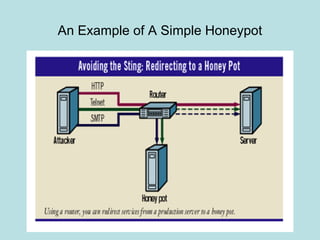
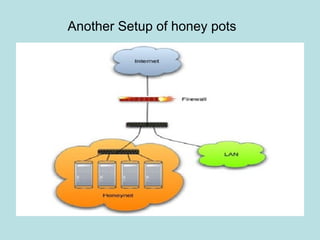
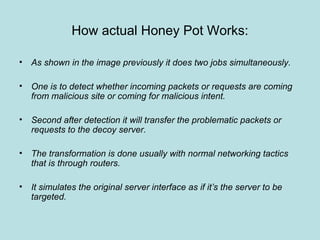
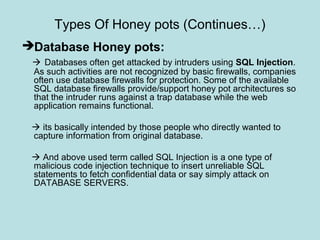
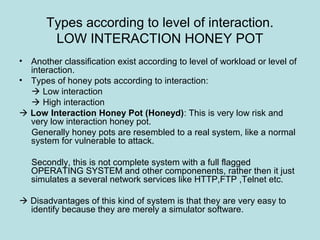
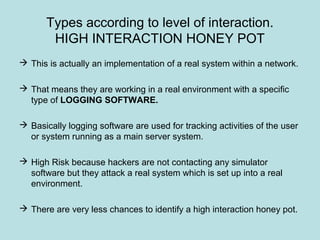
This document discusses honeypots as a solution for internet-based data security. It defines honeypots as fake computer systems designed to collect data on intruders by appearing as legitimate systems. The document outlines different types of honeypots including production honeypots for organizations, research honeypots to study hacker tactics, and database honeypots to capture SQL injections. It also discusses low and high interaction honeypots, with low interaction simulating services and high interaction using whole systems. Finally, it introduces honey nets as networks of monitored high interaction honeypots simulating a production environment.


![[Three Main Issues that are not taken much
care]
1 – Lack of awareness: both at a corporate level and at an end user
level.
This is meant that people who are existed on internet community are
not safe.
In this sense, they must be aware of the risks that can happen to
them while providing personal information and sharing personal
traits on the internet.
They are not enough educated about various threats on internet
now a days.
such as online Scammers , viral attacks , cracking, Phishing ,
hacking Tactics.](https://image.slidesharecdn.com/honeypots-140427082206-phpapp02/85/Honey-pots-3-320.jpg)
![[Three Main Issues that are not taken much
care] (Continued…)
2 – Complacency: This is another threat or say issue that is playing
major role in making data insecure.
generally we never take much care or stay serious about our
information with us.
but, for the other interested person or any hacker it’s the most
important opportunity to steal your data.
In this issue normally user is satisfied and not being aware of future
risks that can come upon their data center or database.
They generally are not having idea about various risks upon their
information that is to occur, sometimes even educated and IT
persons also do this mistake.](https://image.slidesharecdn.com/honeypots-140427082206-phpapp02/85/Honey-pots-4-320.jpg)
![[Three Main Issues that are not taken much
care] (Continued…)
3 – No root cause analysis. Traditionally security solutions, whether
at the perimeter, server or client have focused on detection,
blocking and/or cleaning up the results of malicious software
infections but have not offered effective root-cause analysis.
People need to know from where the malware is coming ? was it a
drive-by download ? , an infected USB drive, email, instant
messaging or something else ? It is not enough to say “Machine X
was infected with malware Y but I cleaned up for you, no need
to worry”
In this case any company or their IT department must have
something like IDS( Intrusion Detection System) or proper firewall
set up.](https://image.slidesharecdn.com/honeypots-140427082206-phpapp02/85/Honey-pots-5-320.jpg)