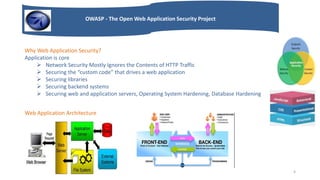
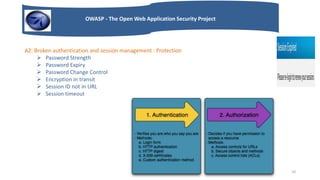
OWASP is a non-profit organization focused on improving web application security. It publishes guides on secure development practices and identifies the top web application vulnerabilities, known as the OWASP Top 10. These include injection flaws, broken authentication, cross-site scripting, insecure direct object references, security misconfiguration, sensitive data exposure, missing access controls, cross-site request forgery, use of vulnerable components, and unsafe redirects. OWASP provides resources to help developers avoid these risks and build more secure applications.