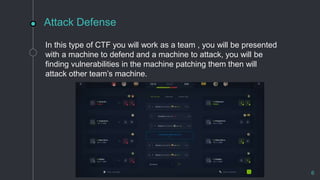
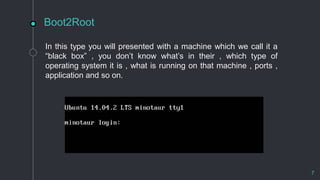
Capture the Flag (CTF) is a gamified cybersecurity competition that allows participants to learn penetration testing through hands-on challenges, which include finding vulnerabilities in systems or web applications. There are three types of CTFs: jeopardy, attack and defense, and boot2root, each focusing on different skills and collaborative experiences. Real-life applications of CTFs include pentesting for companies and participating in bug bounty programs on platforms like HackerOne and Bugcrowd.