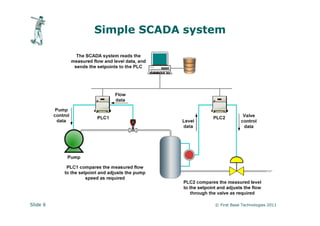
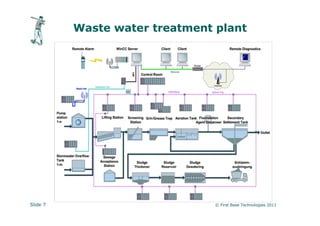
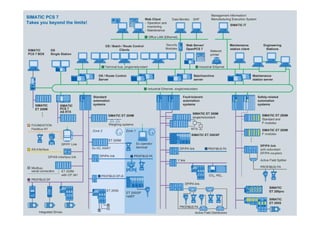
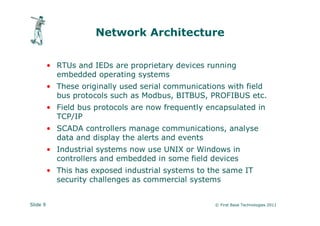
The document discusses vulnerabilities in critical systems, particularly industrial control systems (ICS), and the challenges they face due to outdated security practices and protocols. It highlights the risks posed by inadequate authentication, insecure communication protocols, and poor network segmentation, as well as the catastrophic consequences of improper security testing. The presentation emphasizes the need for thorough audits and careful manual inspections over conventional penetration testing to mitigate these risks.