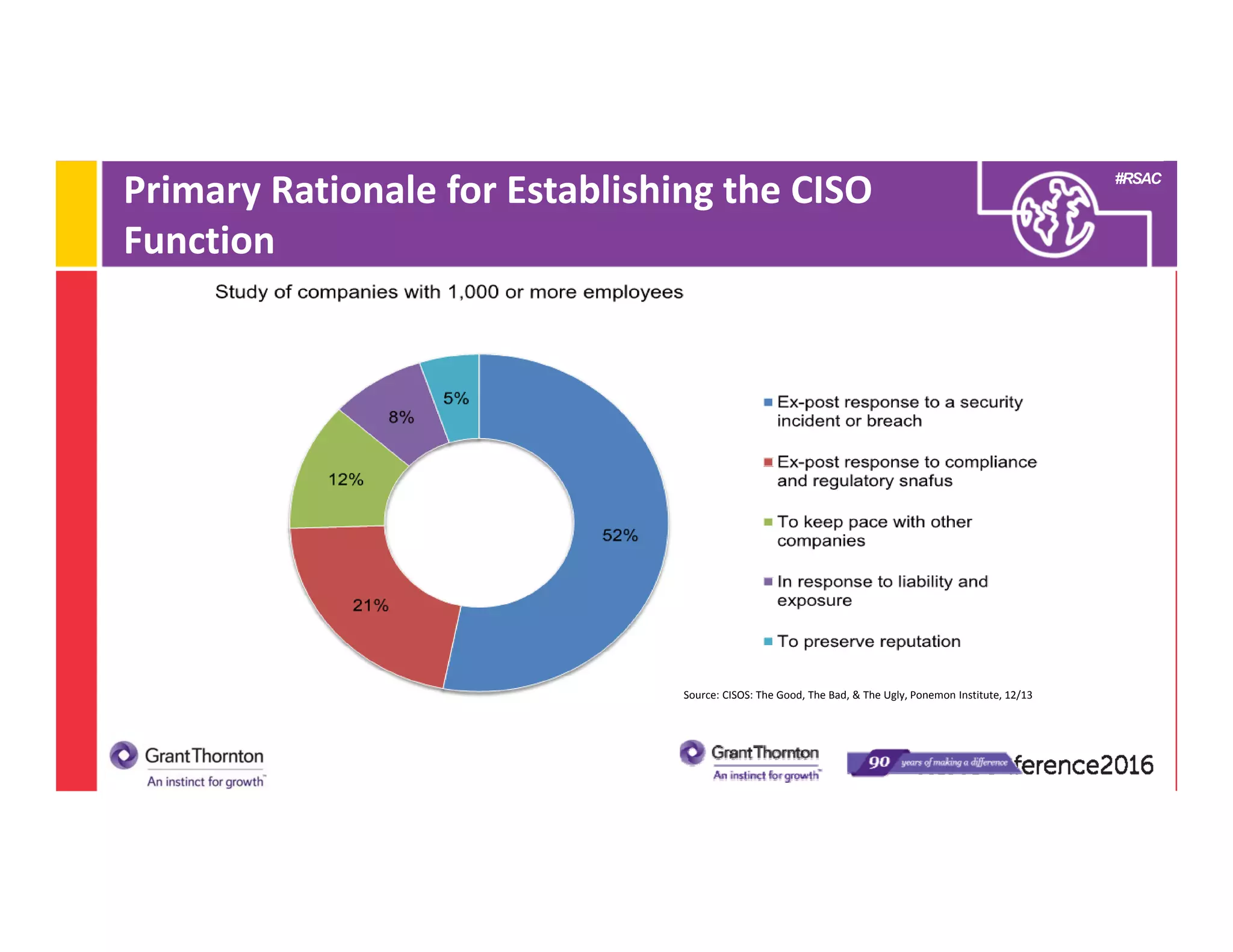
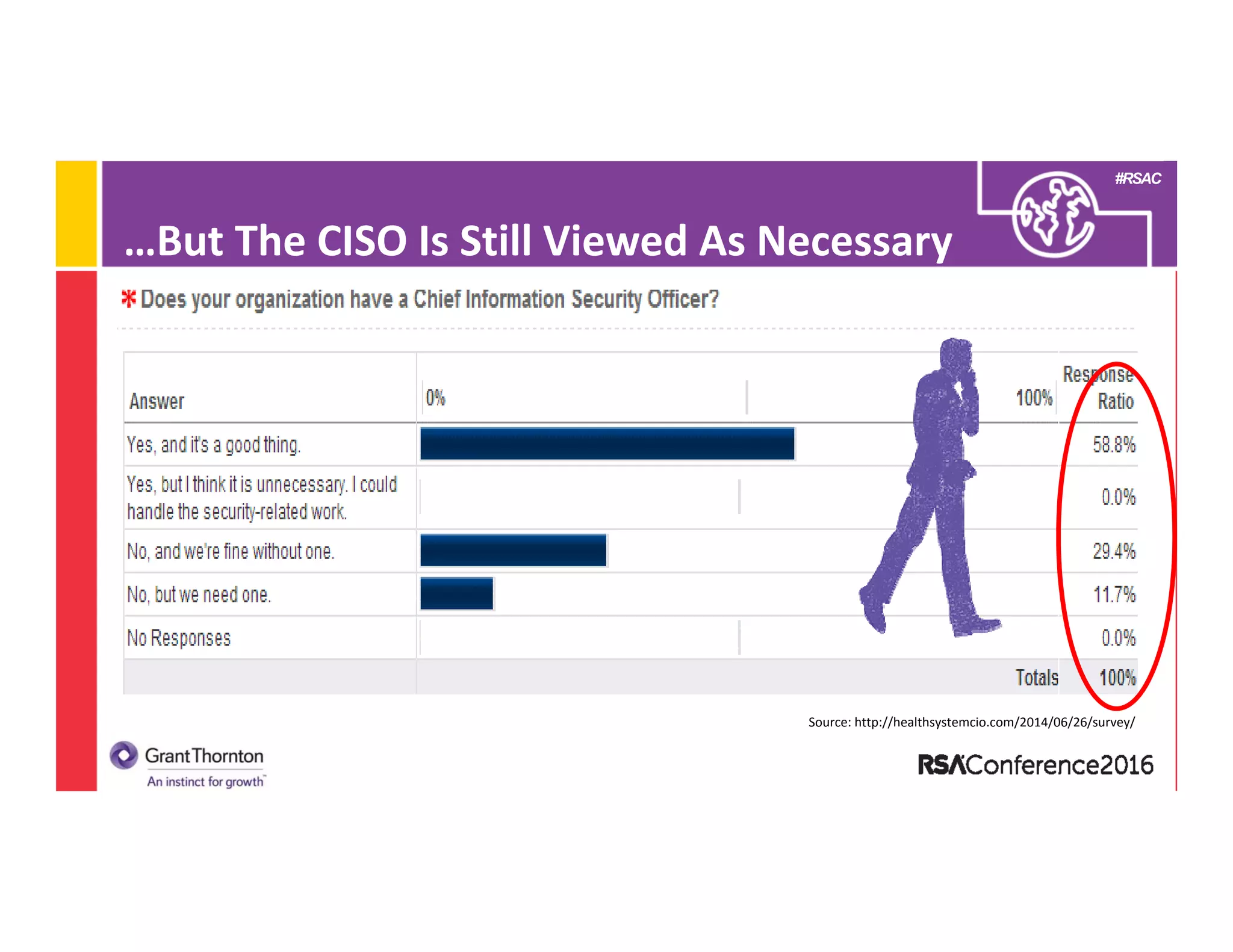
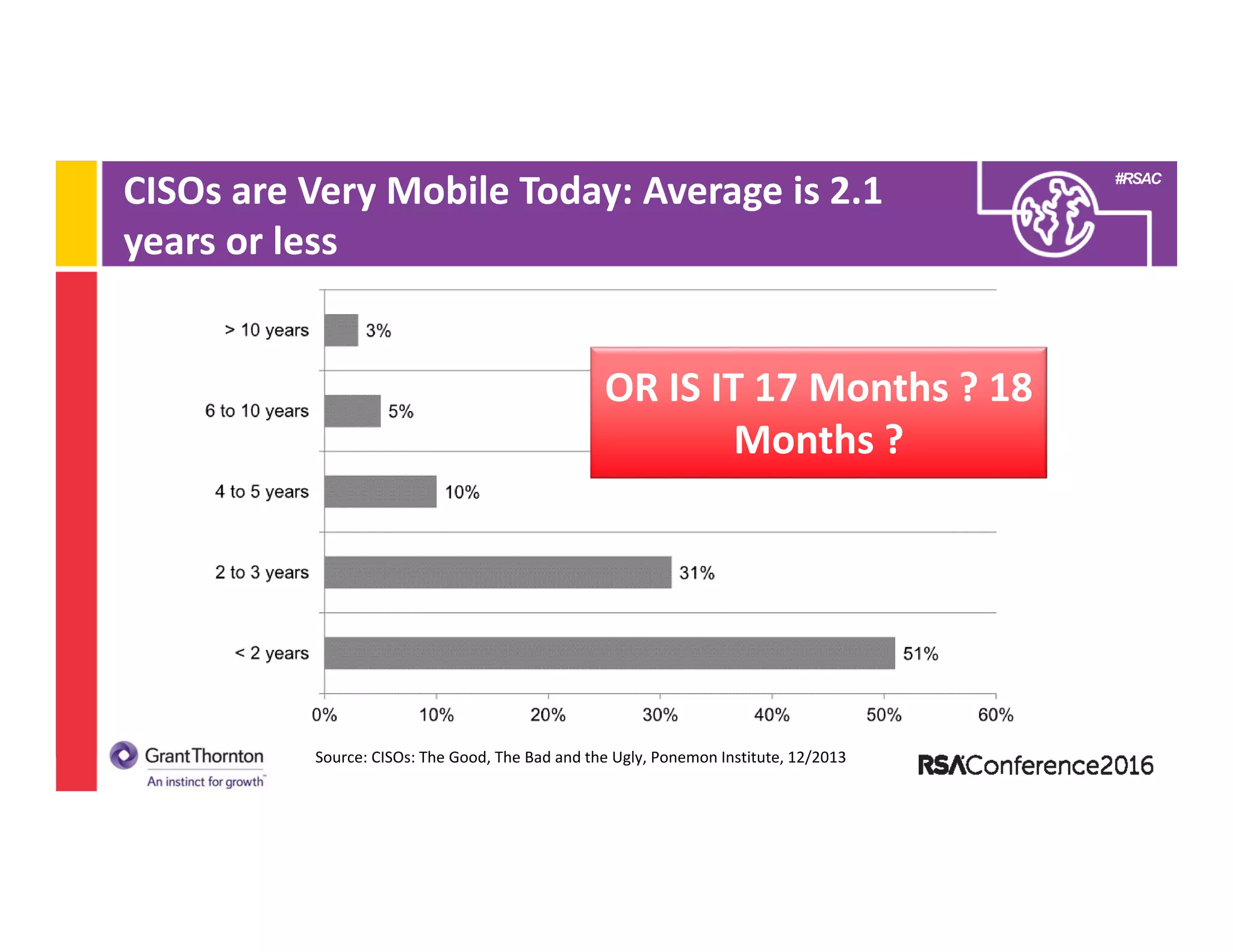
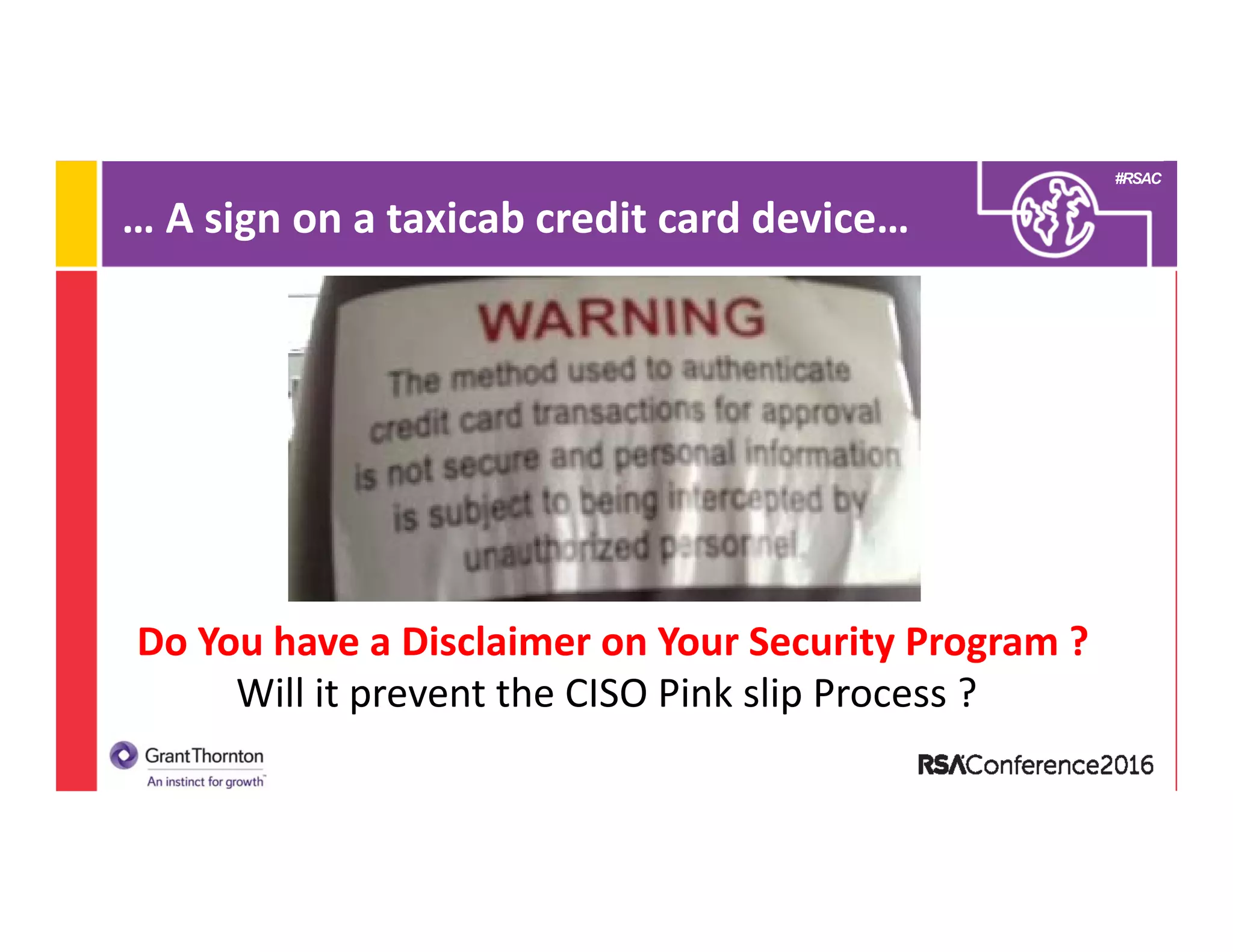
This document provides an overview of the Chief Information Security Officer (CISO) role including:
1) A sample CISO job description outlining responsibilities such as managing the information security program, performing risk assessments, ensuring disaster recovery plans, and more.
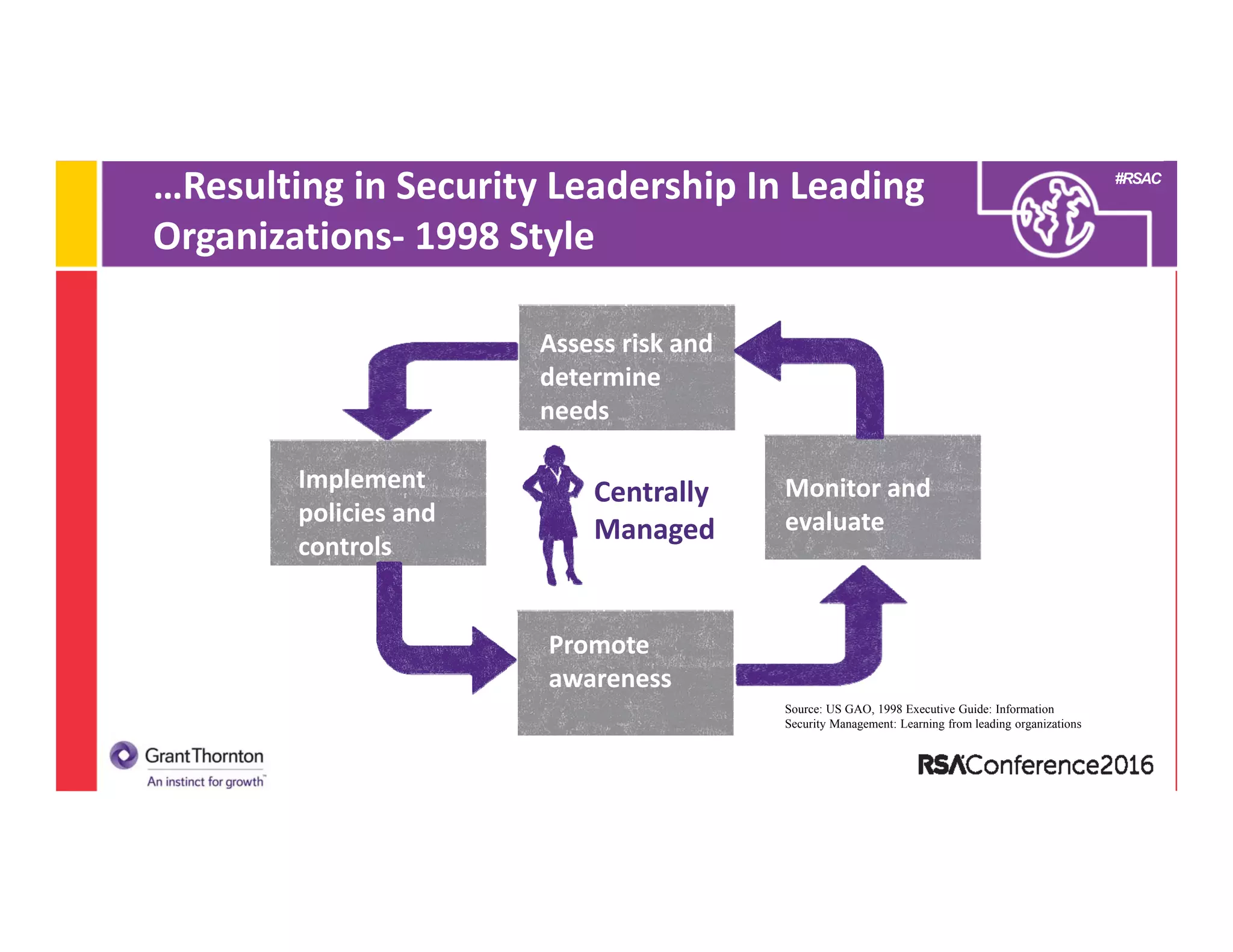
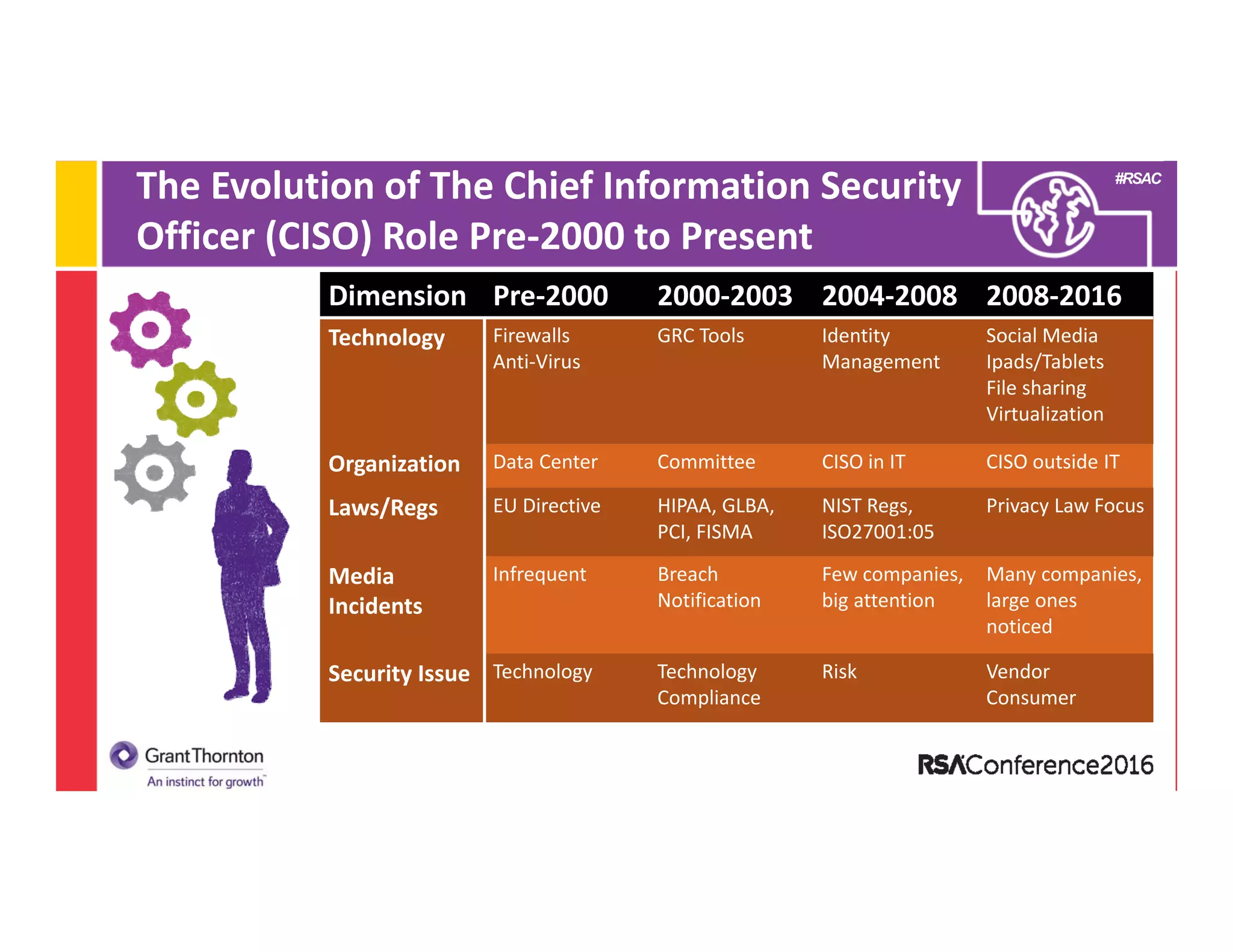
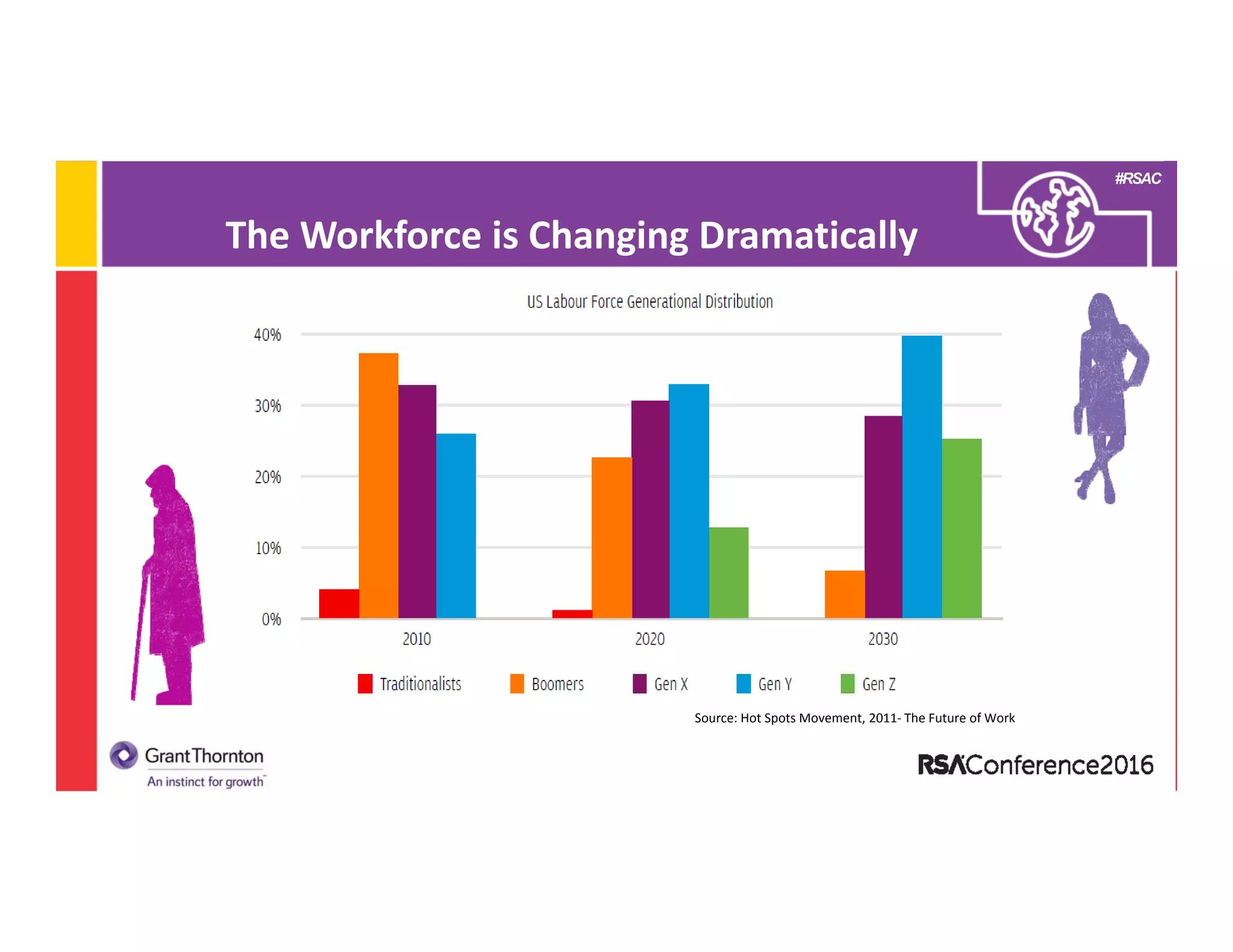
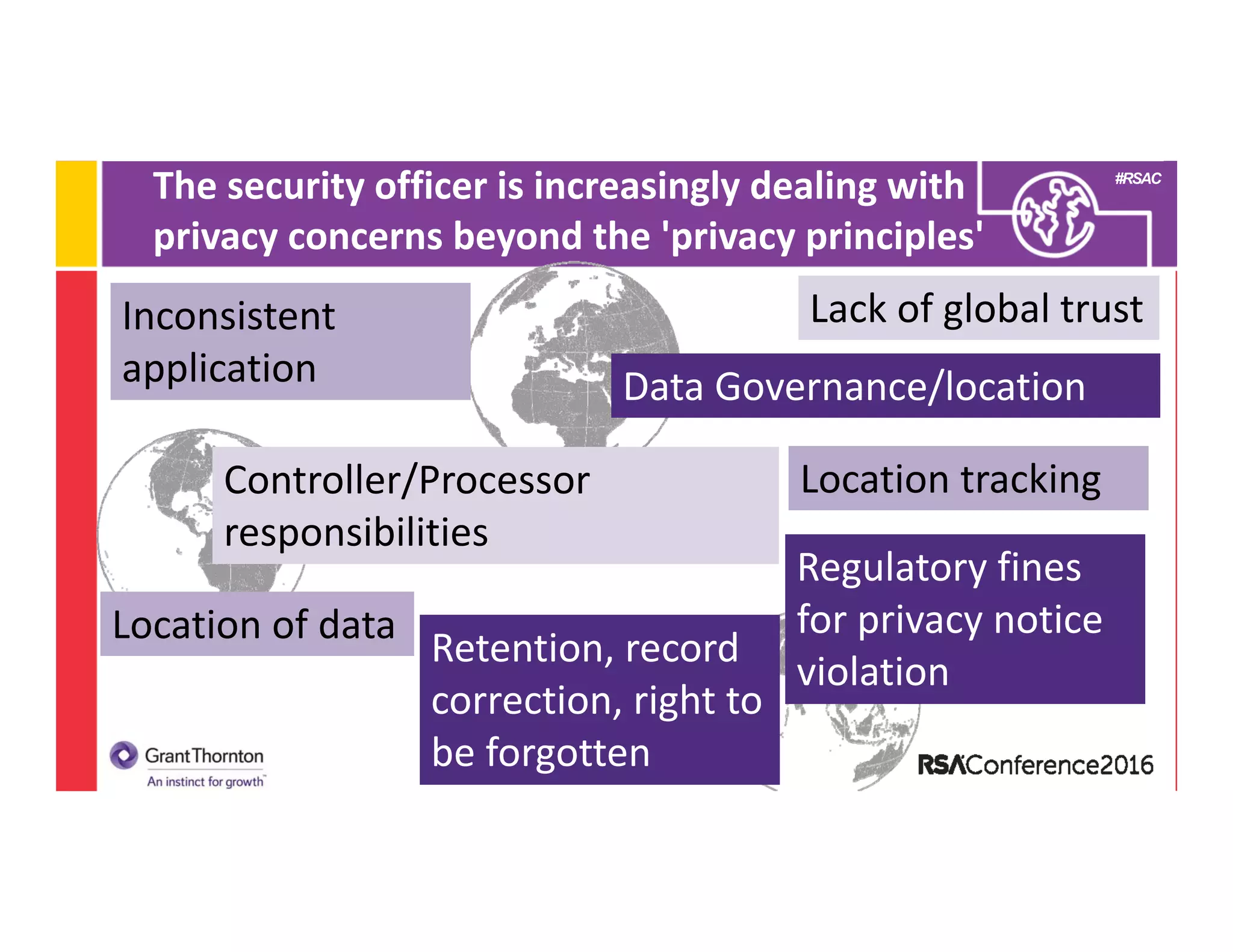
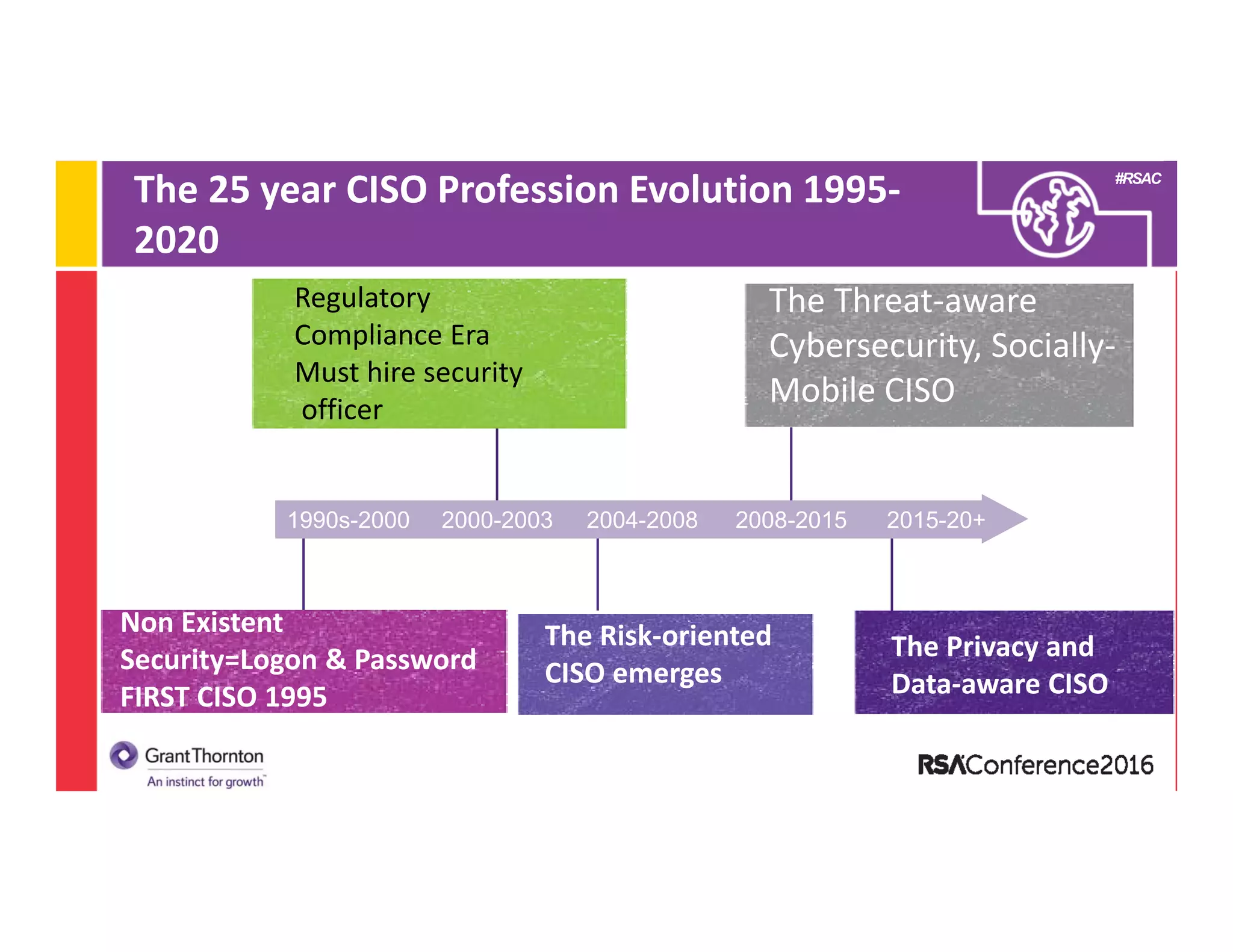
2) A discussion of the evolution of the CISO role from the 1990s to present day, noting changes in technologies, laws/regulations, security issues, and organizational structure.
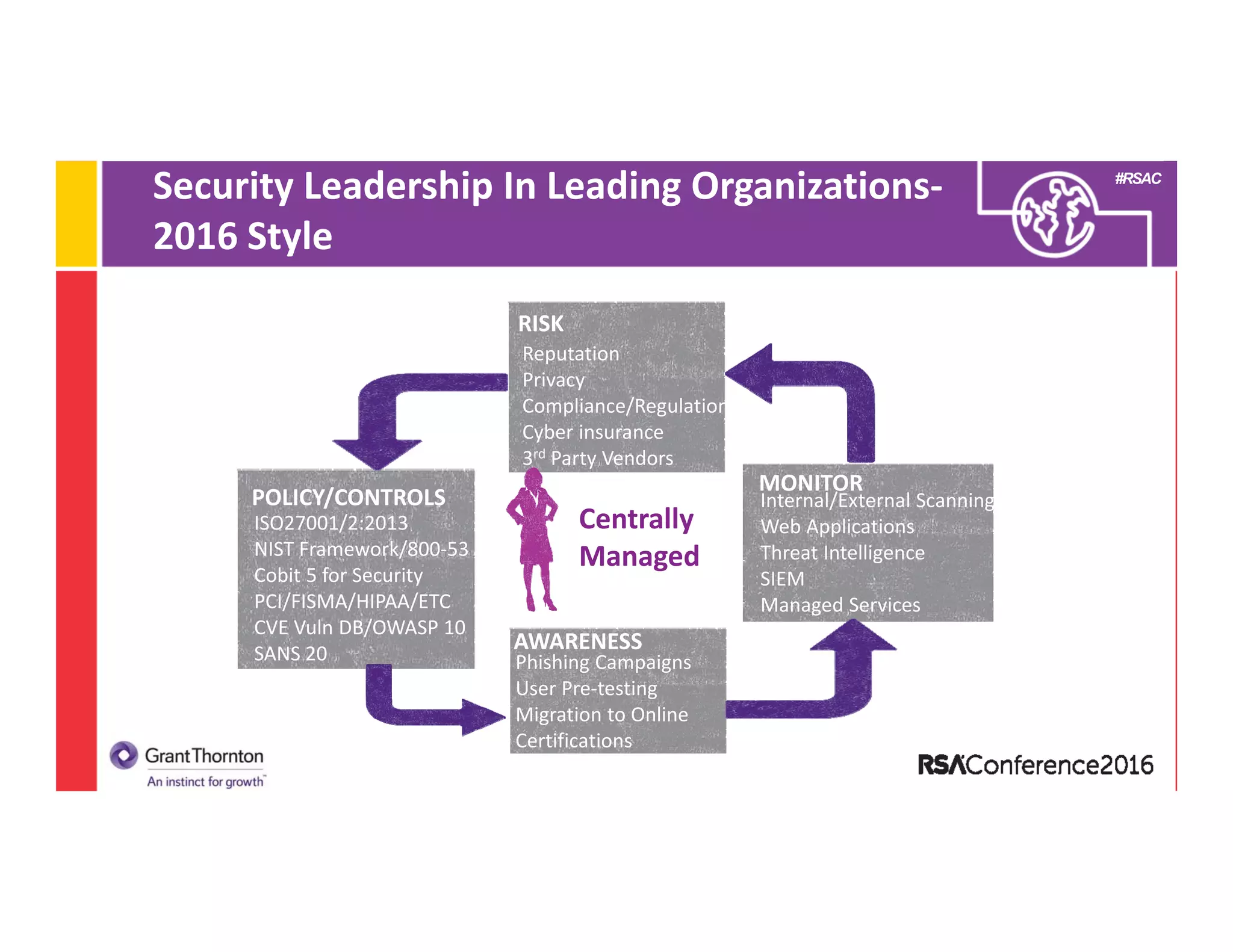
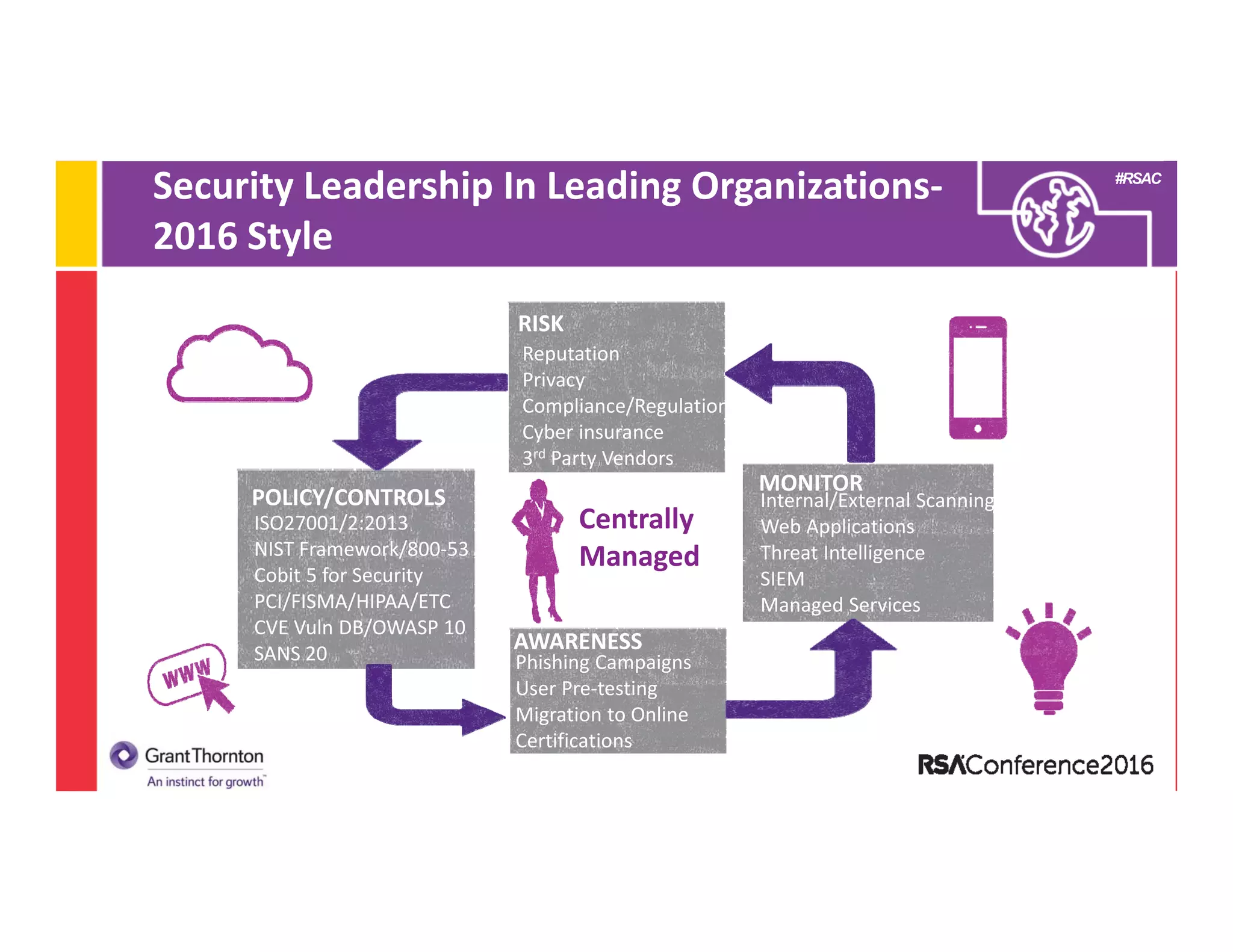
3) An examination of what constitutes a leading information security program in 2016, highlighting areas like risk management, monitoring, policies/controls, awareness, and certifications/frameworks.
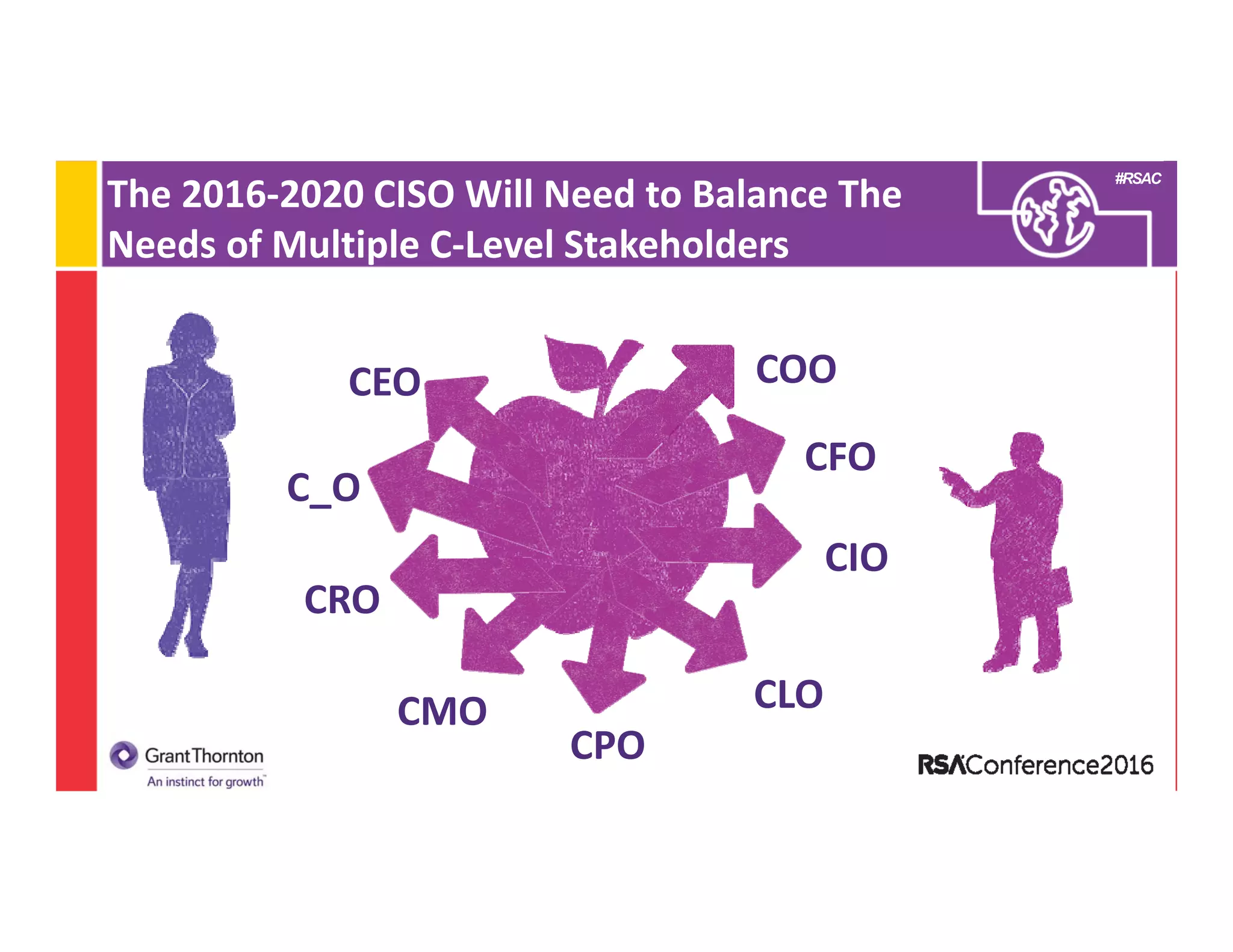
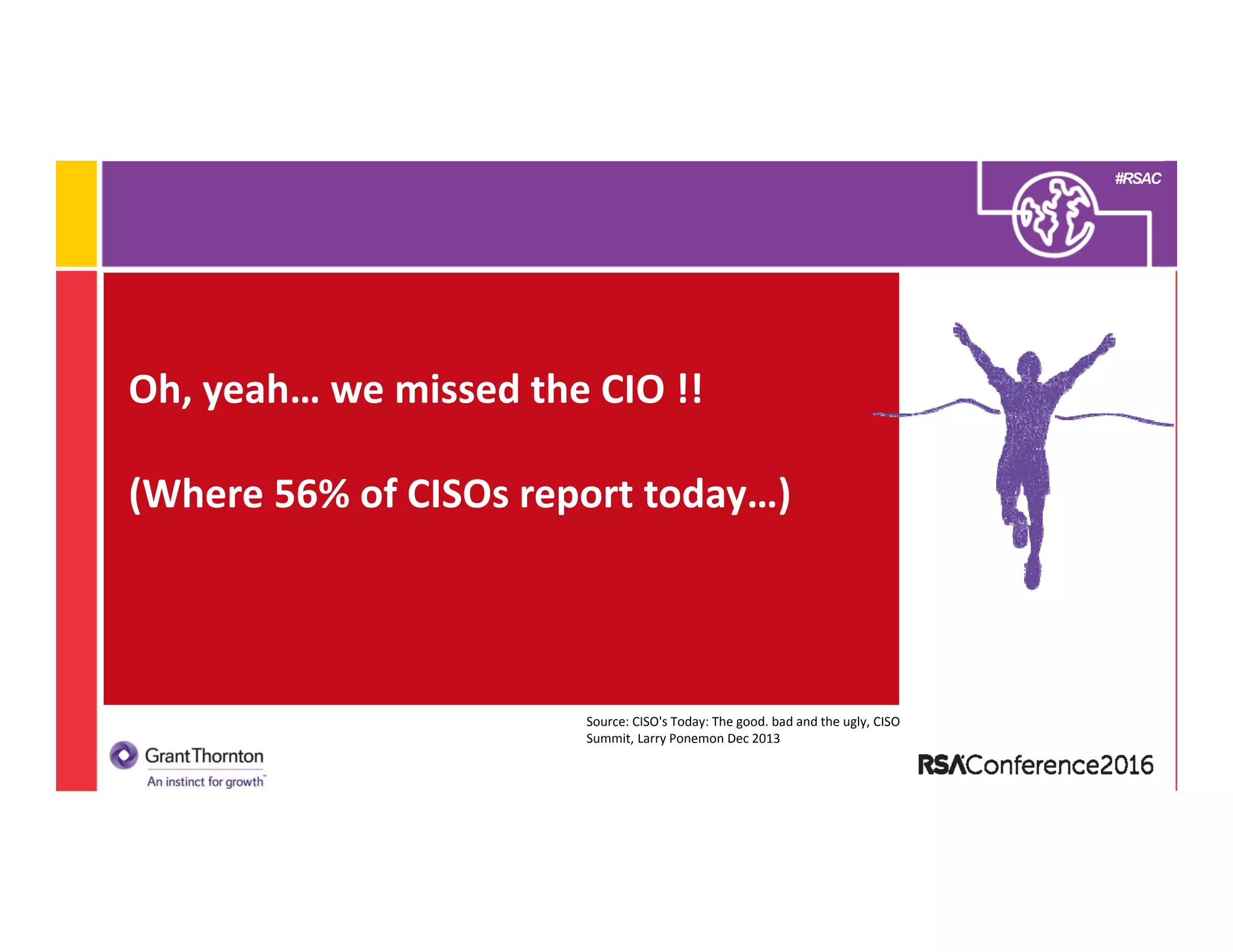
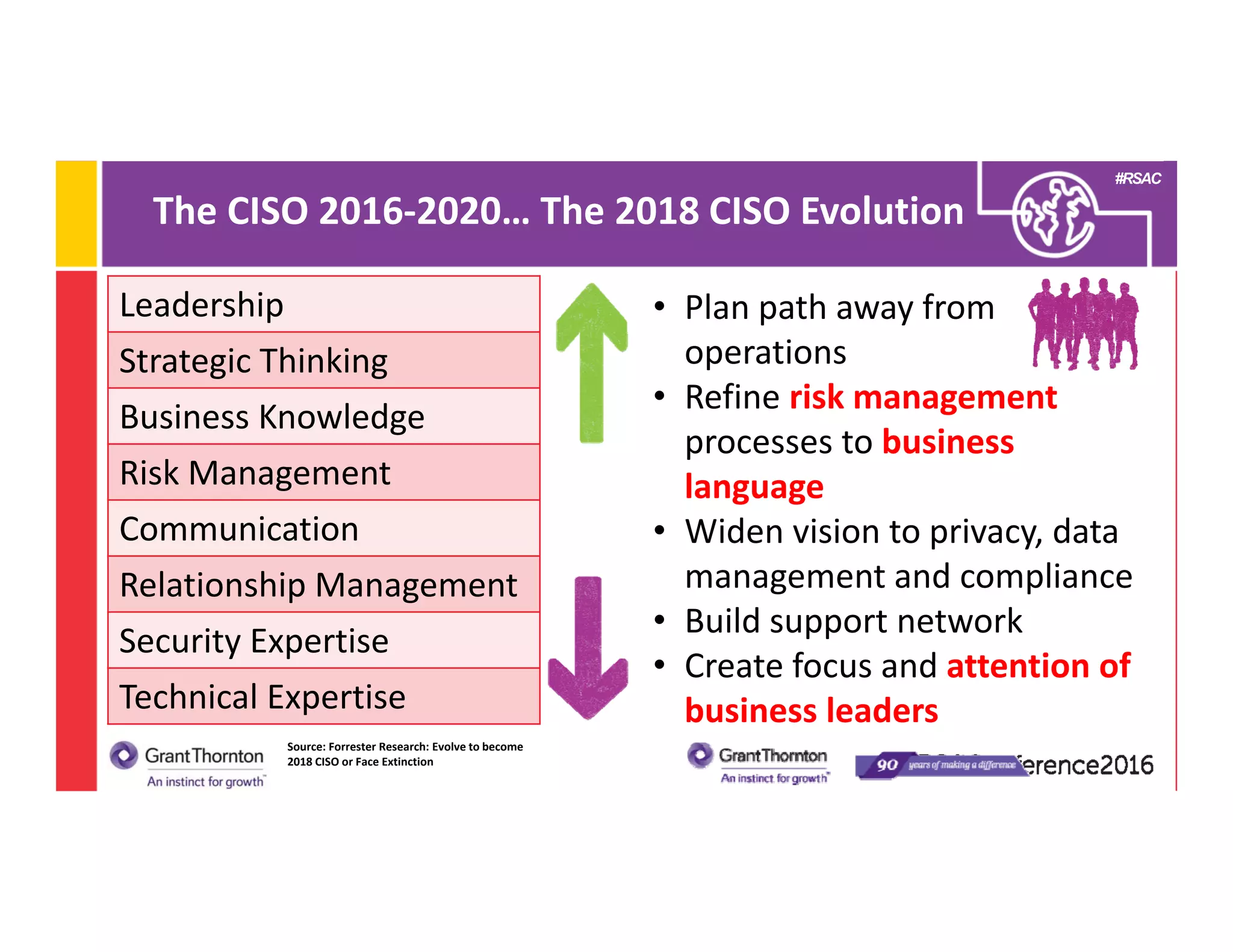
4) A look at how the 2016-2020 CISO will need to balance