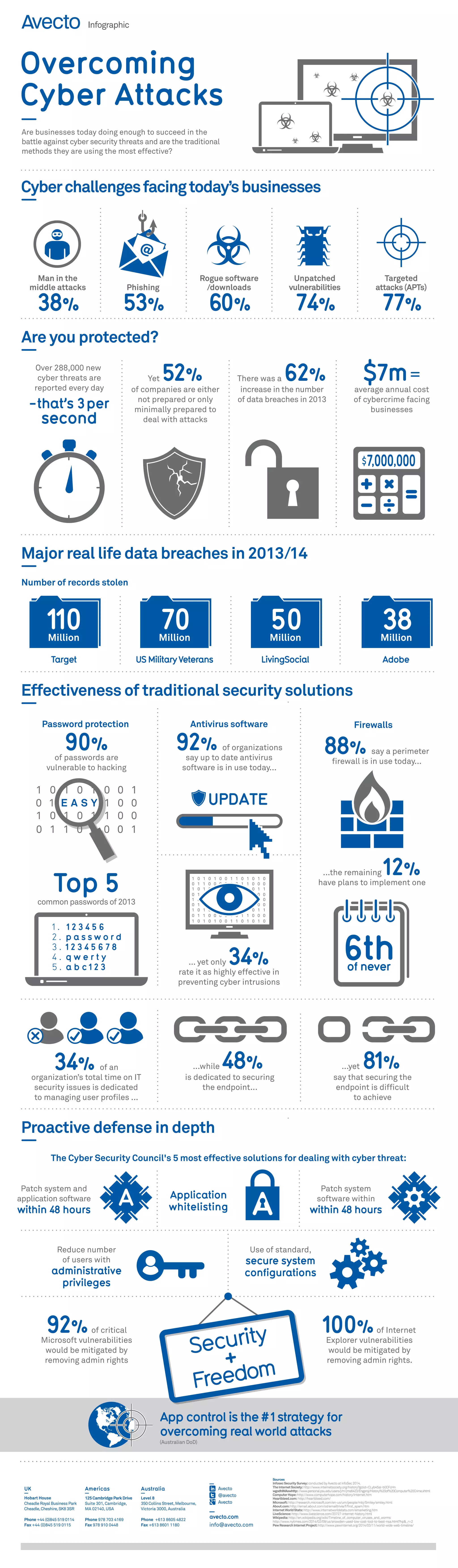
The document discusses the rising costs and challenges of cybercrime faced by businesses, highlighting that 81% of organizations feel unprepared for cyber attacks despite 92% claiming to use updated antivirus software. Key statistics include the effectiveness of traditional security measures and the prevalence of password vulnerabilities. Recommendations include proactive defense strategies such as application whitelisting and reducing administrative privileges to enhance security.