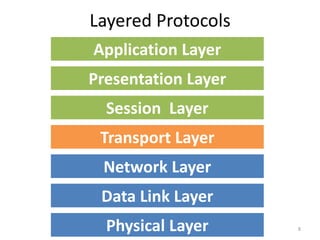
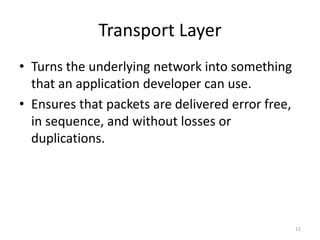
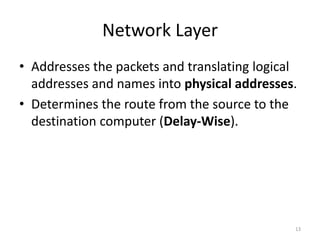
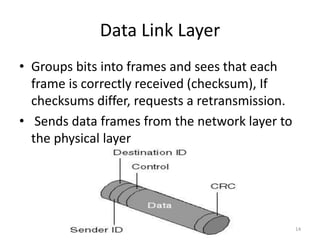
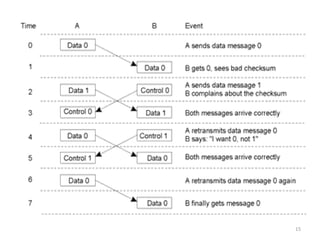
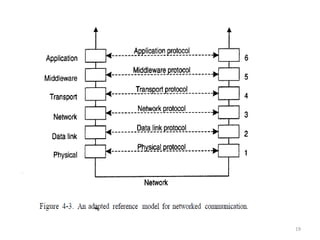
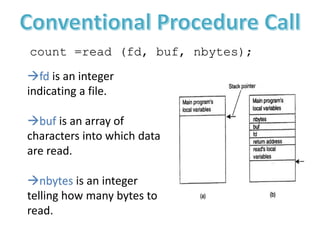
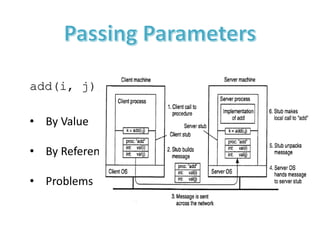
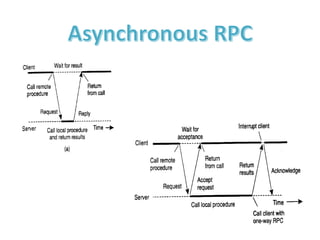
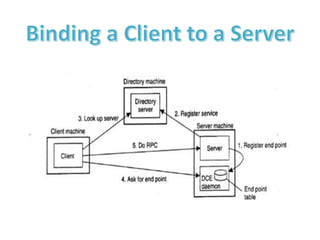
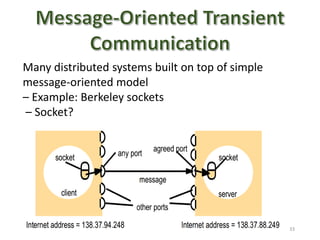
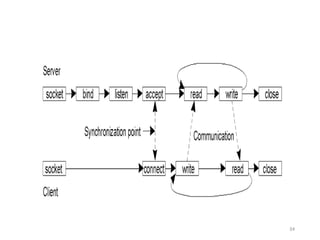
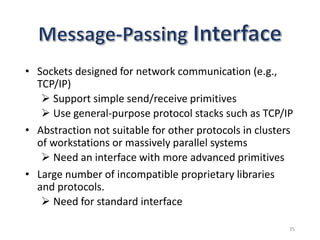
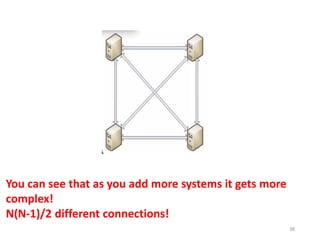
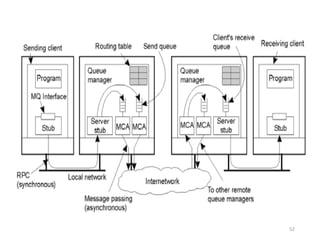
The document provides an overview of inter-process communication (IPC) in distributed systems, focusing on layered protocols and various communication models. It explains the significance of middleware, remote procedure calls, and message-oriented communication, highlighting the complexities and solutions such as message brokers and queuing systems. Additionally, it discusses the OSI model and the responsibilities of different layers in facilitating effective communication between processes.