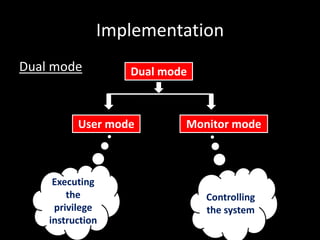
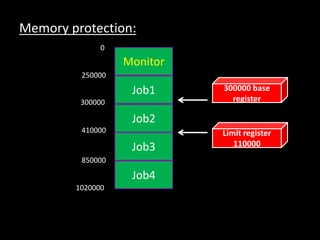
The document discusses the design and implementation of operating systems. It covers design goals for both users and systems, as well as mechanisms like timers and policies for resource allocation. Implementation involves dual mode operation, with the CPU switching between user and monitor modes. Memory and I/O protection are achieved through base/limit registers and privileged instructions only executable in monitor mode. The operating system controls system resources and prevents unauthorized access through these hardware protection mechanisms.