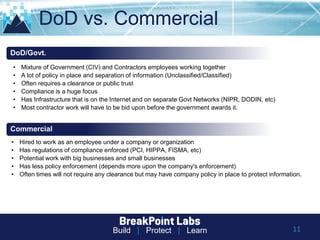
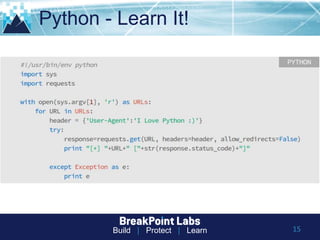
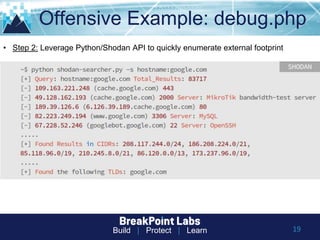
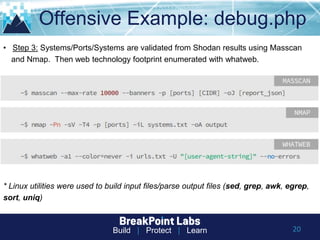
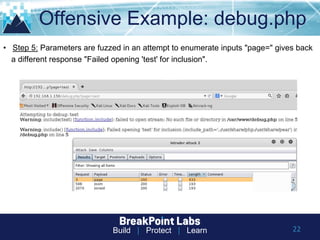
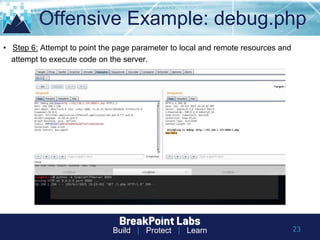
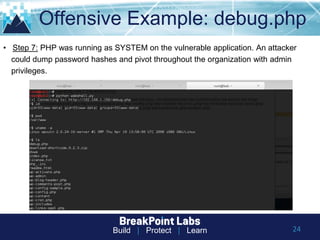
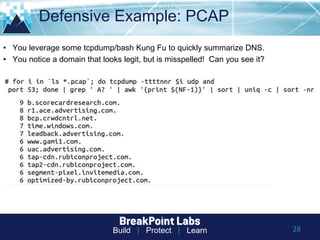
This document provides tips and guidance for starting an information security career. It discusses the importance of continuous learning and hands-on skills development. Some key recommendations include building a home lab, participating in capture-the-flag exercises, learning programming languages like Python and Linux, finding a mentor, considering certifications, and networking within the security community through conferences, Twitter, blogs and open source projects. The document uses examples from penetration testing and security analysis to illustrate real-world scenarios.