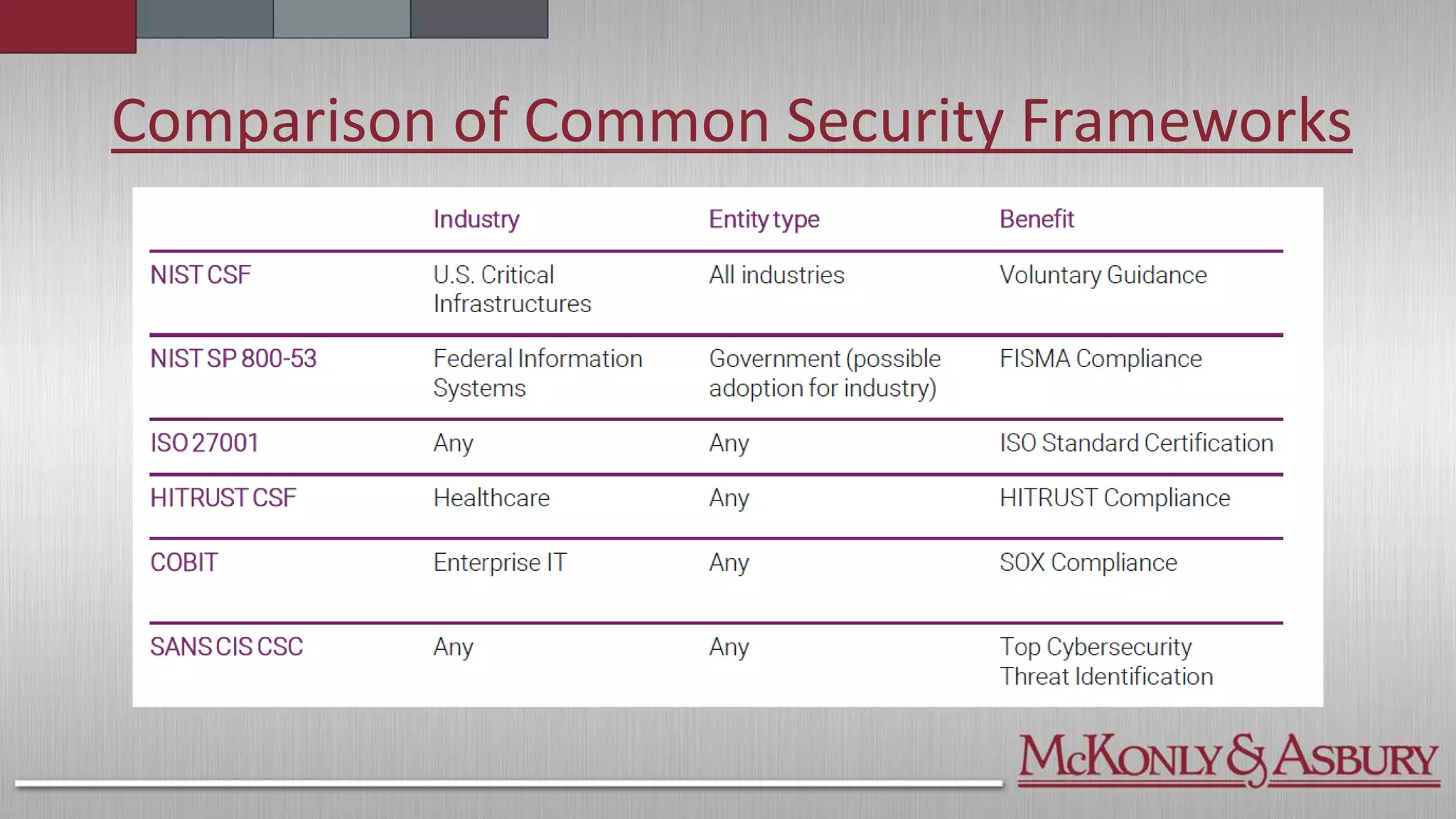
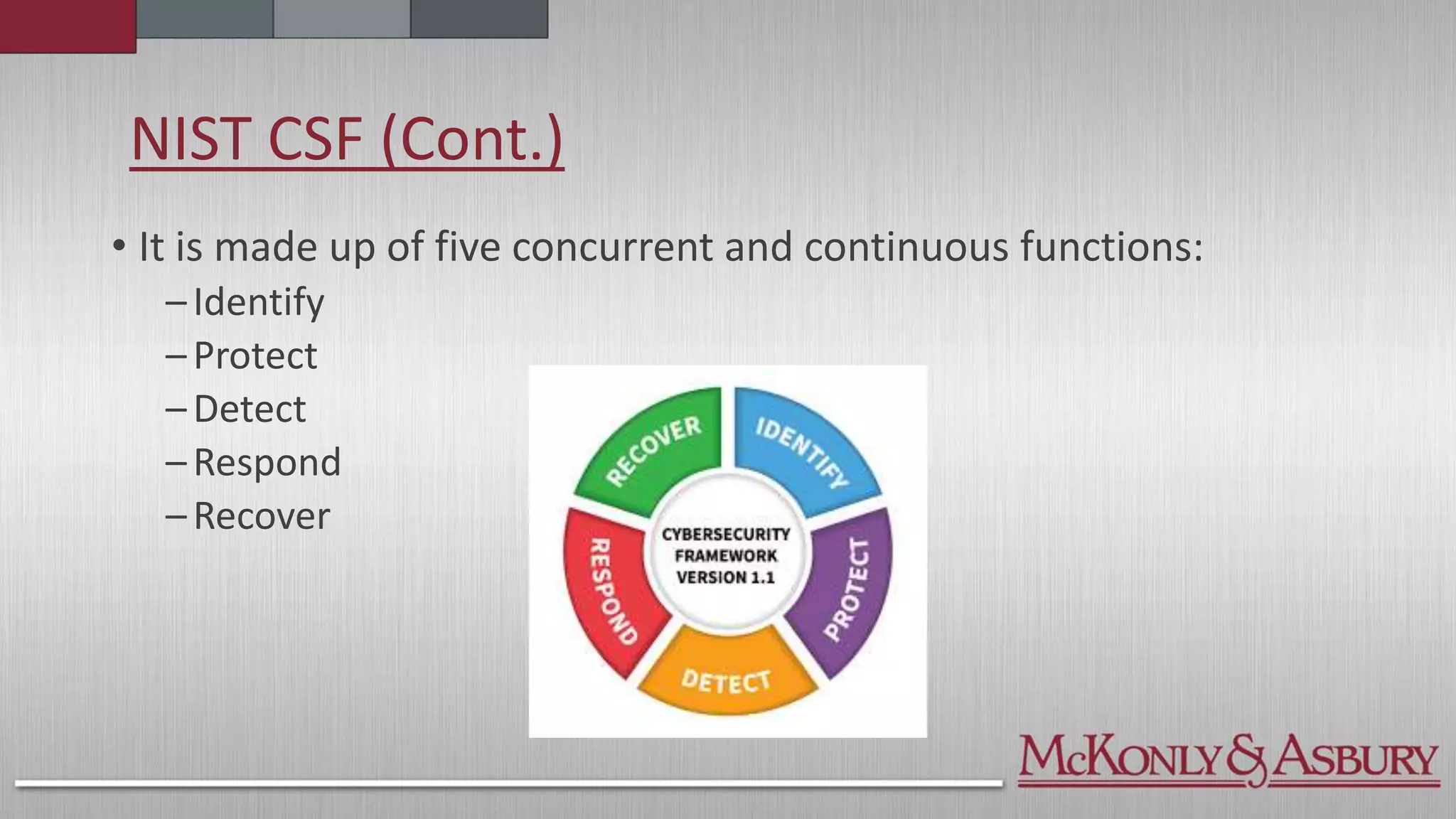
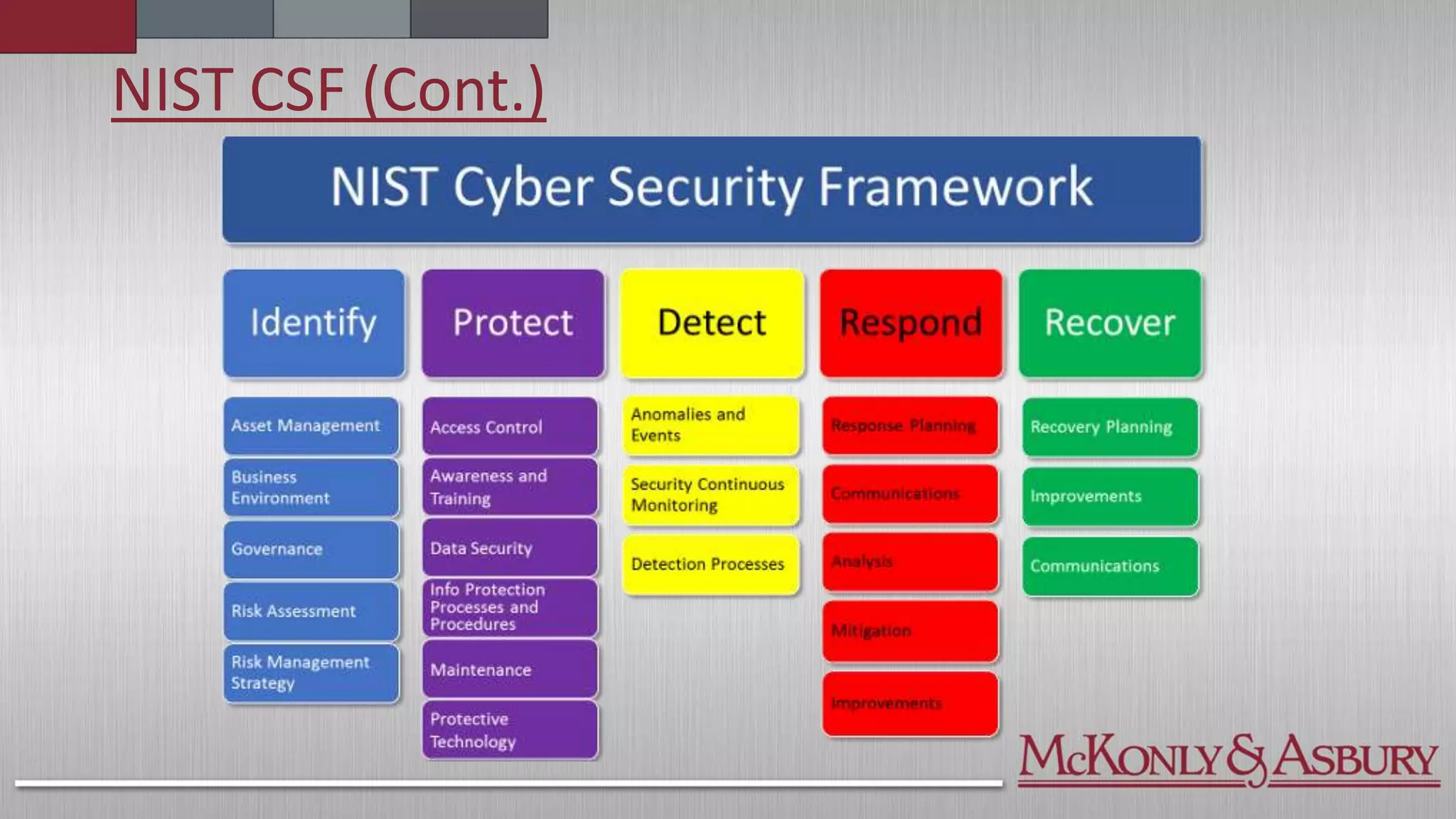
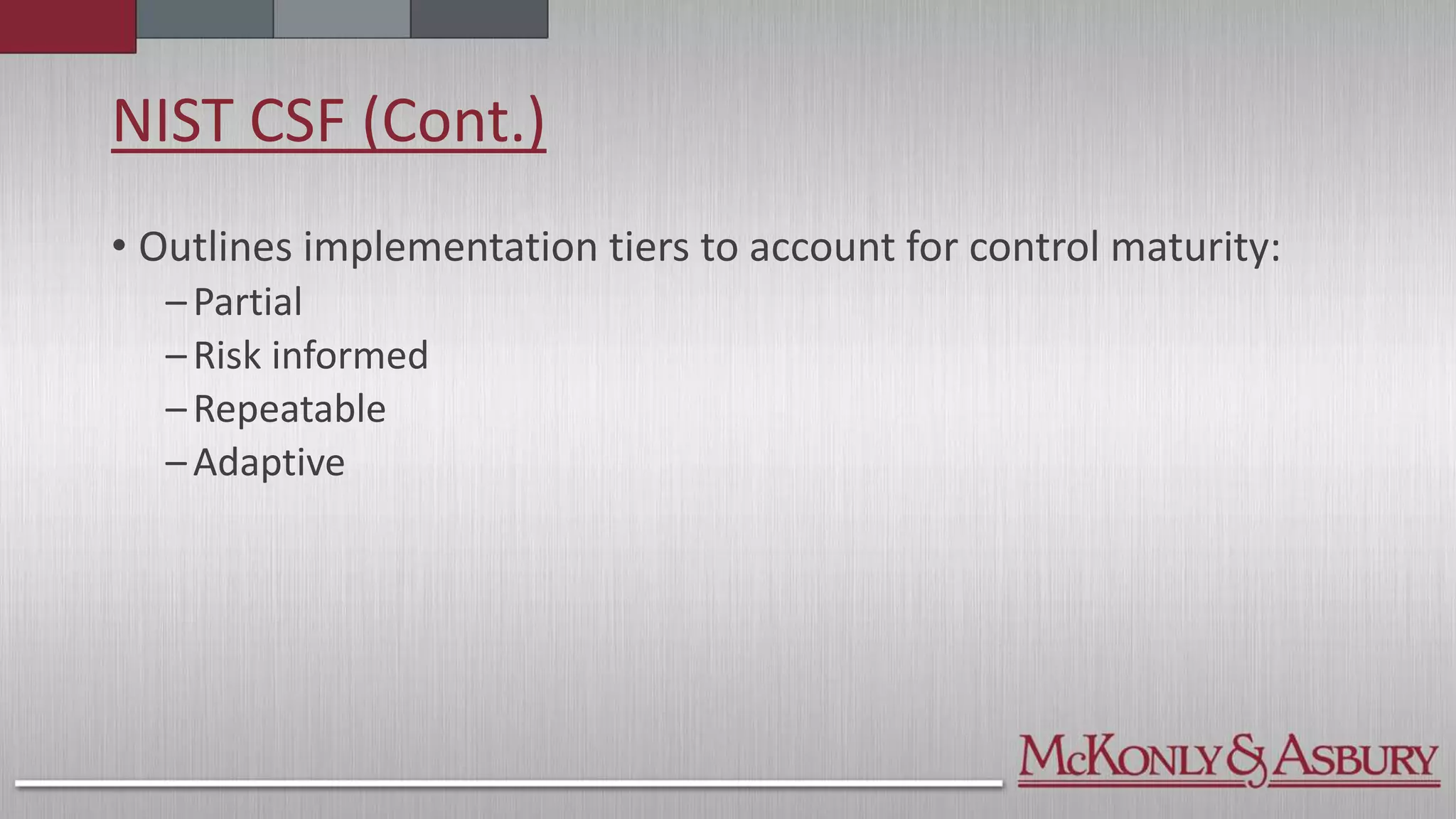
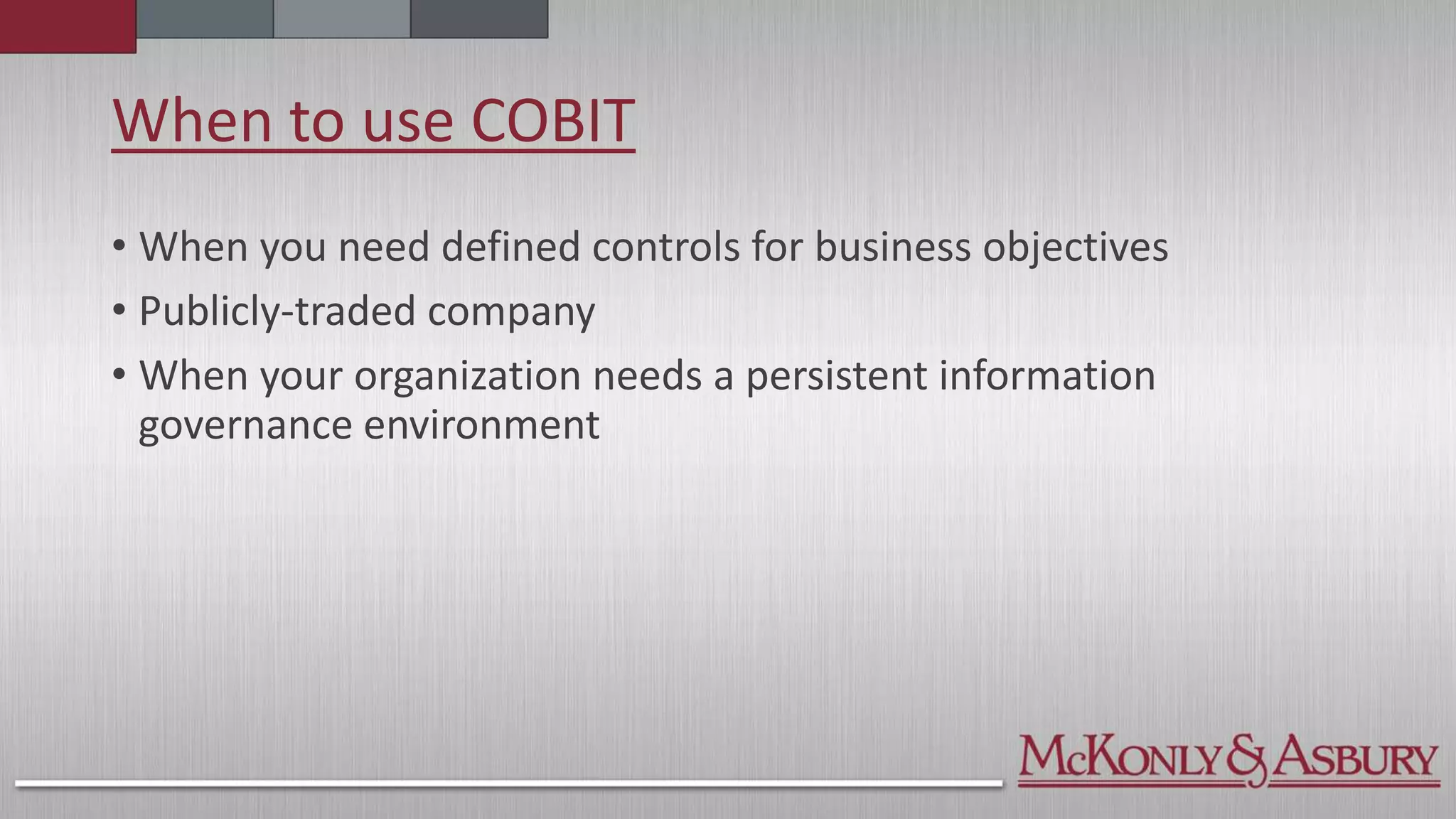
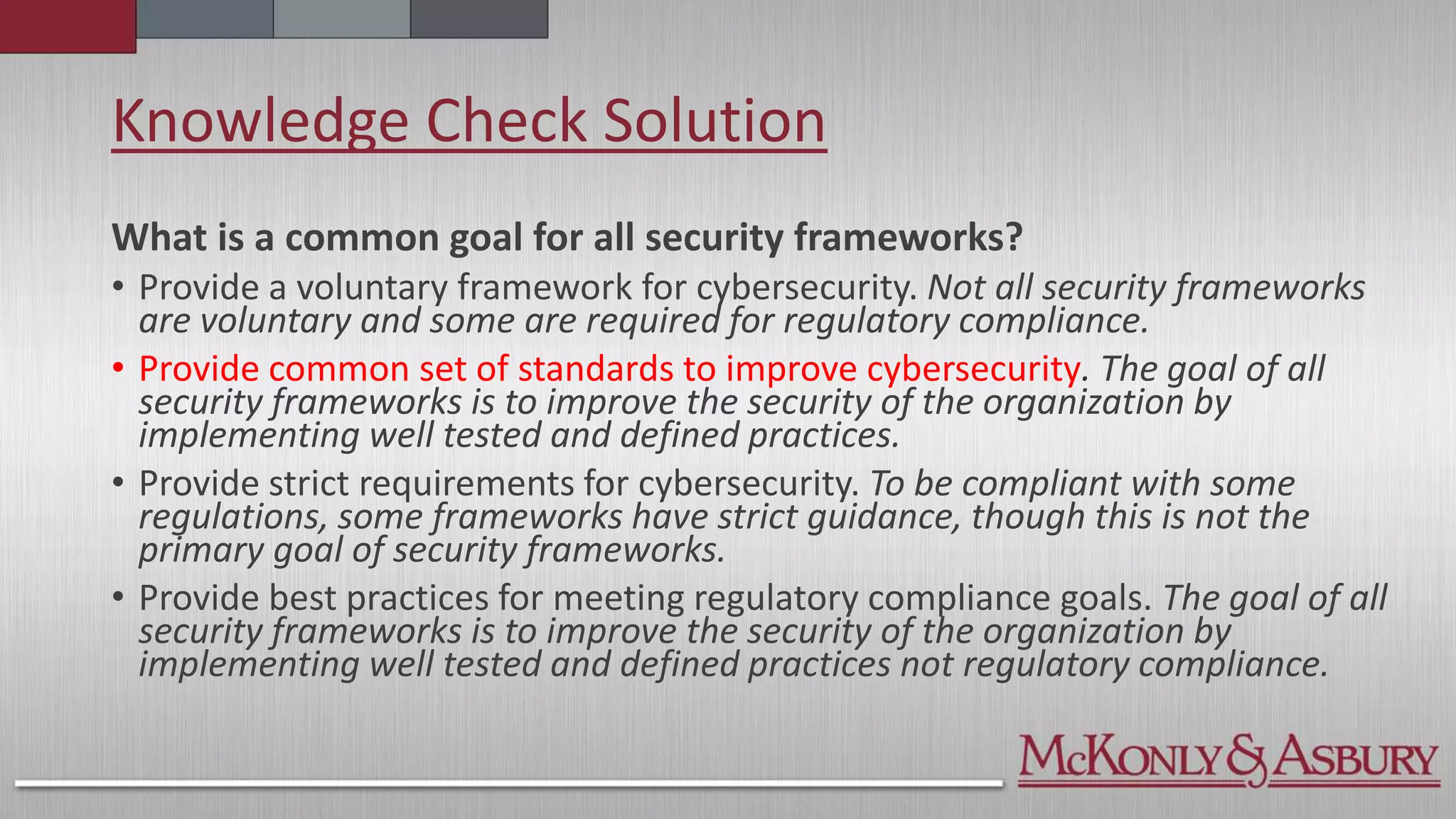
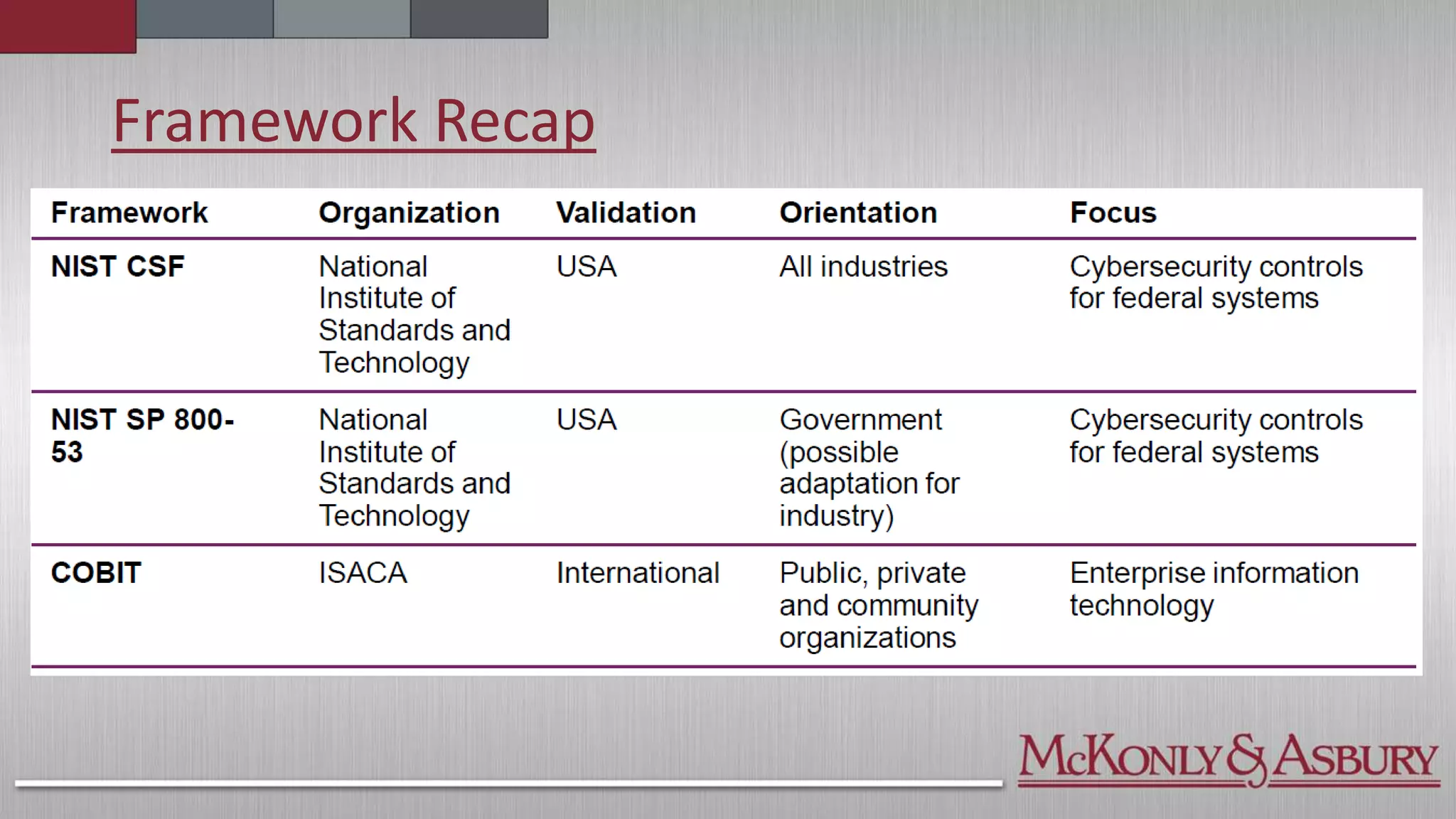
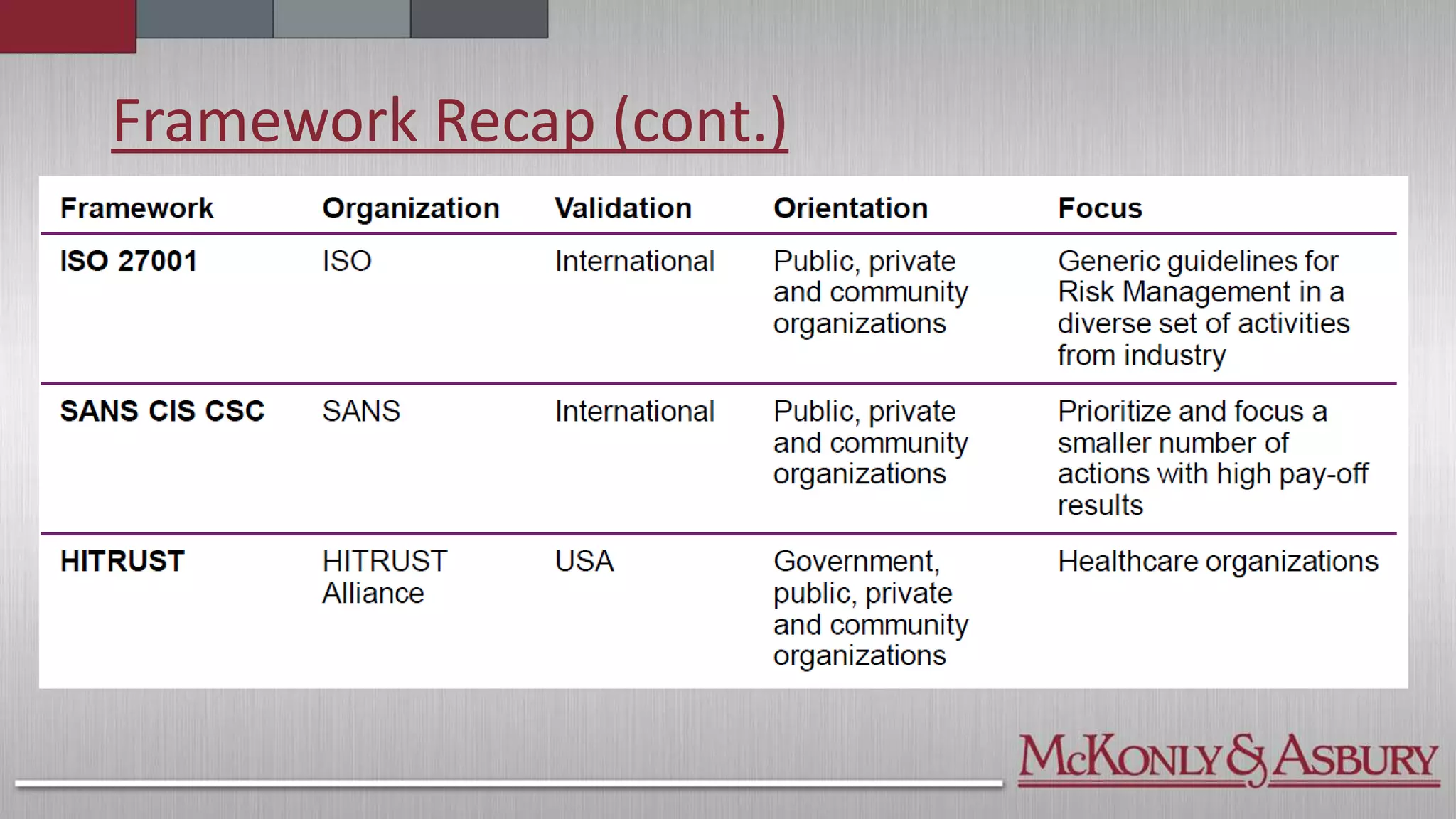
The document outlines the importance of a Cybersecurity Risk Management Program (CRMP) for finance and accounting professionals, detailing its objectives, components, and the protective role it plays in safeguarding data. It also explores various cybersecurity frameworks and standards, such as NIST, ISO, and HITRUST, explaining their functions, pros, and cons, as well as when organizations should utilize them. Overall, the document aims to equip professionals with critical knowledge on cybersecurity risks and management strategies.