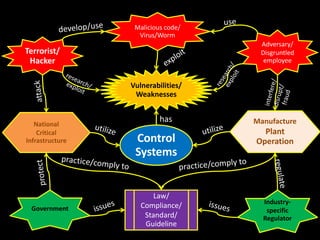
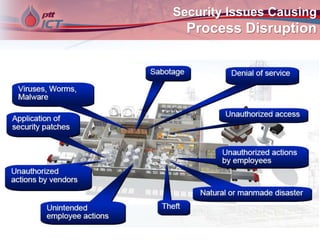
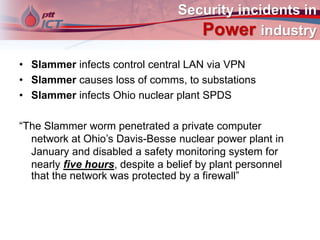
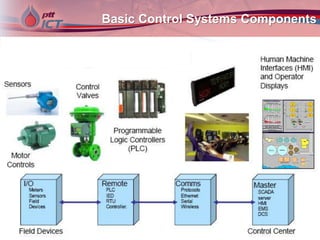
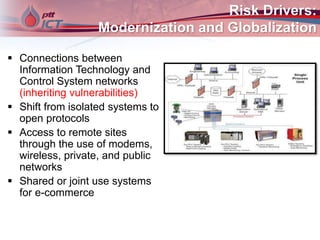
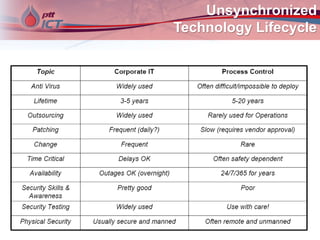
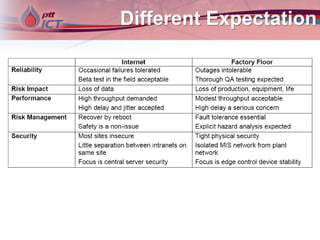
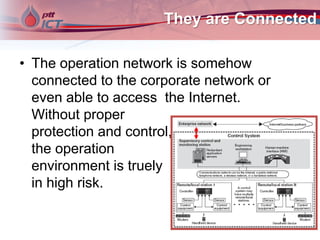
Cyber attacks on industrial control systems pose a serious threat. Several incidents around the world have shown that critical infrastructure systems controlling functions like power grids and water treatment have been hacked, in some cases shutting down safety monitoring systems. These control systems were not designed with security in mind and connecting them to corporate networks and the internet has increased vulnerabilities. Stronger security measures are needed to protect against growing cyber threats.






![Transportation – Road Signs
8
Lessons learned:
Use robust physical access
controls
Change all default passwords
Work with manufacturers to
identify and protect password
reset procedures
Event: Jan 2009, Texas road
signs compromised
Impact: Motorists distracted and
provided false information
Specifics: Some commercial road
signs can be easily altered because
their instrument panels are frequently
left unlocked and their default
passwords are not changed.
"Programming is as simple as
scrolling down the menu selection," a
blog reports. "Type whatever you want
to display … In all likelihood, the crew
will not have changed [the password]."](https://image.slidesharecdn.com/scada-securitycdic2009th-1270321397-phpapp02/85/SCADA-Security-in-CDIC-2009-8-320.jpg)