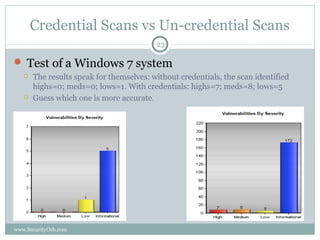
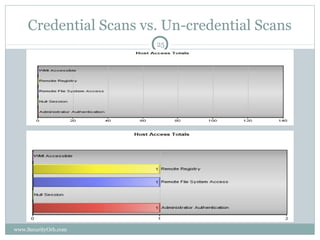
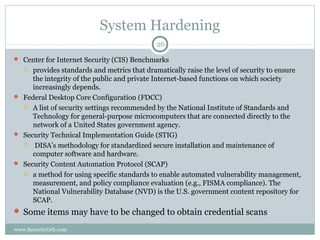
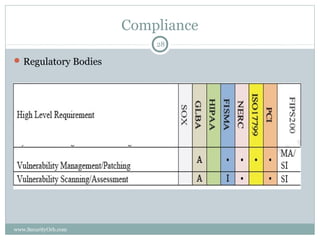
The document discusses the importance of security vulnerability assessments in enhancing organizational security, outlining processes, best practices, and challenges associated with these assessments. It details various assessment types, methodologies, and the significance of regular evaluations to safeguard information systems against vulnerabilities. The conclusion emphasizes that multiple security measures are necessary to create a comprehensive defense against potential threats.