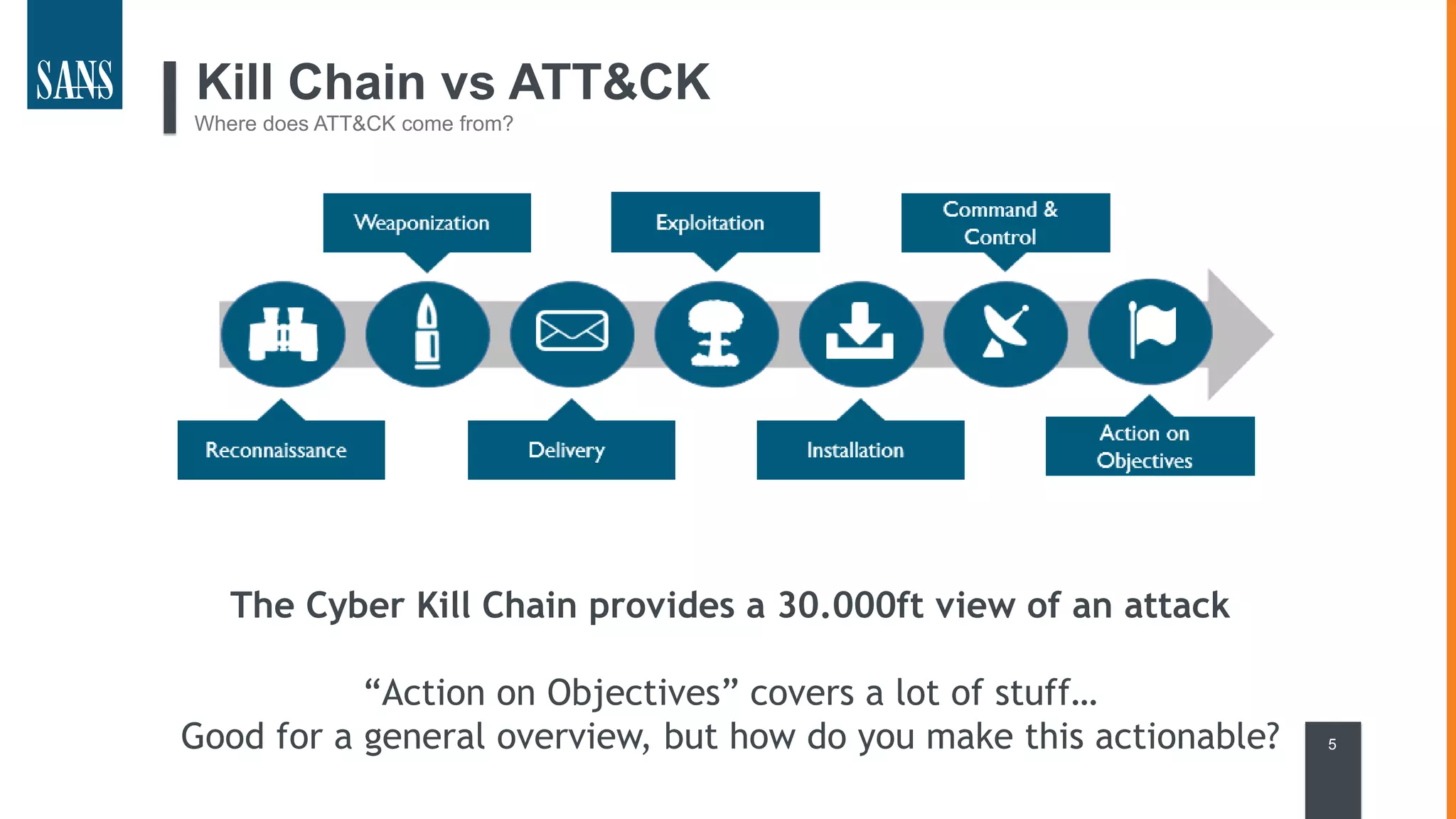
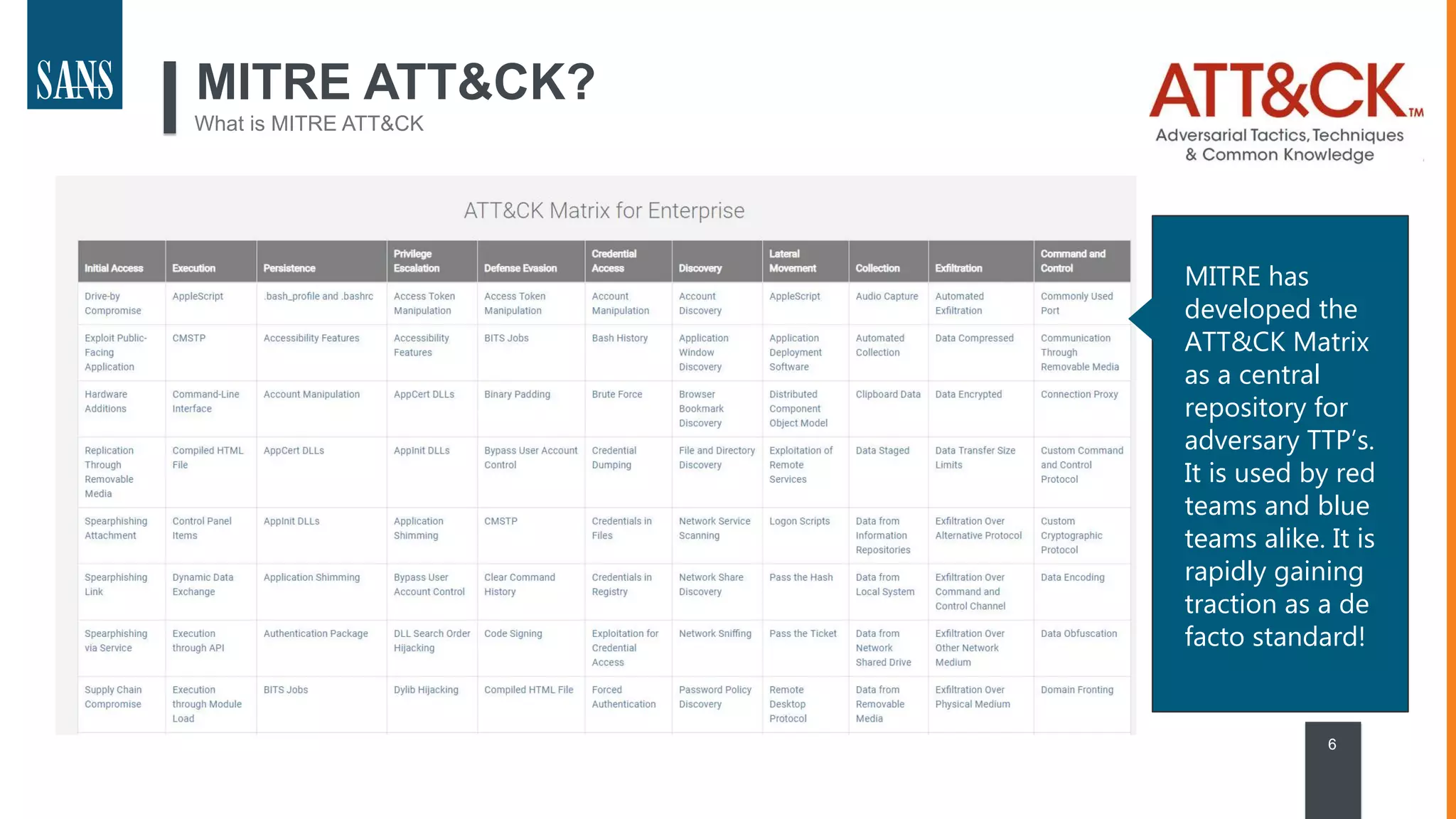
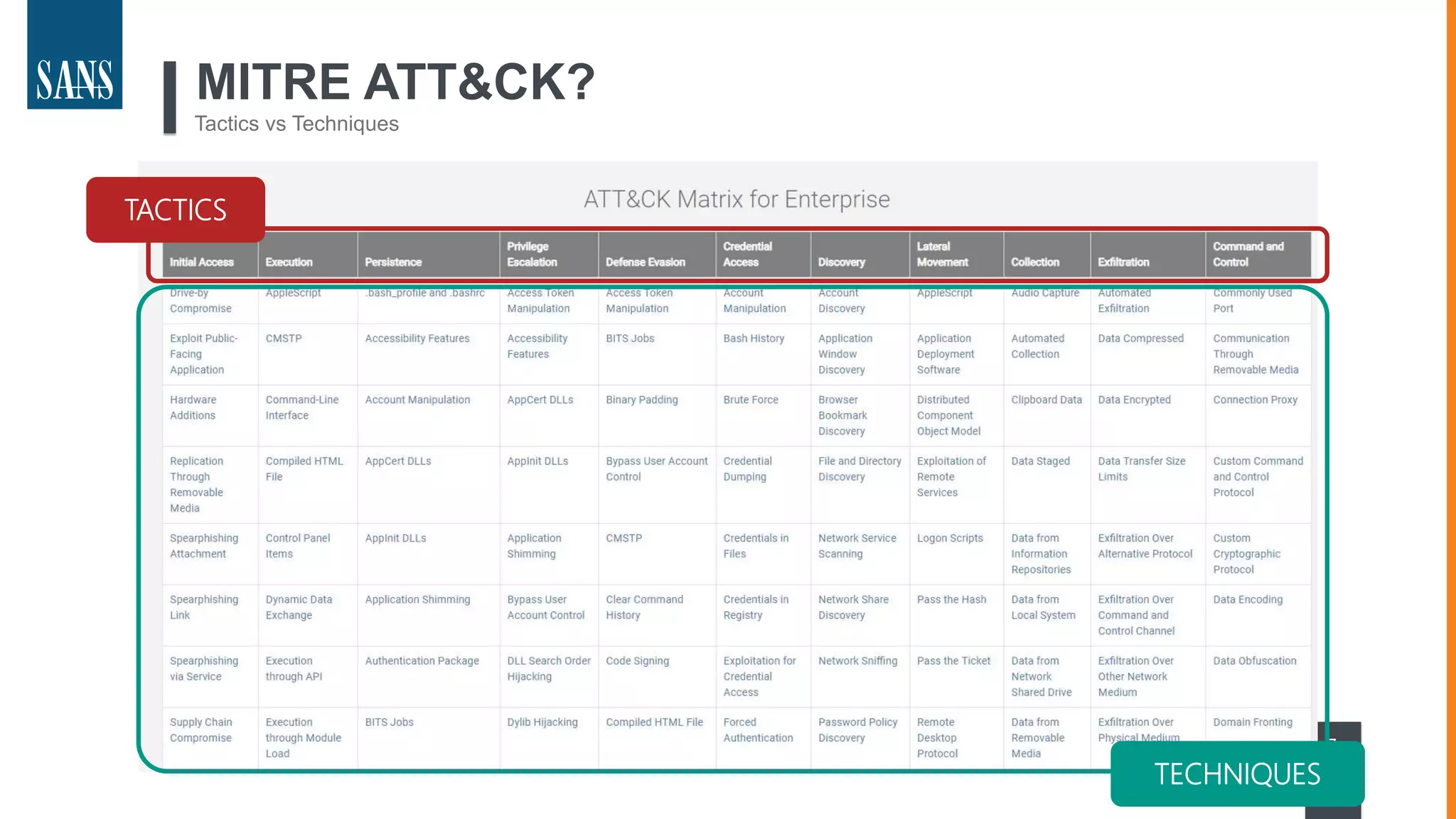
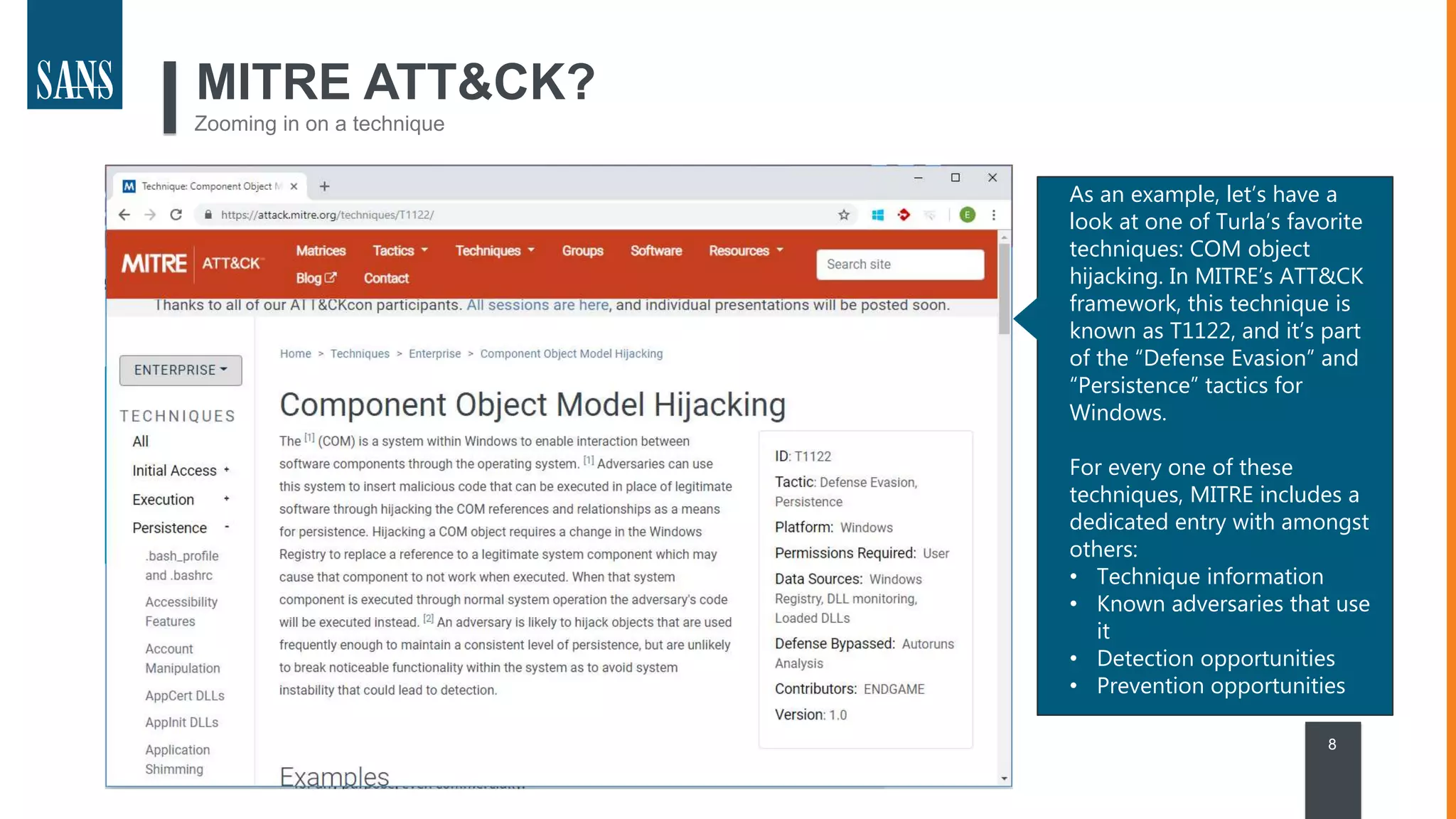
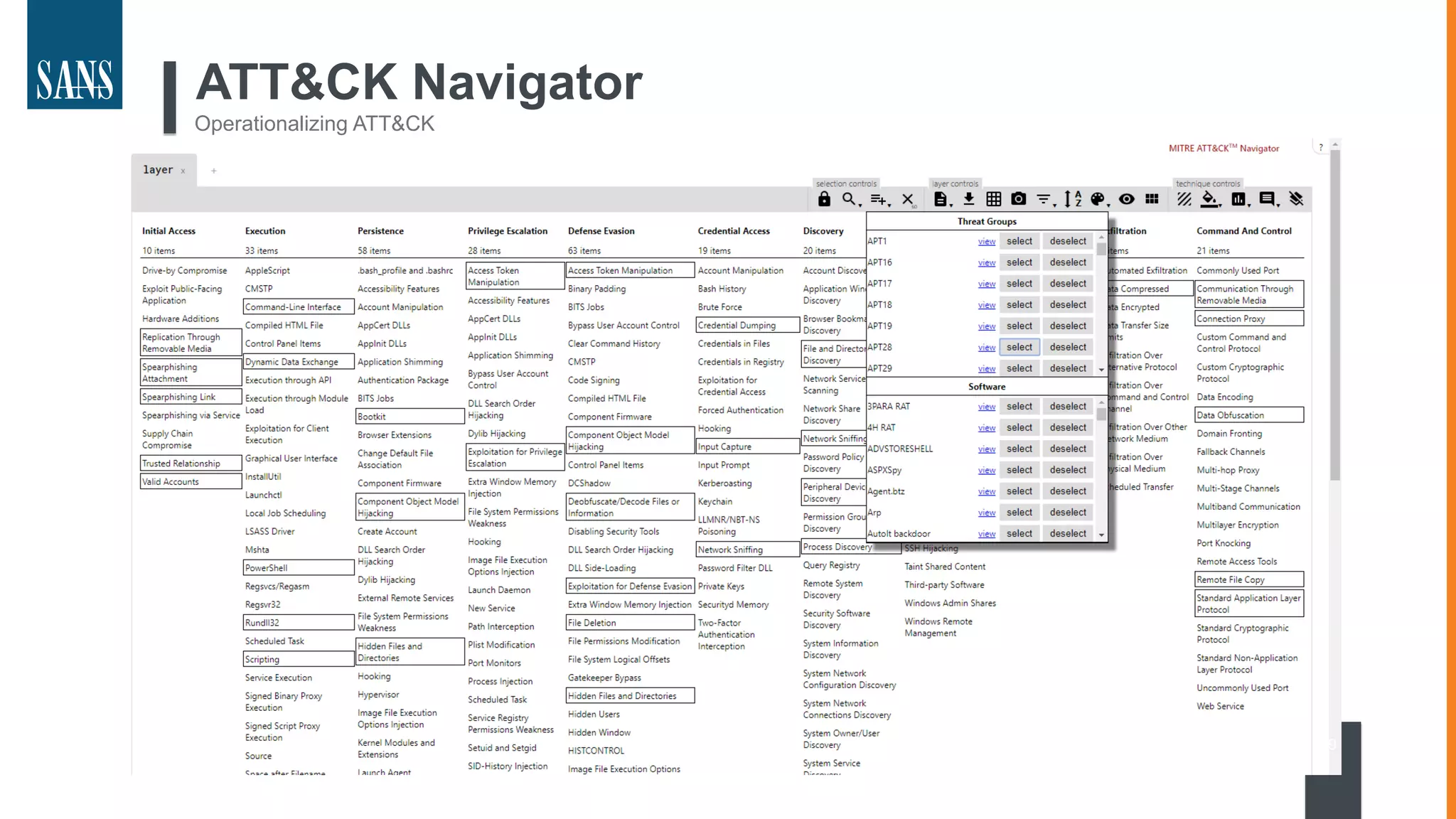
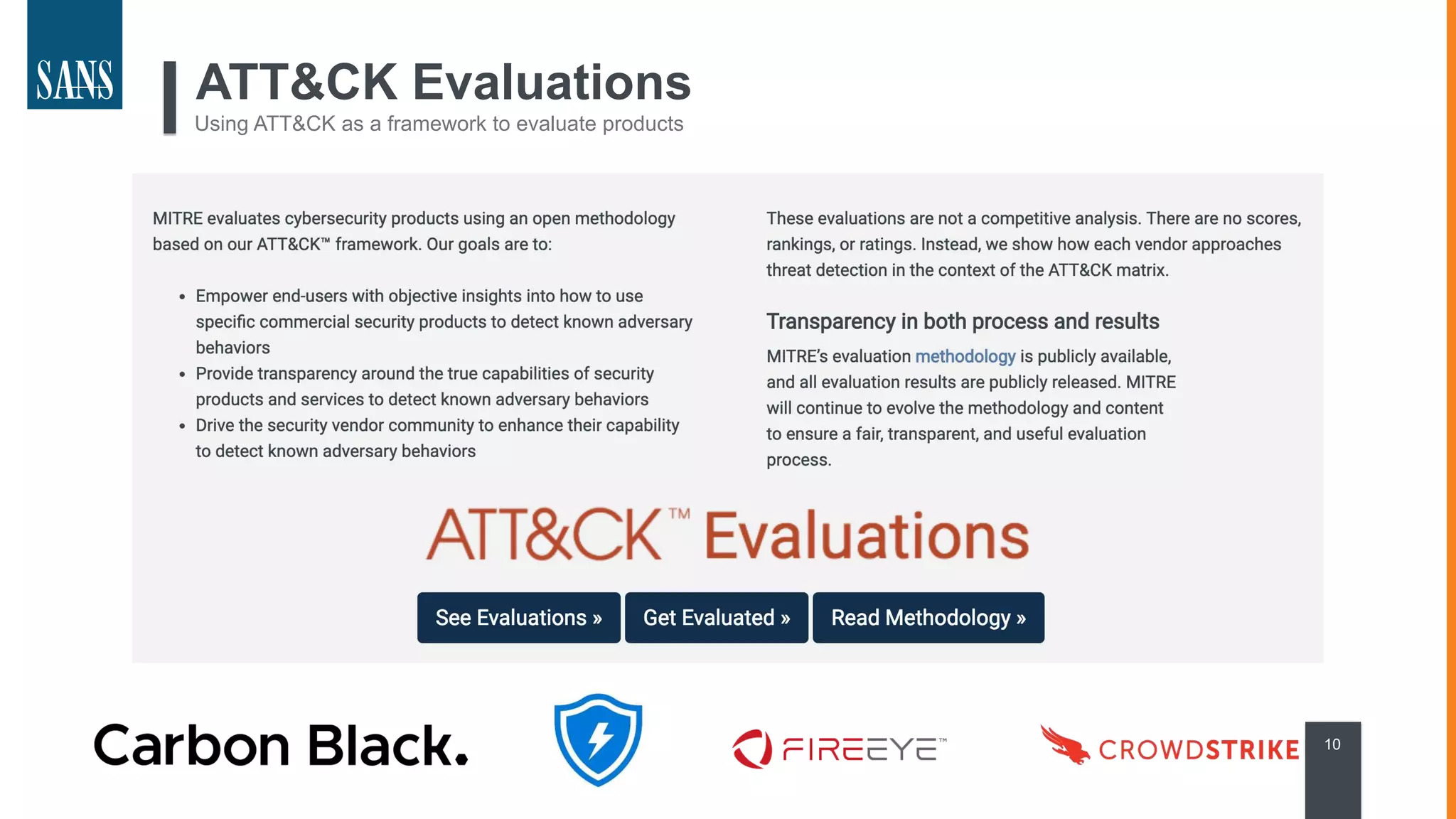
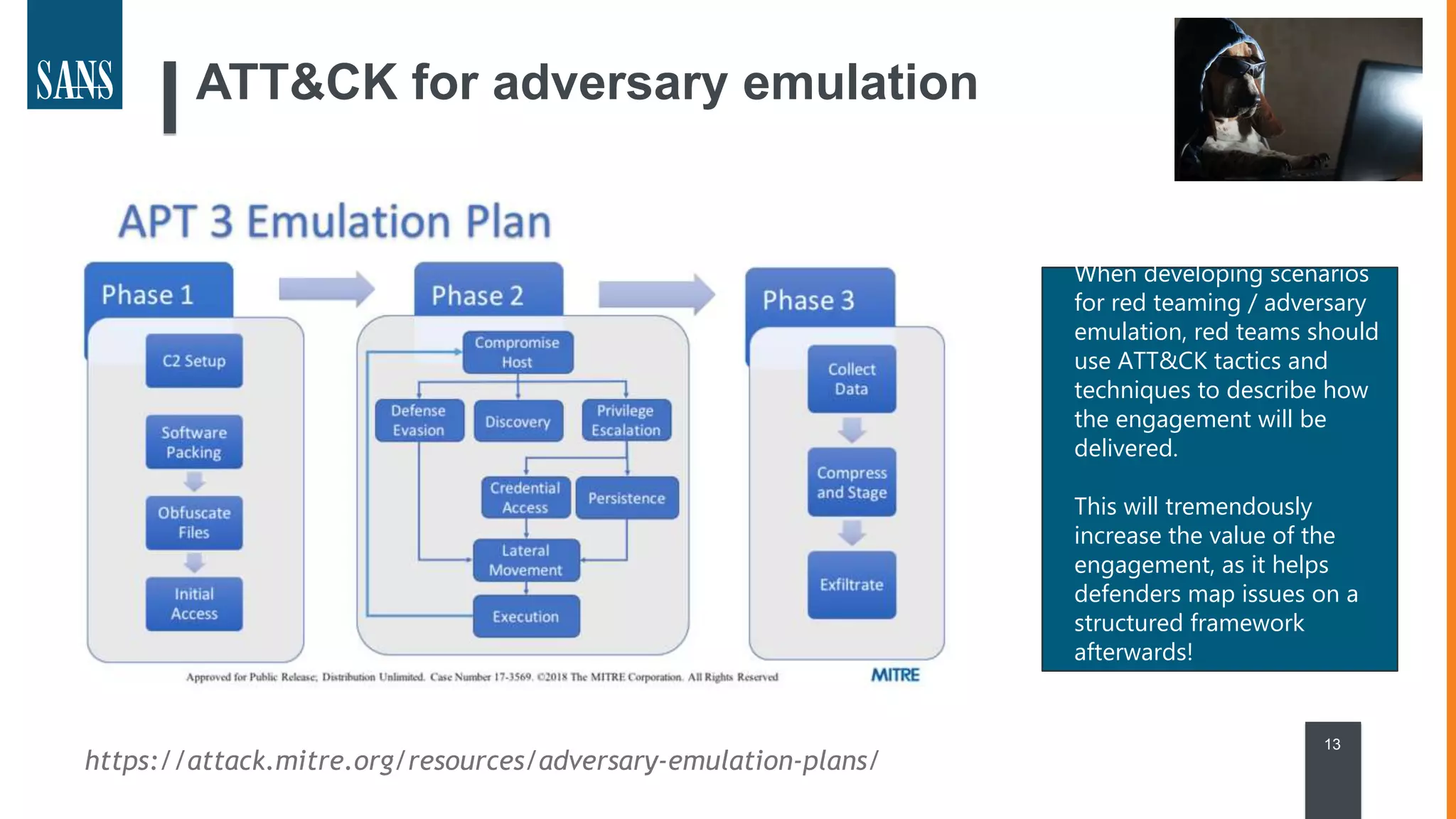
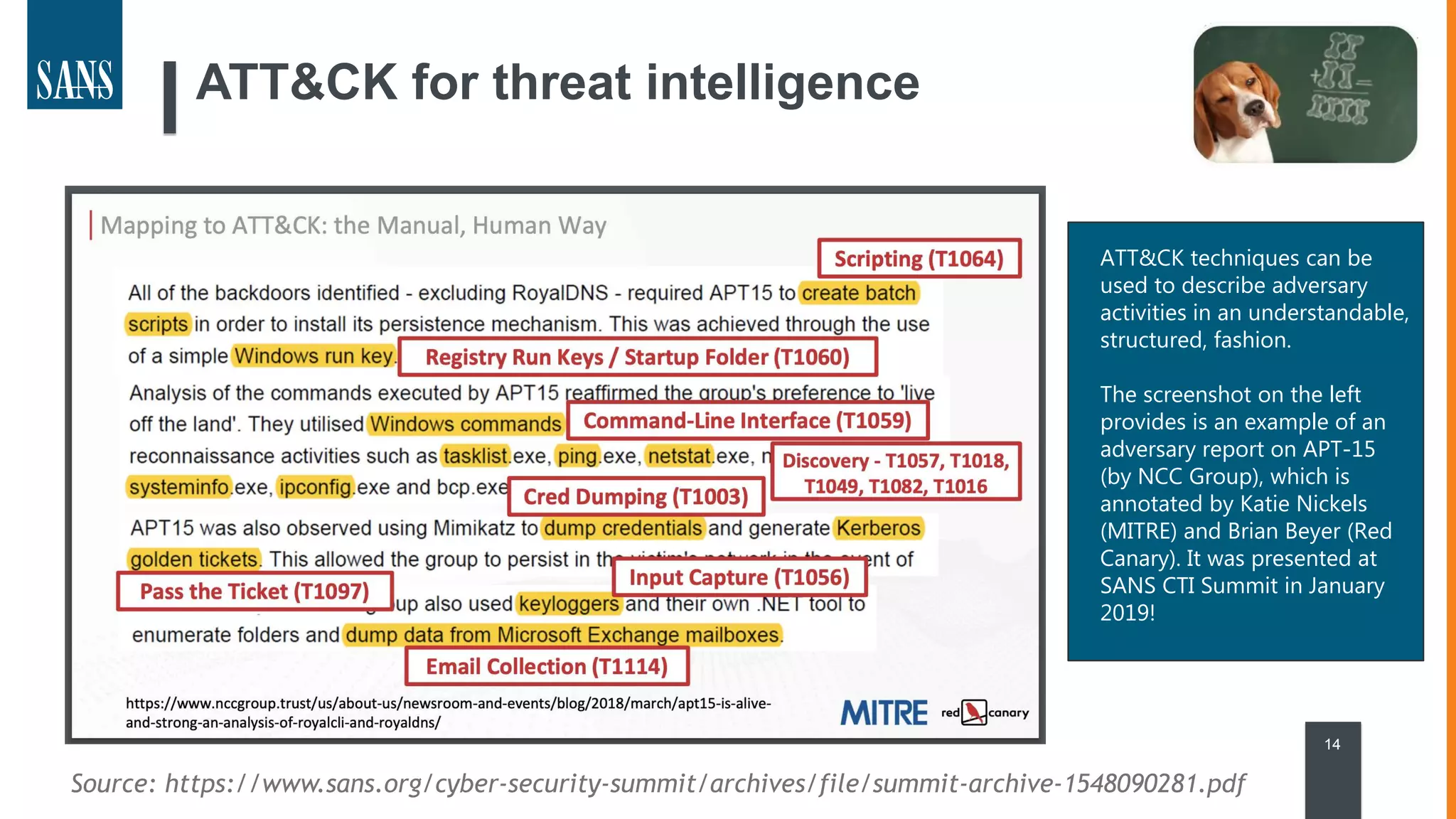
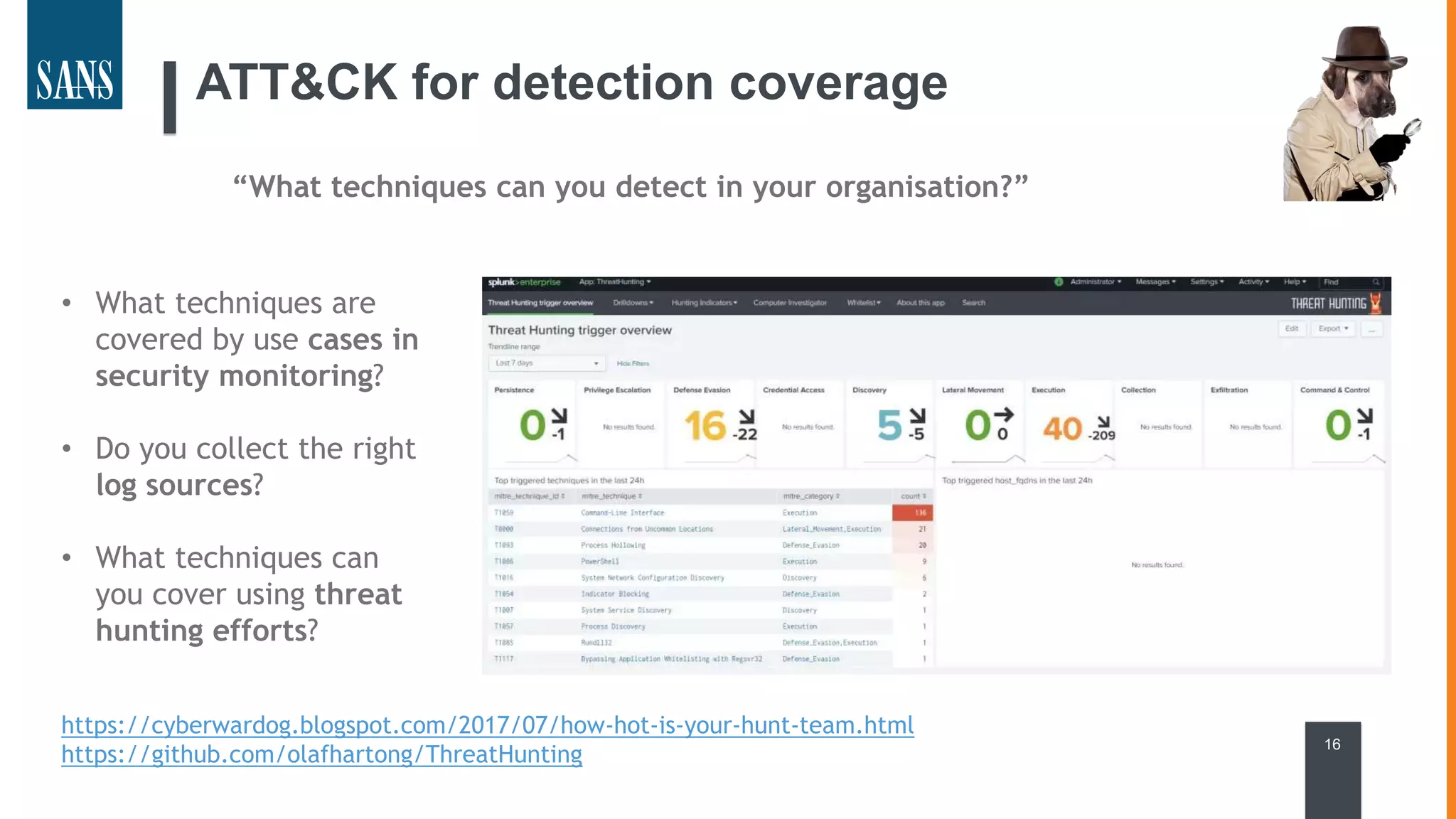
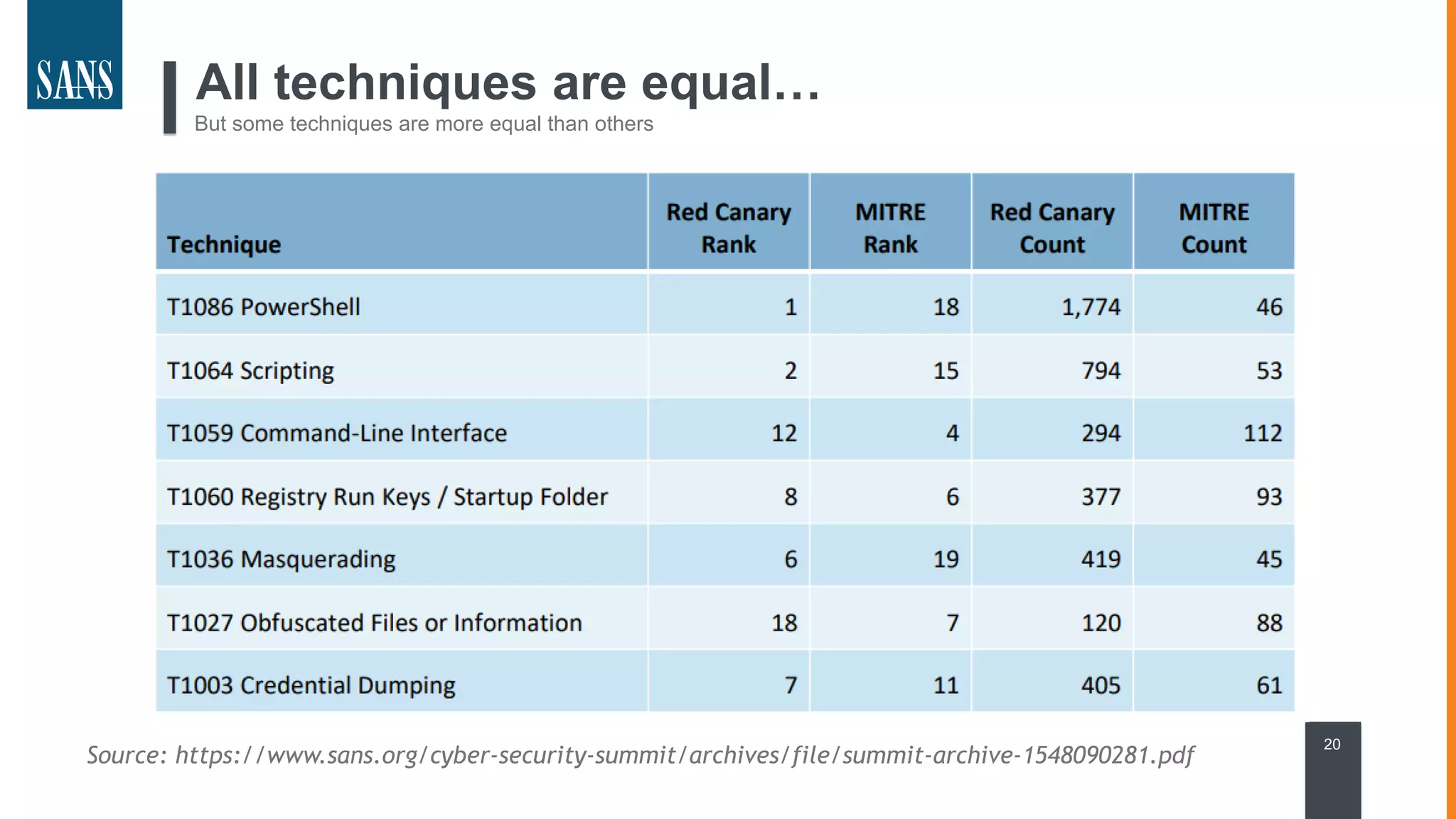
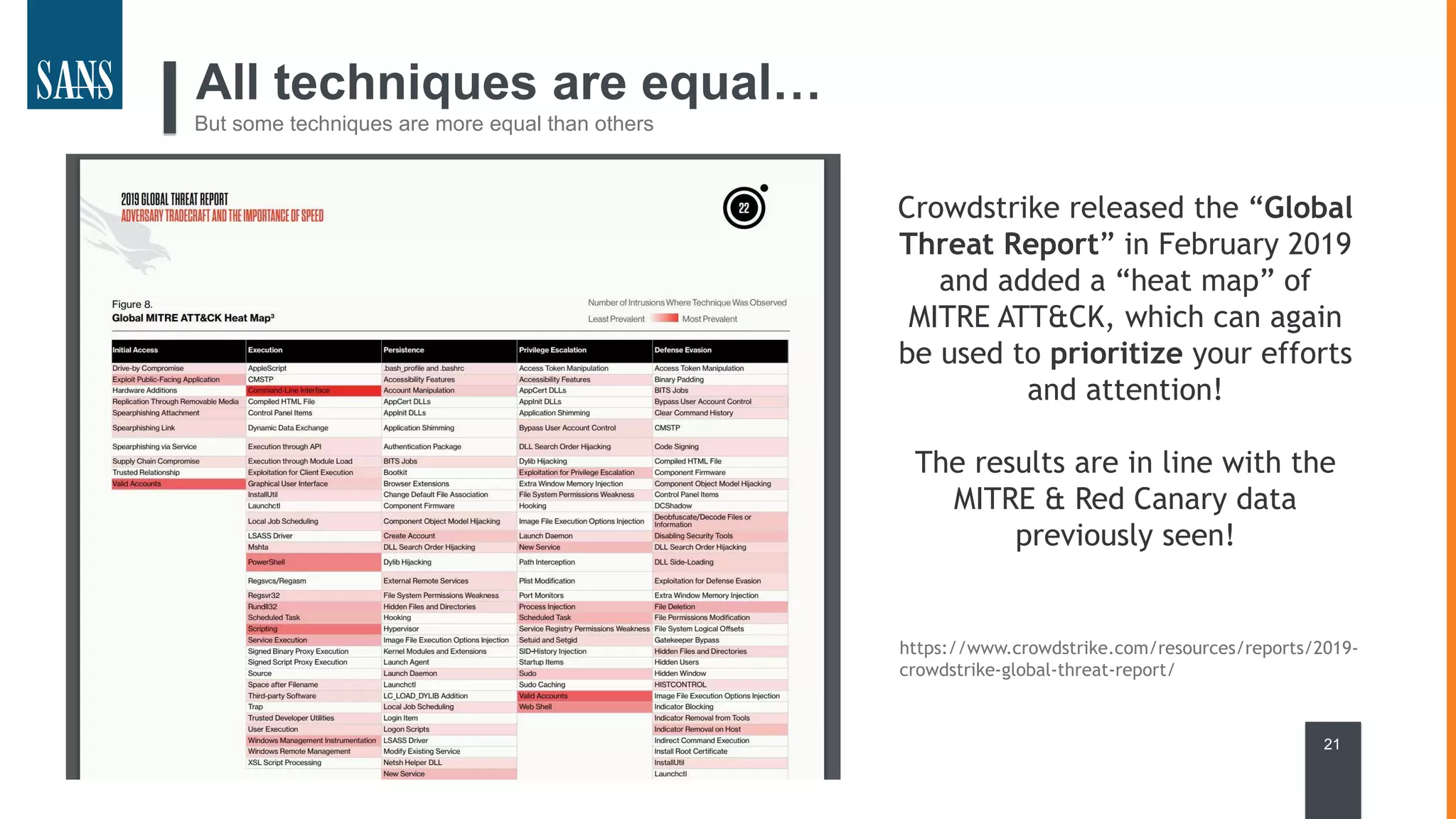
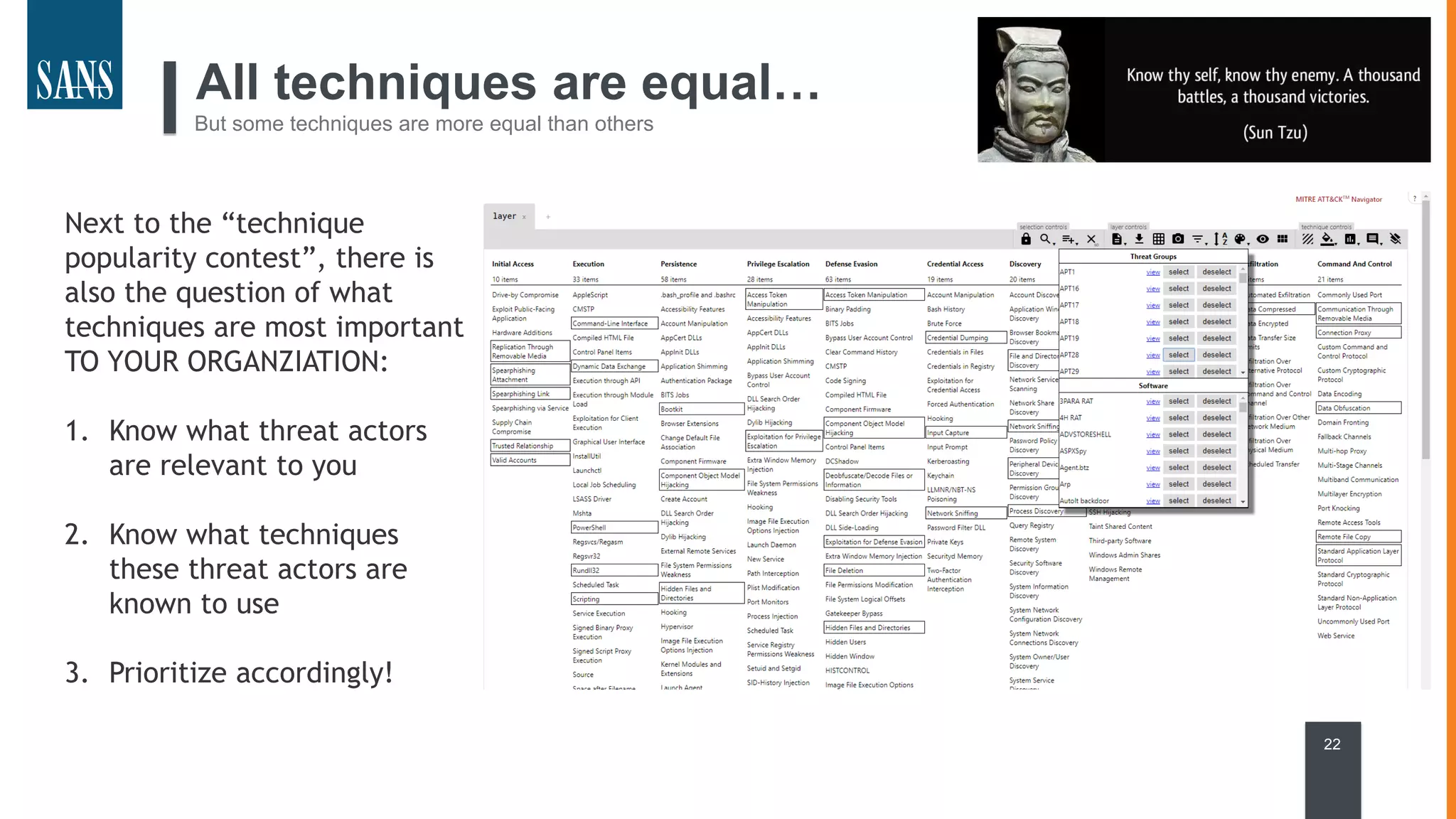
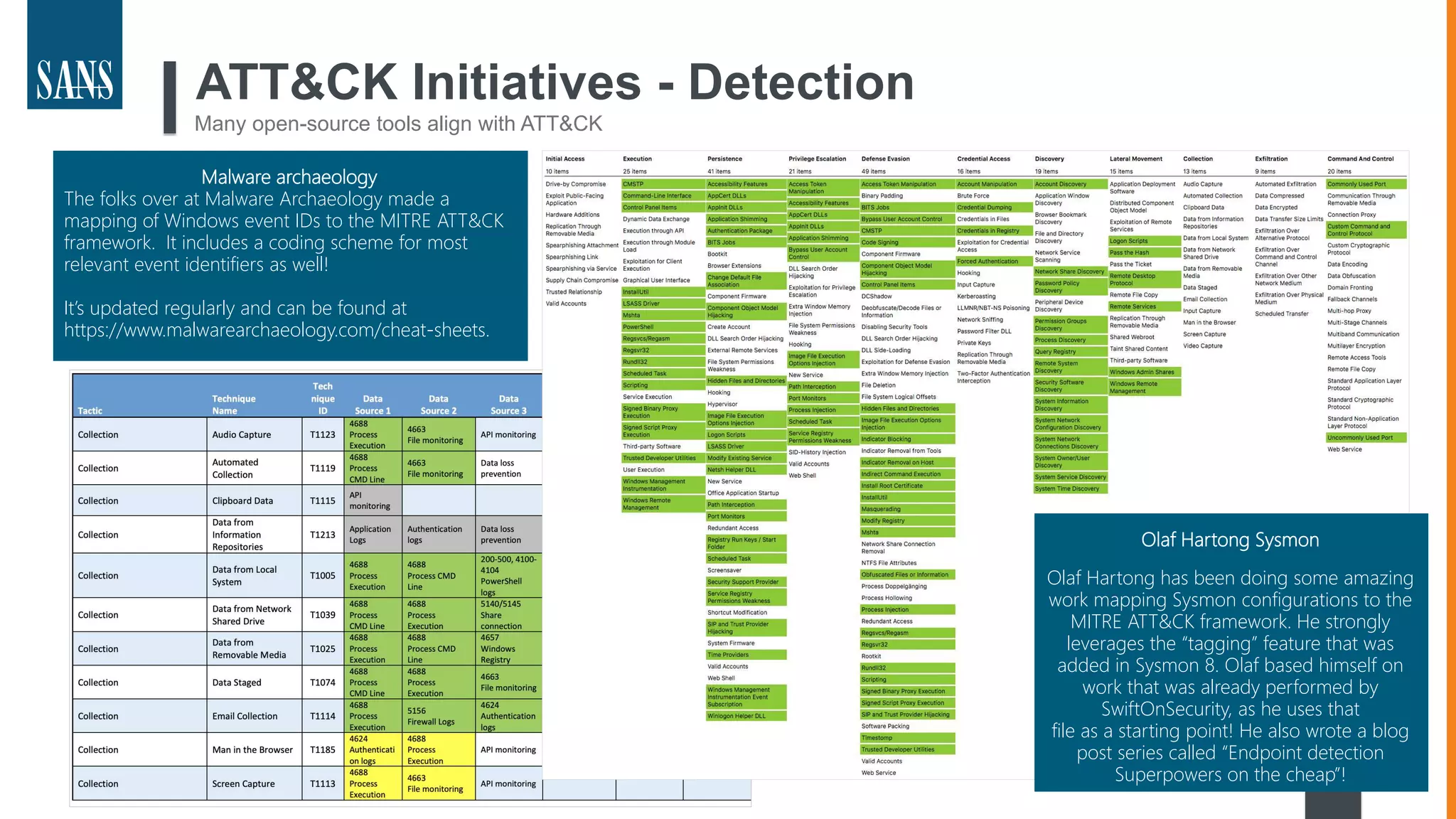
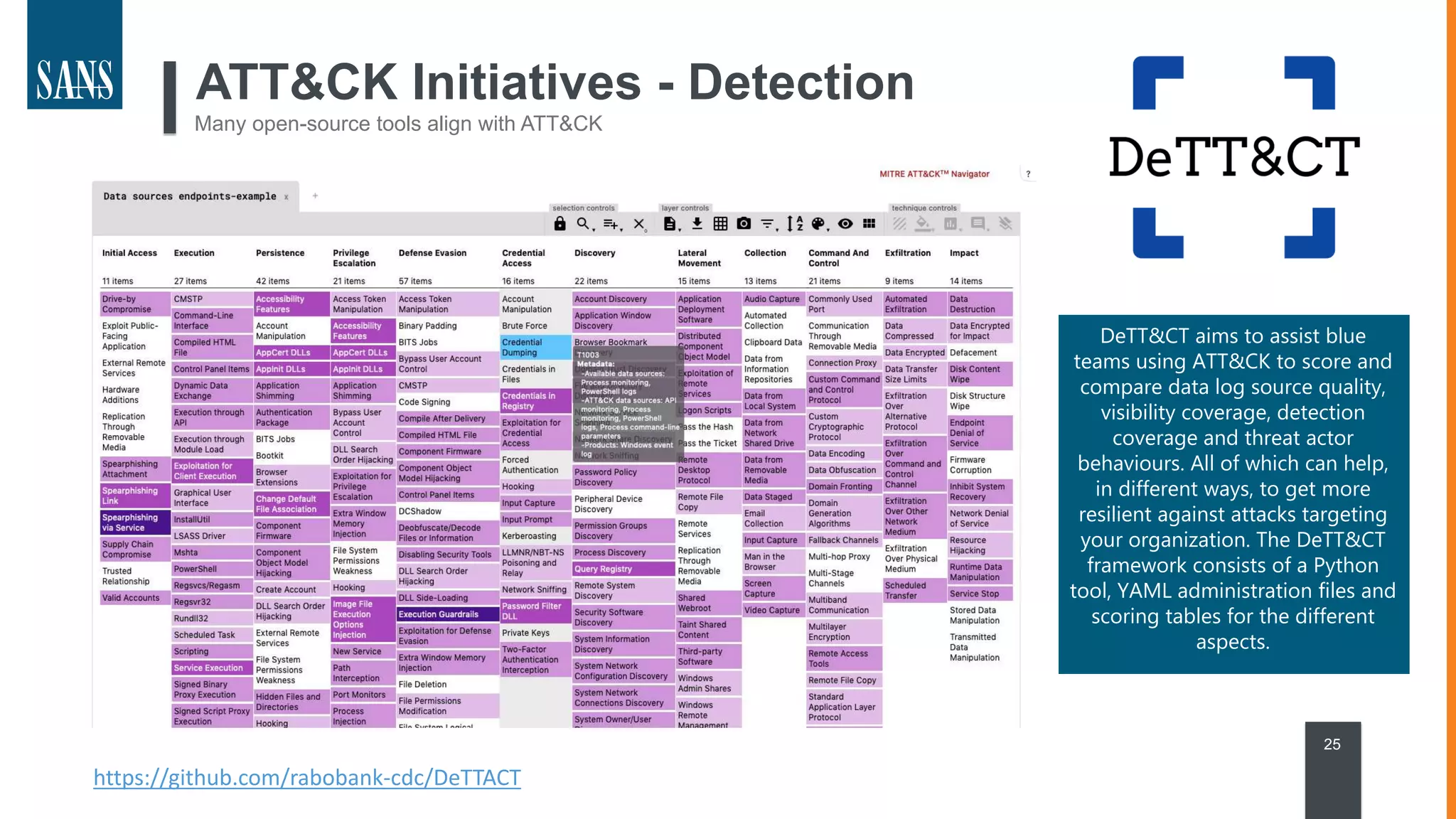
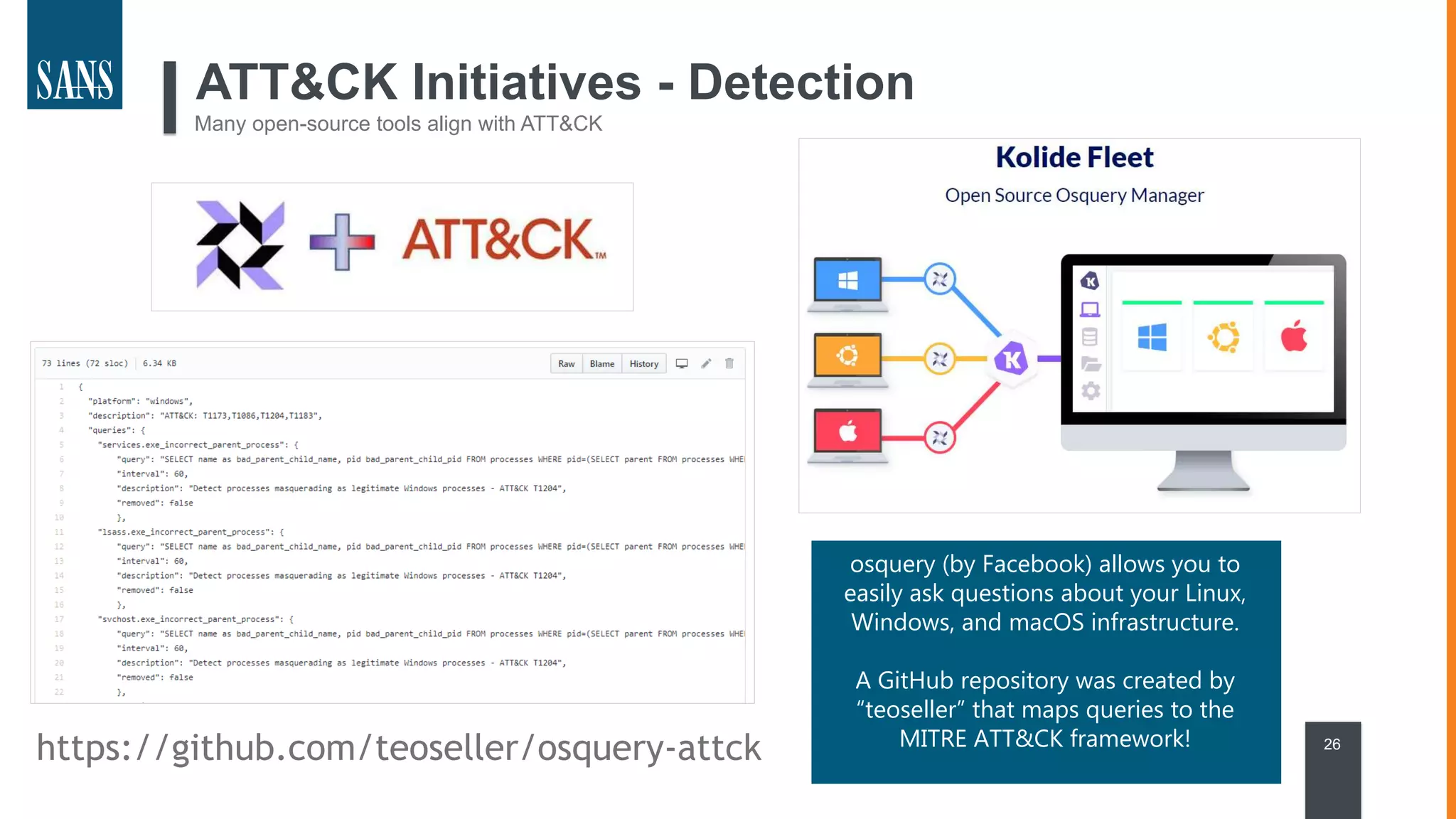
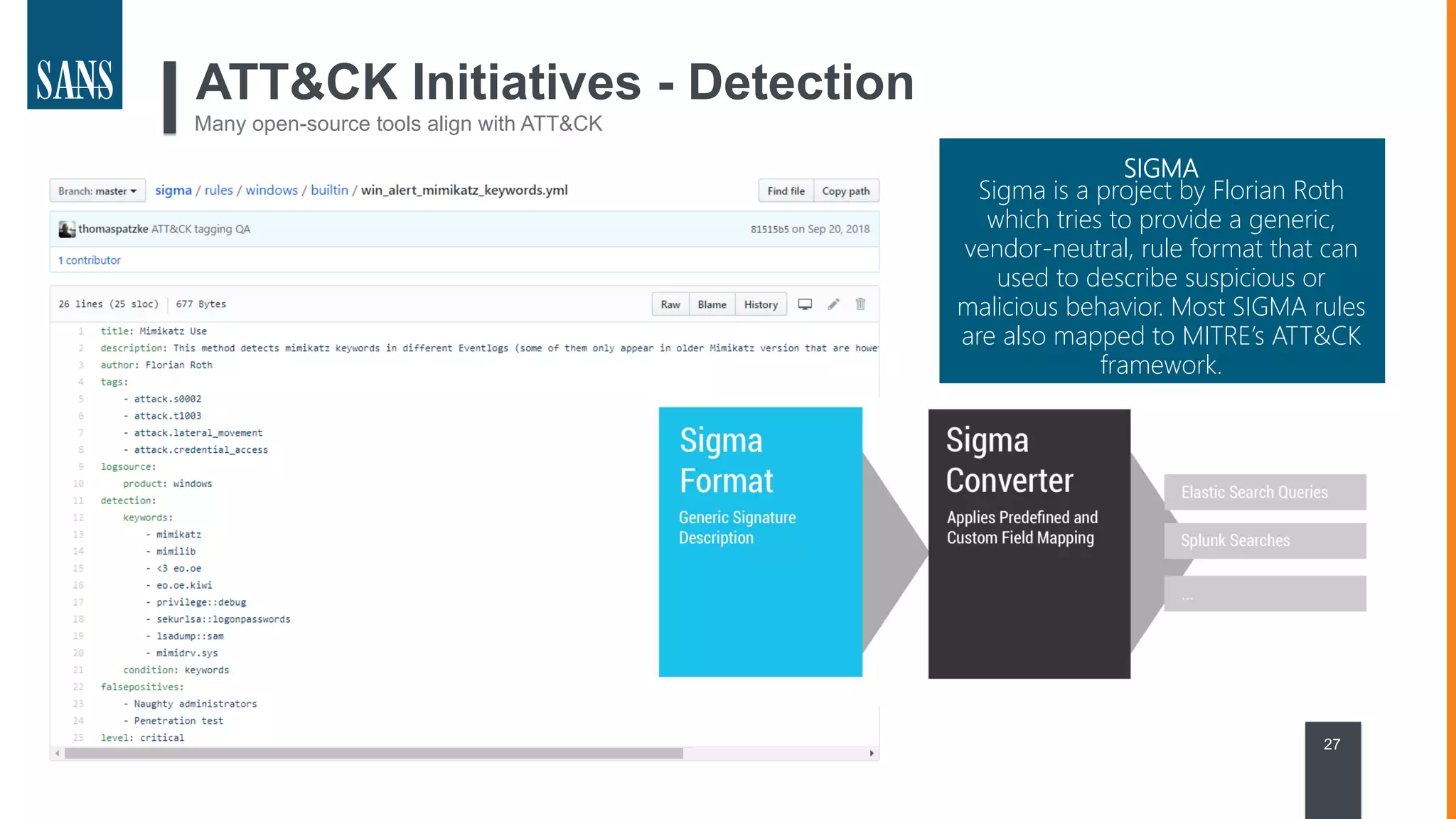
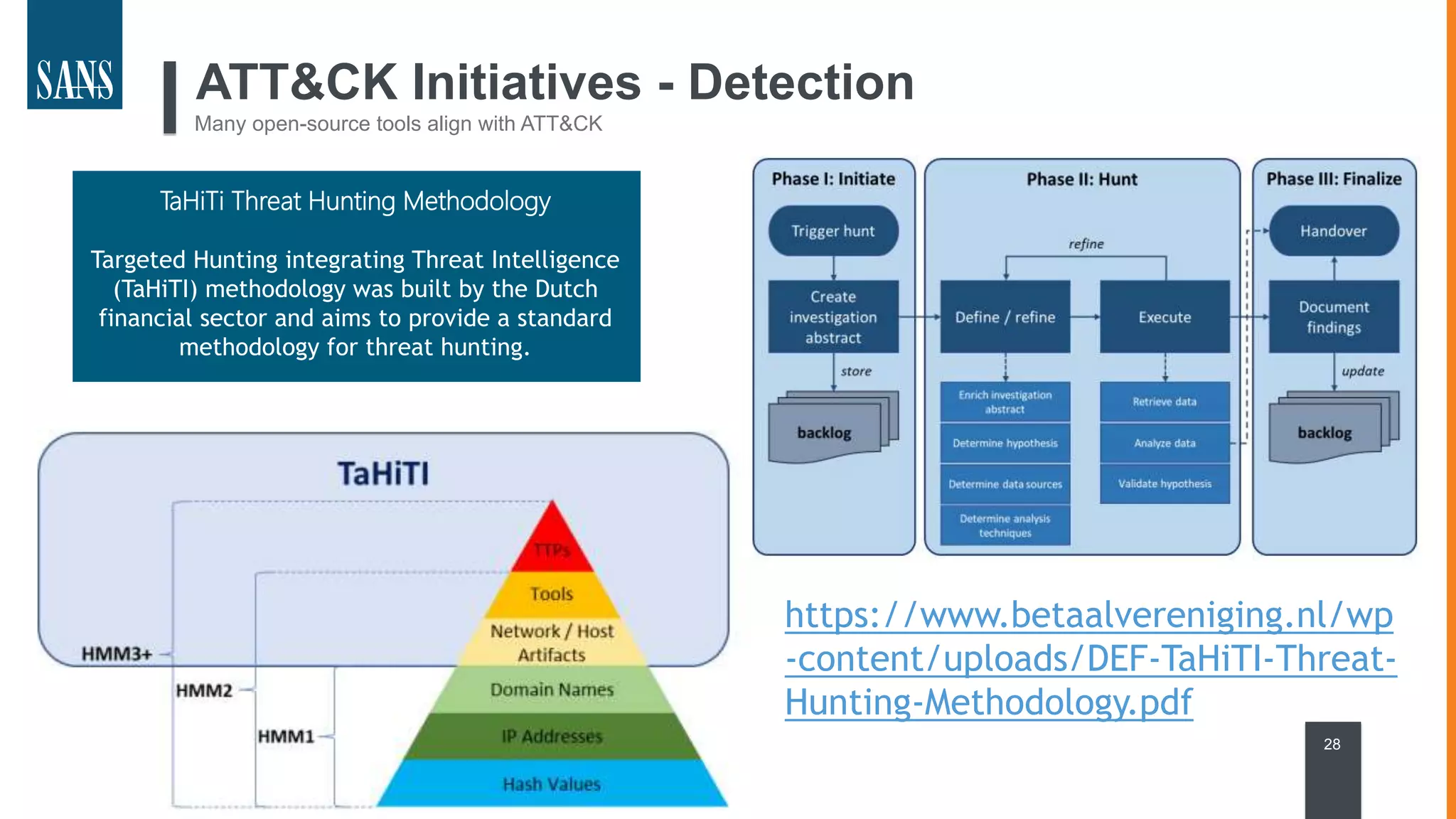
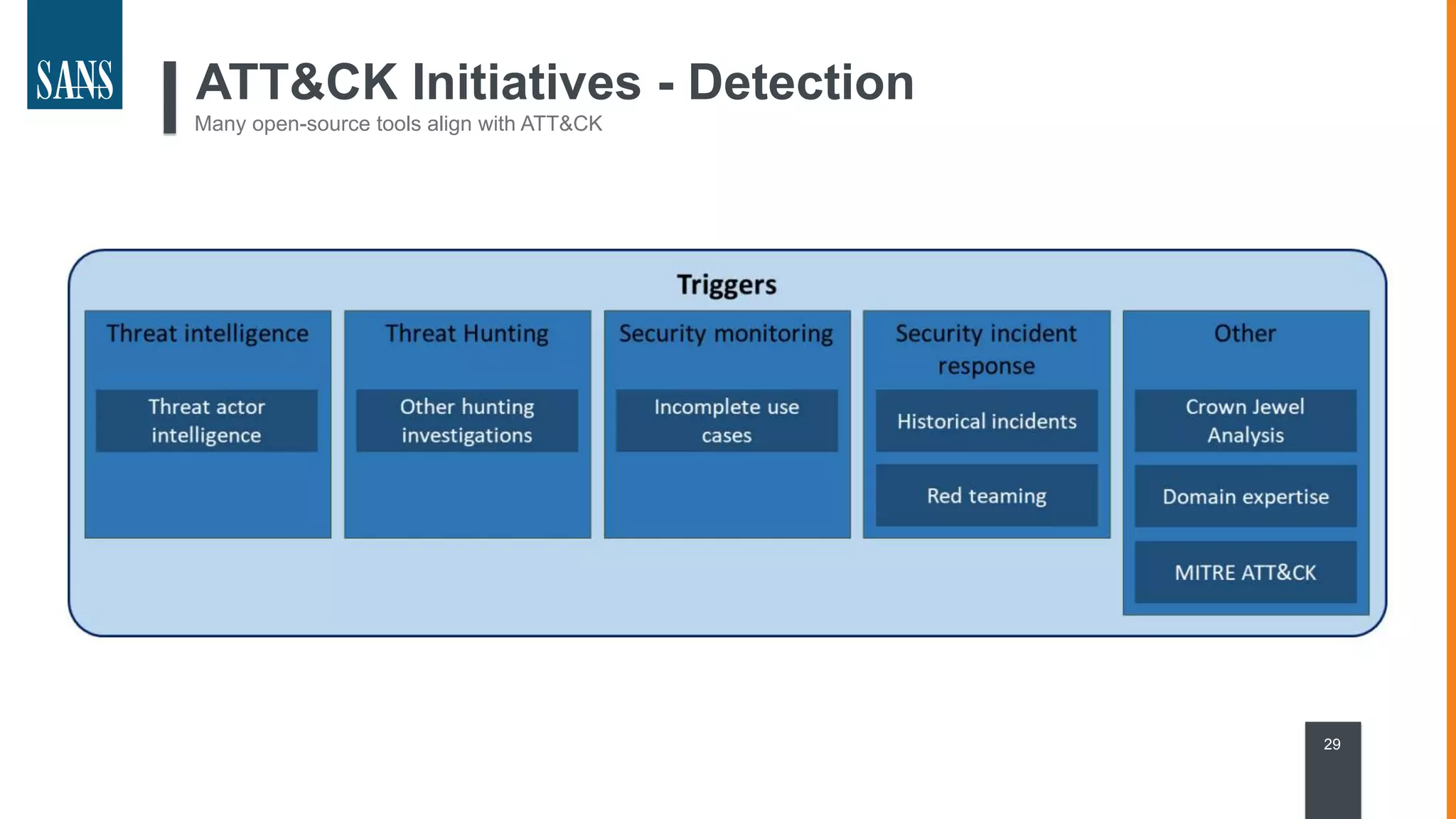
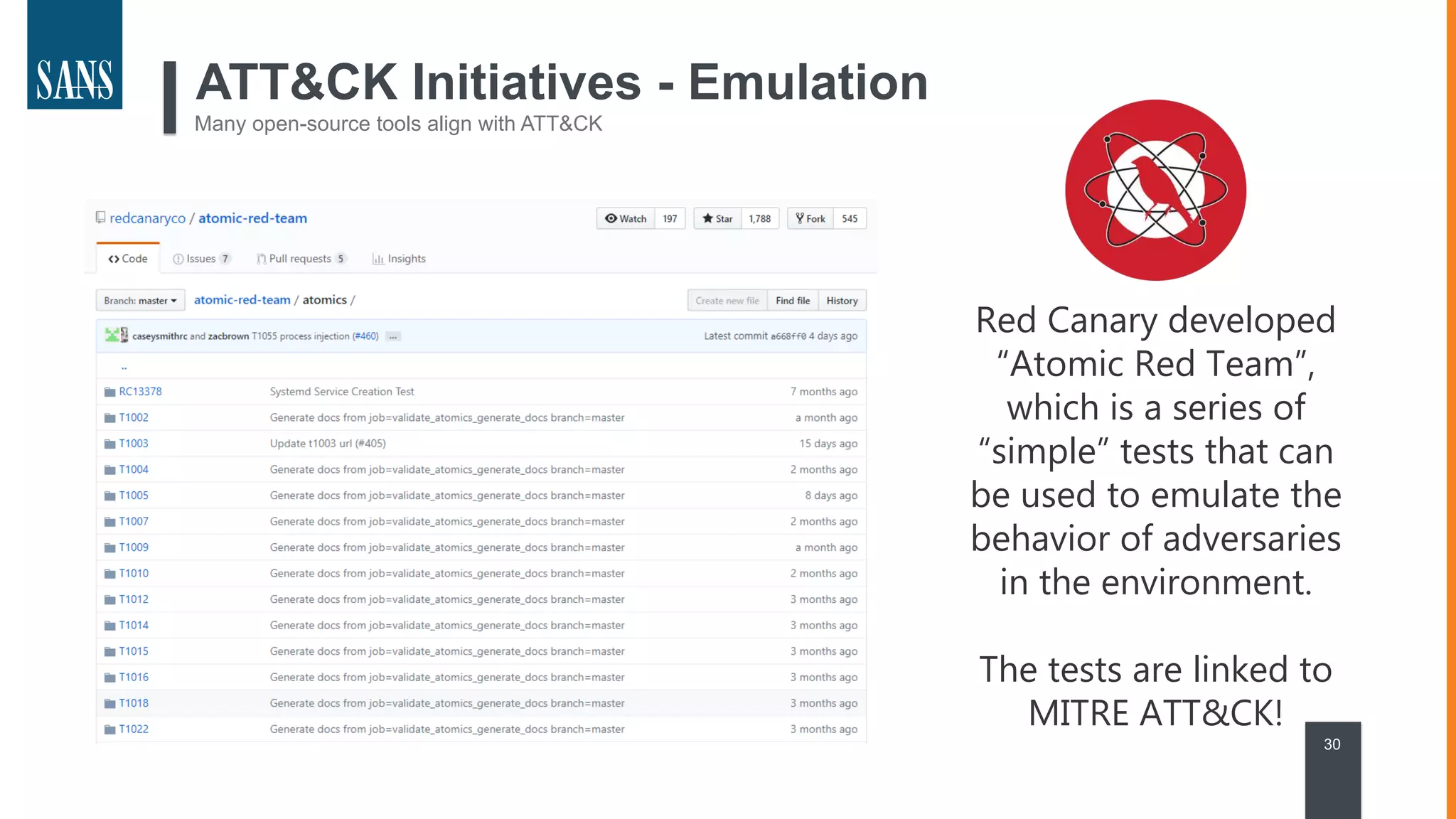
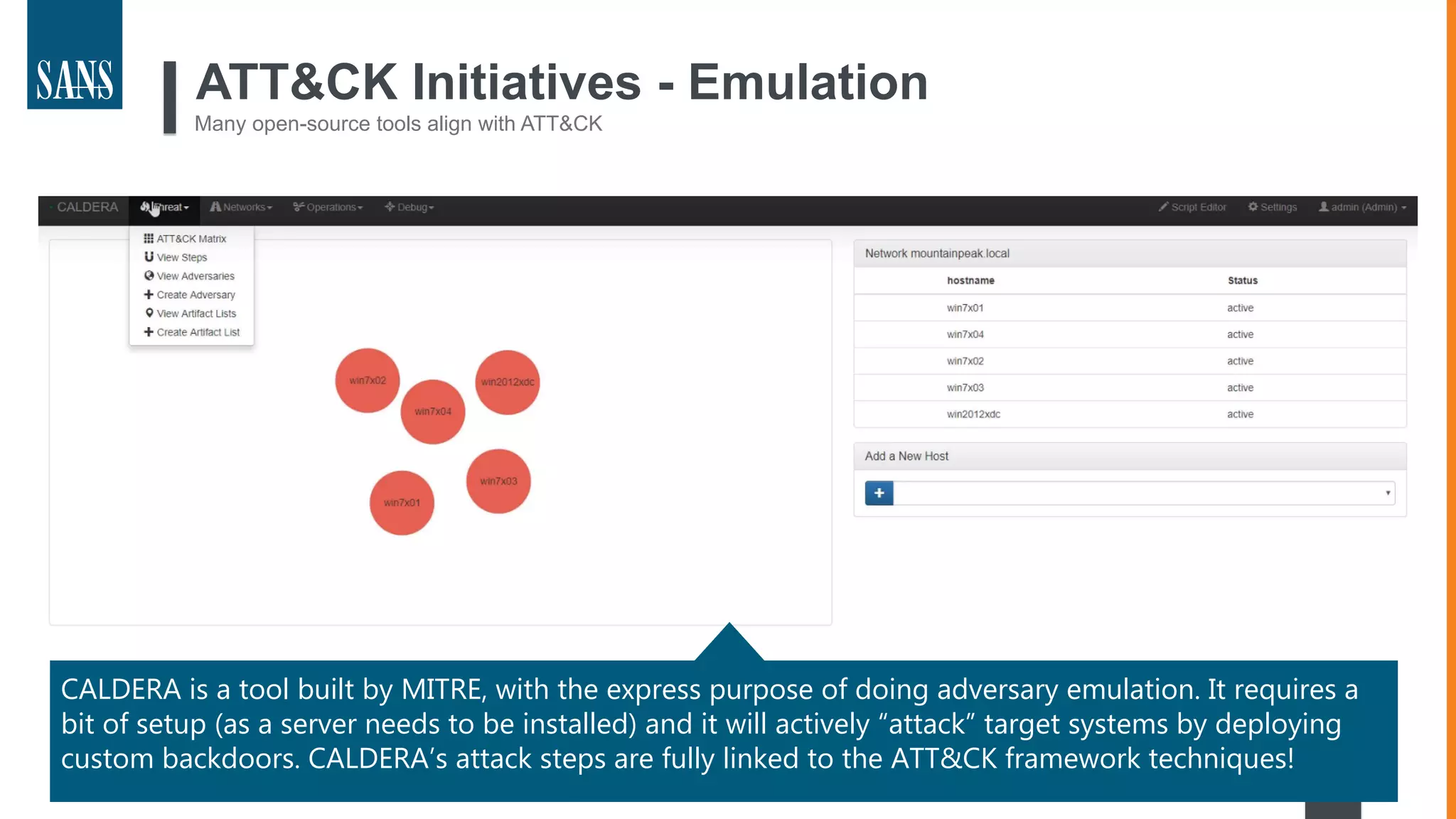
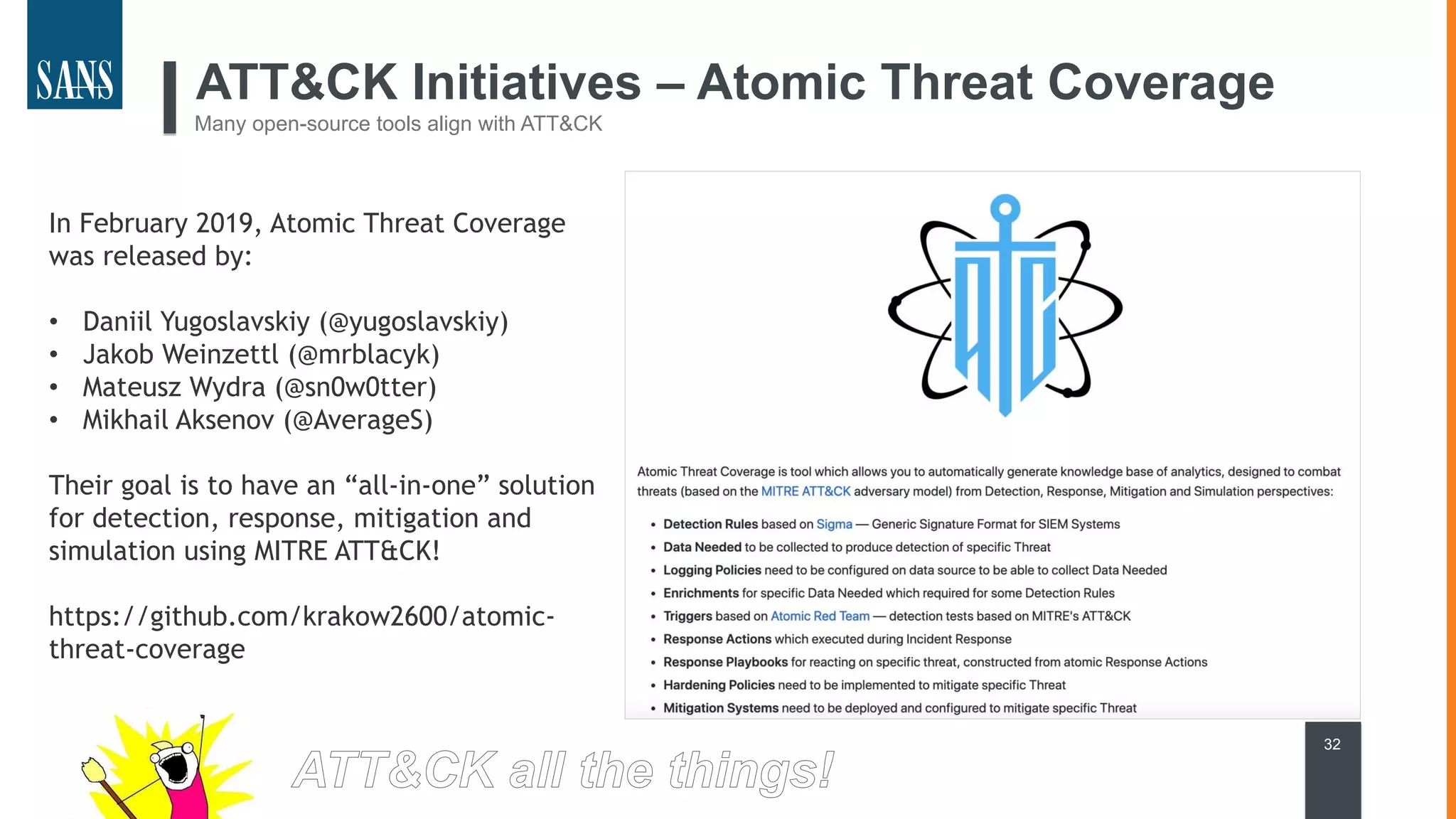
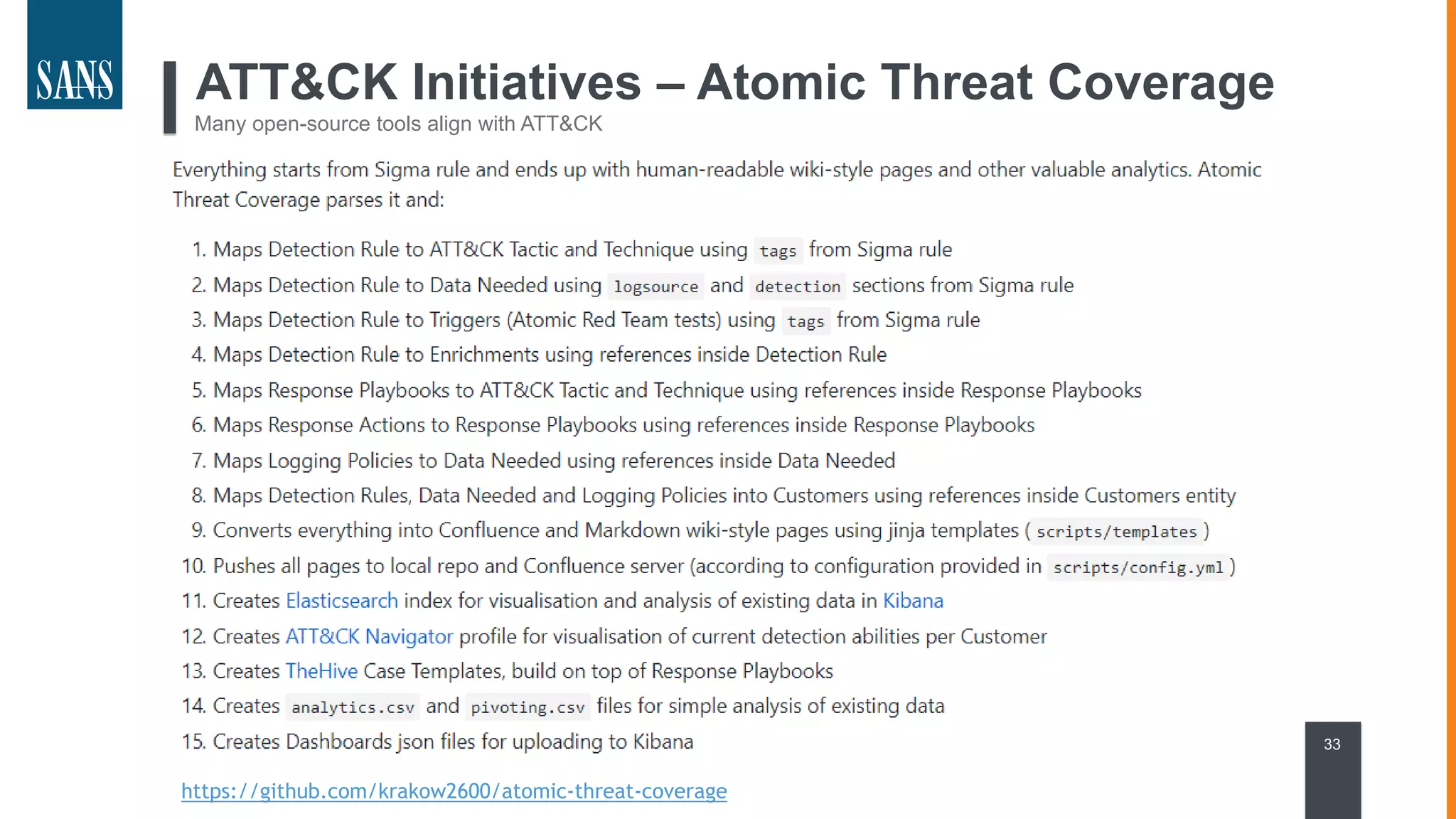
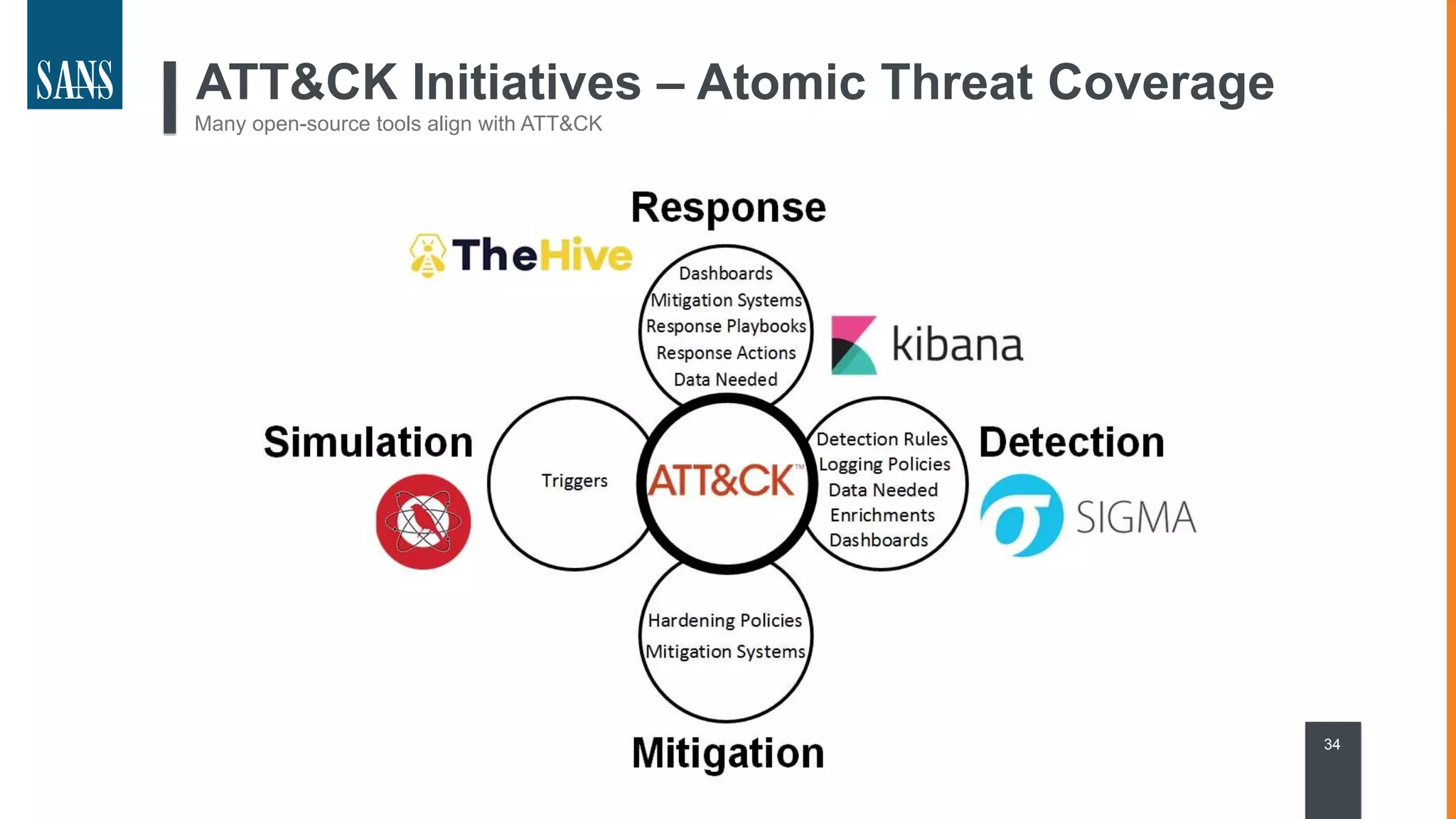
The document discusses the MITRE ATT&CK framework, emphasizing its significance as a central repository for adversary tactics, techniques, and procedures (TTPs). It outlines the framework's use cases, such as adversary emulation, threat intelligence, and defense prioritization, and highlights common pitfalls in its application. Additionally, it mentions various initiatives and tools that align with the ATT&CK framework to enhance security operations and threat detection.