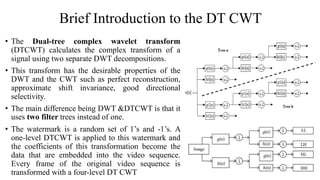
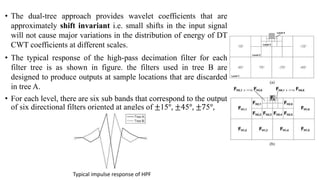
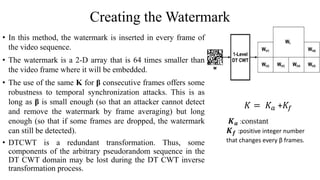
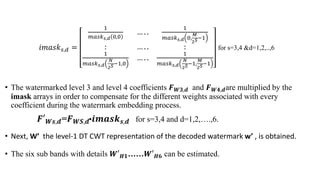
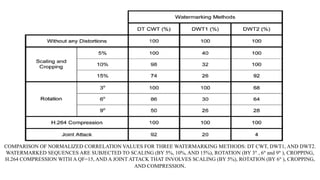
The document proposes a new video watermarking algorithm using the dual-tree complex wavelet transform (DTCWT). The DTCWT offers advantages like shift invariance and directional selectivity. The algorithm embeds a watermark by adding its coefficients to high frequency DTCWT coefficients of video frames. Masks are used to hide the watermark perceptually. Experimental results show the proposed method is robust to geometric distortions, lossy compression, and a joint attack, outperforming comparable DWT-based methods. It is suitable for playback control due to its robustness and simple implementation.



![LITERACY SURVEY
Ref1:Persistent access control to prevent piracy of digital information[1997]
1. Watermarking technology was first introduced in 1990’s where
playback control application, the watermark embedded in the video
sequence.
2. With help of this playback control application it will provide
information that whether video players are authorized to display the
content or not.](https://image.slidesharecdn.com/ppt-150413090817-conversion-gate01/85/Ppt-5-320.jpg)
![Ref2:Rotation, scale and translation invariant digital image
watermarking[1999]
• In this paper author proposed an image watermarking method
based on the Fourier–Mellin transform is proposed
• The embedded marks may be designed to be unaffected by any
combination of rotation, scale and translation transformations.
• The scheme is robust to rotation and scaling but weak to
distortions caused by lossy compression.](https://image.slidesharecdn.com/ppt-150413090817-conversion-gate01/85/Ppt-6-320.jpg)
![Ref3:Rotation, scale, and translation resilient watermarking for
images[2001]
1. The watermark is embedded into a 1-D signal, which is obtained
by taking the Fourier transform of the image, resampling it in to
log-polar coordinates, and integrating along the radial dimension.
2. This method is robust to rotation, scaling, and translation and lossy
compression which is one of advantage compared to previous
results.
3. However this scheme cannot withstand cropping.](https://image.slidesharecdn.com/ppt-150413090817-conversion-gate01/85/Ppt-7-320.jpg)
![Ref4: DWT based high-capacity blind video watermarking ,in
variant to geometrical attacks[2003]
1. In this two watermarks are employed. The first one is used to embed
the message while the second one, a 0-b watermark, is employed as
a geometric reference.
2. Once the reference watermark has been changed, the decoder
assumes that there is no watermark embedded in the content and,
therefore, does not search for the hidden message.
3. Even though this method is tricky secure, introducing two
watermarks in the same video is complex and may effect the host
signal.](https://image.slidesharecdn.com/ppt-150413090817-conversion-gate01/85/Ppt-8-320.jpg)