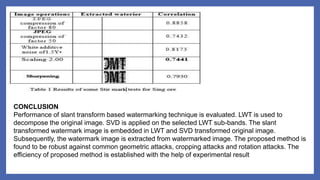
The document presents a semi-blind watermarking scheme for copyright protection in digital images utilizing slant transform, addressing issues of copyright infringement faced by digital content owners. It details the watermark embedding and extraction processes, demonstrating effective integration of a grayscale watermark into the original image using specified frequency coefficients. Experimental results indicate that the proposed method maintains high image quality and robustness against various attacks, making it a viable solution for digital content security.


![• SLANT TRANSFORM
• This section details the proposed semi-blind watermarking scheme for copyright protection of digital images.
The following subsections present the steps involved in the watermark embedding and extraction processes
along with a brief description about the Slant transform, DWT and SVD
Slant transform is derived from saw tooth waveforms.Aslant transform matrix has a constant basis vector
corresponding to zero sequency and slant basis vector basis vectors monotonically decreases with sequency
inconstant step from maximum to minimum. The matrix has sequency property and high energy compaction
property[12]. The lowest order of slant matrix is 2 and 2 X 2 matrix is identical to Hadamard matrix
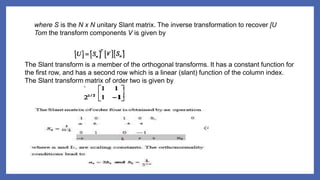
Let é/] be the original image of size N x N , its 2O-Slant transform is given by [5]
(1)](https://image.slidesharecdn.com/grayimagewatermarkingdip-210617080407/85/Gray-Image-Watermarking-using-slant-transform-digital-image-processing-3-320.jpg)

![1. Watermarking in Slant Transform domain
2. A generic block diagram of the blind watermarking system Figure 1. The original image is not necessary at
the watermark recovery stage. This refers to ‘Tlind” watermarking process. A visually recognizable pattern
is embedded by modifying the Slant transform coefficients of relevant sub-blocks of the host image. The
detailed Image-embedded watermark insertion and extraction algorithm are discussed in this section.
3. Copyright information in the form of a trademark or logo can be created as a pattern for watermarking. In our
experiment, a grayscale image of size 64 x 64 is used as the watermark. The watermark insertion process is
shown in Figure 2. We adapt a image-embedded watermark insertion algorithm as in [I], while using the
Slant transform domain instead of the Hadamard transform](https://image.slidesharecdn.com/grayimagewatermarkingdip-210617080407/85/Gray-Image-Watermarking-using-slant-transform-digital-image-processing-6-320.jpg)
![The watermark image, W x,y) , is first transformed into a
set of Slant transform coefficients by equation (1). A Slant transform matrix of order 64 is applied
to this image, Let the original image be fax y) . Similar to the algorithm used in [1,2], it is
decomposed into a set of non-overlapped 8 x 8 sub-blocks. An m-sequence random number
generator is used to select a certain number of sub-blocks for watermark embedding, whose
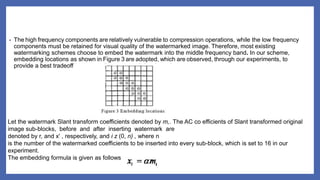
initial seed is also kept in the secret key file. In every selected sub-block, sixteen middle and high
frequency coefficients are used for later modulation. The way of the coefficients selection affects
the performance of the watermarking scheme significantly](https://image.slidesharecdn.com/grayimagewatermarkingdip-210617080407/85/Gray-Image-Watermarking-using-slant-transform-digital-image-processing-7-320.jpg)
![•In watermark detection, the positions of the sub-blocks with watermark embedded are computed
using the seed of the m-sequence and initial state number that is stored in the key file. All the
selected sub-blocks are Slant transformed. Let
•these coefficients denoted by z'’ atid the retrieved
•watermark Slant transform coefficients by m, , i e (0, n],
•where n is the number of the watert marked coefficients to be inserted in every sub-block. The
watermark extraction formula is given by
•
The exacted AC coefficients and the DC component stored in the key file are rearranged
into a 64 x 64 Slant transform coefficients matrix. The extracted watermark image, IP’ (z, y)
, is then obtained by an inverse Slant
transform using equation (2).](https://image.slidesharecdn.com/grayimagewatermarkingdip-210617080407/85/Gray-Image-Watermarking-using-slant-transform-digital-image-processing-9-320.jpg)