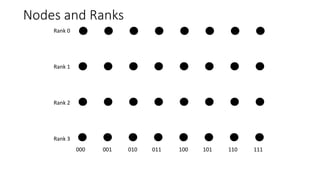
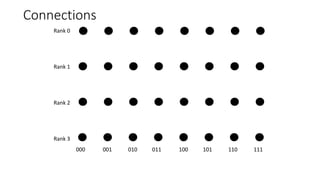
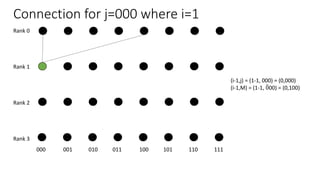
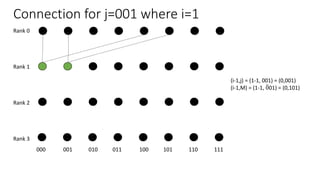
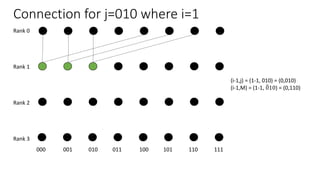
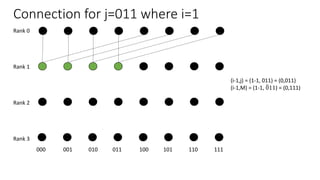
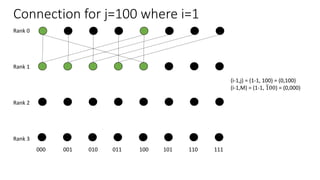
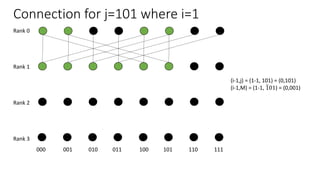
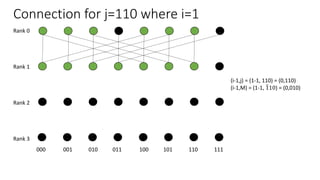
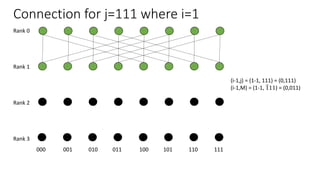
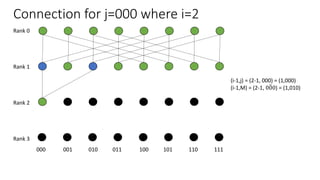
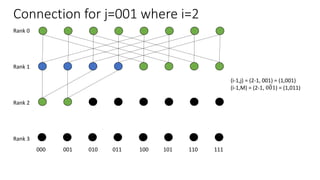
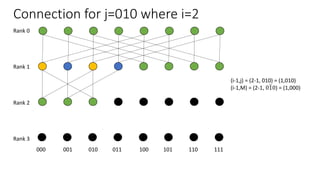
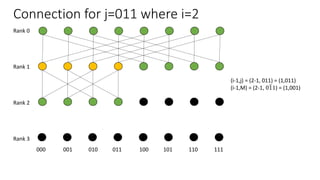
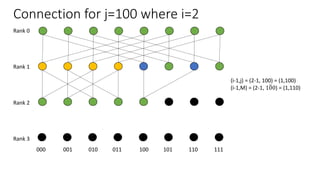
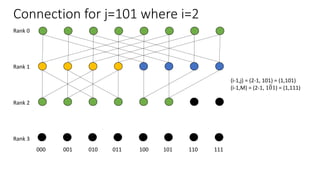
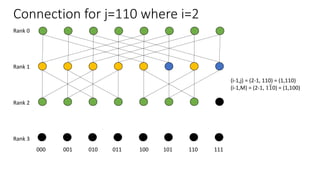
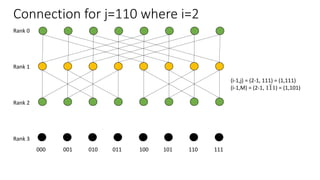
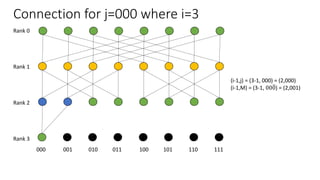
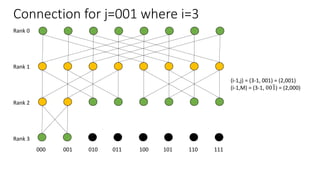
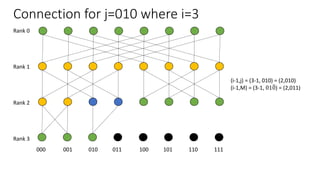
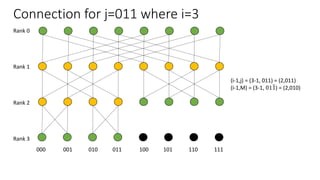
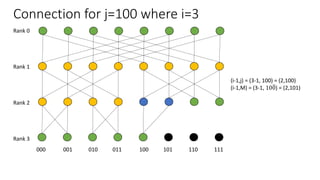
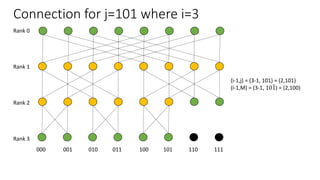
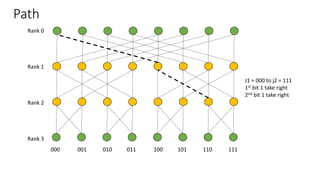
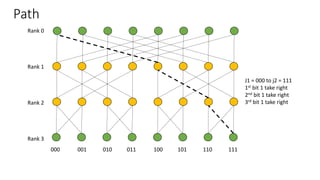
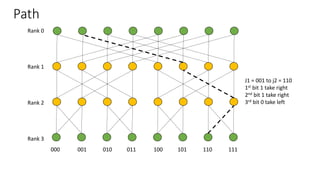
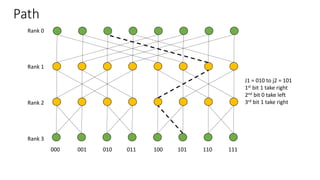
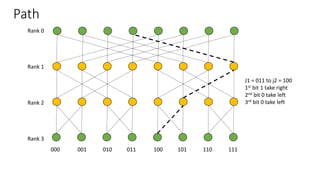
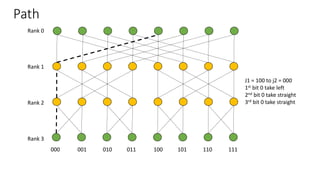
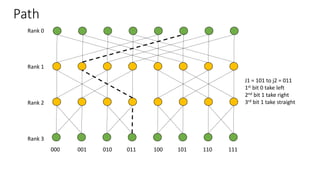
The document describes a butterfly network topology. A butterfly network has the following properties:
- The number of nodes increases exponentially based on the number of ranks K.
- The number of ranks is K+1.
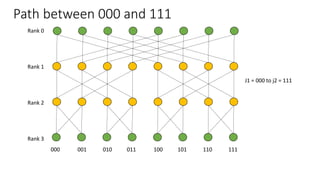
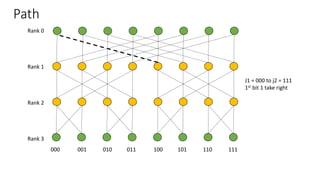
- The diameter of the network, the longest path between any two nodes, is 2K.
- The bisection width, the number of links between the two halves of the network, is 2^K.
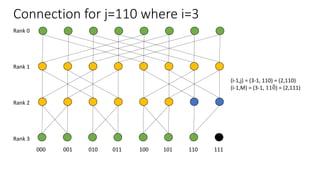
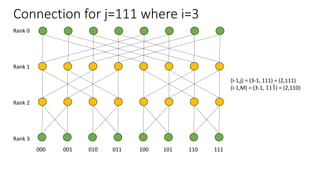
- Nodes are connected based on their rank and identifier, with each node connecting to nodes in the previous rank based on bit inversion rules.