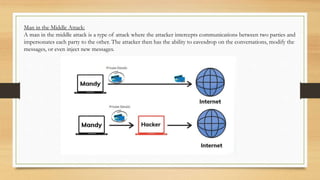
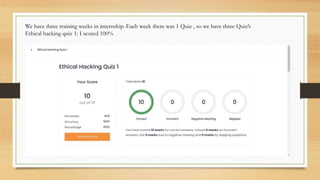
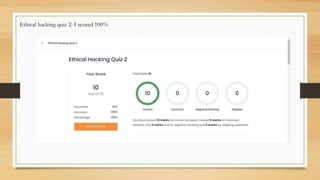
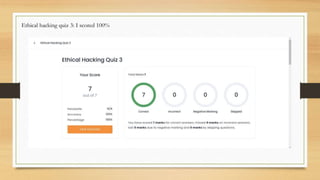
The document is an internship report that includes:
- Details about the internship organization and the internship period.
- An overview of ethical hacking and the internship project involving identifying vulnerabilities.
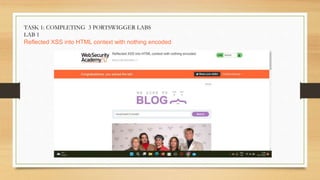
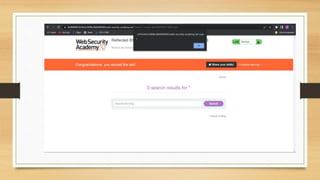
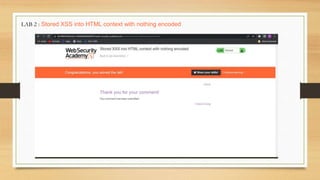
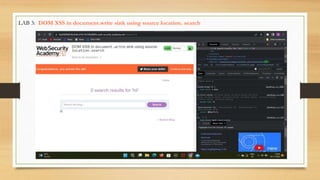
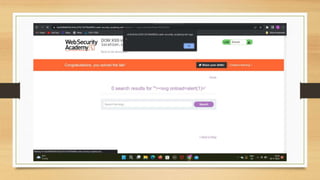
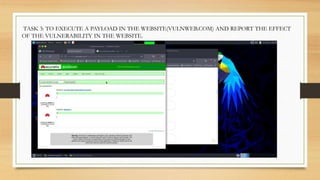
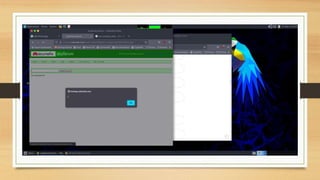
- A description of tasks completed including Portswigger labs, detecting vulnerabilities on a banking website, and executing a payload on a vulnerable website.
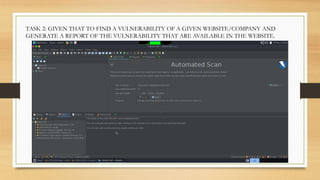
- Results from ethical hacking quizzes and a generated vulnerability report using OWASP-ZAP.
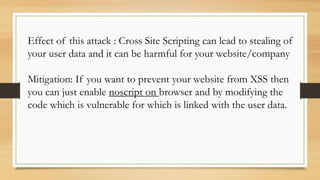
- Conclusions about gaining technical security knowledge around hacking techniques and prevention.