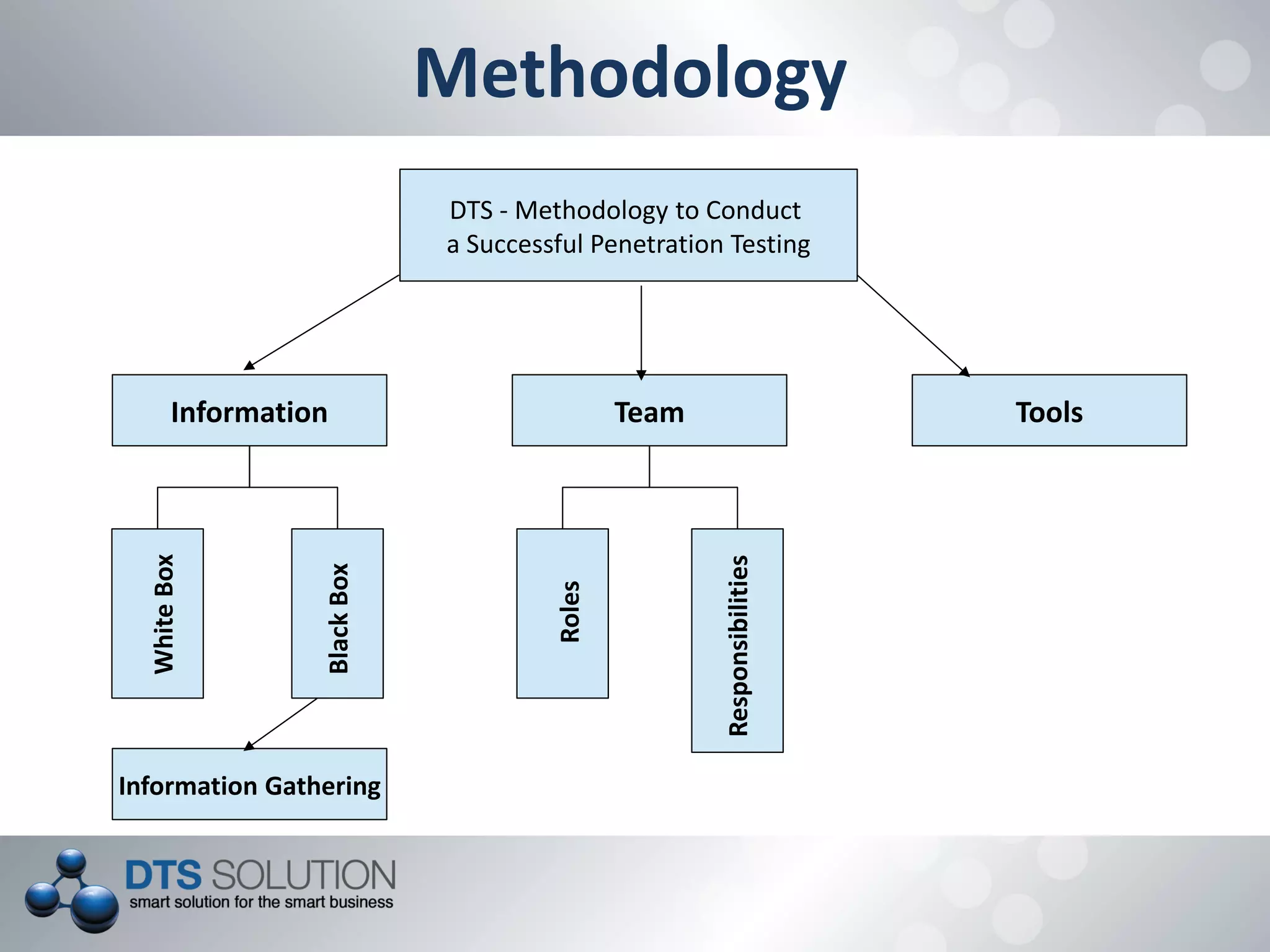
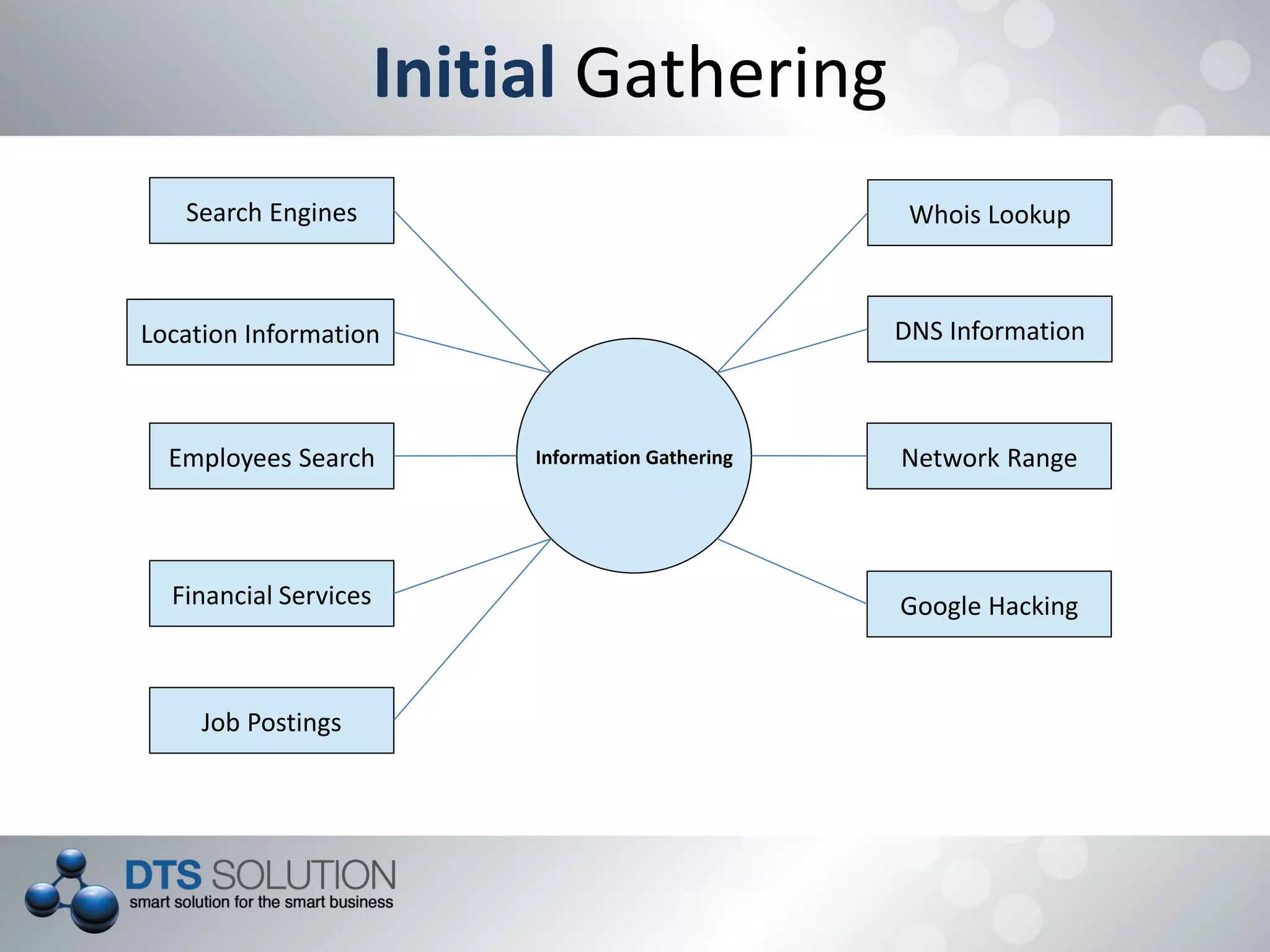
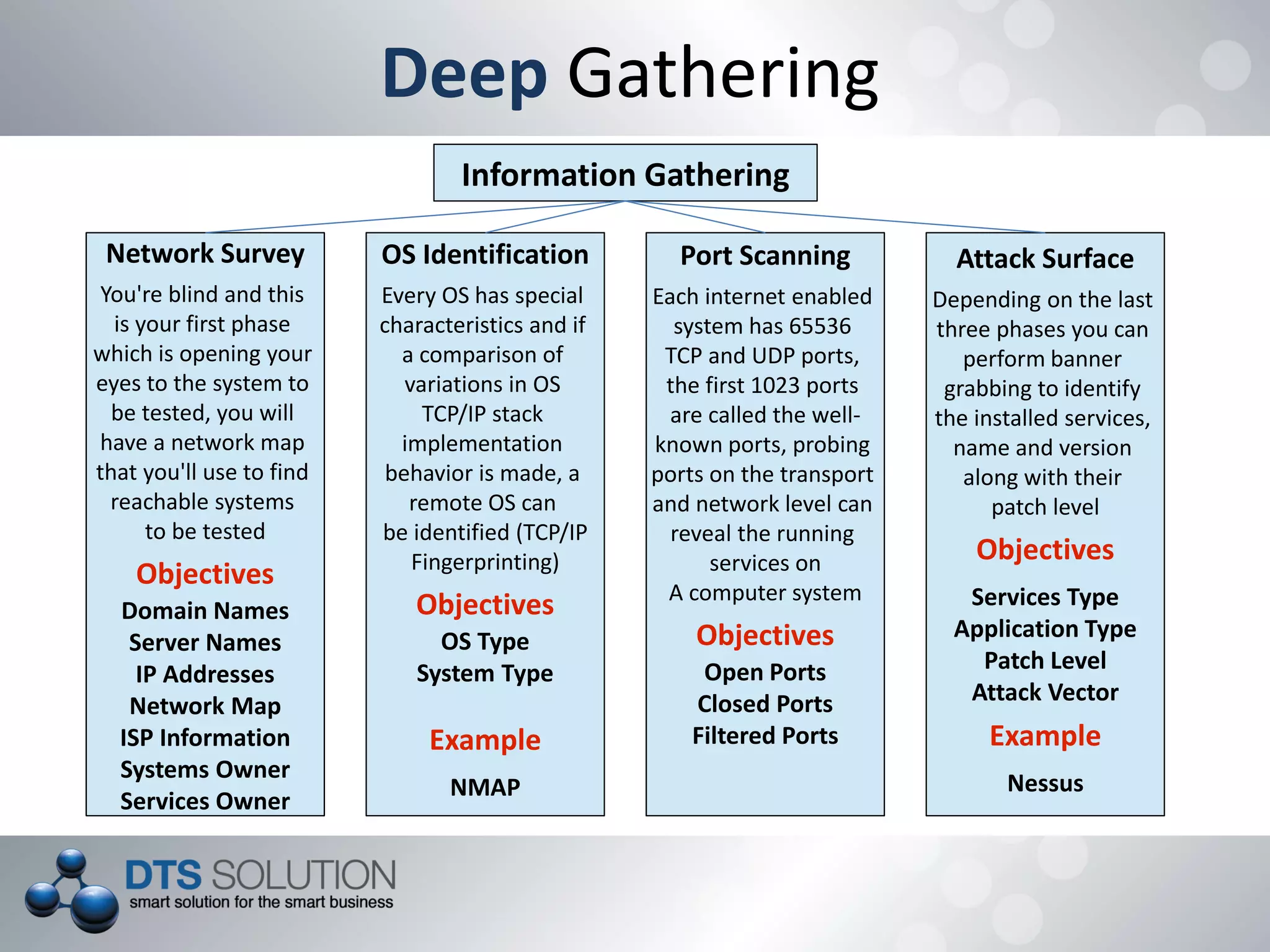
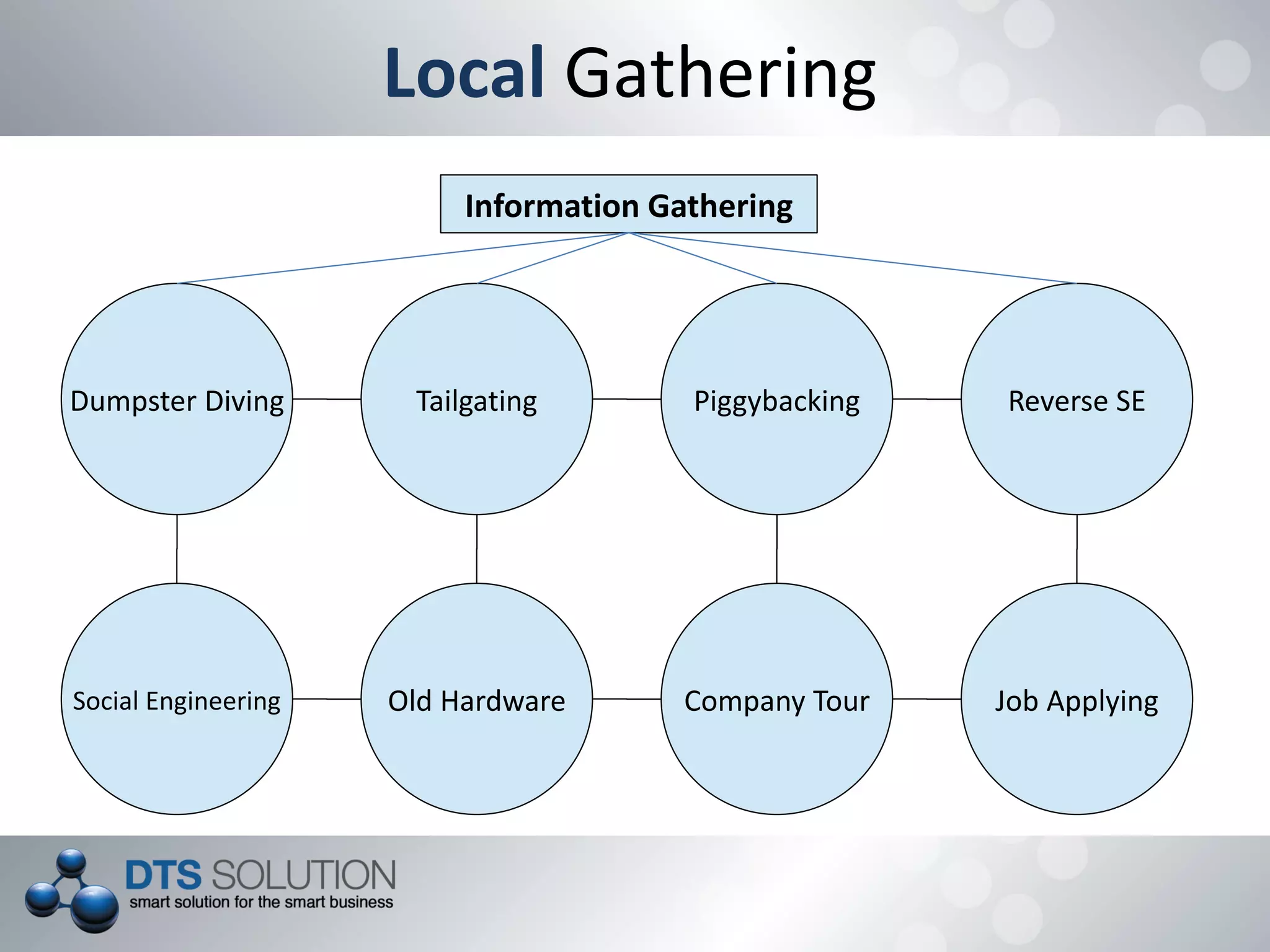
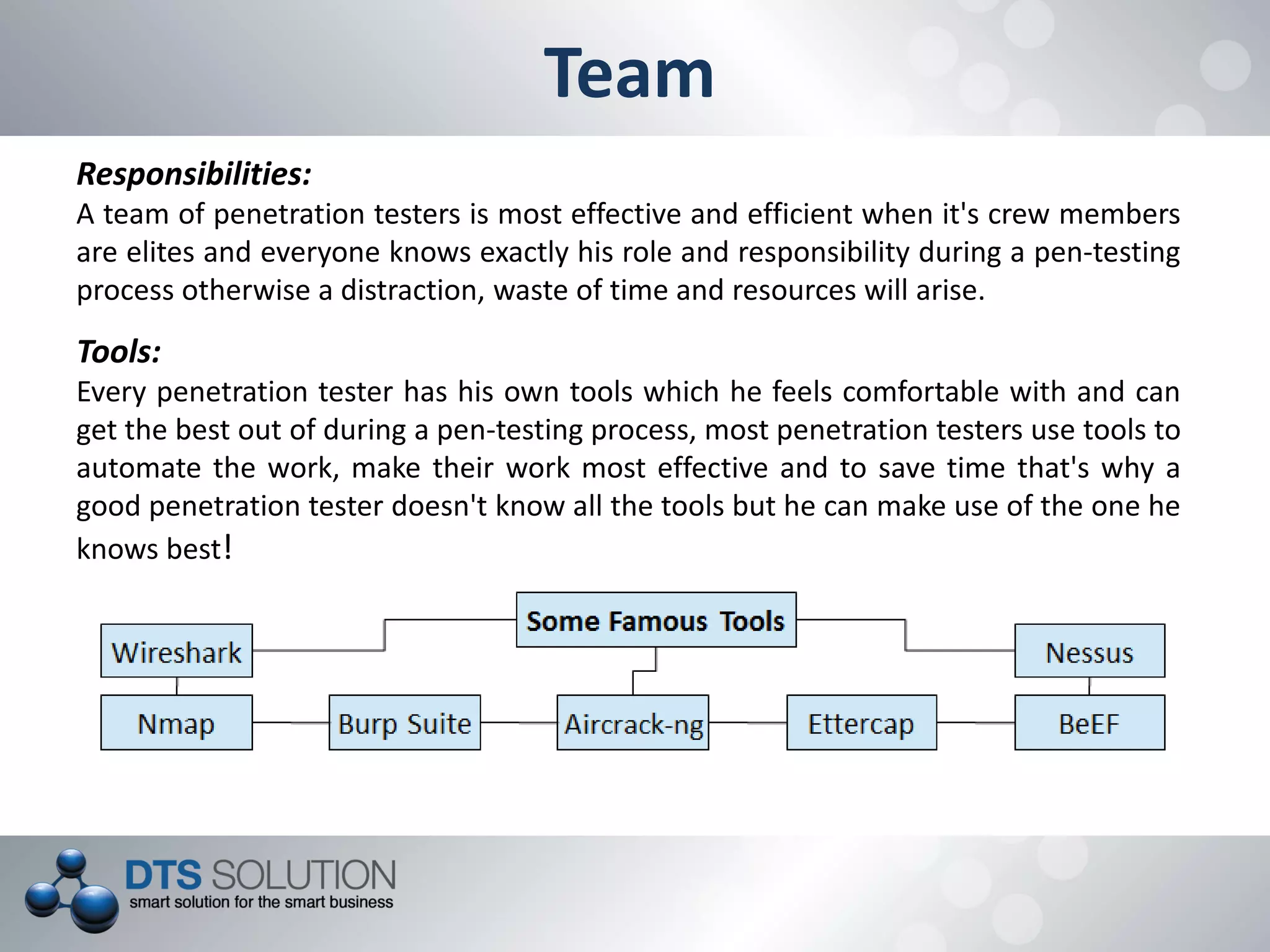
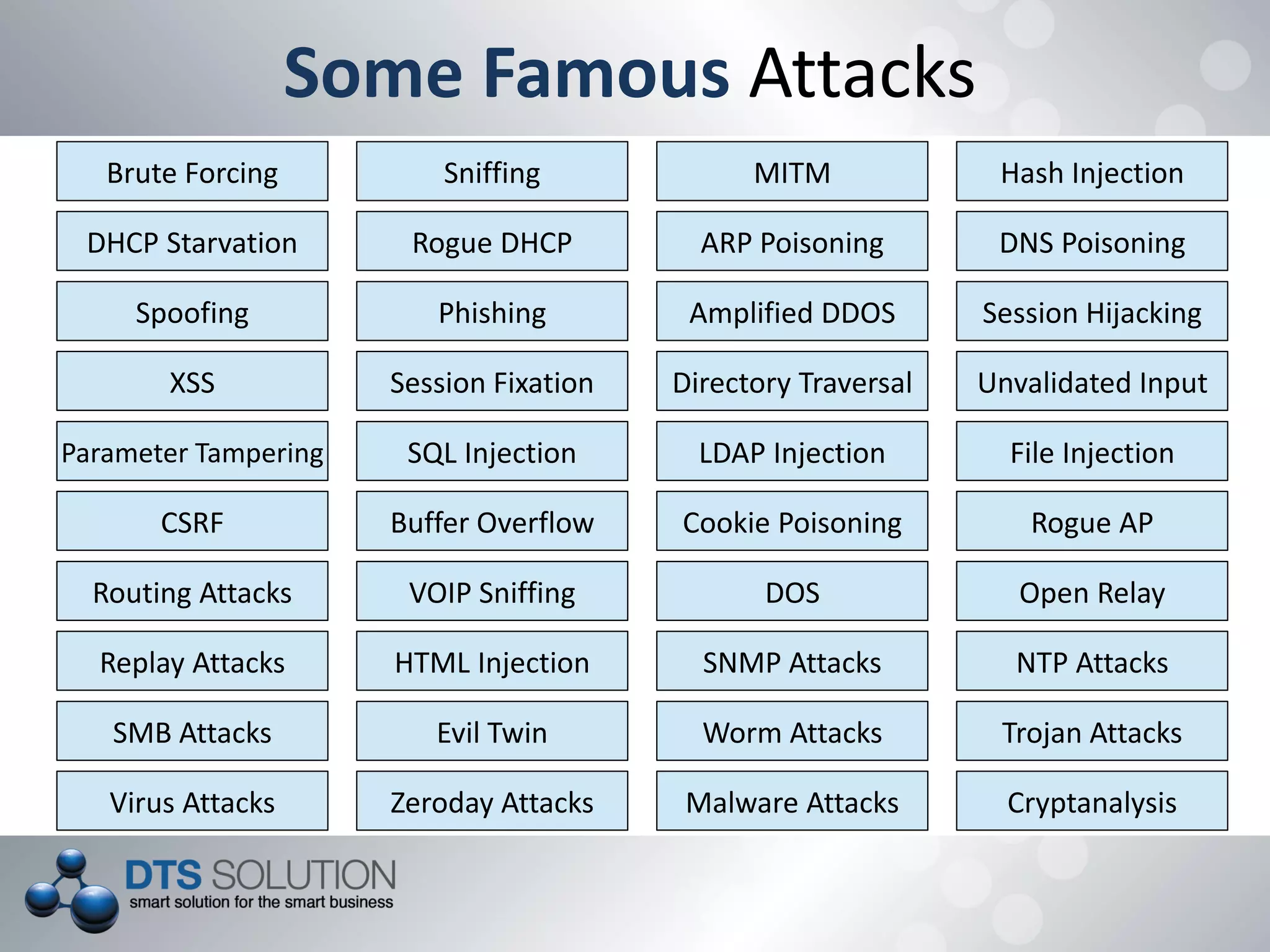
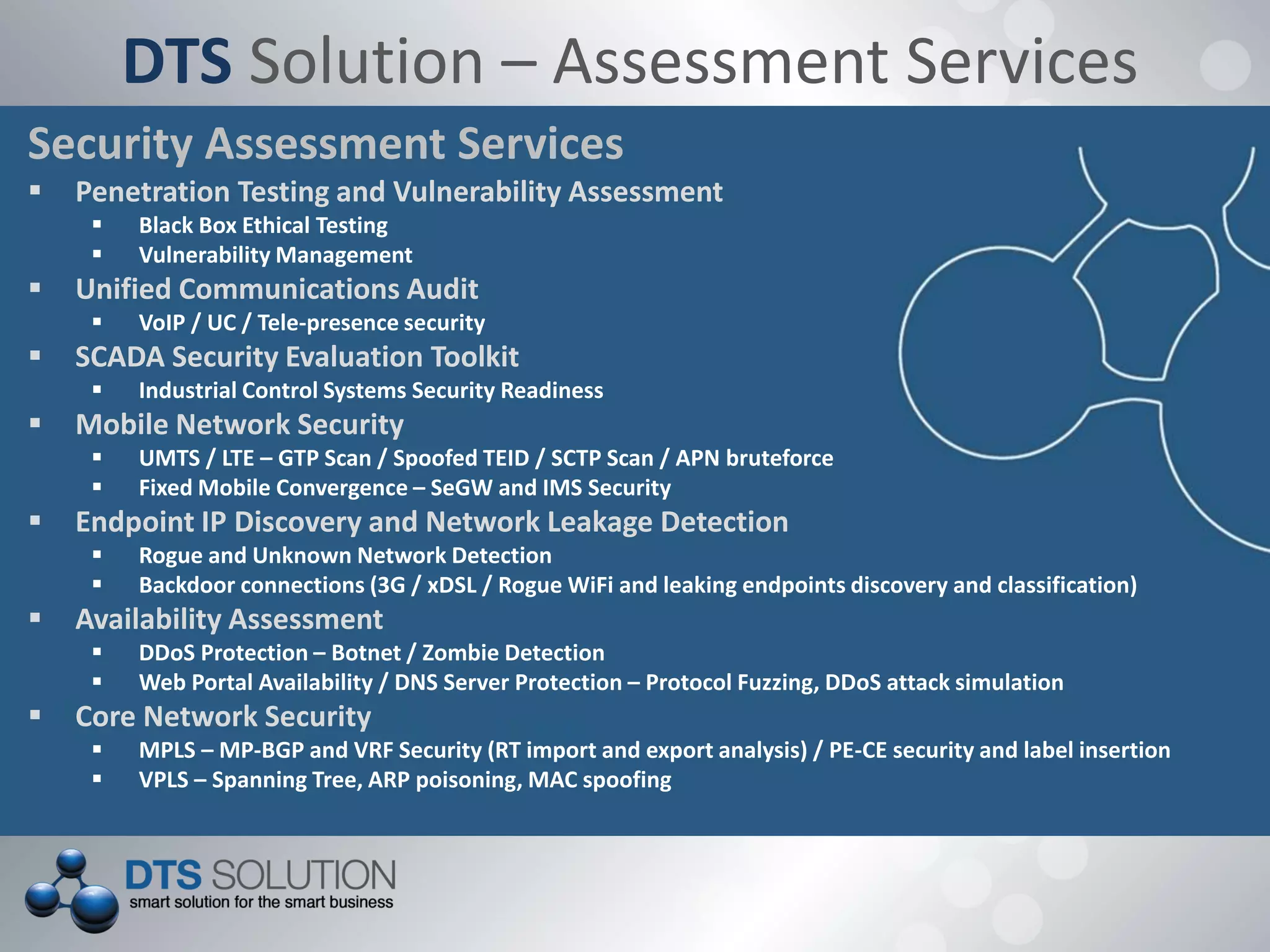
This document provides information about penetration testing services offered by DTS Solution. It includes contact information for two consultants, Shah H Sheikh and Mohamed Bedewi. It then discusses penetration testing methodologies, including white box and black box testing. It also outlines steps for information gathering, including initial gathering through search engines and deep gathering through techniques like port scanning and banner grabbing. The document notes various attacks that could be performed and stresses the importance of documentation. It concludes by listing security assessment services provided, such as penetration testing, vulnerability assessment, and availability testing.