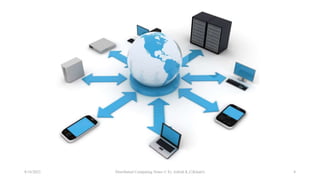
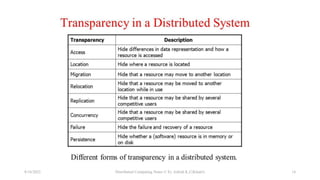
The document outlines the design goals of distributed systems, emphasizing resource sharing, openness, transparency, and scalability. Key transparency types include access, location, concurrency, replication, failure, migration, performance, and scaling transparency, each serving essential functions for user experience and system reliability. Additionally, it discusses difficulties such as varying workloads, heterogeneous environments, and external threats to data integrity.