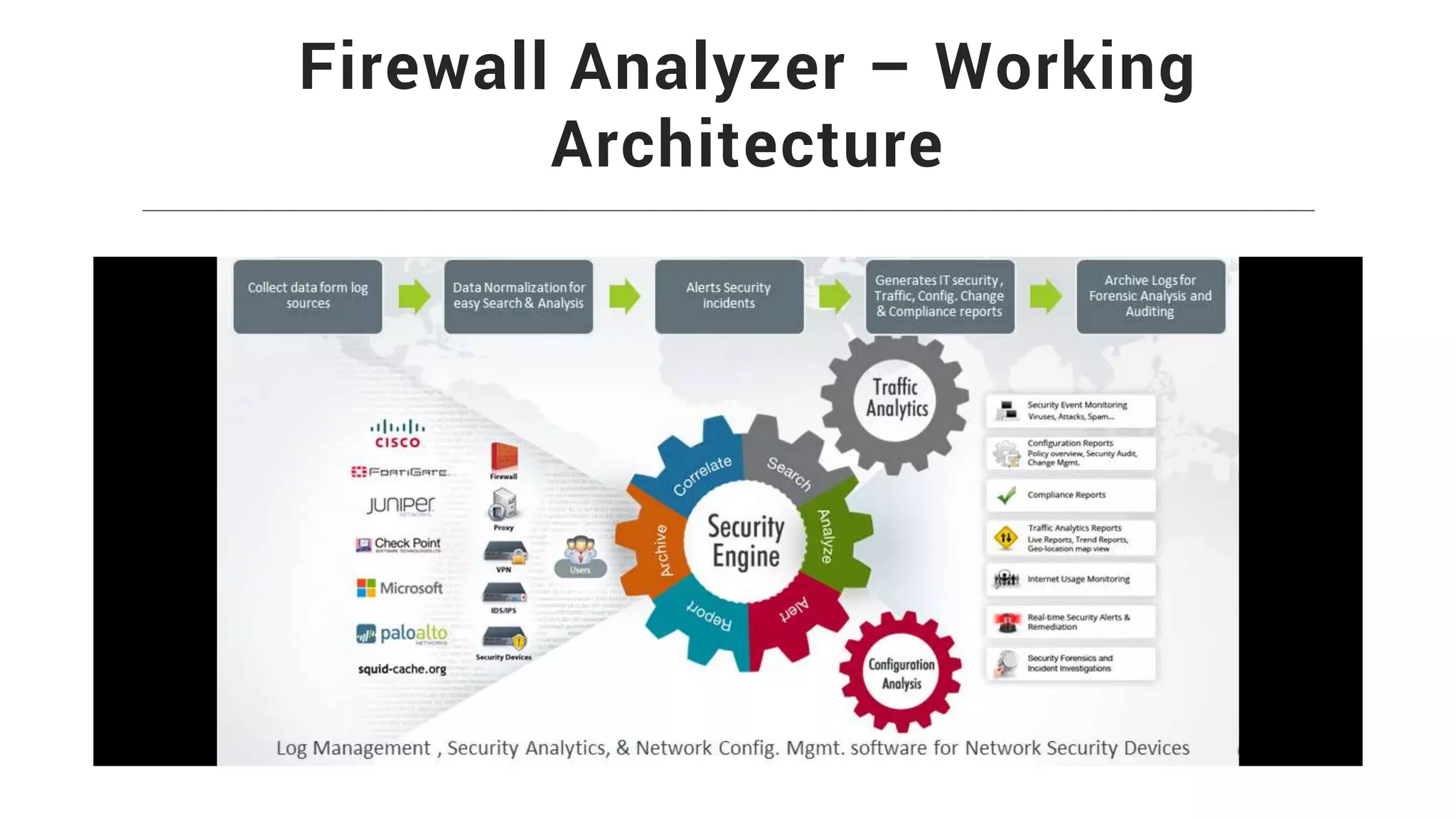
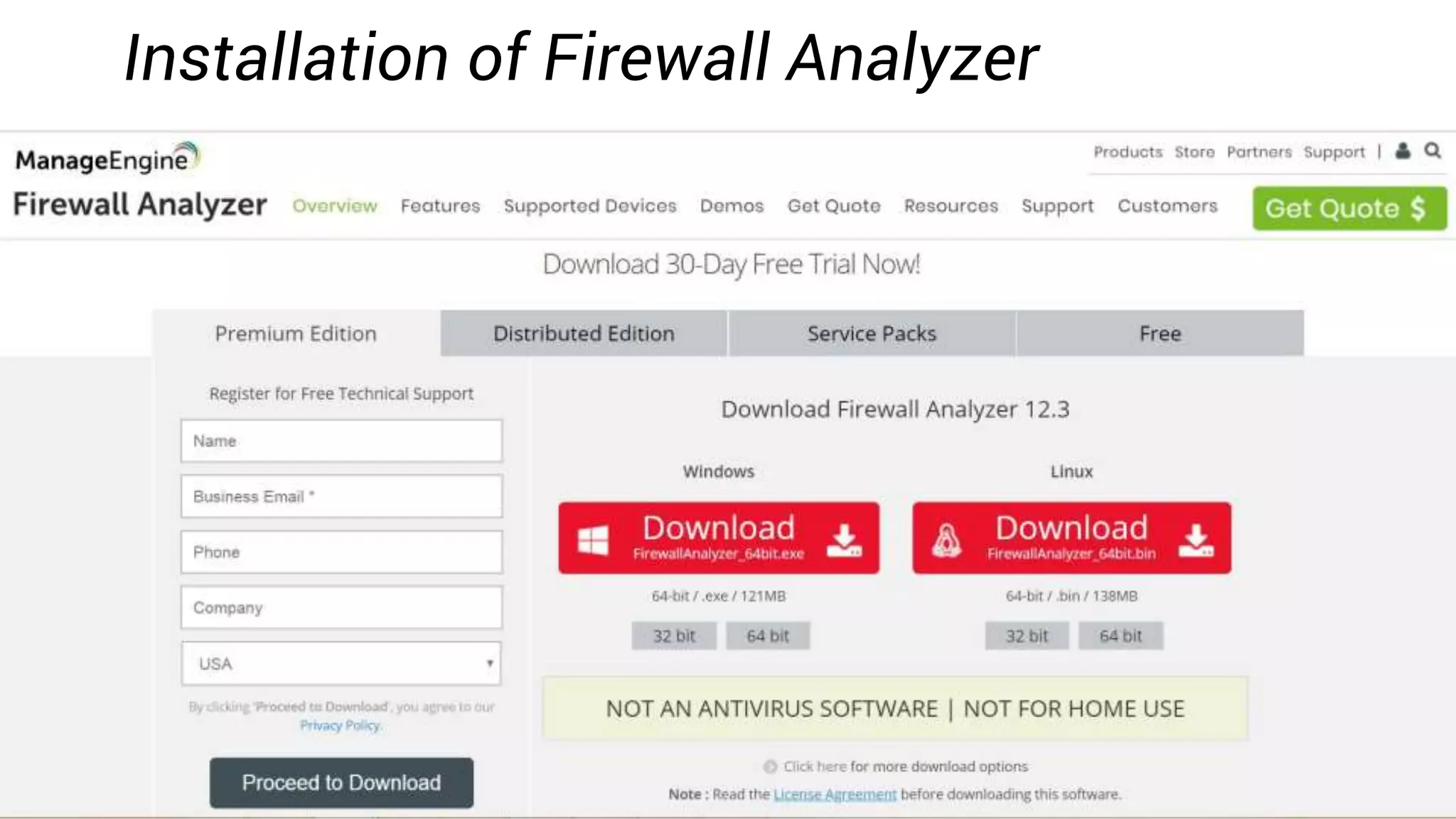
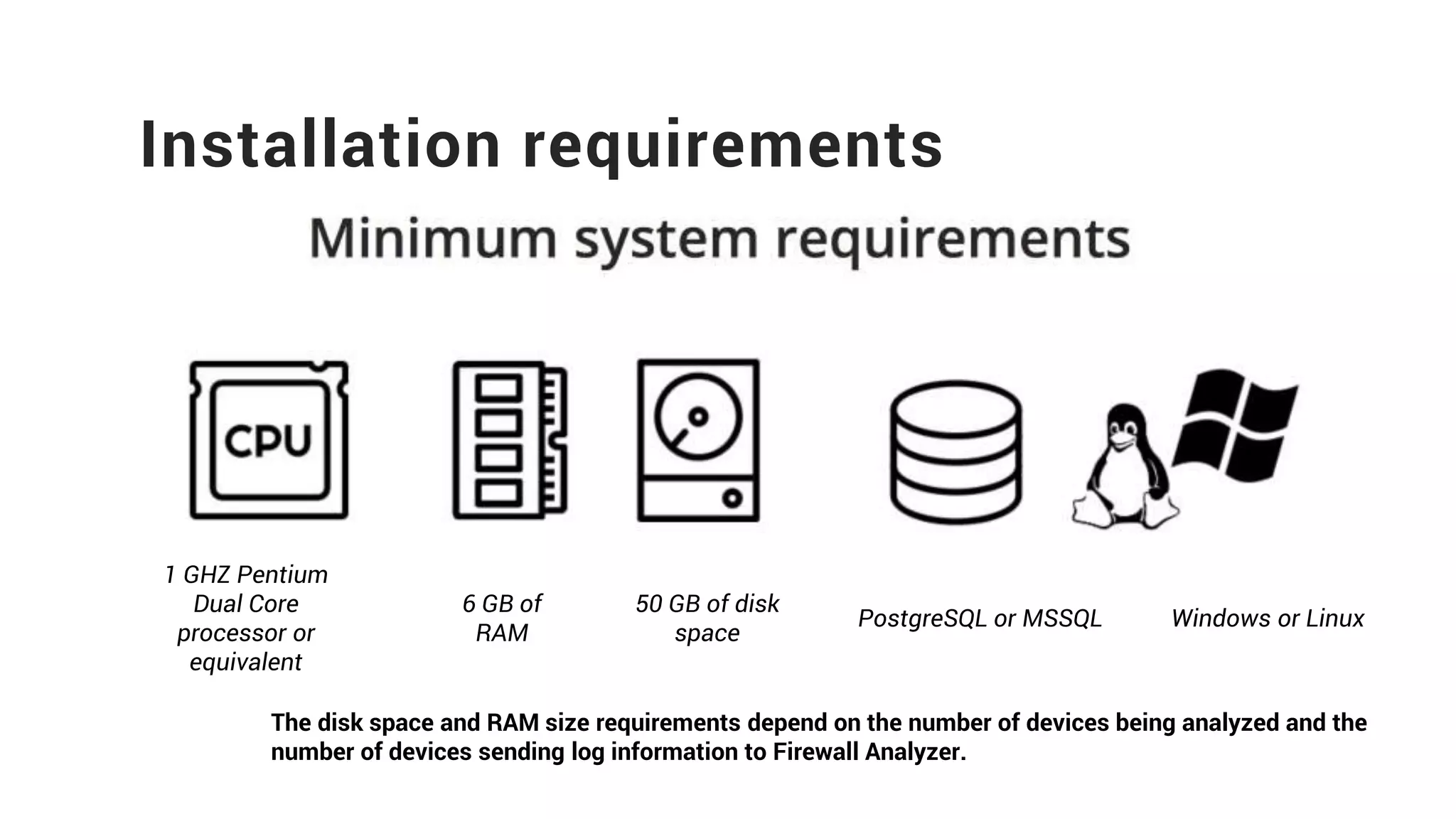
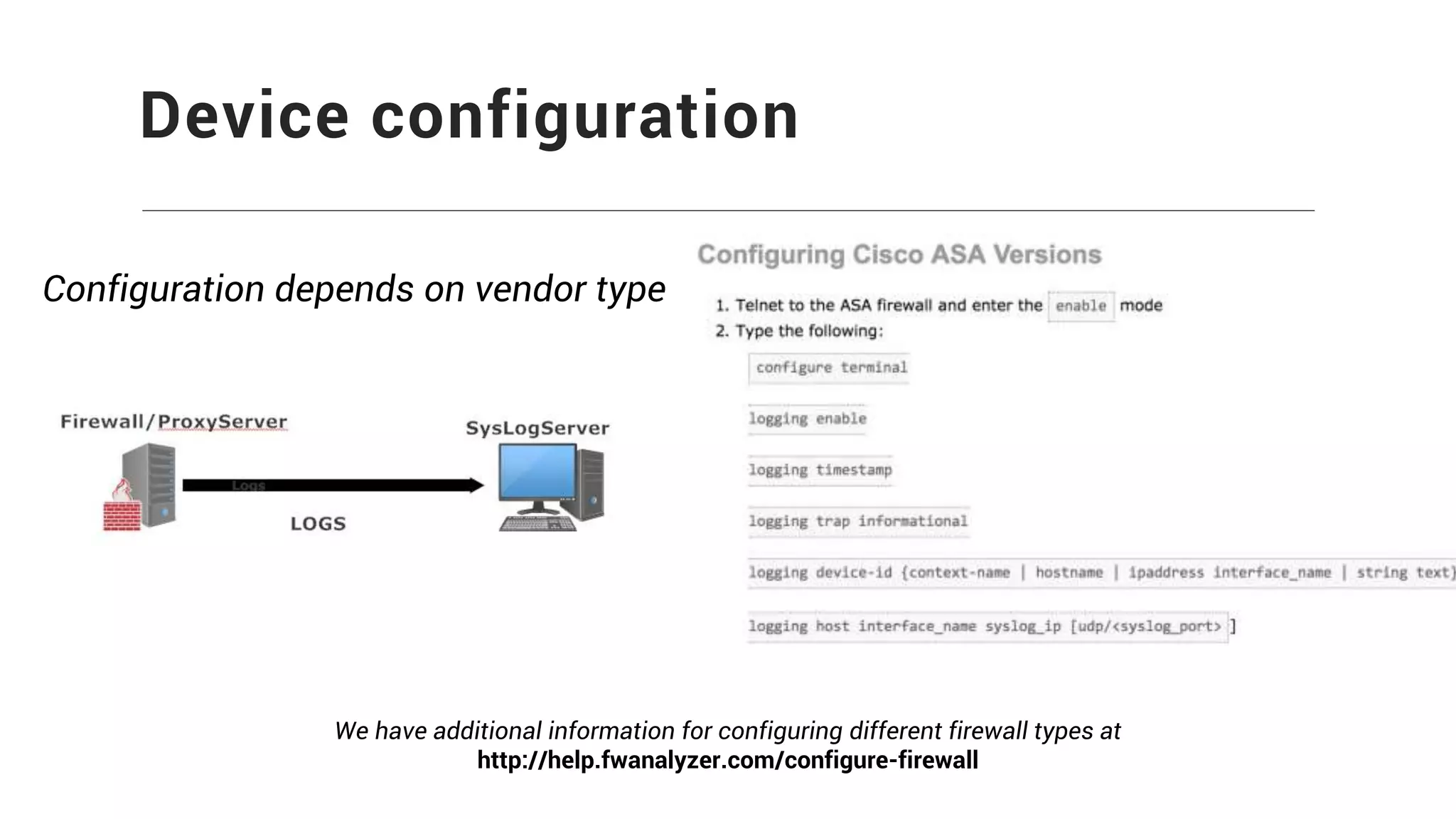
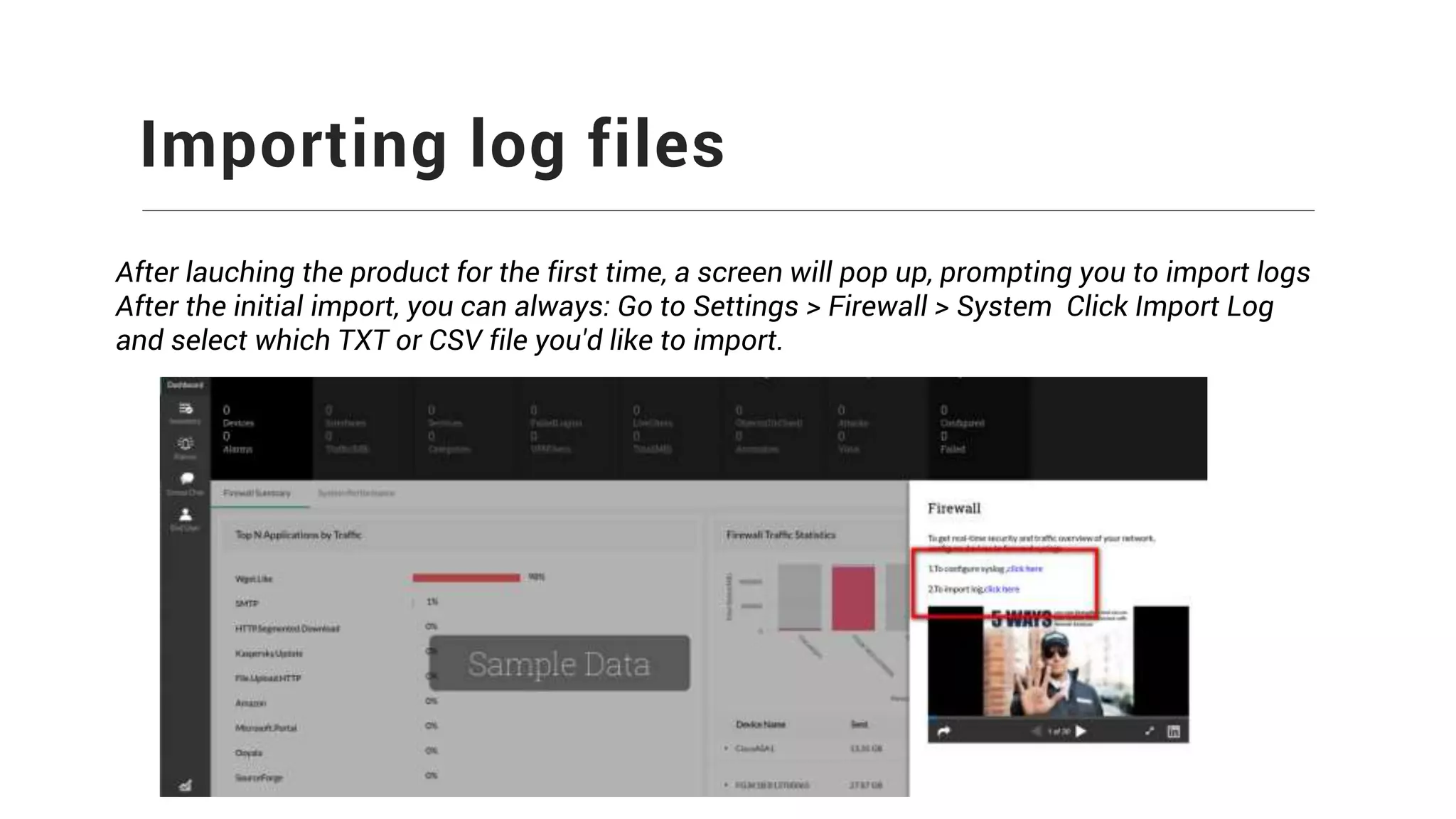
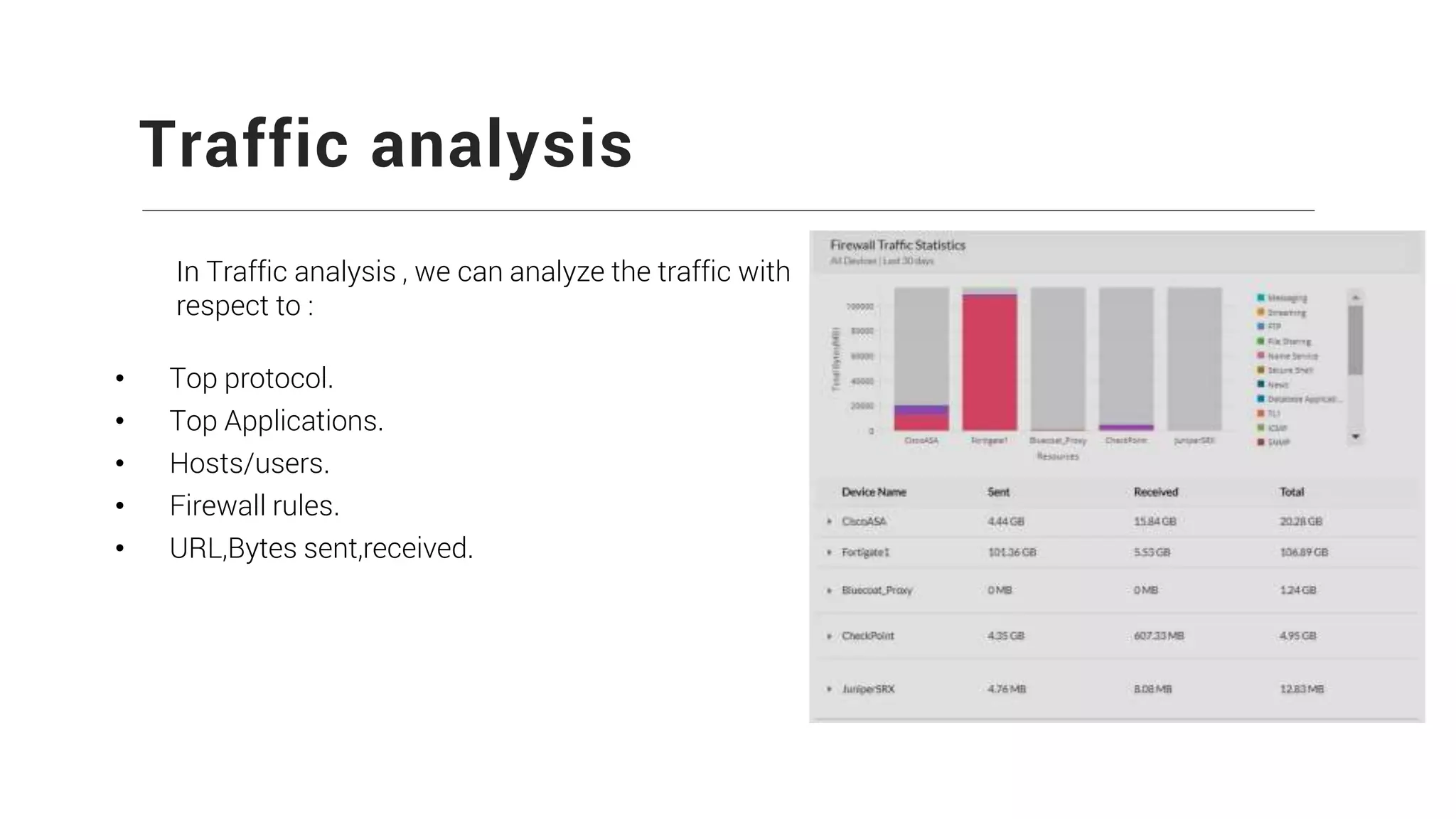
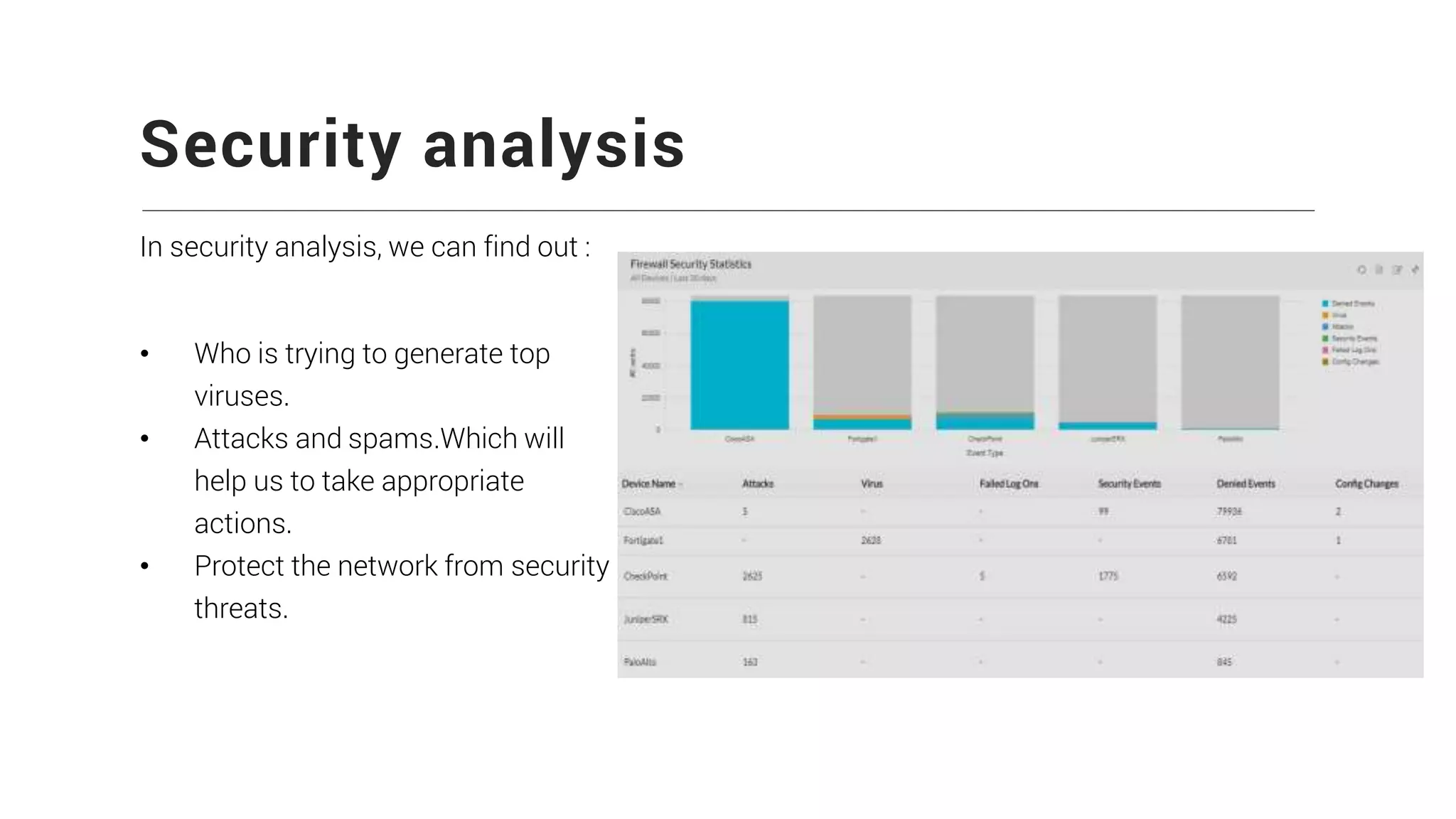
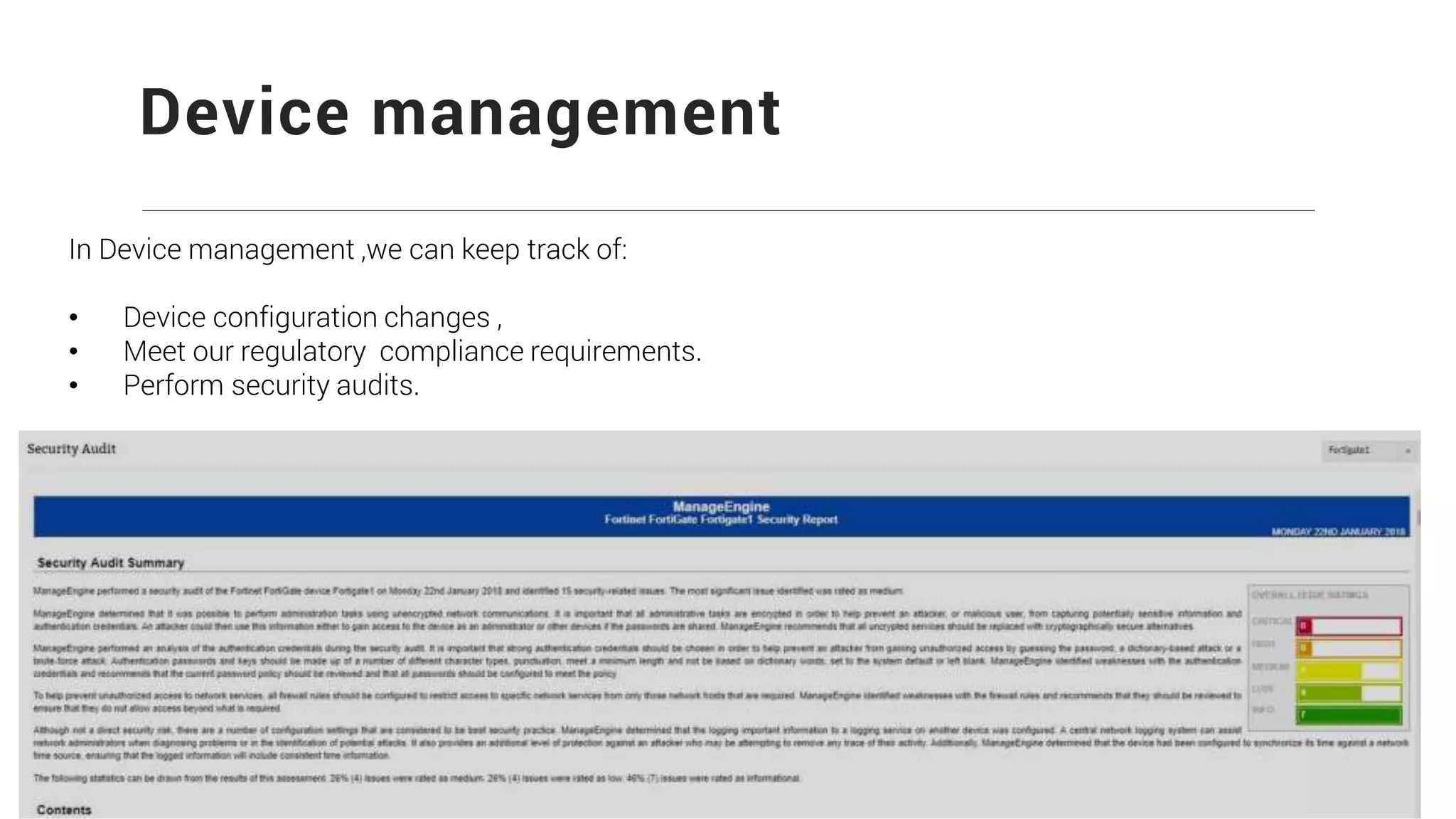
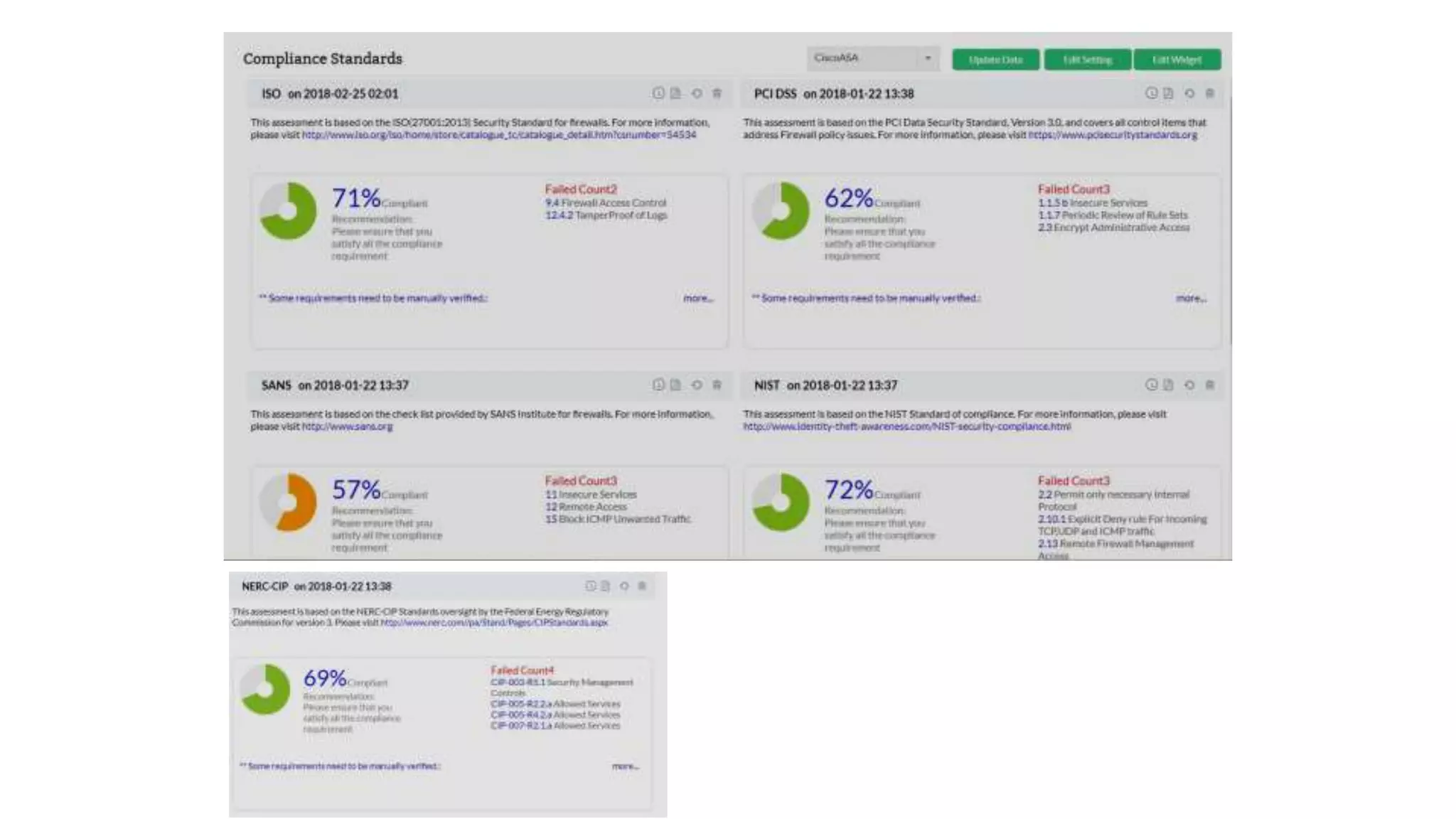
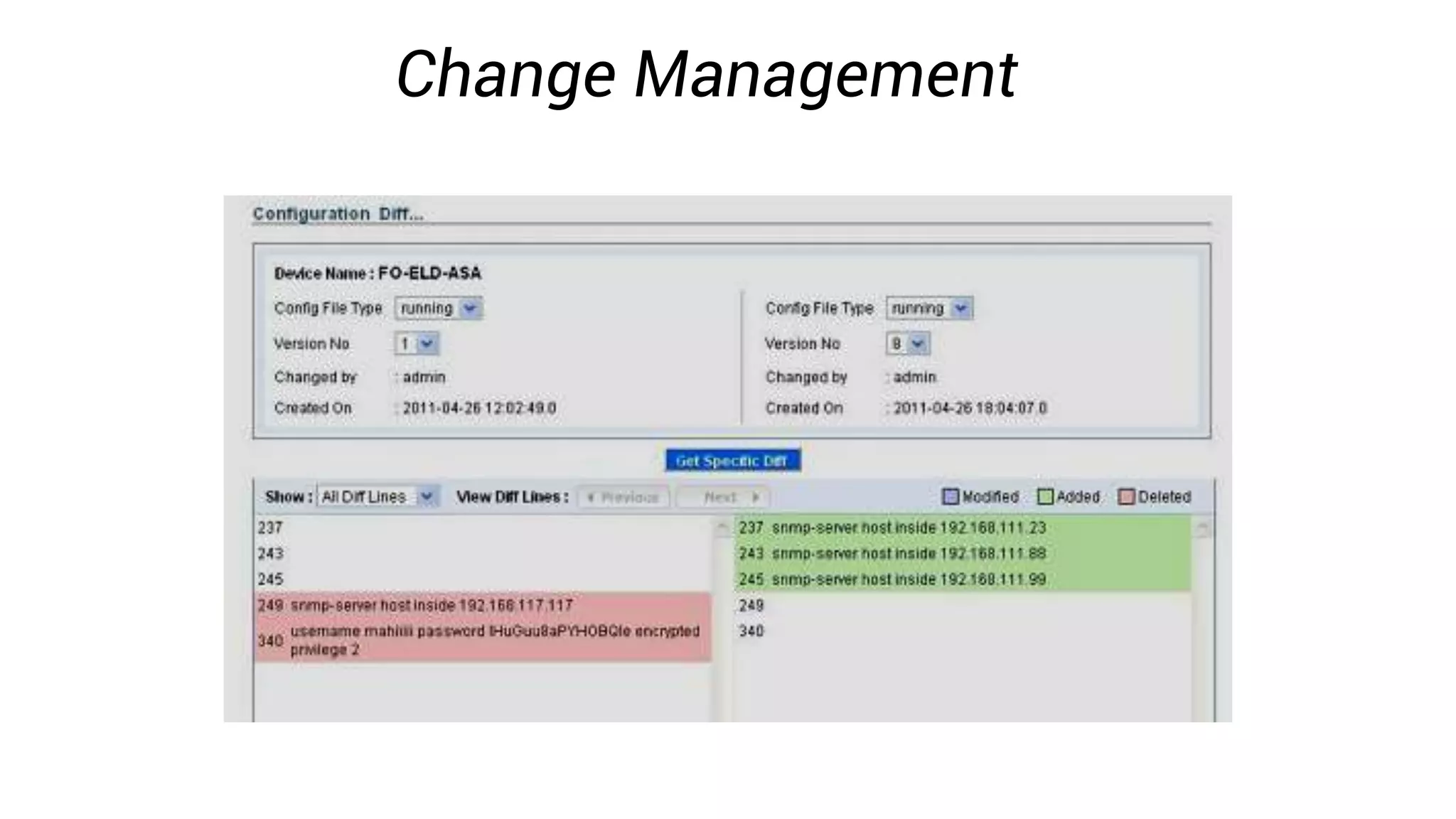
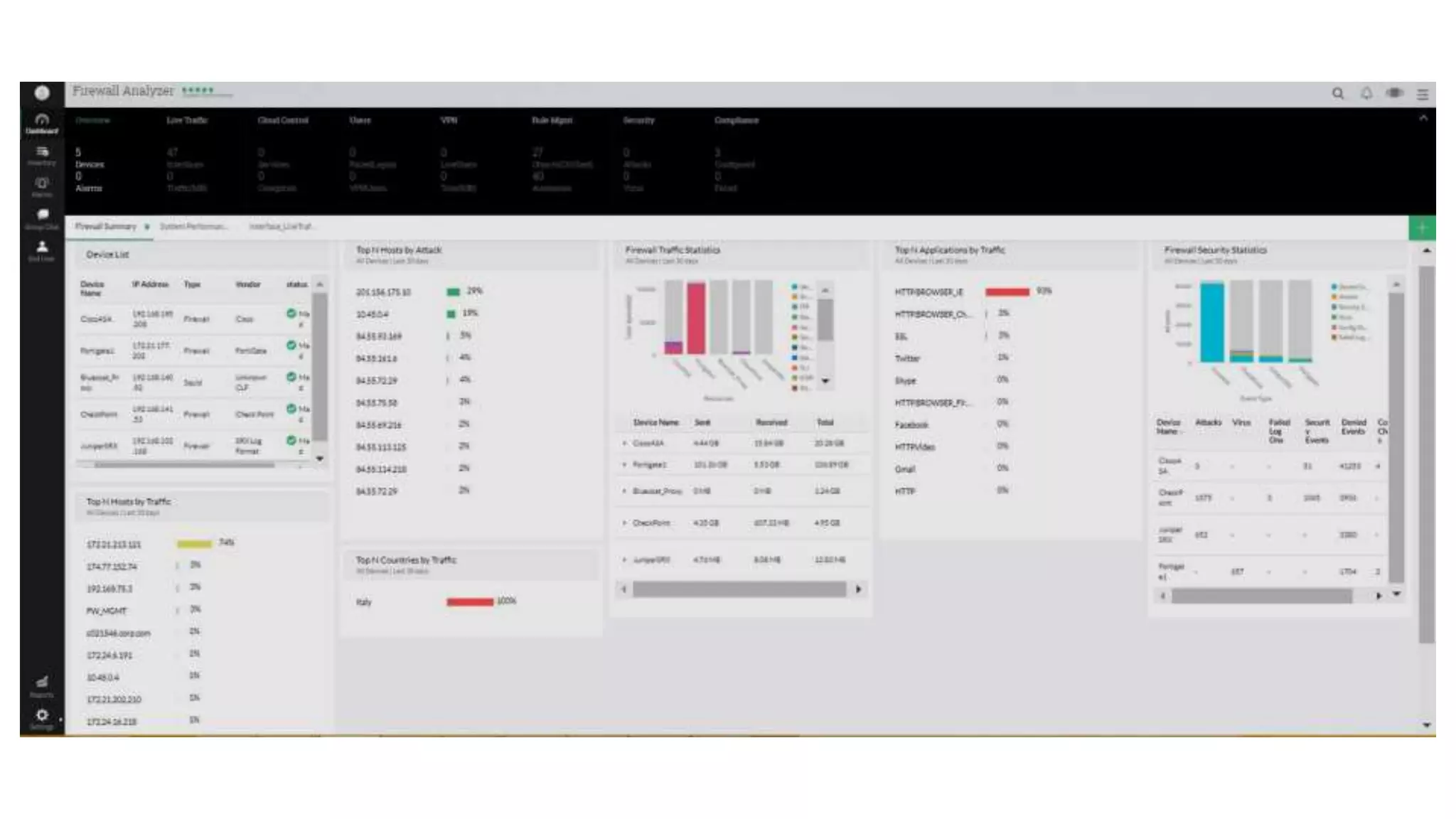
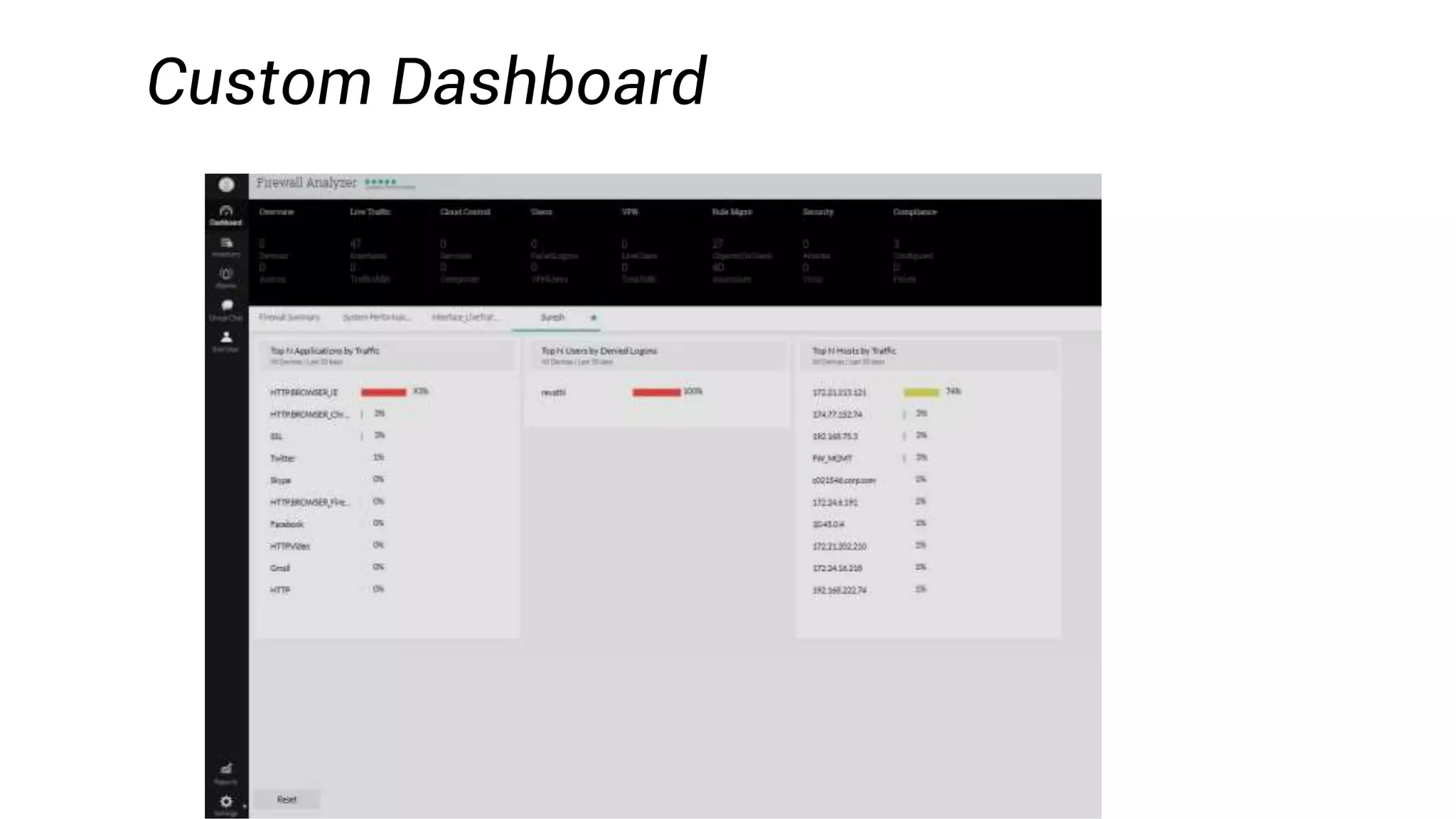
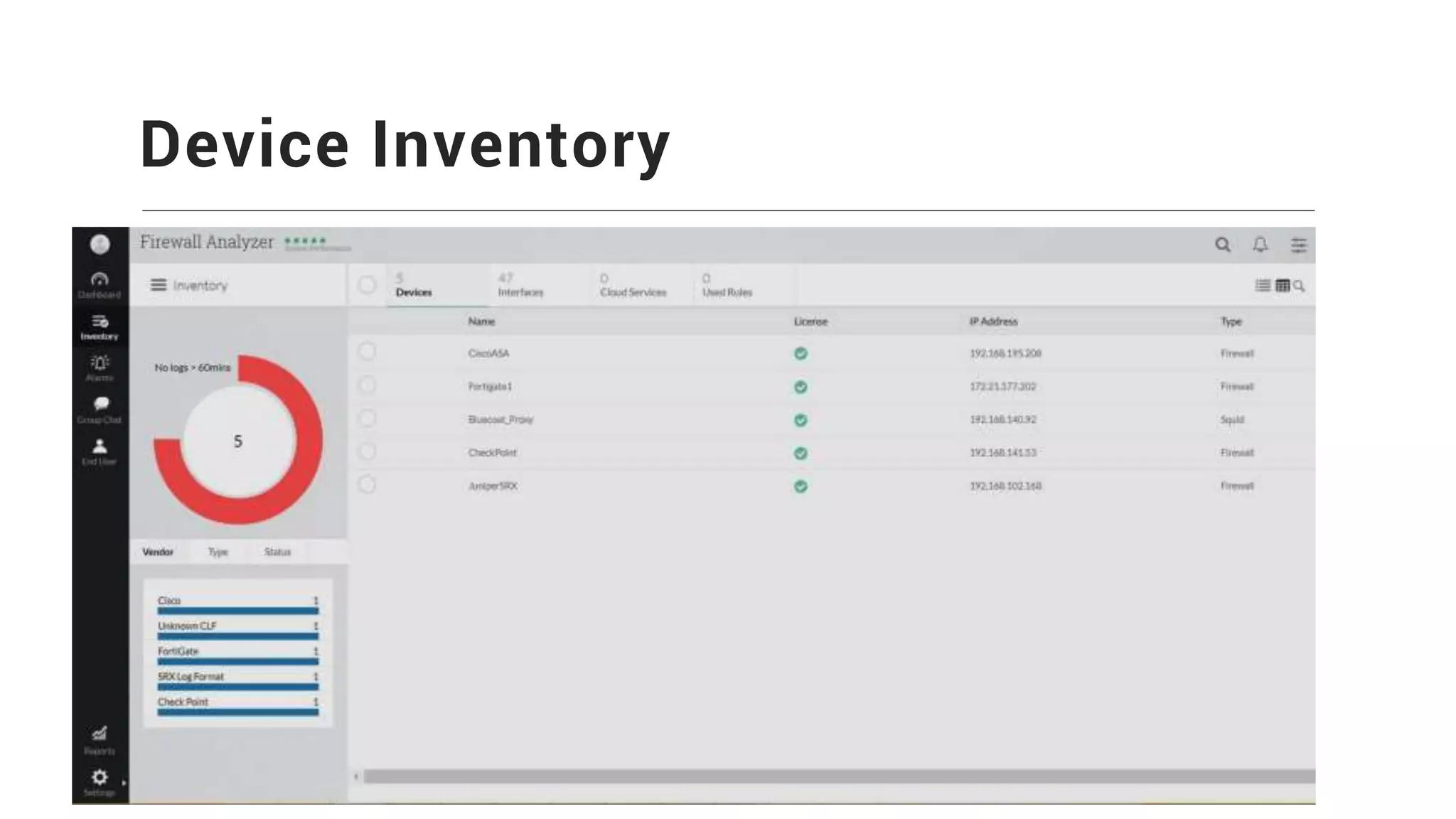
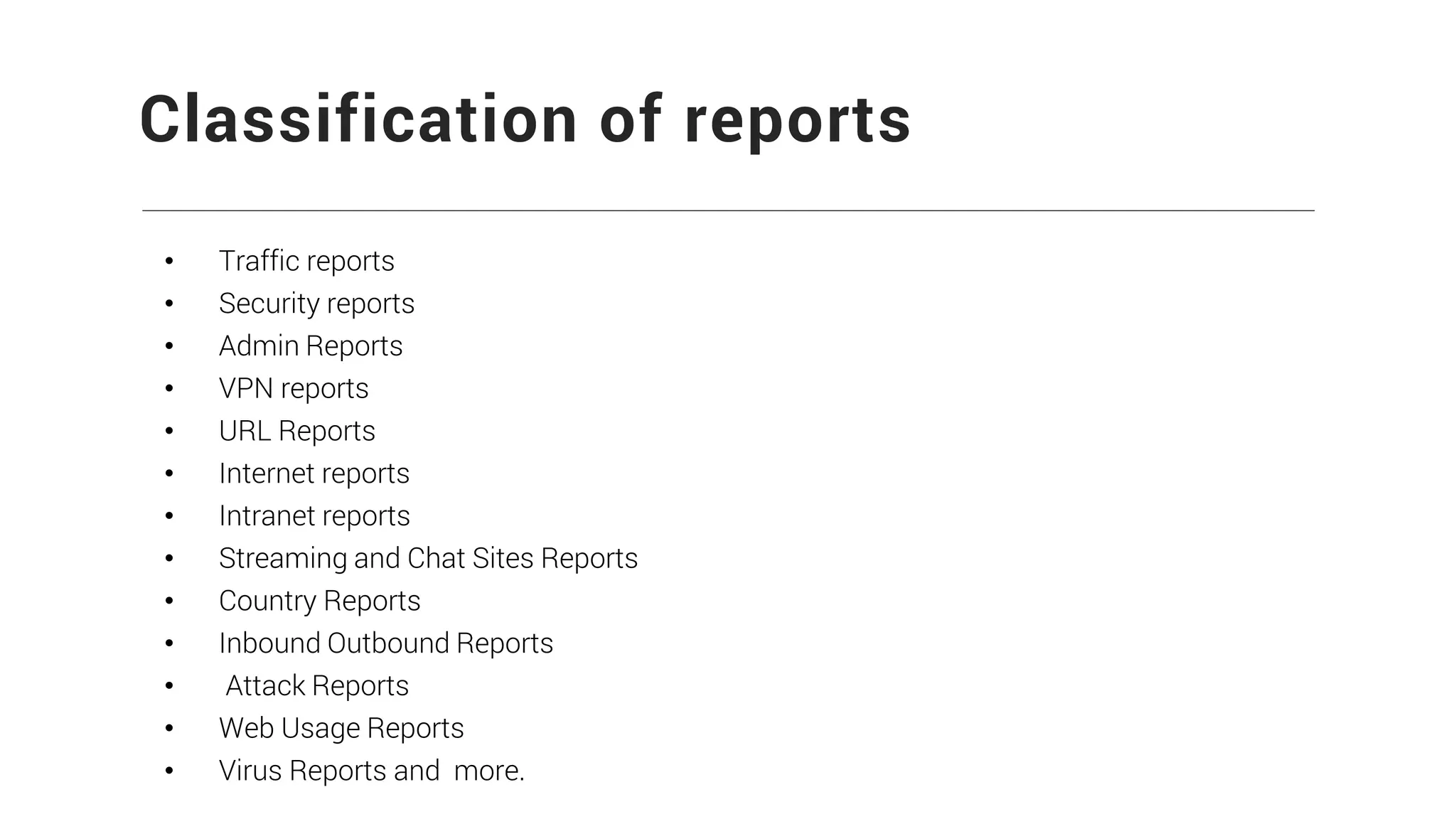
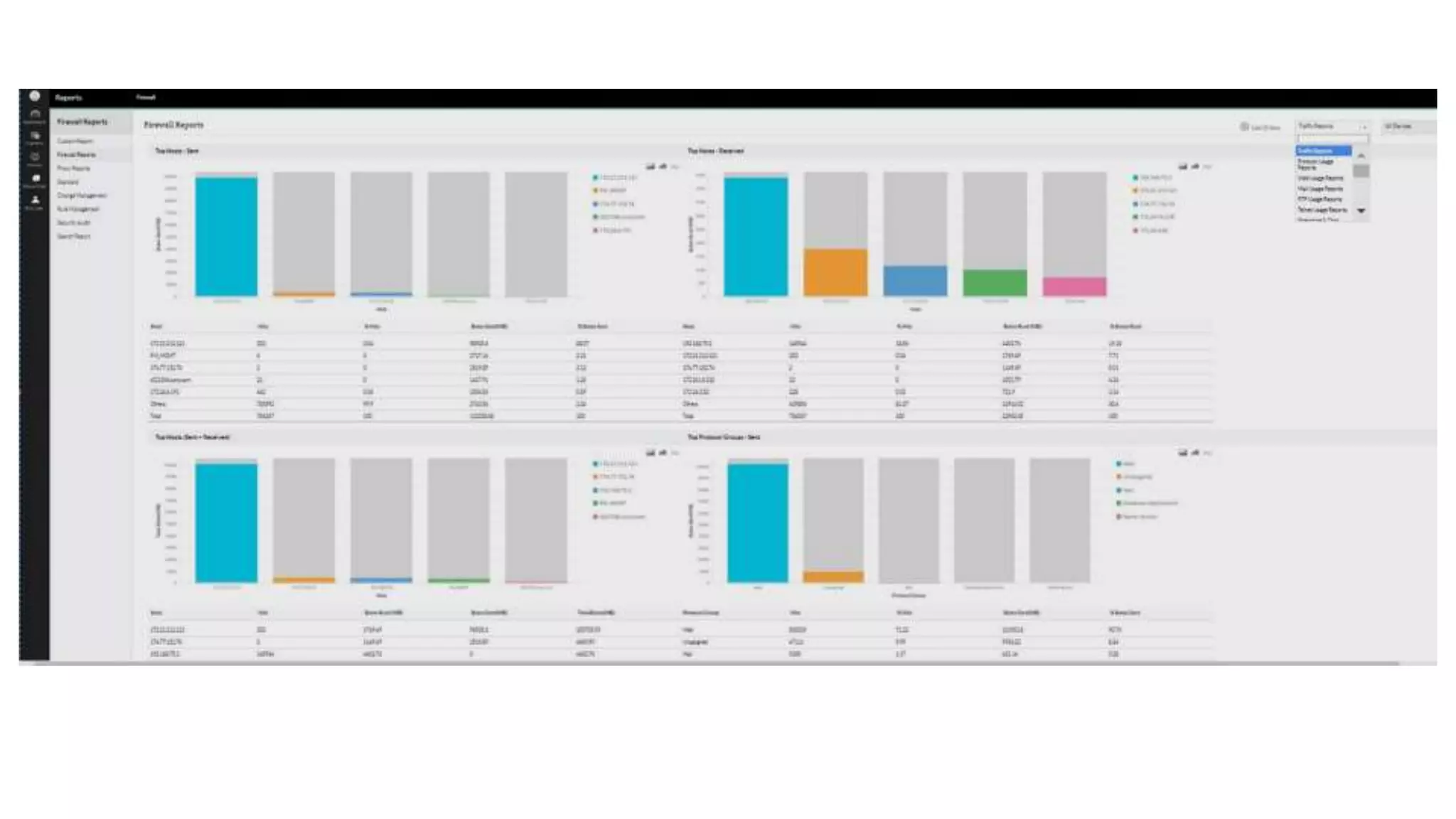
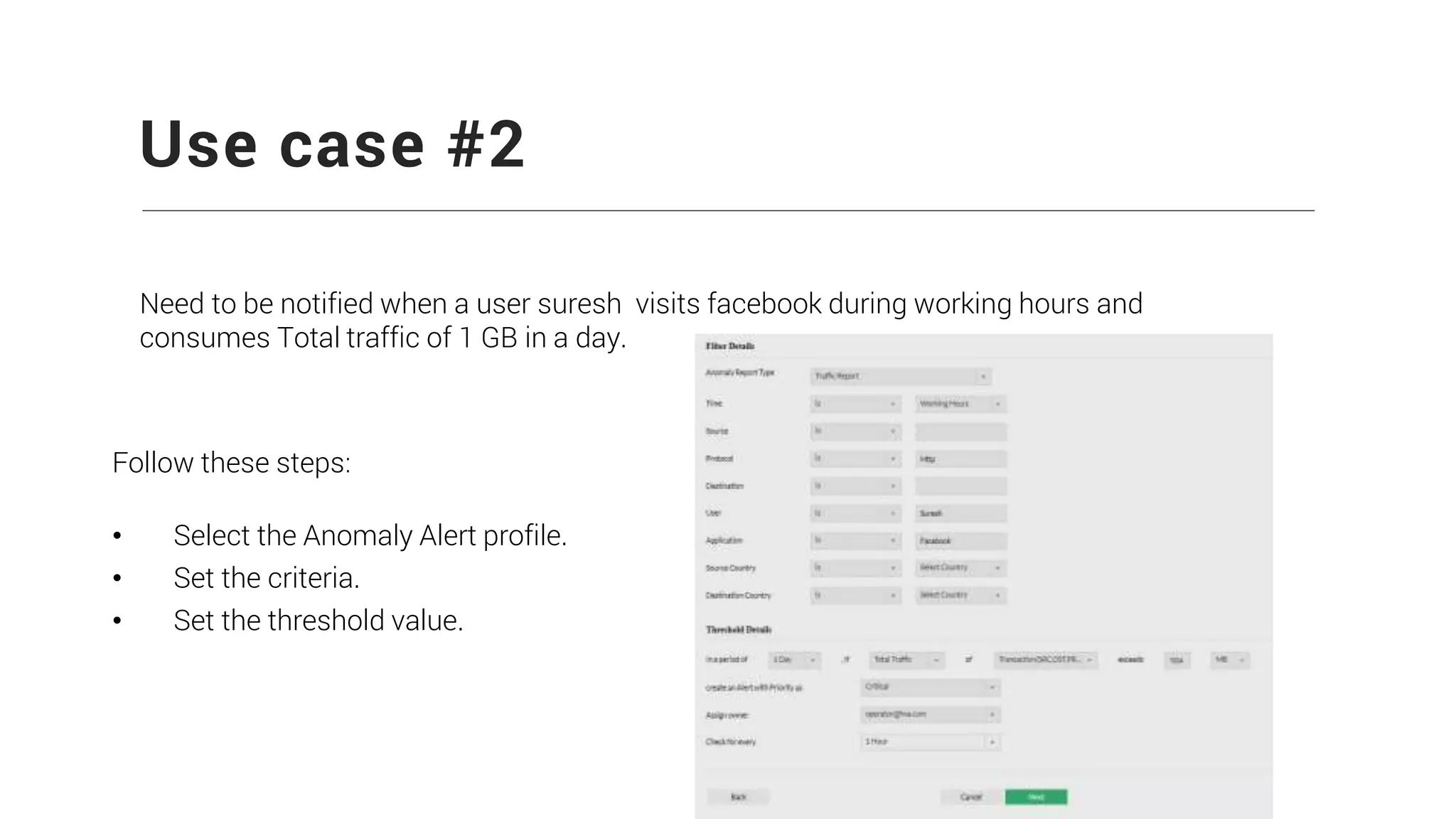
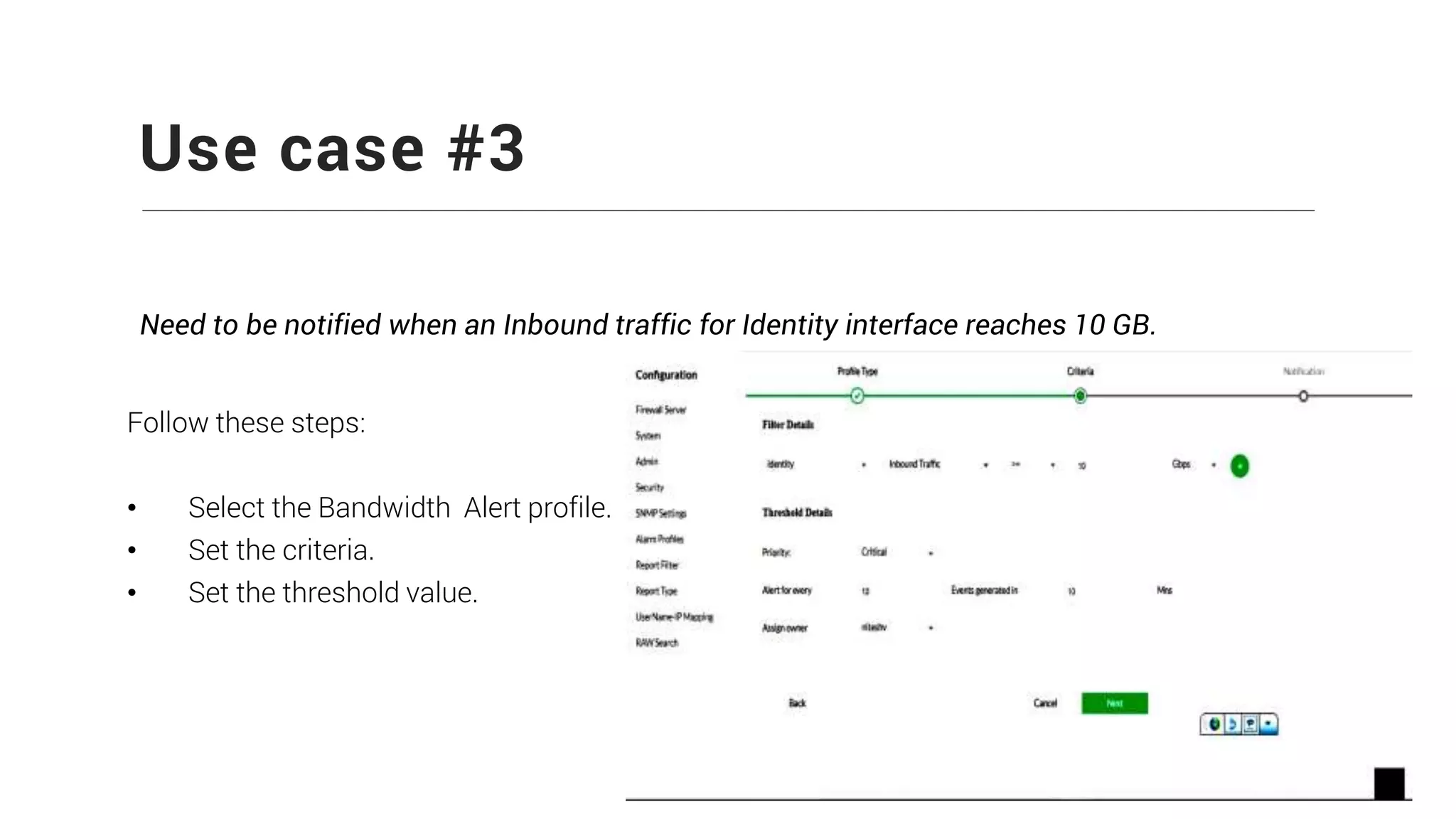
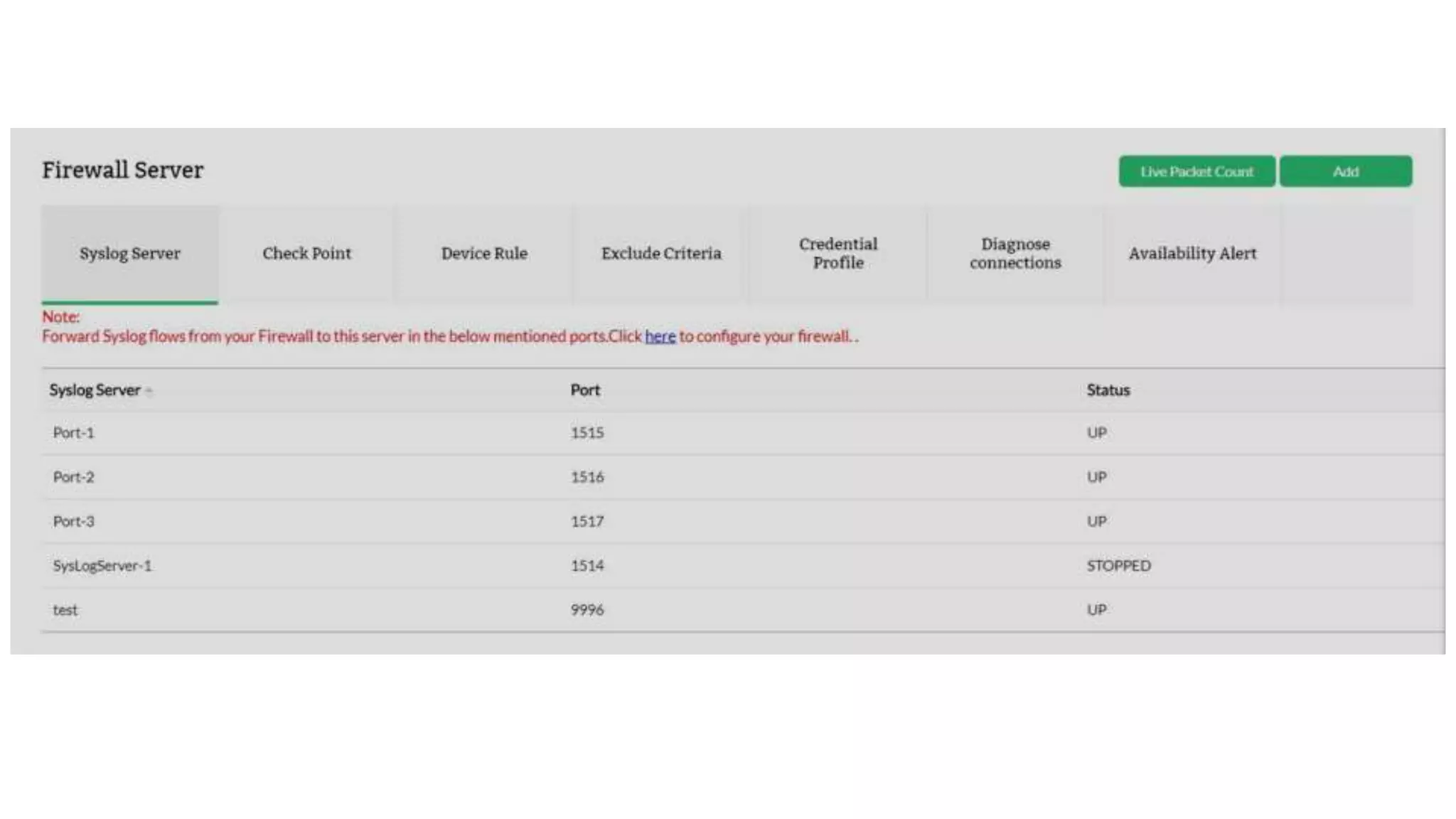
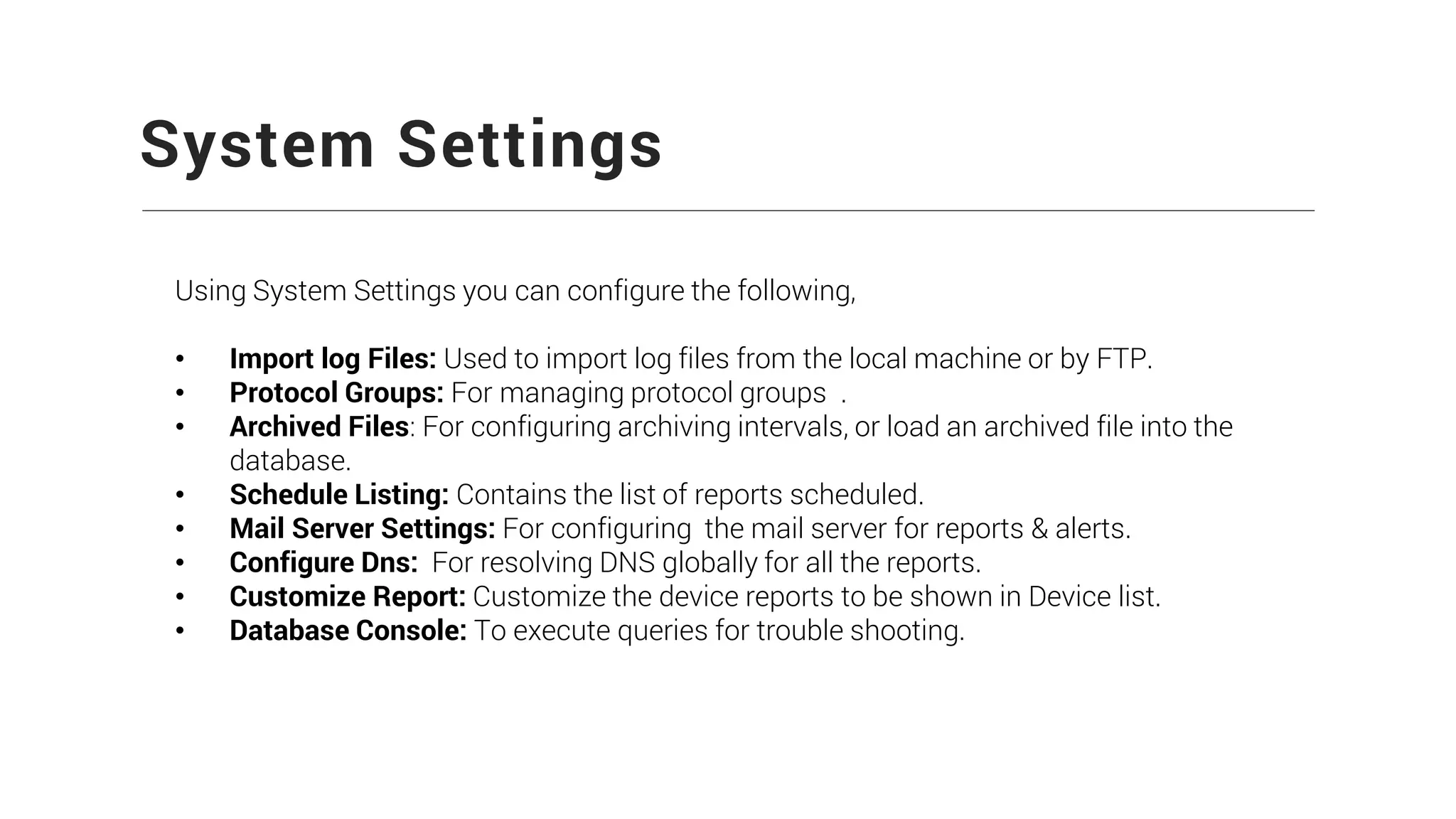
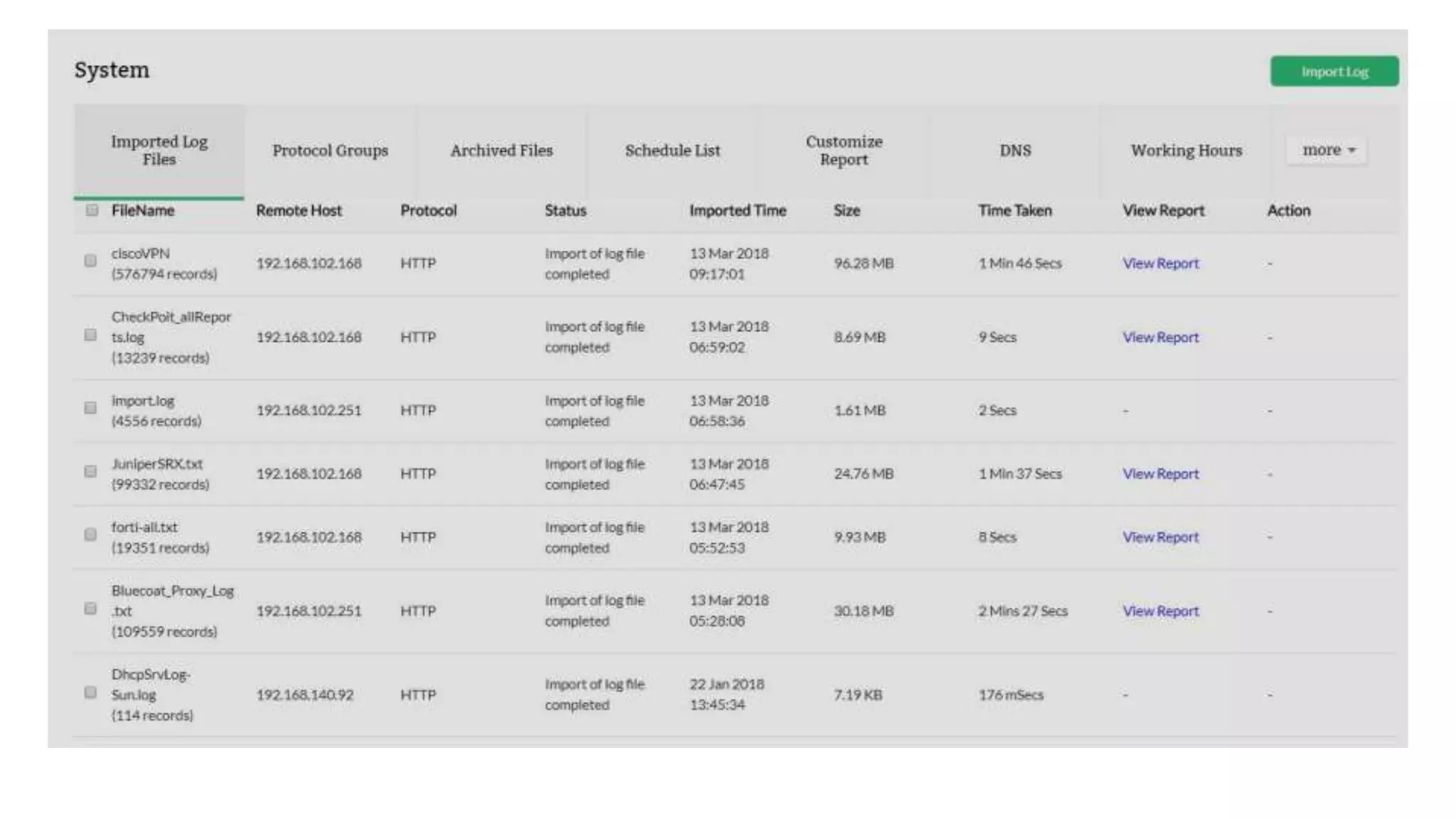
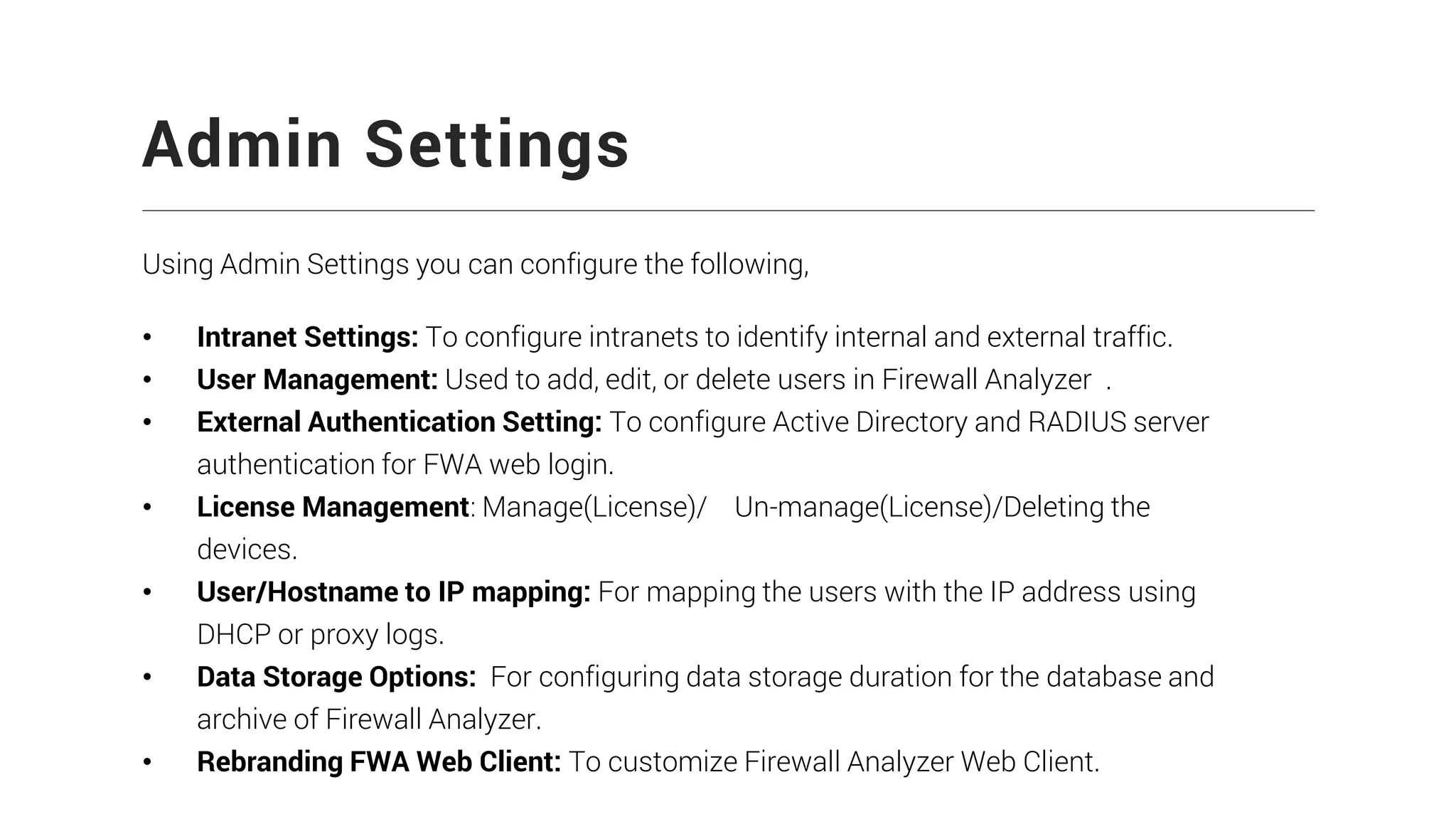
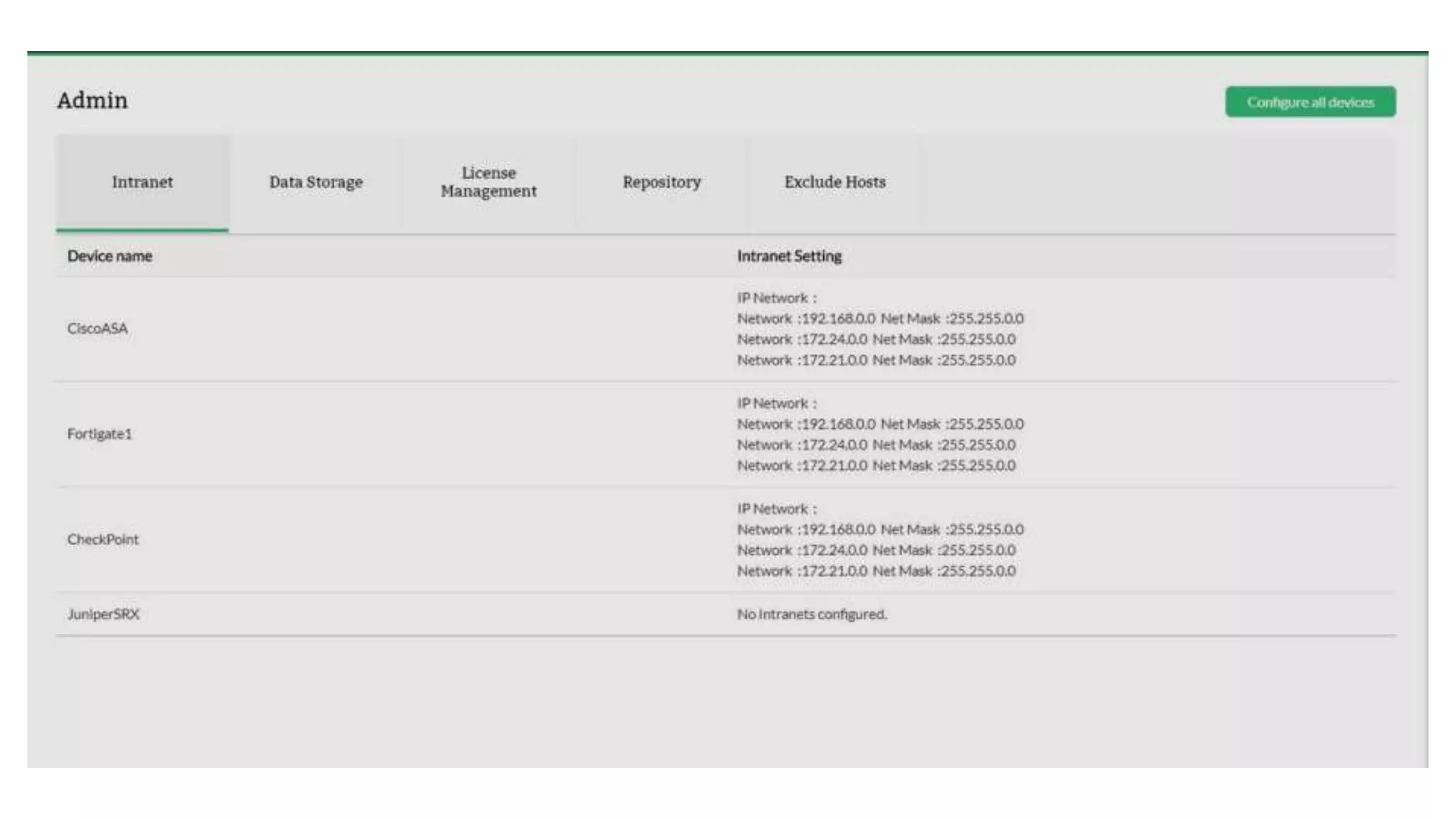
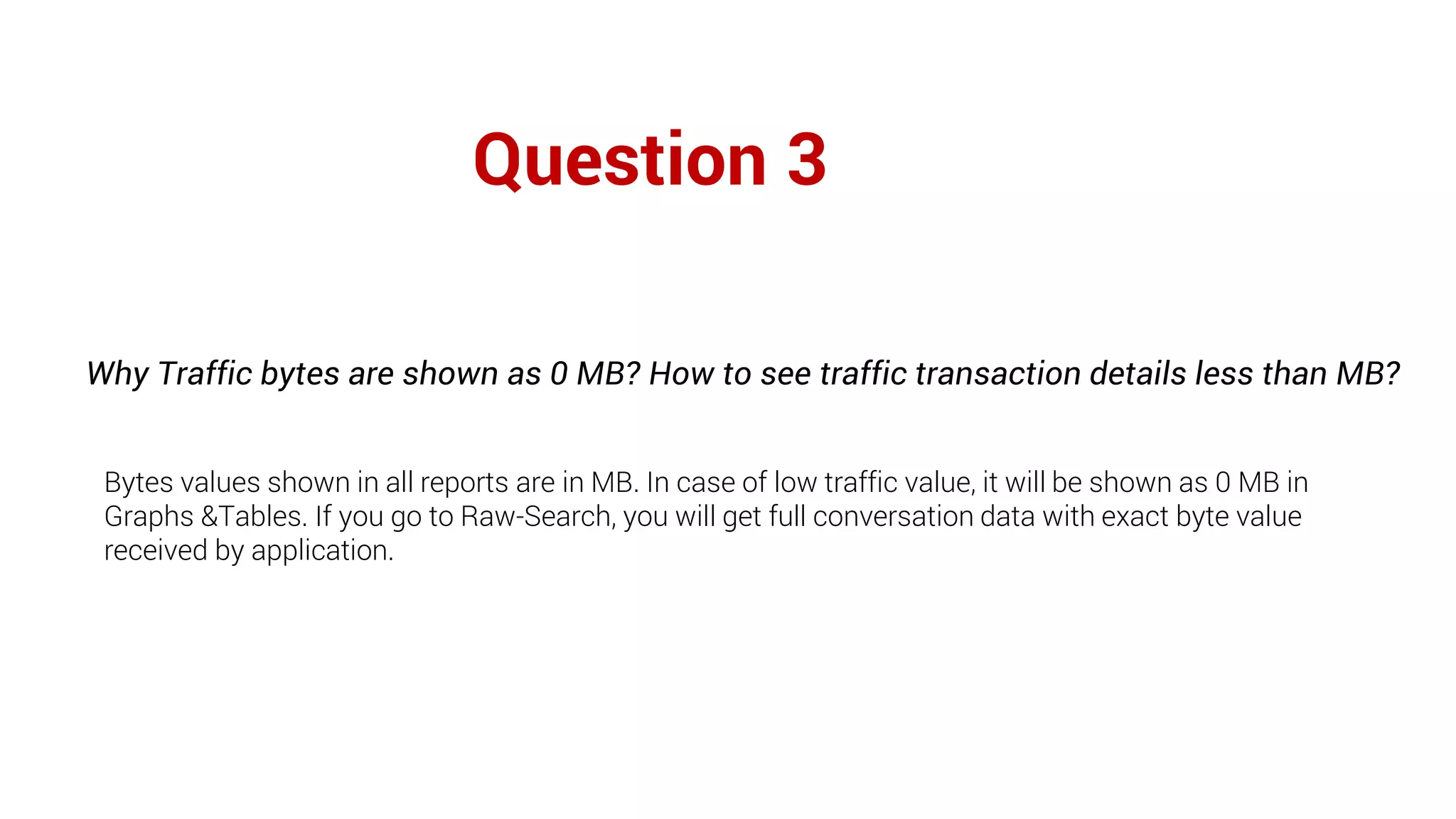
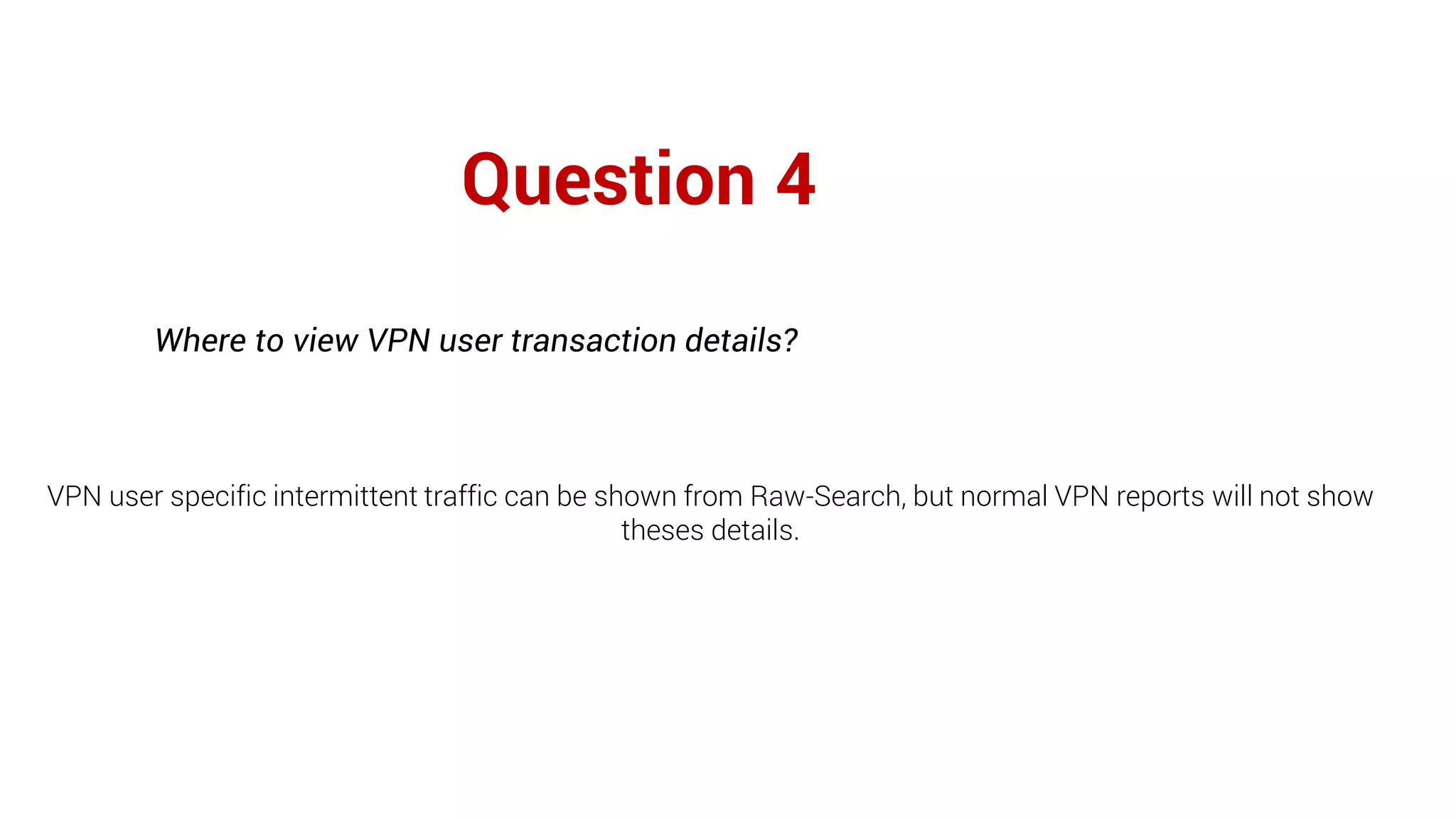
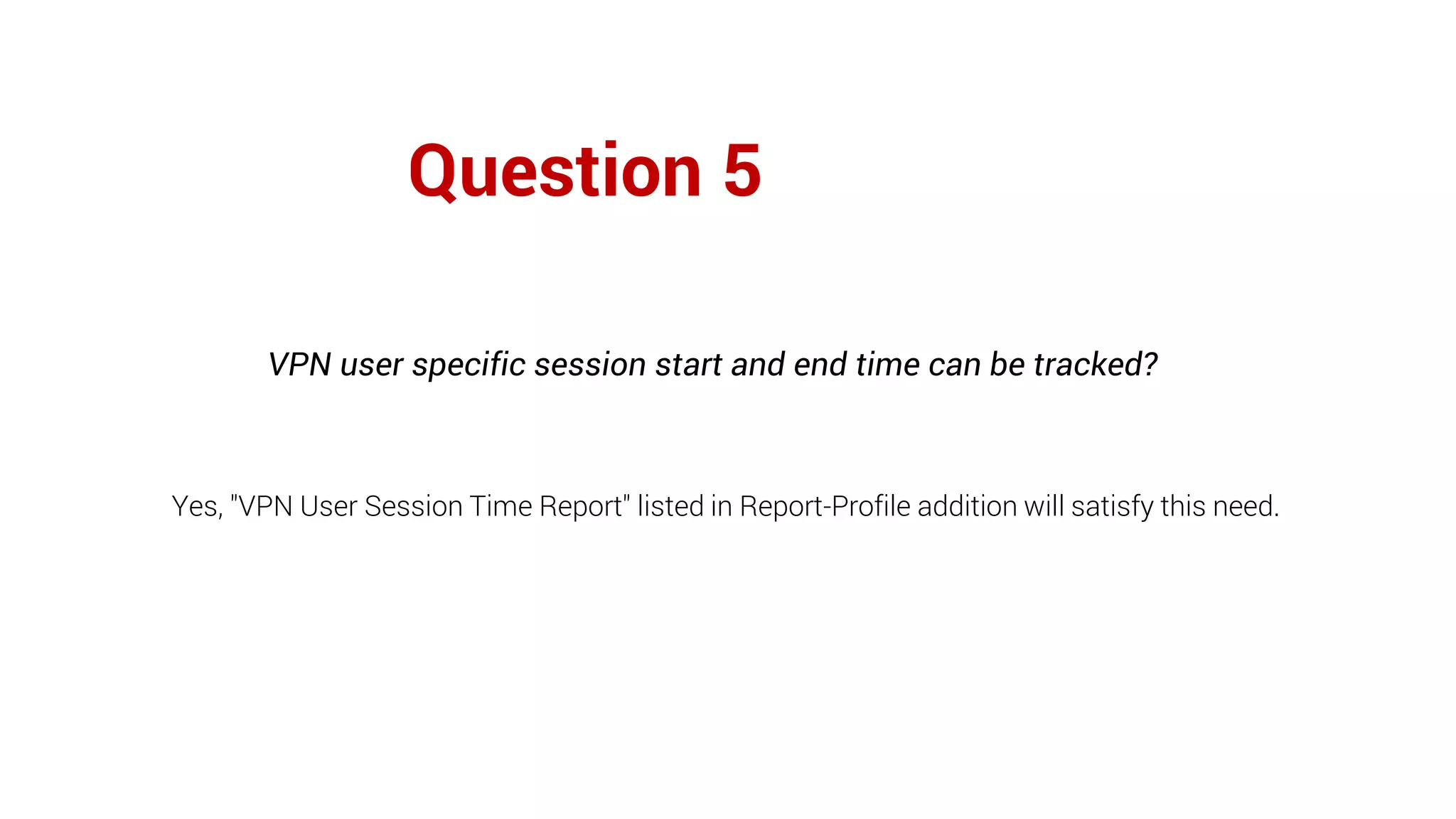
Firewall Analyzer is a tool that analyzes firewall logs to generate various reports. It discusses how Firewall Analyzer helps meet challenges by tracking URL activities, user bandwidth, securing networks, and performing audits. The document outlines how to install, configure and import logs into Firewall Analyzer. It describes the different types of reports that can be generated for traffic analysis, security analysis, and device management. It also discusses how to set up alarms and notifications. Questions from users are addressed at the end regarding issues like seeing traffic bytes, VPN user details, and required hard drive space.