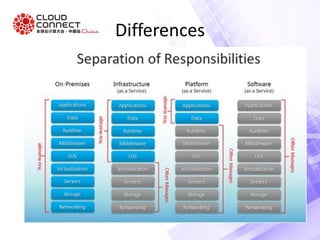
This document discusses penetration testing of cloud environments. It begins with background on the speaker and assumptions about an existing cloud hosting plan transitioning to cloud data centers. It then covers the attack surface and types of attacks for public, private, and hybrid clouds. Specific attack vectors discussed include exposed interfaces, malicious insiders, hypervisor and routing attacks, and certificate issues. The document concludes with questions about properly testing and migrating to the cloud.