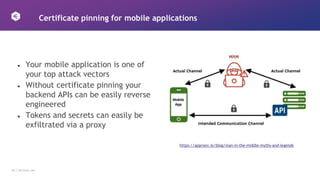
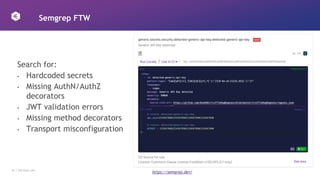
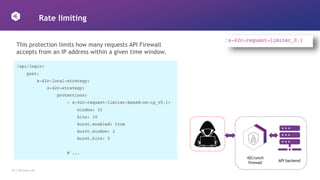
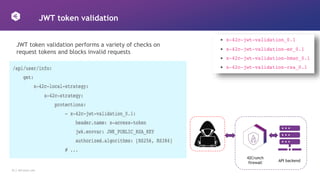
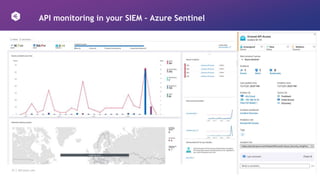
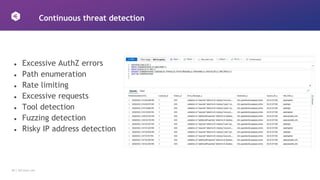
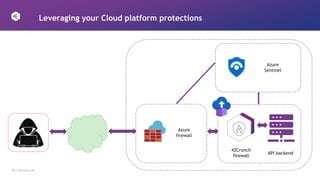
This document discusses how to design APIs to be rugged and resilient against threats. It recommends threat modeling to understand vulnerabilities and abuse cases. It also suggests implementing authorization for every endpoint, explicit anonymous access, and pinning certificates for mobile apps. Runtime protections like rate limiting, JWT validation, and security headers are also advised. Monitoring APIs in a SIEM and leveraging cloud platform protections can help detect and block attacks.













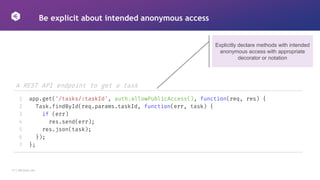
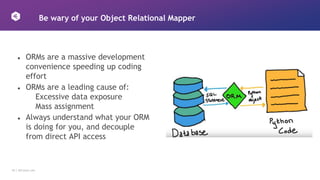
![19 │ 42Crunch.com
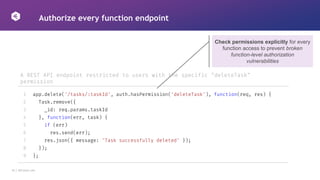
Explicitly enable methods, prevent unused methods
Explicitly specify the methods to be
used, and prevent unused methods in
the framework used
A Python Flask API endpoint
1
2
3
4
5
@app.route('/', methods=['POST'])
def my_first_api_endpoint():
json_data = json.loads(request.data)
...
return "", 200](https://image.slidesharecdn.com/areyourapisrugged-220416032437/85/2022-APIsecure_Are-your-APIs-Rugged-Enough-19-320.jpg)