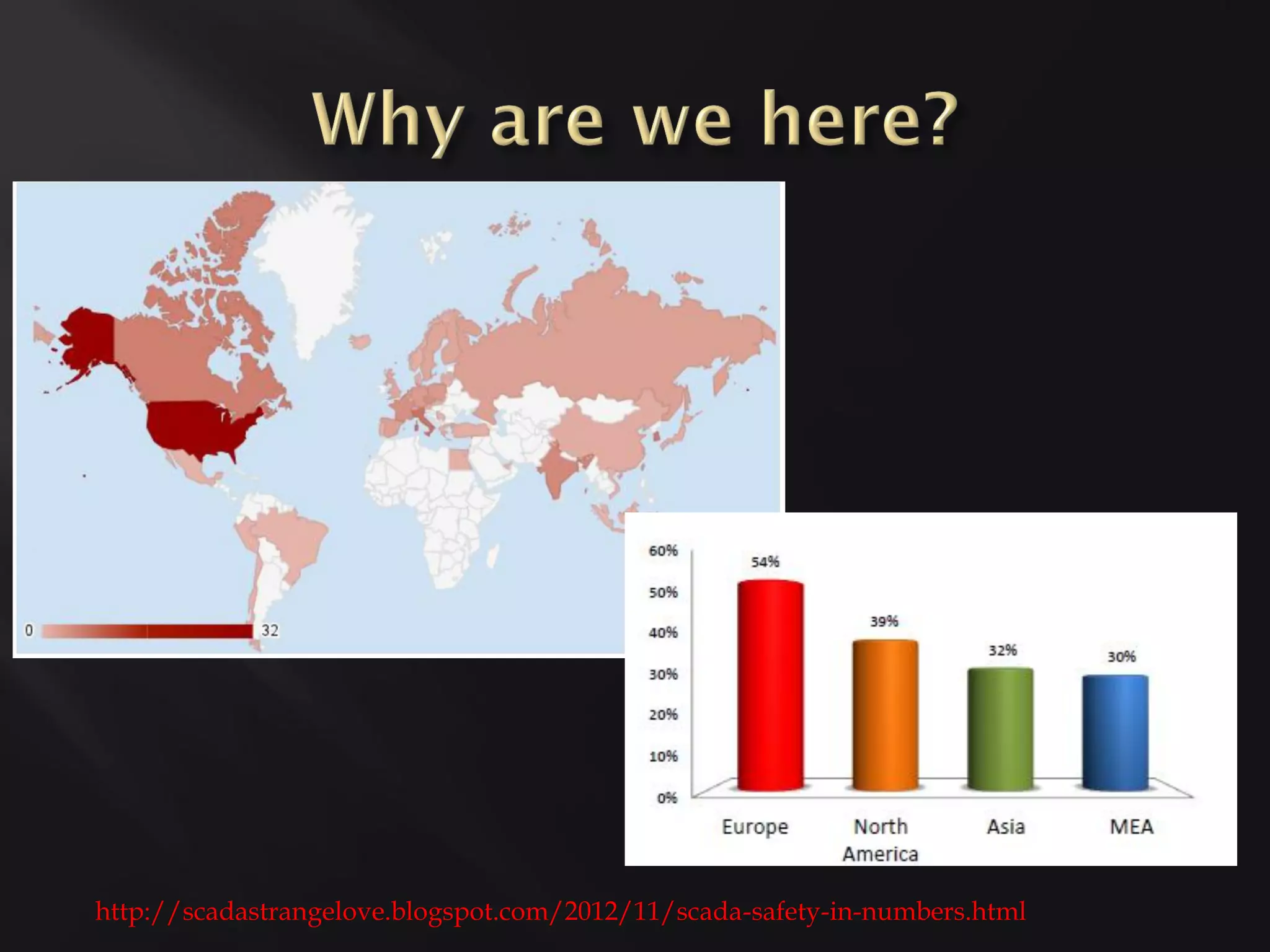
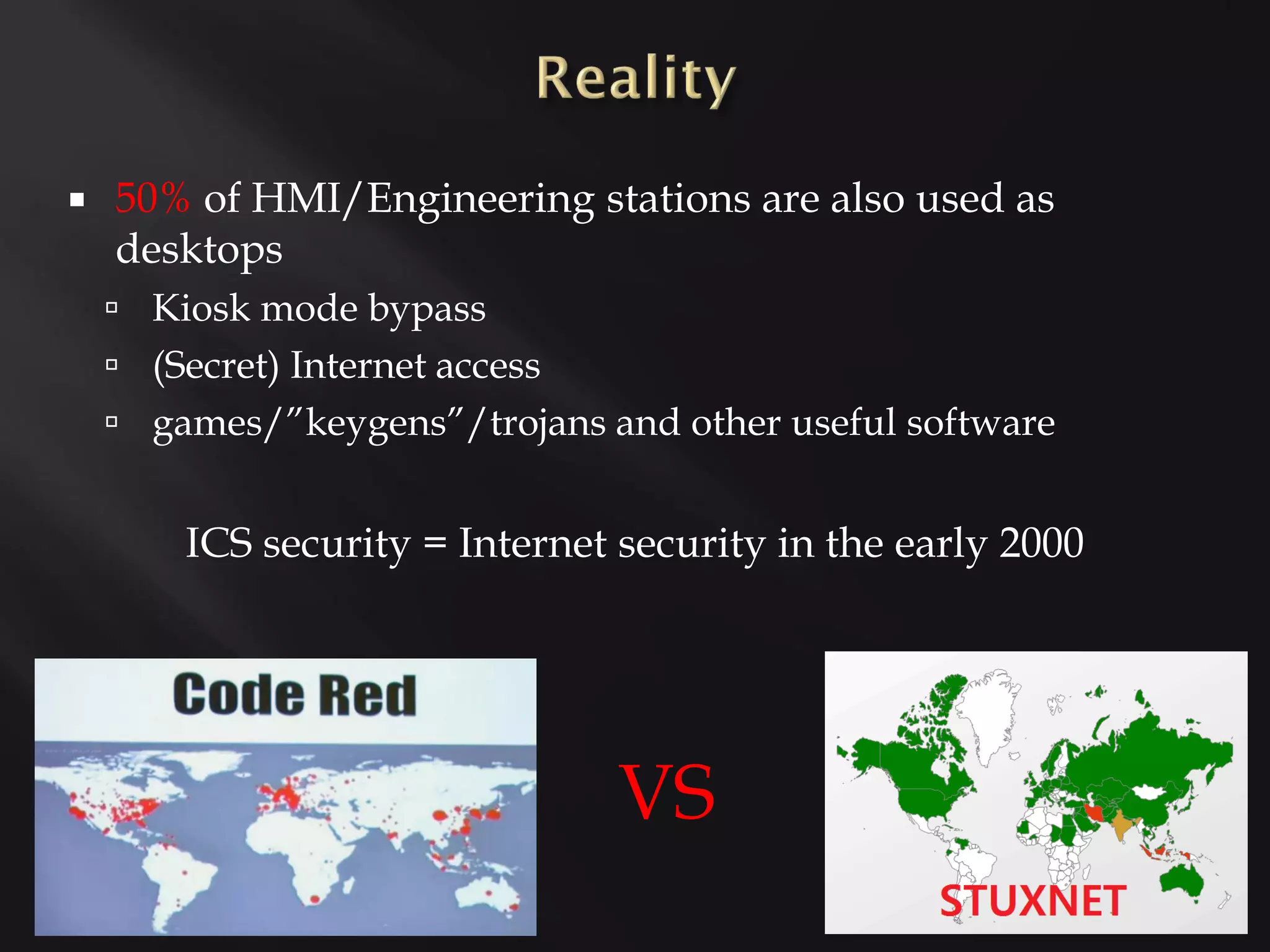
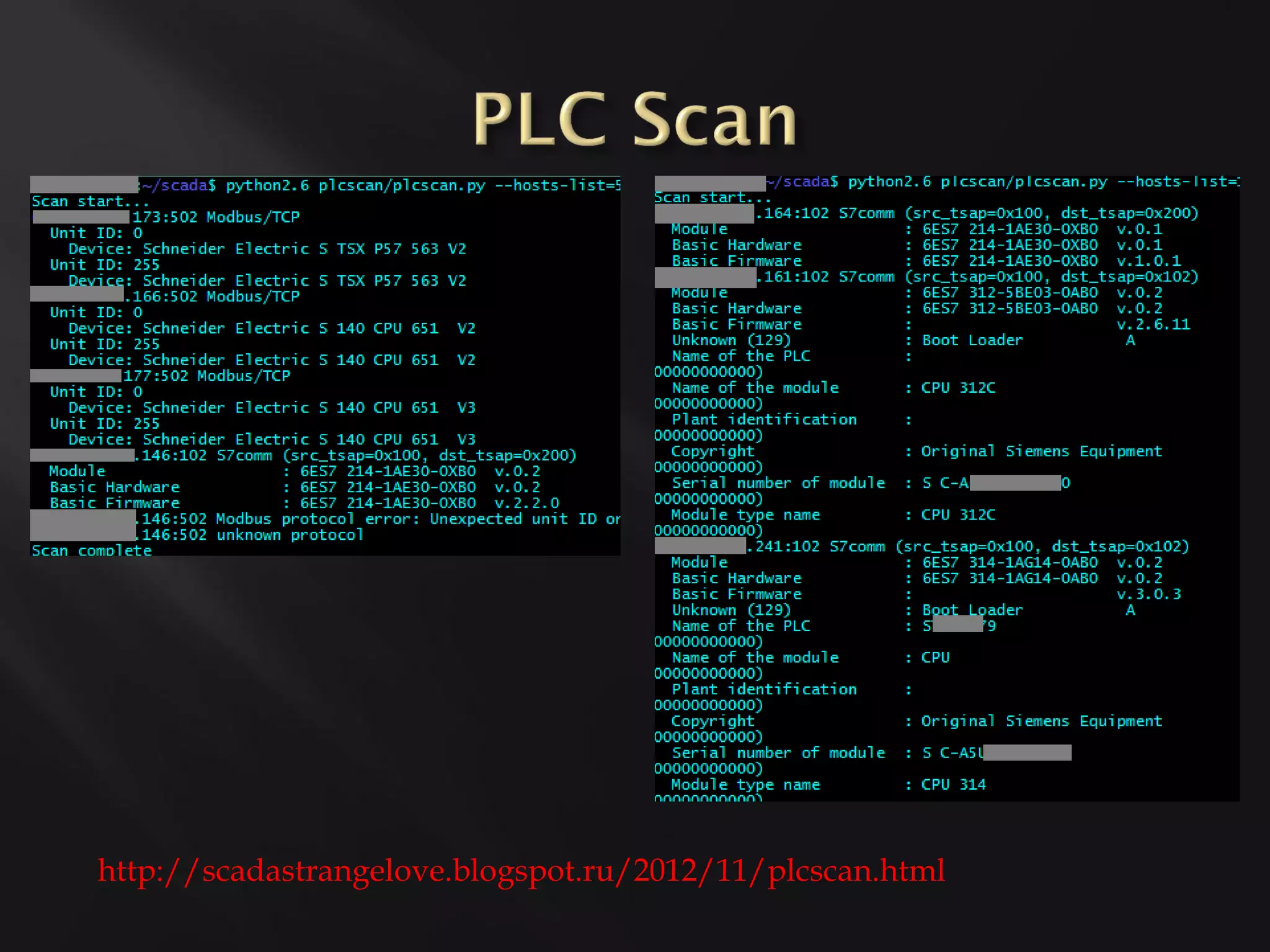
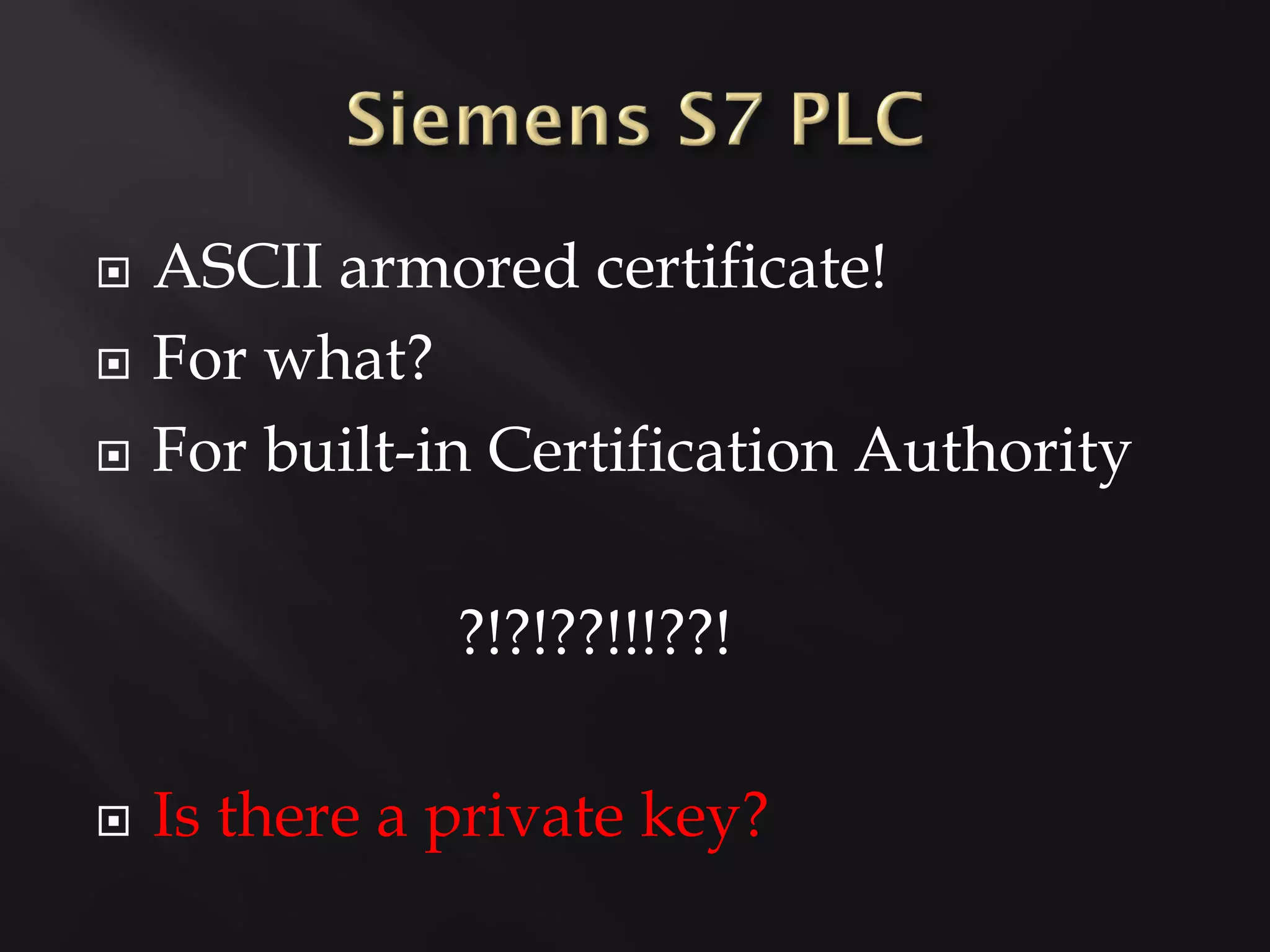
This document profiles several security researchers focused on industrial control systems:
- Sergey Gordeychik is the CTO of Positive Technologies and director of Positive Hack Days, focusing on ICS/SCADA security research.
- Gleb Gritsai and Denis Baranov are researchers at Positive Technologies working on network security, forensics, and challenges related to ICS/SCADA systems.
- The group collaborates to research vulnerabilities in common ICS/SCADA platforms like Siemens, Rockwell, Schneider Electric to help secure critical infrastructure systems from cyber attacks.