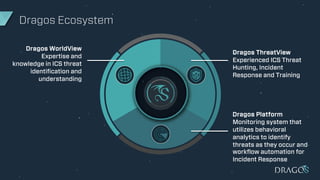
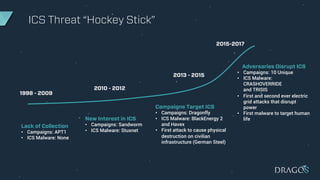
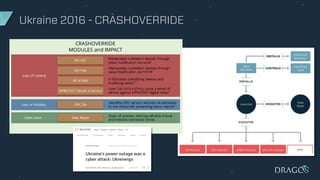
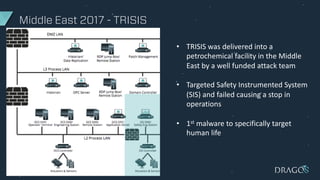
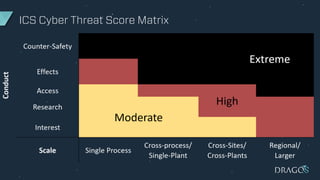
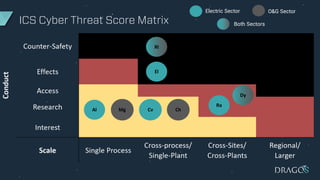
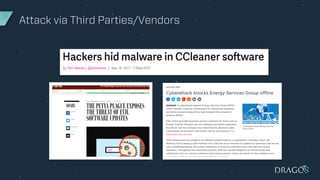
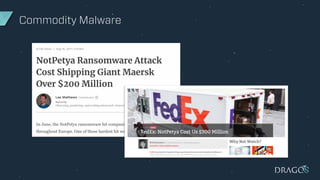
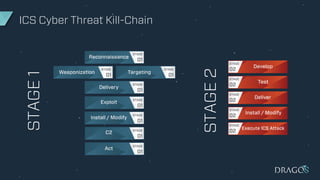
The document discusses the evolving threats to industrial control systems (ICS) and the challenges in addressing these risks, highlighting the increase in cyber attacks targeting ICS from 1998 to present. It emphasizes the lack of adequate threat intelligence, training, and technology dedicated to ICS, alongside specific milestones of attacks that caused physical damage. Recommendations for improving ICS security include enabling two-factor authentication, monitoring systems, and managing third-party risks.