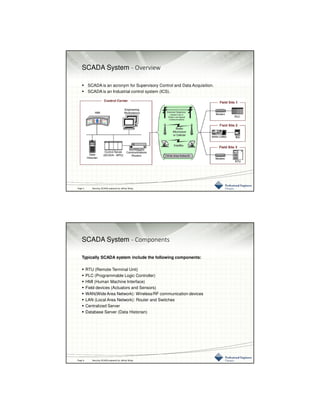
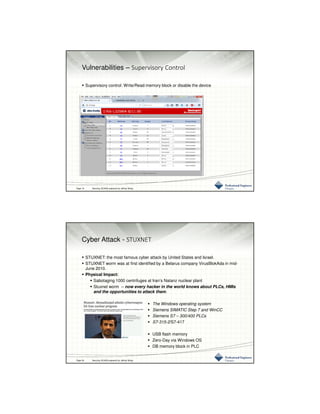
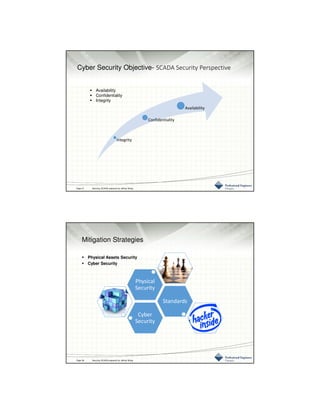
This document provides an overview of SCADA (Supervisory Control and Data Acquisition) security challenges and strategies. It describes common SCADA system components and functionality. It then discusses increasing cyber threats to SCADA systems from sources like hostile governments and employees. The document outlines various physical and cyber vulnerabilities in SCADA systems and components. It recommends security standards from organizations like NIST, ISA, and NERC to help mitigate risks. The document also provides guidelines on physical asset security and cybersecurity strategies.