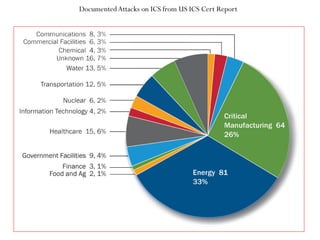
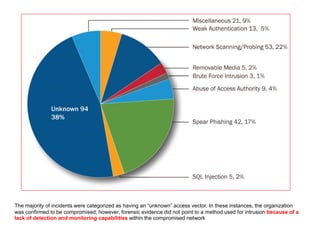
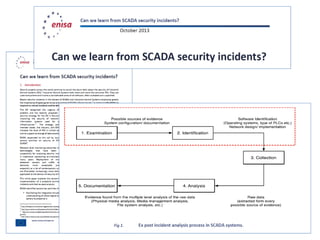
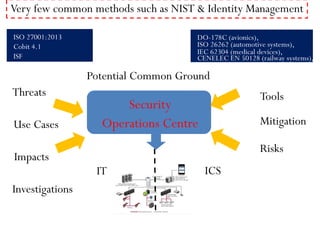
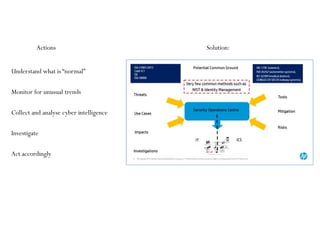
This document summarizes a presentation on cyber security in real-time systems. It discusses threats to industrial control systems and SCADA systems, and the differences between traditional IT and industrial control system cultures. It provides examples of attacks on industrial control systems and poor monitoring of SCADA systems. It suggests that security operations centers may provide common ground between IT and ICS. Finally, it discusses recent media reports relating to hacking of rail signaling systems and aircraft systems.