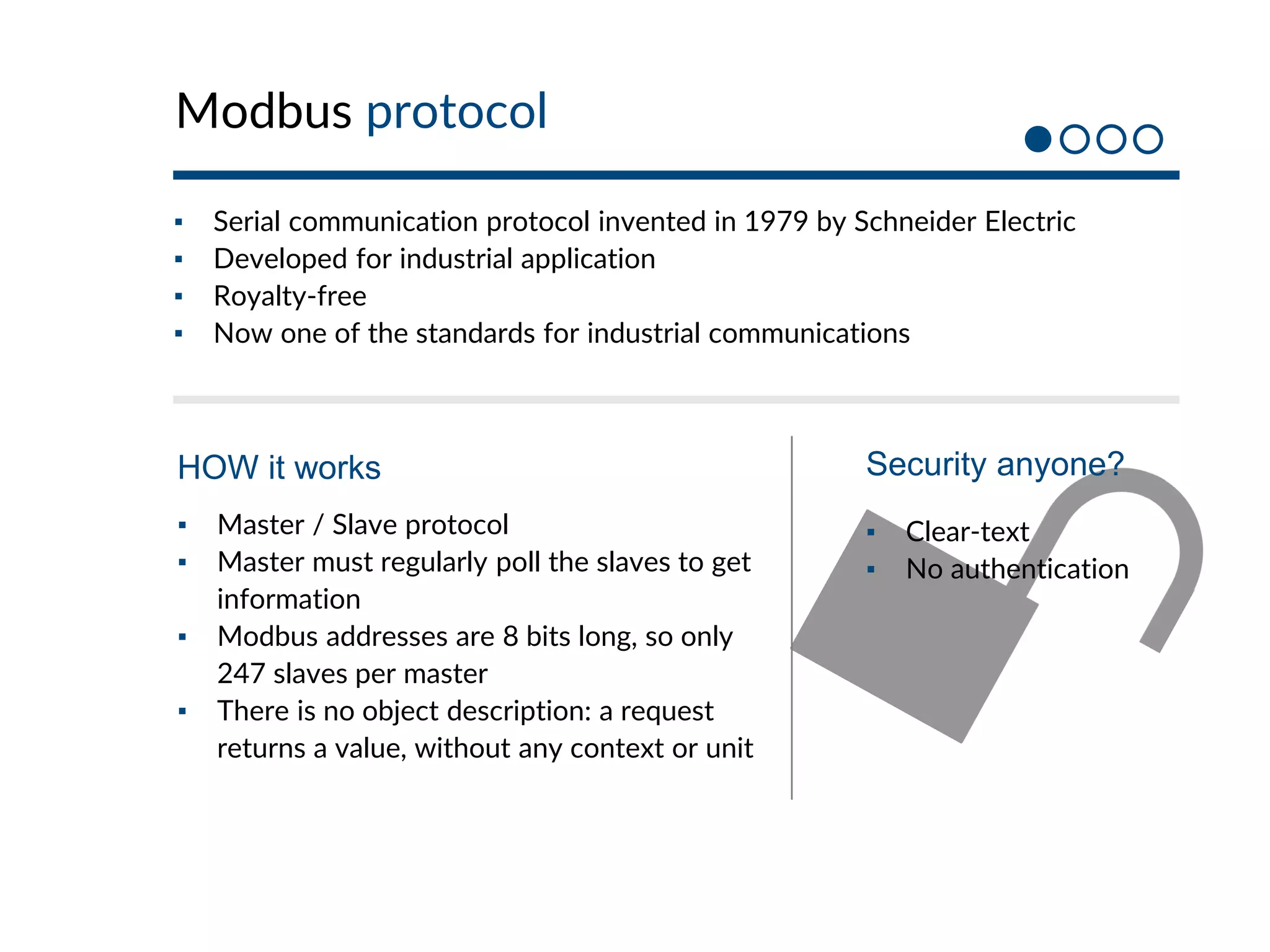
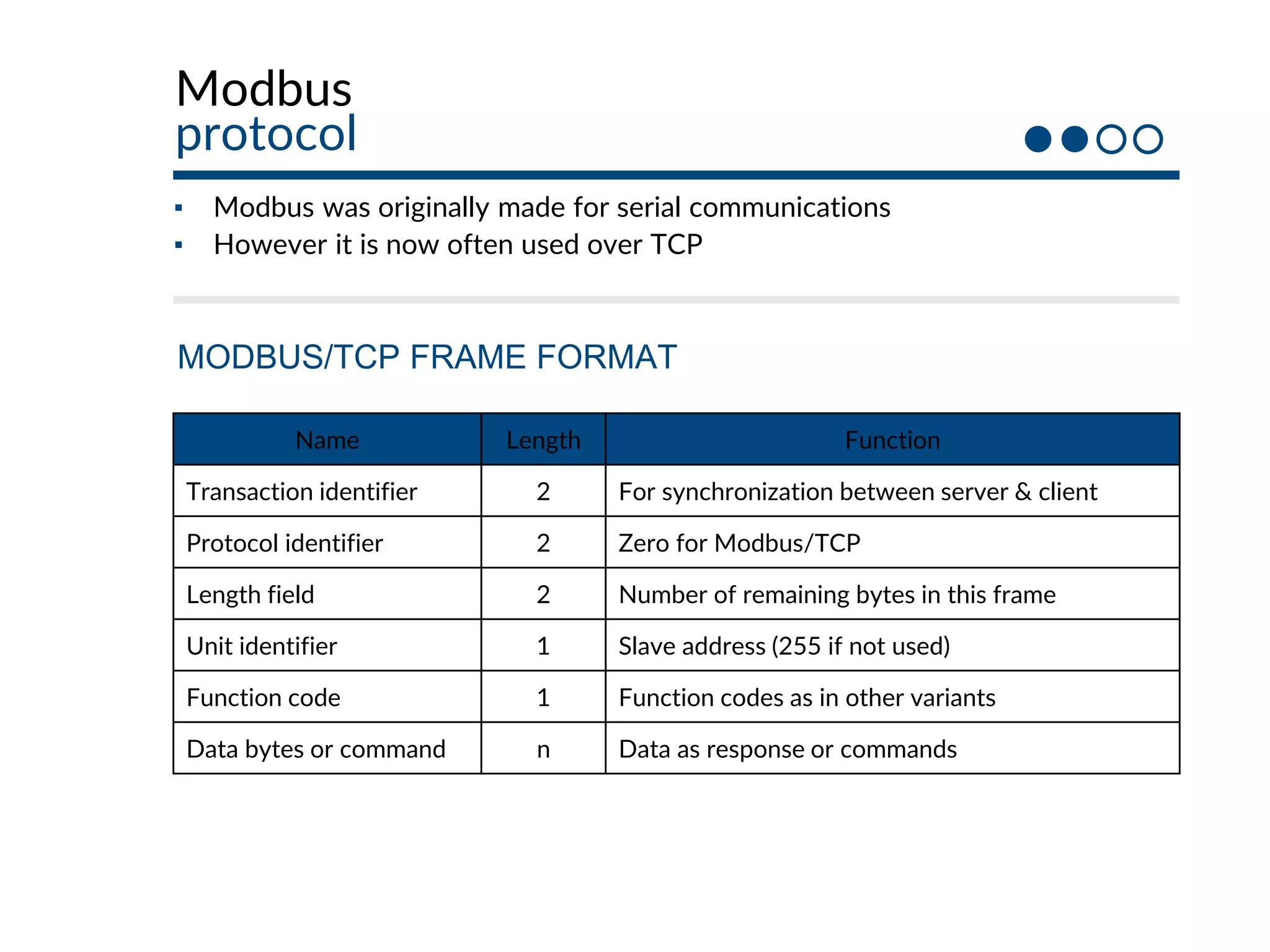
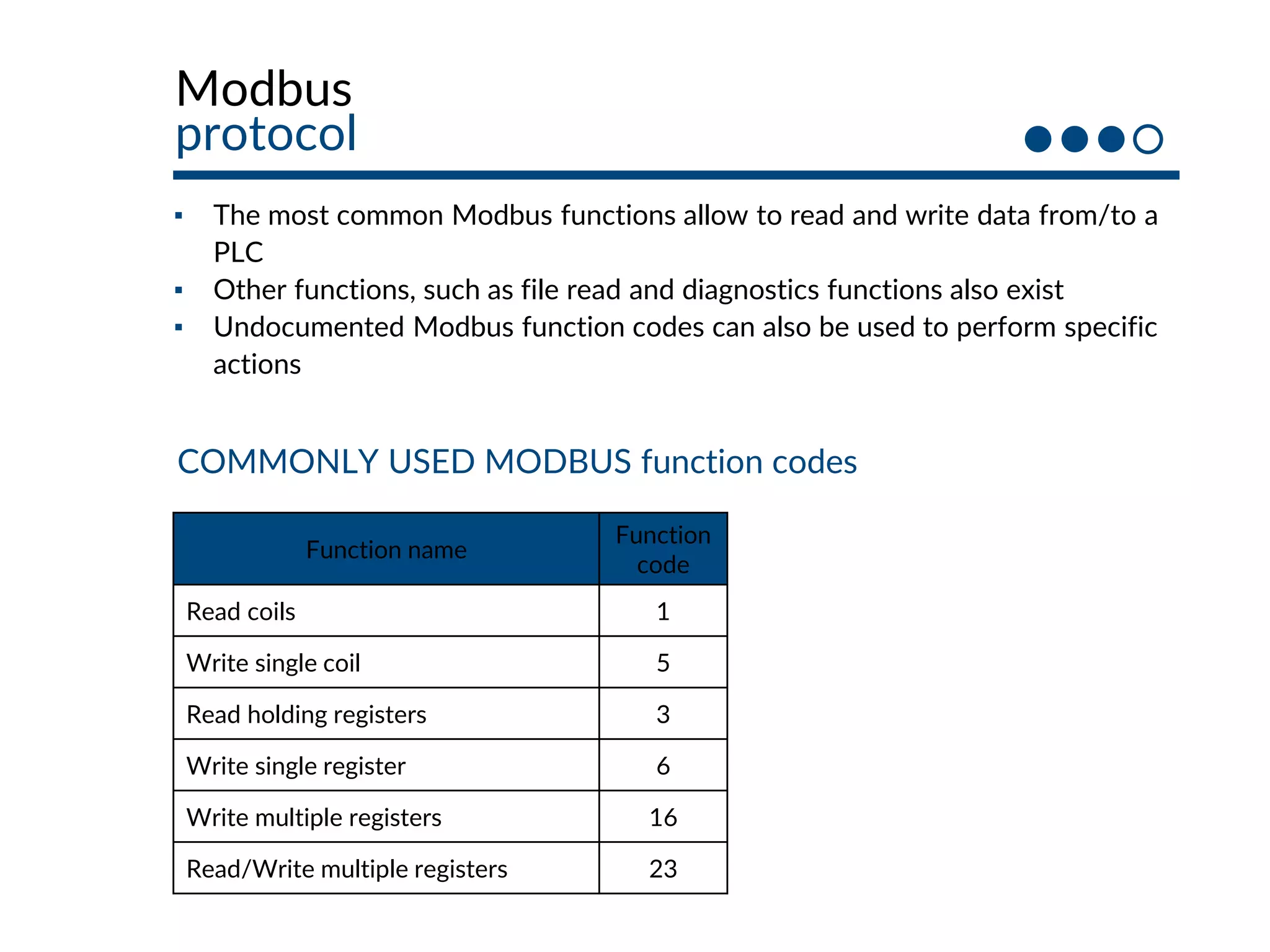
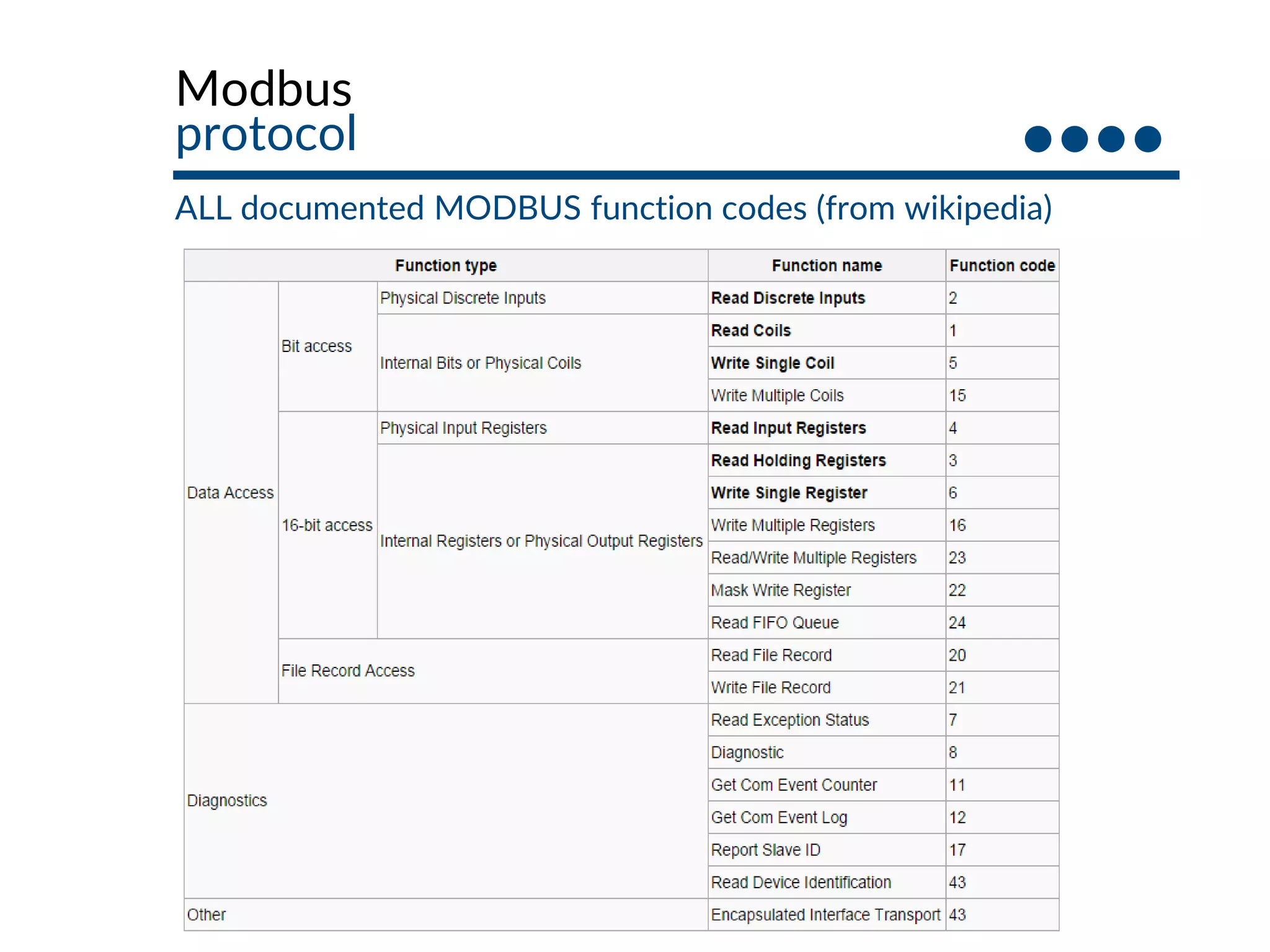
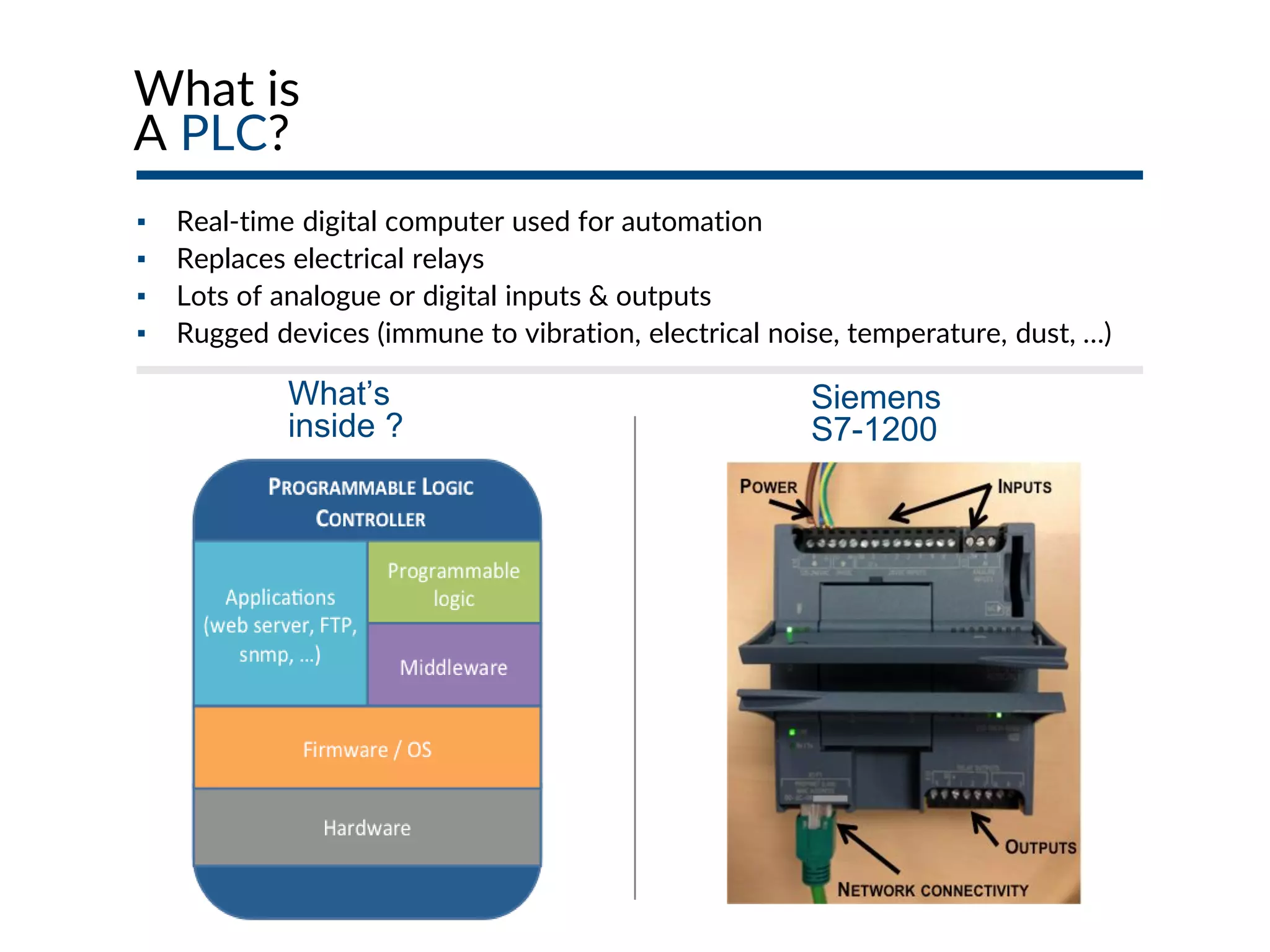
This document provides an overview of industrial control systems (ICS) and SCADA security. It introduces the speakers and defines key ICS terminology. It discusses the evolution of ICS and protocols like Modbus and S7. It outlines ICS components and the differences between IT and OT environments. It also summarizes various tools that can be used for ICS reconnaissance and protocol interaction, and provides an agenda for hands-on lab sessions covering topics like port scanning, protocol analysis and attacks.














![PLC
programming
▪ “Ladder Logic” was the first programming language for PLC, as it mimics the
real-life circuits
▪ IEC 61131-3 defines 5 programming languages for PLCs
▪ LD: Ladder Diagram
▪ FBD: Function Block Diagram
▪ ST: Structured Text
▪ IL: Instruction List
▪ SFC: Sequential Function Chart
Ladder diagram
example
Structured text
example
(* simple state machine *)
TxtState :=
STATES[StateMachine];
CASE StateMachine OF
1: ClosingValve();
ELSE
;; BadCase();
END_CASE;
LD Speed
GT 1000
JMPCN VOLTS_OK
LD Volts
VOLTS_OK LD 1
ST %Q75
Instruction list
example](https://image.slidesharecdn.com/brucon2015-pentestingics101-v1-151018085458-lva1-app6892/75/BruCON-2015-Pentesting-ICS-101-41-2048.jpg)