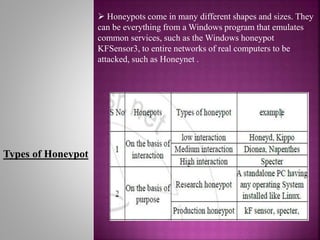
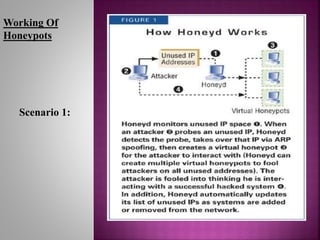
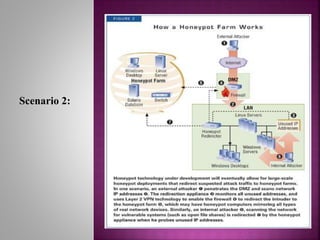
This document discusses honeypots, which are computer systems set up to appear vulnerable in order to attract cyber attacks. It begins by defining honeypots and their purpose of learning about attacks without risking real systems. The document then covers intrusion detection systems (IDS), firewalls, and how honeypots compare to these methods. Honeypots are able to detect both known and unknown attacks, while providing detailed forensic data with fewer false positives than IDS. The document outlines the advantages and disadvantages of honeypots, and concludes they are useful for understanding attack strategies in order to improve security measures.